A Quiet War in the Shadows
Suppose that, a group of hackers, backed by a powerful nation, silently infiltrates the digital fortresses of foreign governments, stealing secrets and disrupting operations all without firing a single shot. This isn’t a plot from a spy novel; it’s the reality of modern cyber warfare.
In recent years, two notorious Russian hacking groups, known as Cozy Bear and Fancy Bear, have been at the forefront of this digital battleground. Their operations have reached deep into the heart of European and American institutions, with the Netherlands becoming a significant focal point in this clandestine conflict.
Who Are the Fancy Bear and Cozy Bear?
Cozy Bear (APT29): Cozy Bear, also identified as APT29, is believed to be linked to Russia’s Foreign Intelligence Service (SVR). Operating since at least 2008, this group specializes in cyber espionage, targeting government agencies, think tanks, and corporations worldwide. Their methods are sophisticated and stealthy, often involving spear-phishing campaigns and custom malware to infiltrate networks and remain undetected for extended periods.
Fancy Bear (APT28): Fancy Bear, or APT28, is associated with Russia’s military intelligence agency, the GRU. Active since around 2004, this group is known for its aggressive tactics, including the use of zero-day exploits and phishing attacks. Their targets have included military organizations, political entities, and media outlets, with a notable focus on disrupting democratic processes and gathering military intelligence.
The Dutch Connection: A Frontline in Cyber Espionage
The Netherlands has found itself at the center of several significant cyber espionage incidents attributed to these Russian hacking groups.
Infiltration of Dutch Intelligence
In a remarkable counterintelligence operation, the Dutch General Intelligence and Security Service (AIVD) managed to infiltrate Cozy Bear’s operations. By compromising the group’s security cameras, AIVD monitored their activities for at least a year starting in 2014. This surveillance provided critical insights into Cozy Bear’s methods and targets, including their involvement in the 2016 U.S. presidential election interference.
Attack on Dutch Police Networks
In September 2024, a previously unknown Russian hacking group, later dubbed “Laundry Bear,” executed a cyberattack on Dutch police networks. The breach exposed work-related contact details of all Dutch police officers. Intelligence officials believe Laundry Bear is linked to the Kremlin and is actively targeting EU and NATO countries to steal information related to military equipment and aid to Ukraine.
How Do These Attacks Happen?
Cyberattacks by groups like Cozy Bear and Fancy Bear typically follow a calculated, multi-stage workflow designed to maximize stealth and impact. It begins with reconnaissance, where attackers quietly collect detailed information about the target such as employee email formats, software in use, and possible weak points often by scanning public resources or using open-source intelligence (OSINT). Once sufficient data is gathered, the attackers move to the initial compromise phase, most commonly through spear-phishing emails that appear legitimate but carry malicious links or attachments. Alternatively, they may exploit unpatched software vulnerabilities to gain unauthorized access.
After breaching the network, they establish a foothold by installing backdoors or remote access tools, allowing them to persist within the system even after restarts or user logouts. With this persistence, they move laterally, seeking elevated privileges and access to critical systems. Once they locate valuable information like confidential documents, communications, or login credentials they proceed with data exfiltration, covertly transferring the data to external servers under their control. To ensure their presence remains undetected, attackers meticulously cover their tracks by deleting logs, encrypting command histories, and using stealth techniques that mimic normal network activity. This entire process can unfold over weeks or even months, often going unnoticed until significant damage is done.
The Human and Economic Cost
The impact of these cyber espionage activities is profound:
- Security Risks: Exposure of sensitive information can compromise national security and endanger lives.
- Economic Losses: The theft of intellectual property and confidential data can result in significant financial losses for businesses and governments.
- Public Trust: Repeated breaches erode public confidence in institutions’ ability to protect personal and national data.
Global Implications
The cyberattacks linked to Russian-backed groups like Cozy Bear (APT29) and Fancy Bear (APT28) extend far beyond the Netherlands. These operations are part of a wider geopolitical strategy leveraging digital espionage to destabilize democratic processes, steal state secrets, and gain leverage in international affairs. Below are key examples highlighting their global reach:
- 🇺🇸 United States
Both Cozy Bear and Fancy Bear played major roles in the 2016 breach of the Democratic National Committee (DNC). Their aim was not just to steal data but to influence the U.S. presidential election, sow distrust in democratic institutions, and manipulate public discourse. The attack involved stolen emails, strategic leaks, and disinformation campaigns that were distributed through social media and media outlets. - 🇫🇷 France
Fancy Bear was reportedly involved in targeting French government agencies and institutions tied to the upcoming 2024 Paris Olympics. These cyber incursions raised red flags about Russia’s long-term objectives whether for intelligence gathering, disruption of critical events, or retaliation against perceived geopolitical rivals. - 🇺🇦 Ukraine
Ukraine has been a consistent target of Russian cyber aggression, with attacks aimed at critical infrastructure such as power grids, financial systems, and military networks. These operations are tightly linked to ongoing kinetic conflict and are used to weaken national stability and cause widespread fear and disruption.
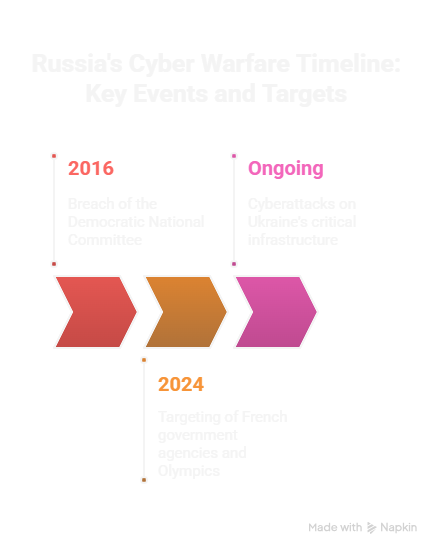
These examples prove that such attacks are strategic, state-sponsored, and global, not random acts of hacking. The implications are severe for governments, private corporations, and citizens worldwide, particularly in Europe and the United States, where political, economic, and defense systems are high-value targets.
Protecting Yourself and Your Organization
In today’s cybersecurity climate especially when facing advanced persistent threats (APTs) like Fancy Bear and Cozy Bear passive defenses are no longer enough. A proactive, layered approach is essential. Here’s what individuals and organizations must implement:
1. Endpoint Security: Secure every device laptops, mobile phones, IoT gadgets, servers connected to your network. Use enterprise-grade antivirus software and endpoint detection and response (EDR), and ensure all devices are regularly scanned and updated. Unprotected devices are often exploited as entry points into larger systems.
2. Employee Awareness Training: Phishing remains the number one method attackers use to get in. Employees must be trained regularly to spot suspicious emails, malicious attachments, and social engineering tactics. Organizations should conduct simulated phishing exercises to improve real-world awareness.
3. Patch and Update Regularly: Outdated software is one of the most exploited vulnerabilities in successful cyberattacks. Maintain a strict patching schedule for all operating systems, applications, and firmware. Automated patch management systems can make this easier at scale.
4. Continuous Network Monitoring: Use Security Information and Event Management (SIEM) tools to track real-time activity across your infrastructure. Monitoring for unusual behavior, privilege escalation, lateral movement, and data exfiltration attempts allows teams to respond before the damage is done.
5. Incident Response Plan (IRP): Prepare for the inevitable. Every organization big or small needs a tested incident response plan. It should include roles, responsibilities, communication protocols, and recovery procedures. Run tabletop exercises quarterly to keep teams sharp.
Need Help to Minimize These Threats?
If you’re unsure where your organization stands or how to begin strengthening your cybersecurity posture, consider consulting with Hoplon Infosec. Our experts provide specialized services such as
· Endpoint Protection & EDR Implementation
· Deep and Dark Web Threat Monitoring
· Tailored Risk Assessments and Advisory for EU and U.S. Markets
Whether you’re a startup, an SME, or a global enterprise Hoplon Infosec can help identify your weak points and close the gaps before attackers find them.
Conclusion
The activities of Cozy Bear and Fancy Bear underscore the evolving nature of global threats in the digital age. As cyber espionage becomes increasingly sophisticated, the importance of robust cybersecurity measures cannot be overstated. By understanding these threats and proactively defending against them, individuals and organizations can better protect themselves in this ongoing digital conflict.




