In a striking turn of events, Canadian airline WestJet became the latest high-profile victim of a cyberattack. The breach occurred during a period of significant geopolitical focus the G‑7 summit, hosted in Alberta, Canada. As global leaders convened to discuss pressing international concerns, including cybersecurity and artificial intelligence, one of the country’s largest airlines faced an internal system breach that raised immediate questions about national cyber resilience and aviation safety.
Although WestJet swiftly issued a public confirmation and began working with law enforcement agencies, the attack sparked alarm across industry and government sectors. Its timing, impact on consumers, and potential geopolitical significance make it one of the most important cyber incidents in North America this June.
The Breach Unfolds: What Happened to WestJet?
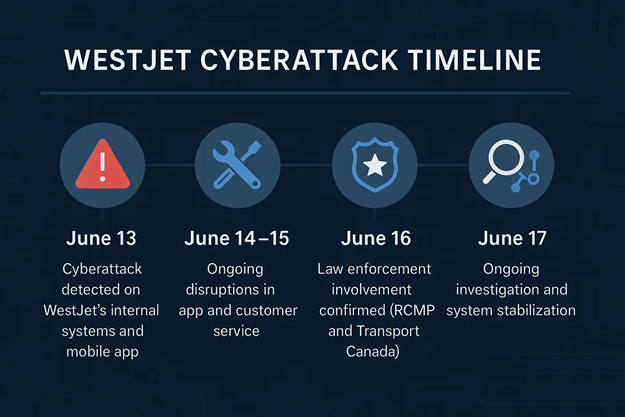
WestJet confirmed the cyberattack on June 13, 2025, citing issues affecting both its mobile app and internal IT systems. Users began reporting problems with the airline’s digital infrastructure particularly with flight bookings, customer service communication, and account access. Although no flight delays were officially tied to the incident, the mobile application experienced significant outages, disrupting the traveler experience at a critical time.
The airline acted swiftly, collaborating with the Royal Canadian Mounted Police (RCMP), Transport Canada, and other federal authorities. The exact scope of the attack, including whether any customer data was exfiltrated, has not yet been publicly disclosed. However, WestJet’s fast response and coordinated efforts were intended to contain the damage before it could expand into a full-scale data leak or ransomware event.
The G‑7 Summit Context: Timing That Raises Eyebrows
The most eyebrow-raising element of the breach was not merely the system disruption but its timing. The G‑7 summit, hosted in Alberta during the same weekend, included multiple discussions on global cyber threats, digital sovereignty, and AI regulation. As world leaders debated the future of cybersecurity governance, a real-world example played out just kilometers away.
This proximity raises questions about the potential motivations behind the attack. Was it merely a coincidence? Or was the breach timed to send a political message or exploit stretched national security resources during the summit? Although speculative, these questions underscore how cyber threats can be carefully orchestrated to maximize symbolic impact.
Data at Risk: What Could Have Been Compromised?
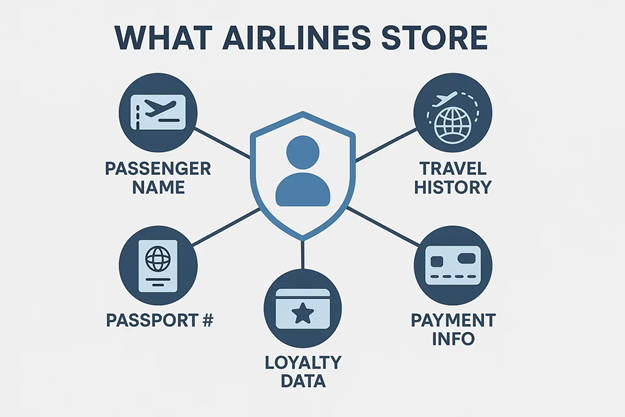
While WestJet has not disclosed whether sensitive data was compromised, the possibility remains significant. Airlines hold a wealth of customer information, ranging from names and contact details to payment credentials and passport data. In addition, mobile apps and internal systems often contain travel history, loyalty program records, and even government-issued IDs.
The potential abuse of this data can range from identity theft and credit card fraud to more serious consequences such as surveillance of high-profile travelers or phishing campaigns impersonating the airline. The integration of customer service, ticketing, and analytics into a single digital ecosystem makes any breach a serious matter with multi-layered exposure points.
How This Compares to Past Aviation Breaches
WestJet’s cyberattack is not the first time the aviation sector has been targeted. Over the past decade, numerous airlines have fallen victim to breaches that range from credential theft to large-scale data exfiltration. This trend highlights how air travel continues to be a lucrative and symbolic target for attackers, be they criminal groups or state-sponsored actors.
| Incident | Year | Airline | Type of Breach | Data Compromised |
| British Airways | 2018 | British Airways | Payment form skimming | Payment data, contact info |
| Air India | 2021 | Air India | Third-party system breach | 4.5M passengers’ data |
| WestJet | 2025 | WestJet (Canada) | Internal IT breach | Unknown (ongoing assessment) |
WestJet now joins a growing list of carriers dealing with complex digital intrusions. What makes this event stand out is not only its location but the surrounding political circumstances, further heightening its severity.
Why the Aviation Sector Remains Vulnerable
Airlines are prime targets for cybercriminals due to their heavy reliance on digital infrastructure and vast stores of sensitive personal data. The nature of airline IT ecosystems often fragmented across legacy systems, cloud platforms, third-party vendors, and mobile apps makes them inherently difficult to defend.
In addition, airlines frequently deal with high volumes of user logins, payment processing, and identity verification, all of which are vulnerable points of entry. Even a temporary disruption in these systems can cause cascading operational and reputational damage.
Cybersecurity in aviation is often underfunded relative to the level of threat. While most carriers maintain some form of defense, the pace of innovation in the cybersecurity threat landscape often outstrips the airline industry’s ability to adapt.
Canada’s Cybersecurity Response and Law Enforcement Involvement

Upon detecting the breach, WestJet immediately engaged the RCMP and Transport Canada, both of which are actively involved in cybersecurity incident response. Federal cybersecurity agencies are now assessing whether the attack originated from a known threat actor, such as a ransomware gang or nation-state group.
Canada’s Canadian Centre for Cyber Security has not issued a public advisory yet, but internal evaluations are likely underway. If a geopolitical actor is eventually identified, it could prompt broader discussions among G‑7 nations about coordinated cyber response frameworks and digital sovereignty.
The fact that such a breach occurred during a time of heightened national security presence further reinforces the need for cross-agency coordination and public–private information sharing. It also tests the resilience of Canada’s national cybersecurity strategy in real time.
Could This Be a State-Sponsored Attack?
One of the most compelling and speculative angles of the WestJet breach is the possibility of foreign nation-state involvement. While there is currently no official attribution, the alignment of the attack with the G‑7 summit raises questions about motive and origin.
Geopolitical adversaries have long targeted symbolic infrastructure during high-profile events. From Olympic Games to political summits, state-sponsored actors often use cyberattacks to create disruption, embarrassment, or strategic distraction. WestJet’s prominence, combined with its proximity to a major international summit, positions it as a tempting target.
If investigations do reveal foreign involvement, the breach could become a diplomatic flashpoint. It would also mark a turning point in how cyberattacks on civilian transportation are interpreted, not just as criminal acts but as political signals.
The Business Impact: Trust and Reputation
Even without a confirmed data leak, the reputational damage to WestJet is non-trivial. Airlines depend heavily on customer trust, particularly when it comes to the handling of personal and payment data. A breach can lead to customer attrition, regulatory scrutiny, and increased insurance costs.
In a competitive market, where customer loyalty is hard-won and easily lost, any crack in perceived security can have lasting consequences. Moreover, the airline may now face new regulatory requirements to strengthen its cybersecurity protocols, adding operational overhead in an already strained industry.
Companies affected by cyberattacks are also subject to legal ramifications, especially if it’s found that insufficient security controls were in place. Data privacy laws in Canada, such as the Personal Information Protection and Electronic Documents Act (PIPEDA), require companies to disclose breaches in a timely manner and mitigate risks to affected individuals.
Cybersecurity Lessons for the Airline Industry
The WestJet incident offers several clear lessons for the broader aviation sector. First, cybersecurity must be treated as mission-critical infrastructure, not just an IT responsibility. Executive teams and boards must integrate cyber risk into core decision-making.
Second, airlines must improve their resilience through the adoption of Zero Trust models, continuous monitoring, and incident response simulations. This includes routine penetration testing, threat intelligence sharing, and mandatory multi-factor authentication across all systems.
Third, supply chain risk management must be a priority. Airlines often rely on dozens of third-party software and infrastructure vendors. Ensuring each partner meets baseline cybersecurity standards is essential to prevent breaches through indirect vectors.
Finally, customer communication during and after such events must be transparent, timely, and reassuring. Clear updates, access to support, and proactive identity monitoring services can go a long way in maintaining public confidence.
The G‑7 Implication: A Real-Time Test Case

The WestJet breach has already become a case study in what the G‑7 summit aims to address: cyber resilience across critical infrastructure. It brings urgency to conversations around cross-border digital protections, shared threat intelligence, and accountability for transnational cybercrime.
Leaders at the summit are likely to use this incident as a springboard for more concrete cooperation frameworks and faster adoption of shared cybersecurity protocols. The incident underscores that no sector, not even aviation, is exempt from the global tide of cyber threats.
In a sense, this attack served as a live demonstration of the issues on the summit’s agenda. It is a potent reminder that cybersecurity policy is not theoretical; it’s a necessity.
Conclusion
The WestJet cyberattack stands out not only for its operational disruption but for its symbolic timing. Occurring during the G‑7 summit, it revealed the vulnerabilities inherent in our most critical sectors, aviation, transportation, and consumer services. Whether or not the incident is eventually linked to a state-sponsored actor, it has already catalyzed discussions at the highest levels.
This incident should serve as a wake-up call to all public-facing industries that cybersecurity is not a back-office function but a frontline defense. For WestJet, it marks a challenging chapter but also an opportunity to lead the way in post-incident transparency, defense, and customer communication.
For governments and global organizations, it’s yet another signal that the cyber battlefield has moved from theory to daily reality. The time for coordinated defense, robust regulation, and systemic investment in cybersecurity has arrived.
Did you find this article helpful? Follow us on Twitter and LinkedIn for more Cyber Security news and updates. Stay connected on Facebook and Instagram as well. At Hoplon Infosec, we’re committed to securing your digital world.




