Cybersecurity threats have become increasingly common across both private and public institutions, with attackers targeting vulnerable systems to exploit sensitive data. In one of the most alarming incidents in 2025, the Texas Department of Transportation (TxDOT) confirmed a massive data breach that exposed the personal information of over 423,000 individuals. The breach centered on the department’s Crash Records Information System (CRIS), a critical database used by police departments, legal professionals, and insurers to access official crash data across Texas.
This breach wasn’t just a technical failure; it was a wake-up call for government agencies across North America. In a time when public trust hinges on how data is protected and handled, the incident raised difficult questions about transparency, oversight, and preparedness.
In this in-depth analysis, we’ll explore how the breach happened, what data was exposed, how TxDOT responded, and what this breach means for the future of public-sector cybersecurity.
The Breach Timeline: From Suspicion to Confirmation

Detection on May 12, 2025
The breach was first detected on May 12, 2025, when TxDOT’s cybersecurity team noticed suspicious behavior involving one of its internal accounts. The account had begun downloading an unusually large number of crash reports, almost 300,000 in total, within a short time window. This behavior triggered security alerts, prompting immediate investigation.
The agency acted swiftly to contain the breach by disabling the compromised account and conducting a deeper analysis to determine the scope and method of intrusion. Initial forensics suggested that the breach stemmed from unauthorized access via compromised credentials rather than a more advanced external exploit.
Containment and Initial Investigation
By the end of the same day, the compromised user credentials were revoked, and access to the CRIS database was temporarily restricted while security experts assessed the damage. TxDOT collaborated with external cybersecurity consultants and notified the Texas Department of Information Resources (DIR), which oversees IT security policies for state agencies.
An internal review followed, focusing on how the account was compromised, how such a large data extraction went unnoticed for any length of time, and what additional safeguards needed to be implemented immediately.
What Was Stolen: The Nature of the Exposed Data
Depth and Sensitivity of the Breached Information
Despite the absence of passwords, Social Security numbers, or banking details, the exposed information remained deeply personal and sensitive. Each crash report contained multiple pieces of identifiable data, such as
- Full names
- Home addresses
- Driver’s license numbers
- License plate numbers
- Contact details like phone numbers and emails
- Insurance policy numbers
- Crash details and law enforcement narratives
This information is particularly valuable to criminals. It enables identity theft, phishing schemes, and insurance fraud, and it may even be exploited in targeted harassment, especially if the reports involve victims of domestic violence or serious personal injury.
In many cases, crash reports also include witness statements, descriptions of injuries, and pending legal information, all of which could be exploited for financial or reputational harm.
Volume of Impacted Individuals
While 300,000 crash reports were downloaded, the total number of people affected exceeded 423,000, since multiple individuals are often listed in each report. TxDOT confirmed this number in early June, stating that it represented a broad sample of the state’s population and included people from nearly every major city in Texas.
Public Notification: Delays and Controversy
Weeks Without Public Disclosure
Despite detecting the breach on May 12 and containing it the same day, TxDOT did not inform the public until early June. This delay sparked significant criticism from privacy advocates, state legislators, and affected residents. Critics argued that earlier disclosure would have given individuals a chance to protect themselves by placing credit freezes, alerting insurers, or monitoring their driver records for suspicious activity.
The agency stated that time was needed to validate the breach, confirm the scope of impact, and prepare formal notification letters, which began reaching residents in the second week of June. However, under Texas law, entities must disclose breaches “as quickly as possible,” which many interpret as meaning within days, not weeks.
Communication Shortcomings
TxDOT posted a limited statement on its website and provided a contact number for affected individuals, but no widespread press release or media briefing was issued. As a result, many people learned about the breach through media coverage rather than directly from the agency itself.
This lack of transparency damaged public trust. In several community forums and local news comment sections, individuals expressed outrage at not being contacted, even though they were involved in vehicle crashes in the recent past. Others questioned the agency’s preparedness and its commitment to protecting public data.

Individual Consequences: What Victims Face
Identity Theft and Impersonation
Driver’s license numbers and home addresses are high-value data points on the black market. With enough context, especially when combined with insurance information and phone numbers, criminals can build a full profile to impersonate someone, apply for credit, or file fraudulent insurance claims. Victims may face months or years of administrative hassle trying to restore their identity and correct misinformation.
Phishing and Social Engineering
Another concern is social engineering. With access to real-world crash data, a scammer could pose as a lawyer, insurance agent, or government worker and reference the victim’s accident details to gain trust. Such an act could lead to further data loss, account compromise, or even financial fraud.
Victims were advised to monitor their credit, be cautious of unsolicited calls, and avoid clicking on links in suspicious emails. Unfortunately, TxDOT did not offer credit monitoring or identity theft protection, further frustrating those impacted.
The State’s Official Response
Remediation Efforts
TxDOT claimed to have launched a full audit of its digital infrastructure. They also promised to enforce stronger access controls, review all CRIS user permissions, and introduce additional anomaly detection protocols. Despite not disclosing specific technical changes publicly, the agency collaborated with third-party security experts to identify flaws and propose several long-term improvements.
Officials from the Texas Attorney General’s Office and Department of Information Resources were also involved in assessing the damage and helping establish whether any regulatory actions were required.
Lack of Material Support for Victims
TxDOT did not provide the free credit monitoring services typically offered in corporate breaches. The justification given was that financial data such as banking or credit card numbers were not part of the breach. However, consumer rights advocates have argued that the depth of exposed PII and crash report content still warrants protective services, especially given the risks associated with identity fraud and impersonation.
National Relevance: How TxDOT Compares to Other 2025 Breaches
To put the TxDOT breach in perspective, it’s useful to compare it to other major data breaches that have occurred this year. Although some breaches affected more victims, the sensitive and contextually rich nature of the data in the TxDOT breach makes it particularly harmful.
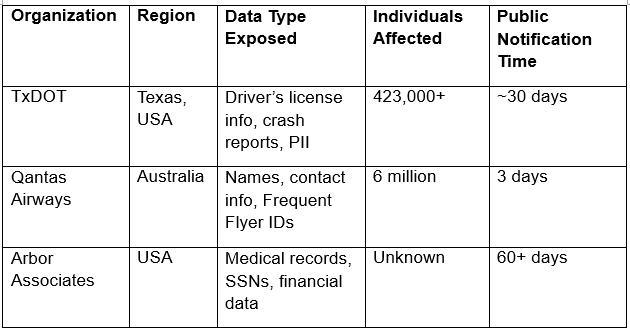
In terms of scale, Qantas affected more users, but the TxDOT data was more contextually sensitive, especially as crash reports can intersect with court cases, health insurance claims, and trauma-related events.
Policy Implications and Legislative Response

Need for Stricter Reporting Laws
The delay in disclosure reignited debates about how soon government agencies should be required to notify the public of a data breach. Many states, including Texas, have relatively vague language in their breach notification laws, allowing leeway that may hurt consumers. Some Texas lawmakers have now proposed tightening the language, suggesting mandatory notice within 7 business days of breach confirmation.
Call for a Cybersecurity Task Force
Following the breach, several Texas lawmakers began advocating for the creation of a Texas Cybersecurity Task Force, a specialized team focused on securing public infrastructure. Its mandate would include regular audits, training programs, centralized threat detection, and a public reporting dashboard.
There are also increasing calls for federal standards for public-sector cybersecurity, similar to what private companies must follow under data protection laws like HIPAA or the GDPR.
Lessons Learned and Next Steps
The TxDOT breach shows that technical tools are only part of the solution. A robust cybersecurity posture must also include policies, training, communication strategies, and public trust measures.
Public agencies should limit access based on job roles, enforce multifactor authentication, and encrypt internal data, even when it is “just” for state use. Agencies must also prioritize detection: spotting abnormal behavior quickly is key to limiting damage.
Most importantly, community agencies should support those affected, not just offer apologies, when citizens’ data is at risk. to support those affected, not just offer apologies.
Conclusion
The TxDOT data breach stands as one of the most significant and troubling cyber incidents of 2025, not because of sheer volume, but because of the real-world harm it could cause and the inadequate public response that followed. It illustrates how even well-funded government agencies can fail to protect the data entrusted to them and how systemic issues, like vague notification laws and insufficient internal controls, can compound the damage.
For Texans, this incident is a cautionary tale about the fragility of personal data stored in public systems. For state and federal governments, it is a mandate for action: modernize infrastructure, enforce strong cybersecurity standards, and prioritize public transparency. Until such steps are taken, breaches like this won’t be the exception; they’ll be the norm.
Did you find this article helpful? Or want to know more about our Cybersecurity Products Services?
Explore our main services >>
Mobile Security
Endpoint Security
Deep and Dark Web Monitoring
ISO Certification and AI-Management System
Web Application Security Testing
Penetration Testing
Follow us on X (Twitter) and LinkedIn for more Cyber Security news and updates. Stay connected on Facebook and Instagram as well. At Hoplon Infosec, we’re committed to securing your digital world.