On July 6, 2025, Ingram Micro, one of the world’s largest IT distribution companies, confirmed it had suffered a ransomware attack that affected parts of its internal systems. Headquartered in Irvine, California, and operating in more than 160 countries, Ingram Micro is a critical supply chain hub for thousands of retailers, resellers, and enterprise clients across North America. The industry was shocked not only by the high-profile nature of the victim but also by the potential cascading effects on hardware and software supply channels caused by this cyberattack.
While the company worked to contain and investigate the breach, cybersecurity experts raised alarms about the far-reaching consequences such an attack could have on the broader digital ecosystem. The Ingram Micro incident is more than just a company under siege; it underscores persistent vulnerabilities in global IT supply chains and raises urgent questions about resilience, preparedness, and risk mitigation across the sector.
Who is Ingram Micro?
Ingram Micro is a Fortune 100 global technology and supply chain services provider. It acts as an intermediary between hardware manufacturers (like Cisco, HP, Apple, and Lenovo) and vendors, value-added resellers, managed service providers, cloud service providers, and enterprise clients. The company plays a crucial logistical and financial role in distributing IT products, providing cloud solutions, and offering lifecycle services for devices and enterprise infrastructure.
With its massive operational footprint, any disruption at Ingram Micro can affect entire industries, particularly in North America, where tech product distribution and just-in-time hardware inventory depend heavily on logistics reliability and cybersecurity integrity.
What Happened?
On July 6, Ingram Micro publicly confirmed that it had identified a ransomware incident affecting “certain internal systems.” Although details are still limited at this stage, the company stated that it has initiated its cybersecurity protocols, taken steps to isolate the affected infrastructure, and engaged third-party forensics and cybersecurity consultants to evaluate the situation.

Initial reports suggest that phishing or third-party compromise, common entry points for such attacks, may have stealthily introduced the ransomware infection. While the company did not confirm the specific variant of ransomware used, experts suspect a financially motivated group may be behind it, possibly one of the many sophisticated ransomware-as-a-service (RaaS) operations currently active.
Crucially, Ingram Micro did not immediately disclose whether customer data was compromised, whether sensitive internal documents were exfiltrated, or whether a ransom had been demanded or paid. The company is reportedly working with law enforcement agencies, including the FBI and CISA, as part of the ongoing investigation.
How The Ingram Micro Faces A Ransomware Attack (Timeline of the Attack)
Understanding the timeline of a cyberattack provides clarity in how events unfold behind the scenes:
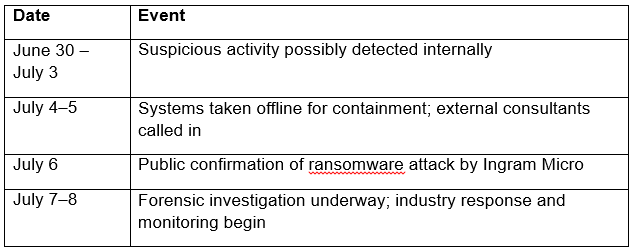
The industry has initiated its response and monitoring, while the forensic investigation is in progress.
While Ingram Micro acted swiftly once the attack was discovered, some cybersecurity experts suggest that the attacker may have been quietly active in their systems for weeks, if not months. This aligns with common ransomware Tactics, Techniques, and Procedures (TTPs), where lateral movement and privilege escalation precede the encryption event.
Potential Impact on Clients and Supply Chains

One of the major concerns in the wake of this ransomware attack is the potential impact on Ingram Micro’s clients, especially resellers and logistics partners in North America. Ingram handles IT infrastructure distribution and warranty services for numerous businesses, from small managed service providers to Fortune 500 companies.
If backend systems were affected, such as order fulfillment platforms, warehouse automation, or partner access portals, it could result in shipment delays, miscommunication with vendors, and disruption in cloud provisioning services. In turn, this could cause delays in enterprise projects, end-user device rollouts, and even security patch delivery, particularly if the affected systems manage update distribution or secure device onboarding.
Furthermore, the compromise of any customer data, particularly reseller contracts or configuration templates, could pave the way for downstream attacks on business partners. Supply chain cyberattacks like these often serve as springboards for attackers to pivot toward other valuable targets, using stolen credentials or intelligence gathered during the breach.
Is This Another Kaseya Moment?
The situation draws comparisons to the infamous Kaseya VSA ransomware attack in July 2021, where remote management software used by thousands of MSPs was exploited by the REvil group. That attack directly impacted over 1,500 businesses globally.
While Ingram Micro is not a software vendor in the same sense, its role in logistics and cloud distribution creates a similar “single point of failure” scenario. If the attackers gained access to Ingram’s enterprise cloud portals or had visibility into partner network configurations, they could hypothetically use this to compromise downstream businesses.
This risk indicates the importance of third-party risk management policies and cyber insurance scrutiny, as vendors and clients alike assess their exposure to this breach.
Industry Reaction
Within 24 hours of the public disclosure, the North American cybersecurity community reacted swiftly. The Cybersecurity and Infrastructure Security Agency (CISA) issued a preliminary advisory encouraging organizations that rely on Ingram Micro to review their access controls, change passwords for any integrated systems, and monitor for suspicious activity.
Several vendors also reached out to customers via email, clarifying that their platforms remained unaffected but urging caution. Incident response teams across retail, healthcare, finance, and education sectors began running threat hunts to ensure no infiltration occurred through third-party connections.
Meanwhile, cybersecurity experts emphasized that the attack was yet another example of how threat actors increasingly target supply chain intermediaries to maximize impact with minimum effort.
Who Might Be Responsible?

While no group has formally claimed responsibility, the nature of the attack strongly suggests involvement from a professional ransomware syndicate. Security researchers have floated names like LockBit 4.0, Black Basta, or 8Base, which have been active in 2025 and known for targeting North American organizations with double-extortion techniques.
These groups encrypt victim systems and exfiltrate sensitive data, threatening to publish it on leak sites unless a ransom is paid. It remains unclear whether Ingram Micro’s data has appeared on any known dark web forums or leak sites, but threat monitoring groups are actively scanning for indicators.
Implications for Cyber Insurance and Compliance
Incidents like this tend to ripple beyond IT teams and hit legal and compliance departments hard. For Ingram Micro, the fallout could include:
- Regulatory investigations under U.S. data breach notification laws
- Partners may file lawsuits if they discover compromised customer data.
- There may be SEC disclosure requirements if the attack impacts public financial statements.
- Organizations may need to reassess their cyber insurance coverage and risk profile.
Organizations that work with Ingram Micro may also be asked by auditors and insurance providers to document their exposure and response to the incident, further straining already-overburdened cybersecurity teams.
The Bigger Picture: Supply Chain Insecurity

The Ingram Micro ransomware attack is not an isolated incident but part of a growing trend of attacks on critical intermediaries in the tech and logistics sectors. Attackers are targeting the underlying infrastructure of various services, including software vendors and third-party billing services.
This trend reflects several harsh truths:
1. Intermediaries hold massive systemic leverage; a disruption at one point can affect hundreds or thousands of businesses.
2. Resilience is uneven; any supply chain companies lack the mature cybersecurity frameworks found in banking or healthcare.
3. Incident response must be collective: when a major vendor is breached, clients must activate contingency plans, not just wait for updates.
The attack reinforces the need for real-time supply chain visibility, risk scoring of vendors, zero trust policies, and contractual enforcement of cybersecurity standards in third-party agreements.
Lessons for Other Organizations
The Ingram Micro attack offers several valuable lessons for IT and security teams:
- Reevaluate Vendor Dependencies: Organizations should assess which suppliers and platforms are “critical” and ensure backups, redundancies, and exit plans exist.
- Strengthen Segmentation: Network and data segmentation can prevent ransomware spread across departments or functions.
- Test Third-Party Access: If Ingram Micro or any vendor integrates with your environment (e.g., API, SSO, shipping automation), audit those connections and access controls.
- Practice Incident Drills: Ransomware response needs to be drilled regularly, with updated playbooks, cross-functional roles, and decision-making escalation paths.
Organizations can learn from this incident and prevent surprises if one of their other vendors becomes compromised.
What’s Next?
As of July 8, Ingram Micro is continuing to investigate the incident, and more details are expected to be released in the coming days. Customers are advised to stay alert for updates, rotate credentials associated with Ingram Micro services, and monitor access logs for anomalies.
In the broader cybersecurity ecosystem, this incident is likely to spur:
- Stricter vendor assessments and risk scoring by CISOs
- Revisions to contractual obligations with distributors
- Greater pressure on the supply chain industry to adopt zero-trust architecture
- Renewed interest in cyber insurance coverage clauses specific to ransomware and supply chain interruption
Conclusion
The ransomware attack on Ingram Micro is a sobering reminder that even the most established players in tech distribution are not immune to cyber threats. It reveals persistent weaknesses in third-party and supply chain cybersecurity while emphasizing that it requires continuous monitoring, shared responsibility, and collective defense.
As digital ecosystems become more interconnected, securing the supply chain is no longer optional; it is a strategic imperative. Businesses must invest in better cyber hygiene, risk awareness, and contingency planning not just for themselves, but for every link in their operational chain. The Ingram Micro attack may not be the last of its kind in 2025, but it could be the one that pushes the industry toward real systemic change.
Did you find this article helpful? Or want to know more about our Cybersecurity Products Services?
Explore our main services >>
Mobile Security
Endpoint Security
Deep and Dark Web Monitoring
ISO Certification and AI-Management System
Web Application Security Testing
Penetration Testing
For more services go to our homepage
Follow us on X (Twitter), LinkedIn for more Cyber Security news and updates. Stay connected on YouTube, Facebook and Instagram as well. At Hoplon Infosec, we’re committed to securing your digital world.




