Cybersecurity researchers started raising concerns about a new and dangerous ransomware strain known as Bert in July 2025. Initially detected in Europe and quickly confirmed in North America and Southeast Asia, Bert represents a significant evolution in ransomware campaigns due to its multi-platform capabilities and strategic targeting of high-value industries such as healthcare, technology, and event services.
The Bert ransomware is designed to encrypt both Windows and Linux systems, making it a formidable threat in hybrid environments. With no known affiliations to established ransomware families and no public data leak portal yet identified, Bert’s emergence has triggered intense scrutiny and proactive threat hunting across global security teams.
Origins and Early Sightings
The first incident involving Bert occurred at a mid-sized European software company. Analysts at GreyLight Threat Intelligence flagged unusual encryption activity and ransom notes labeled “Bert” embedded across file directories. Similar reports from healthcare providers in the U.S. and cloud service firms in Asia quickly followed these early attacks.
The ransom demands were made in Monero (XMR), a privacy-focused cryptocurrency,, and delivered through onion-based anonymous email channels. The group behind Bert has not established a public extortion site, leading to speculation that either the operation is in a “testing phase or the operators are employing an unusually stealthy model without public shaming.
Attribution and Capabilities
So far, no known cybercrime cartel has claimed ownership of Bert. However, similarities in coding patterns, encryption routines, and attacker behavior point to an experienced group with prior exposure to high-level ransomware development.
Key indicators suggest the group:
- Uses a codebase in Rust and C++
- Leverages red-team tools like Cobalt Strike and Sliver
- Employs obfuscation and sandbox evasion techniques
- Maintains offshore C2 infrastructure with bulletproof hosting providers
Researchers believe the operators may be former affiliates of LockBit or ALPHV (BlackCat) who have rebranded under a new campaign, possibly to avoid sanctions, reputation fatigue, or international law enforcement pressure.
Attack Vectors and Infection Methods
Bert ransomware utilizes a multi-pronged approach to infiltration and payload delivery. Its infection chain is highly modular, allowing it to adapt based on the target’s architecture and defenses.
Common initial access techniques include:
- Phishing attacks with malicious attachments disguised as invoices or reports
- Exploitation of known vulnerabilities, such as:
- Fortinet VPN (CVE-2023-27997)
- Microsoft Exchange ProxyShell chain
- Apache Struts has flaws in outdated web apps.
- Abuse of remote monitoring tools, which involves compromised installations of AnyDesk or ConnectWise, allows attackers to gain administrative-level execution.
Once inside the system, Bert quickly elevates privileges, conducts reconnaissance, and begins lateral movement. Critical services are disabled or encrypted, and backup directories are wiped or overwritten to ensure maximum coercion.
Multi-Platform Payload Design

One of the most dangerous features of Bert is its ability to affect both Windows and Linux operating systems. Most ransomware variants focus exclusively on Windows machines, but Bert expands its attack surface considerably through dual-architecture binaries.
In Linux environments, the ransomware:
- Encrypts backend systems running enterprise web applications
- Targets ESXi virtualization hosts
- Removes syslog and history files to cover its tracks.
- Disables cron jobs and daemons to prevent system recovery
This makes Bert especially dangerous in DevOps-heavy or cloud-native organizations, where Linux infrastructure forms the backbone of critical operations. The Windows variant mirrors these features but also includes logic to bypass Windows Defender, kill database processes, and disable system restore.
Industry Impact and Sector Disruption

Healthcare Sector
Hospitals and medical systems have suffered some of the earliest and most damaging attacks. In Canada and the U.S., several facilities reported full system outages that prevented access to electronic medical records (EMRs), appointment systems, and diagnostic machines. These outages created serious risks to patient safety and forced administrators into downtime protocols that included manual record-keeping and patient deferrals.
Healthcare providers, under legal obligations such as HIPAA, face added financial risk due to regulatory non-compliance if patient data is leaked, though no confirmed leaks have occurred as of writing.
Technology and SaaS Firms
Targets have also included cloud service providers and DevOps platform companies. Infections on Linux servers disrupted customer-facing portals, APIs, and internal CI/CD pipelines. The Linux-targeting variant’s ability to affect container orchestration environments such as Docker and Kubernetes underscores how this attack can cripple even well-architected systems.
In some cases, entire production environments were temporarily shut down as security teams scrambled to assess impact and recover from backups.
Event and Entertainment Services
Bert has also affected event ticketing platforms and live venue service providers. In Germany and Texas, ticketing systems were encrypted hours before large-scale events, resulting in access delays, partial refunds, and a loss of public trust. Although this sector is not classified as “critical infrastructure,” its revenue-per-minute nature makes it highly vulnerable to even short-lived disruptions.
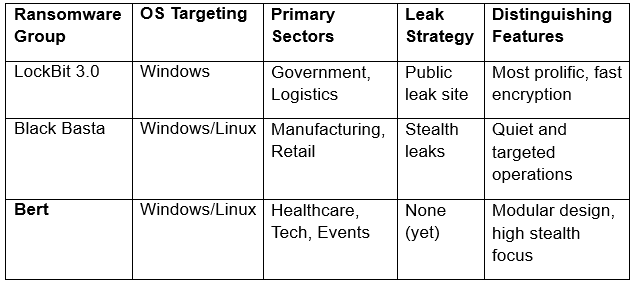
Comparative Snapshot
To better understand Bert’s threat profile, here is a side-by-side comparison with other active ransomware families:
Ransom Demands and Communication
Bert drops ransom notes that include a victim-specific ID and instructions to initiate contact via encrypted messaging platforms or Tor-based email. The demands typically range from 2 to 15 XMR, roughly $300,000 to $1.5 million USD, depending on organization size and perceived data value.

The attackers have avoided use of web-based negotiation portals, possibly to evade tracking. Some speculate that Bert may be testing victim responsiveness or avoiding early exposure as it fine-tunes its strategy.
So far, no victims have publicly admitted to paying, and no data has surfaced on leak forums. However, the silence could indicate privately negotiated settlements, a common tactic among companies hoping to avoid reputation damage.
Technical Characteristics
The Bert ransomware payload exhibits advanced features that differentiate it from more common strains. Upon execution, the malware:
- Uses AES-256 to encrypt data with unique keys
- Terminates common database services (MySQL, MSSQL, PostgreSQL)
- Deletes Windows shadow copies and disables recovery services
- Alters Linux init scripts and clears audit logs
- Conducts environment awareness checks to detect sandbox analysis
The ransomware’s ability to delay execution until after credential harvesting or admin privilege escalation makes it harder to detect using static file scans alone.
Response Challenges
Bert’s stealth, speed, and platform versatility make it extremely difficult to contain once deployed. Many organizations rely on traditional antivirus tools that may not detect fileless or obfuscated malware. Furthermore, Linux environments often lack adequate defense against endpoint detection and response (EDR).
For organizations under active attack, incident response teams must isolate affected subnets, disable all remote access tools, and begin forensic memory analysis immediately. Communication must also be coordinated internally (to prevent panic) and externally (to meet any regulatory notification requirements).
Mitigation and Defense Recommendations
To defend against Bert and similar threats, cybersecurity leaders should focus on a layered defense strategy.
Priority recommendations include:
- Ensure full patching of all externally facing systems, including VPNs and web servers.
- Hardening RMM tools with MFA, IP restrictions, and alerting
- Deploying Linux-compatible EDR agents across all cloud workloads and servers
- We are conducting tabletop exercises that focus on ransomware scenarios specific to healthcare and technology operations.
- Implementing immutable backups stored offline or in segmented cloud environments
Security awareness training should be updated to include emerging phishing tactics and social engineering campaigns, particularly those targeting medical, financial, or administrative staff.
Law Enforcement and Global Response
National and international cybersecurity agencies are monitoring Bert closely. The FBI’s Internet Crime Complaint Center (IC3) has released detailed flash bulletins with known indicators of compromise (IOCs), while Europol’s J-CAT task forcee has included Bert on its active investigation radar.
Private cybersecurity vendors have also acted swiftly. CrowdStrike, SentinelOne, and Palo Alto Networks have released threat detection signatures, and third-party threat feeds are actively tracking Bert’s C2 infrastructure.
Governments in the U.S. and EU are discussing policy updates requiring faster breach disclosures and minimum baseline security for healthcare and software providers. Some insurance companies are even revising policy terms to account for Linux-based ransomware risks, previously overlooked in underwriting.
Conclusion
The Bert ransomware campaign represents an evolution in cyber extortion, one that is more selective, cross-platform, and operationally silent. By targeting sectors where even a few hours of downtime can result in lost lives or massive revenue loss, the actors behind Bert are maximizing pressure while minimizing public exposure.
Its absence of a leak site or PR-driven taunting suggests a quiet but calculated strategy, possibly one still evolving. Whether Bert becomes a short-lived threat or the next LockBit will depend largely on how the global security community responds over the coming weeks.
In the meantime, organizations, especially in healthcare and technology, must treat Bert not as a hypothetical risk but as an active, adaptable threat. Preparation, detection, and a strong incident response culture are no longer optional. In the age of modern ransomware, they are the new minimum standard.
Did you find this article helpful? Or want to know more about our Cybersecurity Products Services?
Explore our main services >>
Mobile Security
Endpoint Security
Deep and Dark Web Monitoring
ISO Certification and AI-Management System
Web Application Security Testing
Penetration Testing
For more services go to our homepage
Follow us on X (Twitter), LinkedIn for more Cyber Security news and updates. Stay connected on YouTube, Facebook and Instagram as well. At Hoplon Infosec, we’re committed to securing your digital world.