Imagine this. You are just looking for a cool mod for your favorite game. Maybe it is GTA or Minecraft. You click a link someone shared in a Discord server or Telegram group. It looks normal, maybe even exciting. But the moment you open that file, your private data starts leaking silently. This is how most of the Gen Z cybersecurity threats are happening today. You need to hear about this. Stay with me. I’ll explain what’s happening, who’s doing it, how they’re doing it, and how to stay safe.
What actually happened?
Between April 2024 and March 2025, cyber attackers launched over 19 million attempts to trick Gen Z users into downloading fake game files. These files were disguised as cracked versions, mods, or cheats for games like GTA, Minecraft, and Call of Duty. Instead of fun content, these downloads contained malware that stole user information. Kaspersky reported a direct impact on approximately 400,000 users during this period.
The attackers used the most popular games among Gen Z as bait. For example, fake GTA files triggered over 4.4 million attacks, Minecraft led to 4.1 million, and Call of Duty about 2.6 million. The goal was simple. Use fake game tools to get Gen Z users to install harmful software. Once installed, the malware would start collecting sensitive data, including credentials, social media access, and payment details. This was one of the biggest examples of targeted Gen Z cybersecurity threats seen in recent years.
Why Gen Z Is the Perfect Target
Let us take a moment to understand why Gen Z is being targeted more than any other group. Gen Z users have grown up with the internet. They spend a lot of time online, especially in gaming and social media spaces. But they often prioritize speed over safety. Quick clicks, fast downloads, and a strong belief in tech-savviness can create a false sense of security.
Many Gen Z users feel confident online, but studies have shown that this confidence does not always match their cybersecurity habits. Phishing emails, fake download links, and social engineering attacks are not always simple to spot. And because Gen Z likes to share and explore, attackers know this is the easiest group to exploit through peer-to-peer links, shared mods, and enticing new tools.
This makes Gen Z cybersecurity threats different from others. The attackers are not always looking for millions of dollars from companies. Sometimes they just want access to social accounts, Steam credits, or personal data that can be used later. The low barrier to success is what makes these attacks so frequent and dangerous.
How it happened: the workflow
Let me walk you through the process, step by step. Picture someone setting a trap with candy. In this case, the candy was your favorite video game cheat or mod.
Step one. The attackers identified which games Gen Z users love the most. They focused on titles like Minecraft, GTA, Roblox, and Call of Duty. These are games that young users play daily. That made them the perfect bait.
Step two. The criminals created fake installers that looked like mods or cheats. These were uploaded to file-sharing platforms, chat groups, and even fake websites. The files were named to match the real content they imitated, so they did not look suspicious at first glance.
Step three. Distribution occurred in locations where Gen Z typically spends time. Discord servers, Telegram groups, shady mod websites, and sometimes even YouTube video descriptions. Links were posted offering exclusive content or rare cheats.
Step four. A user downloaded and opened the file. At this point, the malware silently installed itself on the system. Most of the time, the user saw nothing strange. But in the background, tools like Hexon Stealer began scanning for browser data, Discord tokens, game login information, and even cryptocurrency wallets.
Step five. All the stolen data was sent back to the attacker. Sometimes they sold it on dark web forums. Sometimes they used it themselves to break into more accounts. Either way, the victim lost access to valuable accounts and sometimes suffered financial loss.
This process shows how easy it is for Gen Z cybersecurity threats to succeed. Young users trust their peers. They download content without double-checking. And the attackers know this very well.
Who was behind the attack?

Now let us talk about who did this. No single criminal gang has claimed responsibility. But investigators believe it is the work of several small cybercrime groups working independently or in partnership. These groups often operate in what is called the malware-as-a-service model. That means one person develops the malware and rents it out to others who distribute it.
Cybersecurity Threats are often made up of younger people. Some are teenagers who started off in gaming communities. They understand how Gen Z behaves. They know where Gen Z hangs out online. And they use that knowledge to make the attacks believable.
Often, the malware used was Hexon Stealer, a tool designed to collect login credentials, browser data, and app tokens. Some of these operators might also be linked to groups known for similar behavior, like Lapsus$ or Scattered Spider. Those names might sound funny, but their actions cause serious damage. In this campaign, the criminals stayed in the shadows, using encrypted messaging apps and anonymous wallets.
This kind of attacker is dangerous because they look like you. They are from your age group. They act like friends. But they are building traps behind the scenes to gain control of your digital life. That is what makes Gen Z cybersecurity threats so serious.
Consequences and financial impact; impact on individuals
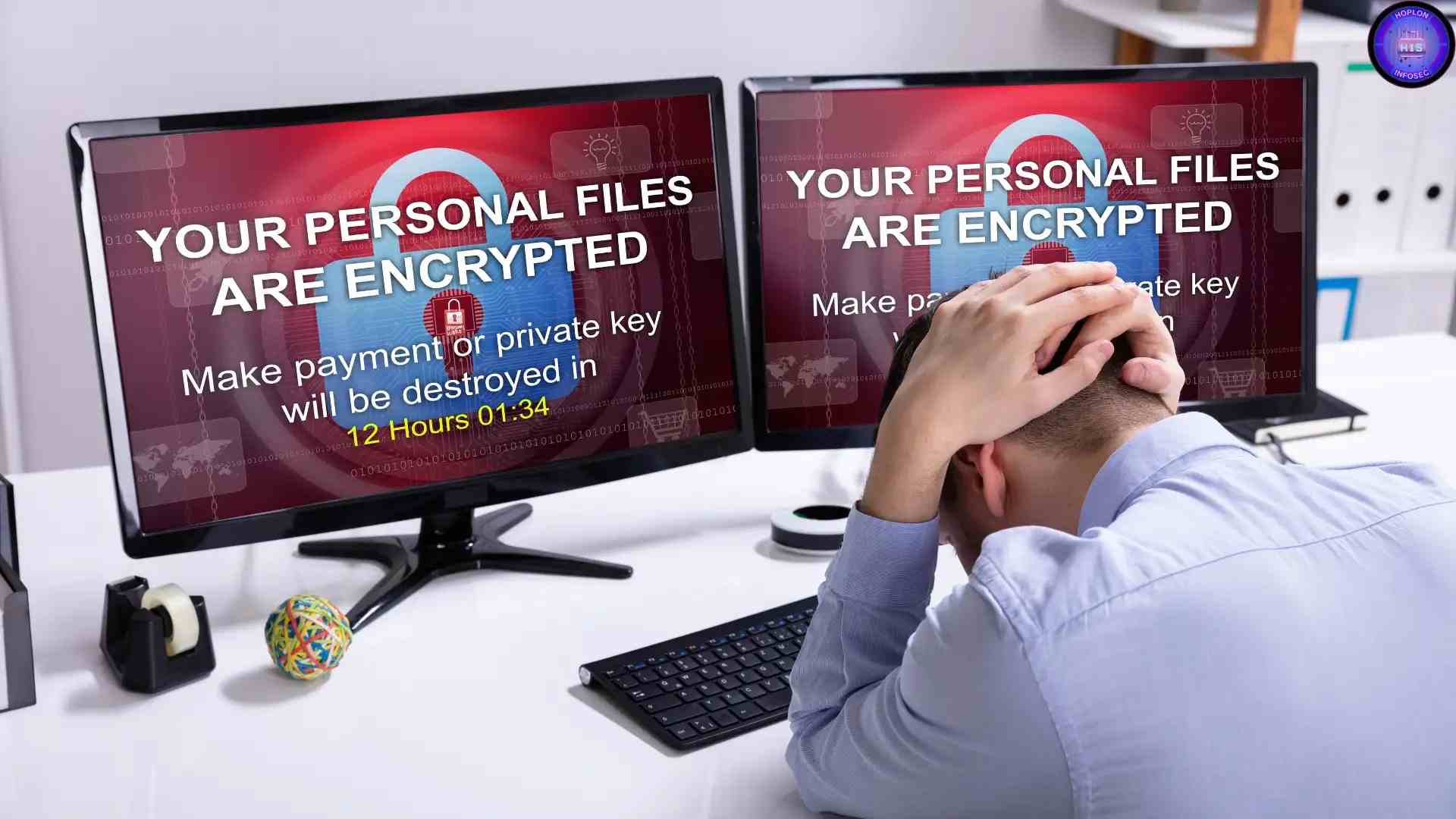
The financial impact was huge. Imagine this. You download what you think is a game cheat. The next day, you try to log in to your Discord or Steam account, and you are locked out. Your profile picture has changed, your messages are being sent to strangers, and your in-game purchases are gone.
This is what happened to thousands of victims. They lost access to their gaming accounts, their social media profiles, and sometimes their banking apps. Some victims reported unauthorized purchases. Others had their saved payment details stolen. And for younger users, it often meant going to parents or guardians and explaining what happened.
There was also a heavy emotional impact. Being hacked makes you feel exposed. It breaks trust. Many young victims said they felt embarrassed and scared. In some cases, victims were bullied after their accounts were misused. One young user reported that his Instagram account was used to send offensive messages. He lost friends and followers before he could even explain.
On a broader level, this incident was a warning. Journalists highlighted how Gen Z, despite being born in the digital world, are not naturally safe. International news agencies discussed the need for better digital literacy. Some governments even considered stricter rules for file-sharing sites. The whole world saw how real Gen Z cybersecurity threats have become.
How to protect yourself
Let us discuss the ways you can protect yourself. This is the part you really need to remember.
First, never download game files or mods from random links. Use official sources only. If a friend sends you a file, double-check where it came from.
Second, always use strong passwords. Make them long, use symbols, and do not reuse the same password on different sites. Use a password manager to keep track.
Third, enable two-factor authentication. Use an app, not your SMS. That extra step will stop most attackers.
Fourth, scan new files before opening them. Use trusted antivirus software. And if something feels odd, do not run the file.
Fifth, avoid running programs as an administrator unless it is truly necessary. That gives malware full control over your device.
Sixth, please make it a habit to regularly review your accounts. See if there is any unusual activity. If you notice any issues, please update your passwords promptly.
Lastly, learn. Study how stealers work. Understand how phishing looks. Teach your friends too. Stay informed. This is your digital life, and you have to guard it.
Summary list of actions
Only use trusted websites to download mods.
- Avoid clicking unknown game links in chats.
- Use long and unique passwords
- Turn on two-factor authenticatio
- Always scan downloaded files.
- Monitor account activity regularly
- Study basic cybersecurity tactics
Lessons learned from Gen Z Cybersecurity Threats
Let us wrap up by looking at what we have learned. Gen Z is a prime target. Your online activity surpasses everyone else’s, not because you lack intelligence. You trust links from your friends. You act fast. That speed makes you vulnerable.
The attackers are smart. They do not need giant budgets or advanced skills. They just need to know what tricks work. And right now, fake game mods work extremely well.
This incident shows the importance of caution. If a file appears excessively promising, it’s likely fraudulent. If a cheat promises unlimited game points, think twice.
Final tips
- Share this knowledge with your friends.
- Take your online safety seriously.
- Always double-check before you download.
- Think before you click.
In closing, we must realize this is not just about losing a game account. This is about your identity, your finances, and your privacy. Gen Z cybersecurity threats are growing fast. The best defense is awareness.
What Hoplon Infosec does
At Hoplon Infosec, we are working hard to educate young people. We provide training programs, simulations of phishing attacks, and detection strategies. Our goal is to help you recognize danger before it hits. We teach you how to protect yourself in this connected world.
Stay safe. Stay alert. The internet is yours, but only if you protect it.
Explore our main services:
- Mobile Security
- Endpoint Security
- Deep and Dark Web Monitoring
- ISO Certification and AI Management System
- Web Application Security Testing
- Penetration Testing
For more services, go to our homepage.
Follow us on X (Twitter) and LinkedIn for more cybersecurity news and updates. Stay connected on YouTube, Facebook, and Instagram as well. At Hoplon Infosec, we’re committed to securing your digital world.