You download a VPN app to protect your online privacy, but instead it exposes your device to hidden threats. These fake VPN apps look legitimate but are designed to steal sensitive data, install malware, and monitor your every move. Cybercriminals are using them to silently breach personal and corporate networks.
To stay protected, you need more than awareness.
You need a cyber security incident response plan that stops fake VPN scams before they spread.
As digital threats continue to evolve, organizations and individuals must remain alert to one of the fastest-growing cyber scams recently: fake VPN apps. Despite their seemingly legitimate appearance, these malicious tools aim to steal user data, infect devices with malware, or conduct covert surveillance. With the increasing sophistication of cybercriminals, having a solid cybersecurity incident response plan in place is no longer optional. It is essential.
In this article, we explore what fake VPN apps are, how they deceive users, and why their growing popularity poses a serious risk. We also break down major scam campaigns, signs of fake apps, and how to choose safe alternatives. Most importantly, we explain how a robust cybersecurity response plan can help detect, contain, and neutralize these threats before serious damage occurs.
What Are Fake VPN Apps?
Fake VPN apps are malicious programs that disguise themselves as legitimate security tools. A real VPN aims to encrypt internet traffic and safeguard user privacy, whereas a fake VPN operates in the opposite manner. These apps often come with sleek user interfaces and false promises of free or unlimited security services. However, behind the scenes, they are collecting your private data, injecting malware, or tracking your activities.
Many users trust these apps simply because they are listed in app stores or advertised on social media. This false sense of legitimacy allows scammers to spread their malicious apps widely and rapidly. Including the detection of fake VPNs in your cybersecurity incident response plan allows your security team to isolate suspicious apps quickly, avoiding widespread compromise. Moreover, a well-maintained cybersecurity incident response plan ensures that any threats from such deceptive tools are addressed efficiently before they can cause serious damage.
How Fake VPNs Scam Users
Fake VPN apps operate through social engineering, technical deception, and manipulation of trust. Scammers design these apps to look like real VPNs, often copying logos, names, and color schemes of trusted providers. Once installed, these fake VPNs may display fake encryption messages, purporting to secure your connection, but in reality, they are monitoring or harvesting your data.
Some fake VPNs also encourage users to enter sensitive information, such as email credentials, bank details, or even login information for work-related platforms. Phishing techniques collect valuable data or enable access to broader networks. To counter this type of threat, your cybersecurity incident response plan should include guidelines for early detection, system isolation, and post-incident analysis of malicious apps.
Major fake VPN campaigns were uncovered.
Several cybersecurity firms have reported widespread campaigns involving fake VPNs. These campaigns have been known to affect millions of users around the world. In certain instances, major app marketplaces hosted malicious apps that remained undetected for weeks. During that time, they collected user data, redirected users to harmful sites, or infected devices with trojans and spyware.
One notable campaign involved a series of fake VPNs installed by users who believed they were accessing restricted content. In reality, the apps connected devices to remote command centers controlled by hackers. The absence of a proper cybersecurity incident response plan allowed these attacks to go unnoticed in many organizations, leading to massive data breaches.
How to Identify a Fake VPN App
Identifying fake VPN apps requires a careful examination of multiple factors. First, look at the source of the download. Trusted VPNs are typically available only through official websites or verified app store pages. An unknown third-party site hosting the app is a major red flag. Second, consider the app’s reviews. Suspicious or overly generic reviews, especially those posted in large quantities over a short time, can indicate fraud.
Check the permissions requested by the app. A real VPN does not need access to your photos, contacts, or microphone. If the app demands access to features that have nothing to do with internet privacy, it should be considered dangerous. Including these checks in your cybersecurity incident response plan enables your organization to educate users and reduce risk exposure.
The Risks of Using Fake VPNs
Installing and using fake VPNs can lead to serious consequences. These risks include identity theft, unauthorized access to banking information, and complete control over the user’s device by a remote attacker. Some fake VPNs have even been linked to ransomware attacks, where the victim’s files are locked until a ransom is paid.
For organizations, the damage can extend further. Fake VPNs installed on employee devices can act as a gateway into internal systems, compromising customer data or intellectual property. This kind of breach could severely damage a company’s reputation. A clear and tested cybersecurity incident response plan provides the structured approach necessary to contain and eliminate such threats before escalation.
Common Myths Scammers Use to Trick Users
Cybercriminals often use misinformation to convince users to install their fake VPN apps. One of the most common myths is that all free VPNs are safe and that privacy is guaranteed simply by using a VPN. Another widespread misconception is that any app available in the Google Play Store or Apple App Store must have passed a strict security review.
Other myths include claims that VPNs protect users from all types of malware or that no technical knowledge is needed to stay secure online. These misleading statements are meant to lower the user’s guard. To combat this, your cybersecurity incident response plan should include a regular awareness campaign and security training to debunk these myths and prepare users for real-world threats.
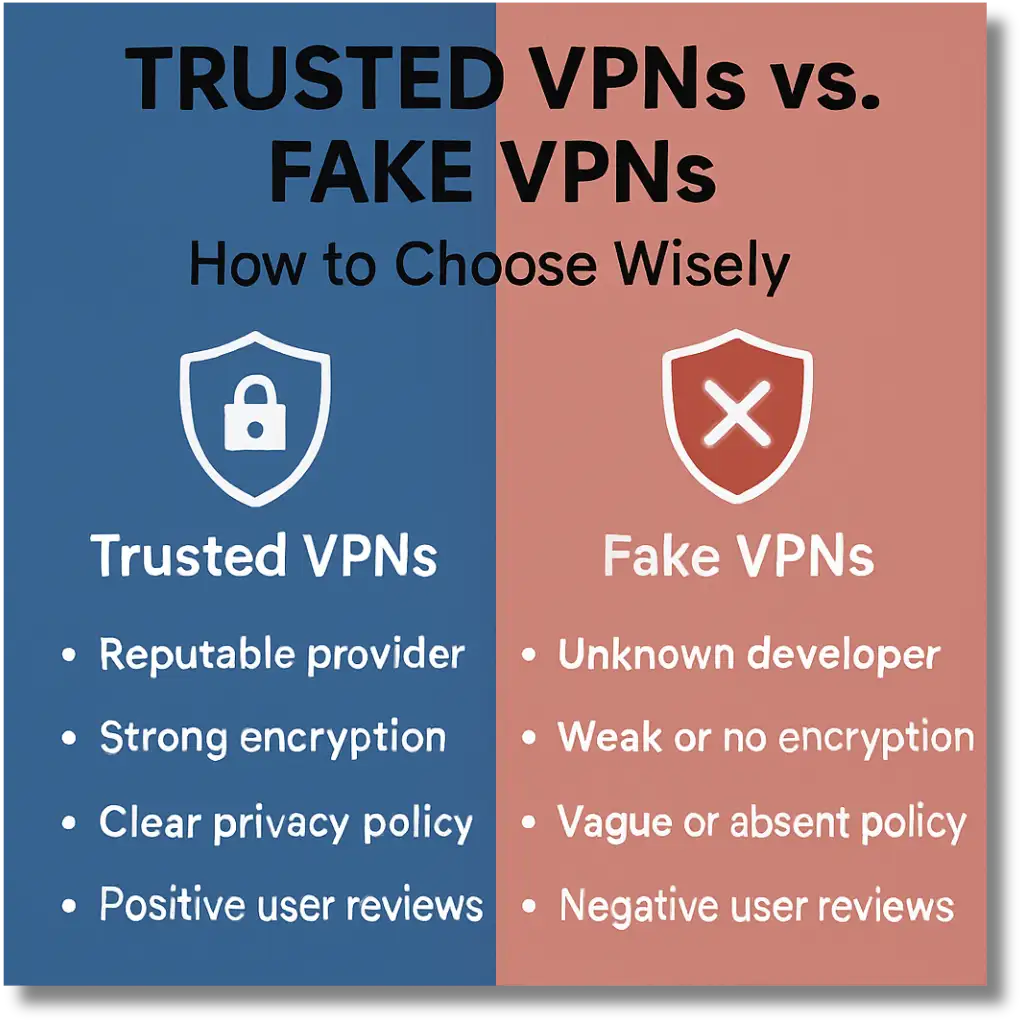
The best way to stay safe is to choose your VPN provider wisely. A trusted VPN provider will offer transparency regarding its data policies, encryption standards, and privacy practices. Look for independent security audits, customer support availability, and strong reputations in the cybersecurity community.
Fake VPNs often avoid such transparency and may provide no technical documentation or direct contact information. Before deploying any VPN software within your organization, verify the provider’s credentials and ensure it aligns with your internal security standards. Integrating this evaluation process into your cybersecurity incident response plan guarantees that only secure, vetted software is used.
How to Stay Safe from VPN Scams
Avoiding fake VPN scams requires a proactive approach. Never download apps from unknown sources or install software based on a pop-up ad. Use antivirus tools that include VPN monitoring features to detect suspicious activities. Keep your mobile and desktop operating systems up-to-date, and monitor network traffic for irregular behavior.
For companies, employee training and access controls can make a huge difference. Establish strict policies on mobile device management and remote software installation. Your cybersecurity incident response plan should also include a real-time alert system that flags unauthorized VPN use or data traffic anomalies.
Final Thoughts: The Growing Threat of Fake VPNs
The rise of fake VPN apps is a serious concern that shows no sign of slowing down. As these threats become more sophisticated, the need for a dedicated cybersecurity incident response plan becomes increasingly urgent. With sensitive data and online privacy at stake, ignoring the problem is not an option.
By adopting a proactive approach and preparing a comprehensive cybersecurity incident response plan, individuals and organizations can defend themselves against these hidden dangers. Staying educated, applying strict security policies, and performing regular incident simulations are key components of long-term protection.
How Hoplon Infosec Can Help
Hoplon Infosec provides tailored solutions to support your organization’s cybersecurity efforts. We help you build a custom cybersecurity incident response plan that includes tools for threat detection, malware containment, and user awareness. Whether you are dealing with a fake VPN app or another form of digital fraud, our specialists are equipped to help you respond quickly and effectively.
With years of industry experience and a focus on innovation, Hoplon Infosec ensures that your business stays ahead of emerging cyber threats.
Action Table: Strengthen Your Incident Response Plan Against Fake VPNs
| Step | Action | Outcome |
| User Education | Train users to recognize fake VPN signs | Reduce chances of downloading fake apps |
| Secure App Sources | Use official app stores and vendor websites | Avoid counterfeit app installations |
| Monitor Network Traffic | Implement real-time network activity monitoring | Early detection of suspicious behavior |
| Incident Response Setup | Develop detailed response procedures for VPN threats | Quick containment and mitigation |
| Regular Updates | Keep software and systems up to date | Close security gaps exploited by malware |
| Use Trusted VPN Services | Choose VPNs based on security features and reputation | Minimize risk exposure |
| Partner with Experts | Collaborate with cybersecurity firms like Hoplon Infosec | Enhance overall security posture |
Fake VPN apps are a growing concern that demands proactive attention. By integrating awareness and strategic defense measures into your cyber security incident response plan, you can protect your data, privacy, and network from these scams. Stay vigilant and trust only verified VPN providers to maintain your digital security.
Explore our main services
- Mobile Security
- Endpoint Security
- Deep and Dark Web Monitoring
- ISO Certification and AI Management System
- Web Application Security Testing
- Penetration Testing
For more services, go to our homepage.
Follow us on X (Twitter) and LinkedIn for more cybersecurity news and updates. Stay connected on YouTube, Facebook, and Instagram as well. At Hoplon Infosec, we’re committed to securing your digital world.






