Erlang/OTP CVE-2025-32433 exploitation
It was a late evening in a busy telecommunications control center when a systems engineer spotted something strange in the network logs. A series of SSH connections had been made to one of their operational servers. The odd part was that none of the connections showed any sign of authentication, yet one of them had managed to execute commands. The engineer knew this was not a normal login attempt.
That night, the incident revealed a serious vulnerability later identified as Erlang/OTP CVE-2025-32433. It was a flaw that allowed remote attackers to gain control of a system without ever logging in. Similar events began appearing in other industries, proving that this was not just an isolated glitch but the start of a much bigger security concern.
What Erlang/OTP Is and Why SSH Plays a Big Role
Erlang is a programming language designed for building systems that need to stay up without interruption. OTP, which stands for Open Telecom Platform, is a collection of tools and libraries that make it easier to create applications that can handle large numbers of users and operate across multiple machines. Erlang/OTP is widely used in telecommunications, messaging services, IoT devices, and other environments where reliability matters most.
Part of Erlang/OTP’s appeal is that it comes with a built-in SSH server. SSH, or Secure Shell, allows administrators to securely connect to a system, run commands, and make updates. In an operational technology environment, this remote management capability is extremely useful. However, the same convenience that makes it attractive can also become a security risk if the SSH service has a flaw. This is exactly what happened with Erlang/OTP CVE-2025-32433.
Understanding the Core of the Vulnerability
The flaw in Erlang/OTP CVE-2025-32433 was found in how the SSH server processed certain messages. Normally, when someone connects to an SSH service, they must authenticate before the server allows them to perform any action. In this case, a specific type of message called SSH_MSG_CHANNEL_OPEN was processed before authentication had been completed.
This meant an attacker could craft a message that tricked the system into opening a communication channel without verifying their identity. Once that happened, the attacker could execute commands remotely as if they had been fully authenticated. In simple terms, the vulnerability allowed remote code execution before login. This kind of weakness is highly dangerous because it bypasses one of the core safeguards of secure remote access.
The Patch Arrives, but the Race Against Attackers Begins
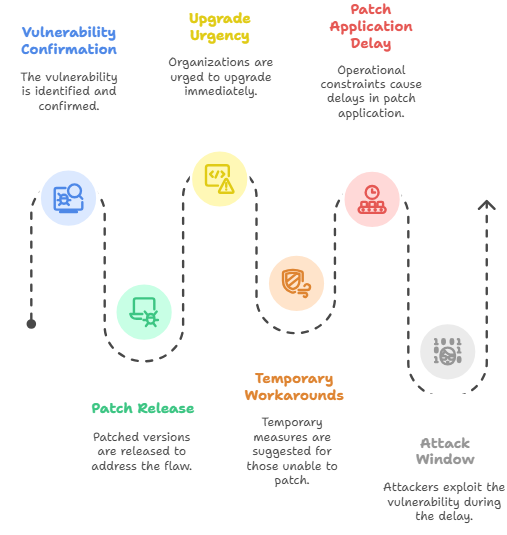
As soon as the Vulnerability was confirmed, the Erlang/OTP maintainers released patched versions that removed the flaw. These included OTP-27.3.3, OTP-26.2.5.11, and OTP-25.3.2.20. Organizations running older versions were urged to upgrade immediately.
For those unable to patch right away, temporary workarounds were suggested. These included disabling the built-in SSH service completely or using firewall rules to limit which IP addresses could connect. While these were effective short-term measures, they were not perfect. In many operational networks, taking systems offline for updates is difficult because it can interrupt production. This delay between the release of the patch and its application left a critical window of opportunity for attackers.
The Start of Real-World Exploitation
By May 2025, security researchers and monitoring firms began detecting active exploitation of Erlang/OTP CVE-2025-32433. Attackers were scanning the internet for vulnerable systems and sending the crafted SSH messages that triggered the flaw. Once access was gained, many attackers deployed reverse shells, allowing them to control the system from anywhere in the world.
What made these attacks so dangerous was their stealth. Since no login credentials were required, intrusion detection systems that relied on failed login attempts often missed them. In some incidents, organizations only discovered the breach after noticing data transfers or unusual processes running on their machines. This proved how quickly a public vulnerability could be weaponized.
The Sectors and Regions Most Affected
Analysis from multiple cybersecurity firms showed that the majority of attacks targeted operational technology networks. About seventy percent of detected attempts were aimed at OT systems that use Erlang/OTP as part of their internal management.
The most affected sectors included healthcare, education, agriculture, media, and high-tech manufacturing. Hospitals faced the risk of disruptions to internal communications, educational institutions saw threats to their administrative systems, and agricultural operations risked downtime in automated monitoring systems. Geographically, the exploitation was spread across North America, Europe, and parts of Asia, with no single region spared from risk.
Why IT and OT Networks Are More Connected Than Many Realize
One of the most revealing aspects of this vulnerability is how it demonstrated the deep connection between information technology networks and operational technology environments. Many OT systems rely on IT services such as SSH for remote management and configuration.
When a vulnerability like Erlang/OTP CVE-2025-32433 emerges, it affects both worlds at once. A flaw in a software library that may seem like a purely IT issue can have serious consequences in factories, power plants, hospitals, and transportation systems. This overlap means that defending OT environments requires awareness of IT security flaws as well.
Defensive Strategies to Prevent Exploitation
Protecting against this kind of vulnerability starts with ensuring all affected systems are upgraded to the patched versions of Erlang/OTP. For environments where immediate patching is not possible, administrators should disable the SSH service provided by Erlang or restrict access to it using strict firewall rules.
Intrusion prevention systems can also help by detecting the specific malicious messages used in the exploitation. Network segmentation is another important defensive measure. By separating critical OT systems from internet-facing systems, organizations can reduce the likelihood of an attacker reaching vulnerable targets. Finally, continuous monitoring for unusual activity, such as unexpected outbound connections, can help detect attacks in progress.
How the Impact Spread Across Software Ecosystems
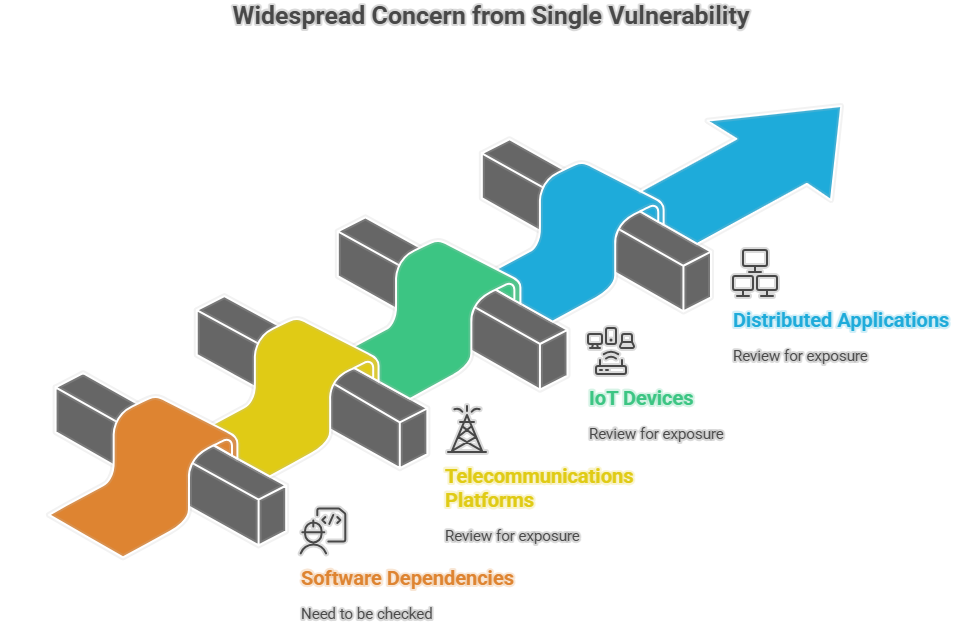
The effects of Erlang/OTP CVE-2025-32433 were not limited to organizations directly running Erlang/OTP. Many software products use Erlang/OTP as a component. For example, RabbitMQ, a widely used messaging broker, is built on Erlang. Although RabbitMQ maintainers confirmed that it was not affected by this specific flaw, the incident served as a reminder that software dependencies need to be checked whenever a vulnerability is disclosed.
Telecommunications platforms, IoT devices, and distributed application frameworks all had to be reviewed for possible exposure. This chain reaction showed that a single vulnerability in a foundational component can create widespread concern across multiple industries.
The Role of Patch Management in Preventing Erlang/OTP Exploitation
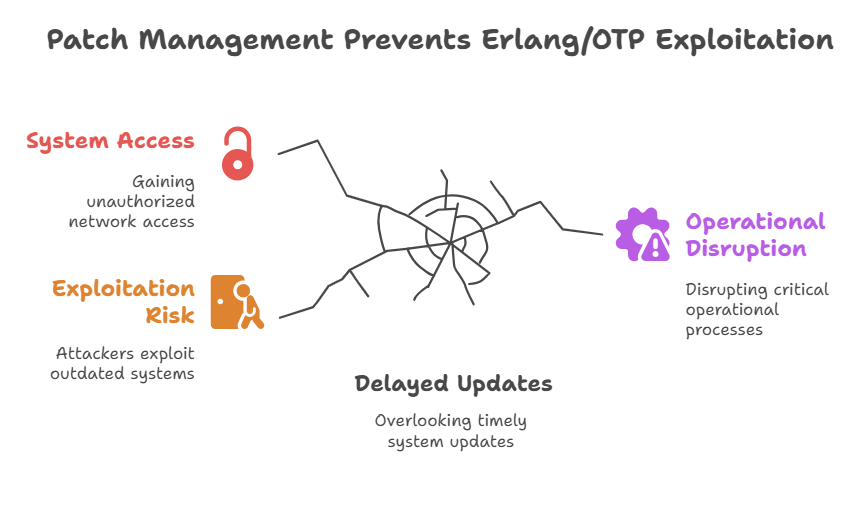
Patch management plays a critical role in defending OT networks from vulnerabilities like the recent Erlang/OTP exploitation. Many organizations overlook timely updates because patching in operational environments can be complex and risky. However, attackers actively search for outdated systems, and once they find an unpatched Erlang/OTP component, they can quickly exploit it to gain access or disrupt operations.
In this case, the Erlang/OTP vulnerability became a golden opportunity for threat actors targeting industrial systems. By delaying updates, affected organizations unknowingly provided an open door for malicious code execution.
A strong patch management strategy involves creating a detailed inventory of all devices and software within the OT network, assigning update priorities based on risk, and testing patches in a safe environment before deployment. Automation tools can also help detect missing updates and apply them efficiently, reducing the window of exposure.
If patching immediately is not possible, organizations should implement temporary security measures such as network segmentation, access controls, and intrusion prevention rules to limit exploitation risks until updates can be safely applied. In the case of the Erlang/OTP incident, companies that acted swiftly with patches and compensating controls avoided major downtime and financial loss.
Incident Response Strategies for Erlang/OTP Vulnerability Attacks
An effective incident response plan can be the difference between a contained security event and a full-scale OT network shutdown. When dealing with a vulnerability such as Erlang/OTP exploitation, speed and coordination are essential.
The first step is early detection. OT environments require specialized monitoring solutions that can identify unusual behaviors, such as unauthorized command executions or unexpected traffic patterns, which may indicate an ongoing exploitation attempt. Once detected, security teams should follow a predefined playbook that includes isolating affected systems, blocking malicious IPs, and collecting forensic data.
Communication is another key element. Internal teams, third-party vendors, and regulatory authorities must be informed promptly. This ensures that containment actions are aligned and compliance requirements are met. In the Erlang/OTP case, some organizations suffered longer downtimes because communication between IT and OT teams was delayed, allowing attackers more time to move laterally.
Post-incident analysis is equally important. Reviewing logs, attack vectors, and response timelines helps identify what worked and where the process failed. Updating the incident response plan based on these findings strengthens the organization’s resilience against future attacks.
In today’s threat landscape, every organization running OT systems should have a living, regularly tested incident response framework. The Erlang/OTP vulnerability is a reminder that preparation is not optional; it is essential for survival.
Lessons for the Future from Erlang/OTP CVE-2025-32433 exploitation
The timeline of events surrounding this vulnerability offers valuable lessons. From the moment the flaw was disclosed to the release of the patch and the beginning of active exploitation, the process moved extremely quickly. Attackers did not wait for organizations to update their systems.
This makes it clear that rapid response is essential. Organizations must have processes in place to quickly assess their exposure and apply patches or workarounds. Threat intelligence, regular vulnerability scanning, and incident response planning are all vital parts of staying ahead of similar security events in the future.
Closing Reflection
The engineer who first spotted the unusual SSH activity in the control room eventually saw their organization apply the patch, update firewall rules, and strengthen monitoring tools. The incident could have turned into a serious breach but instead became a catalyst for improved security practices.
The story of Erlang/OTP CVE-2025-32433 shows that even the most reliable tools can have weaknesses. Staying secure in today’s connected world requires vigilance, quick action, and a commitment to ongoing improvement. By understanding the risks and taking decisive steps to address them, organizations can protect both their digital and physical systems from future threats.
Hoplon Infosec provides expert support to detect and patch SSH vulnerabilities in OT systems, protecting them from cyberattacks.