In recent months, a serious Citrix vulnerability exploited in key sectors has captured the attention of cybersecurity experts worldwide. This flaw, found in widely used Citrix products, has opened doors for attackers to infiltrate sensitive systems across industries. Understanding the nature of this vulnerability, how it is being exploited, and its impact on critical sectors is essential for organizations aiming to protect themselves in an increasingly connected world.
What Is the Citrix Vulnerability?
The Citrix vulnerability exploited in key sectors refers to a security weakness in Citrix’s remote access and application delivery solutions. These products allow employees and partners to connect to corporate networks remotely, which has become essential in today’s work environment. Unfortunately, the flaw allows attackers to bypass security controls and gain unauthorized access to systems.
At its core, the vulnerability stems from improper validation of user inputs in Citrix Application Delivery Controller (ADC) and Citrix Gateway products. This weakness can lead to remote code execution, giving attackers the ability to run malicious code on targeted systems without needing valid credentials. Simply put, cybercriminals can take control of affected servers remotely, often without being detected immediately.
How Attackers Exploit the Citrix Flaw
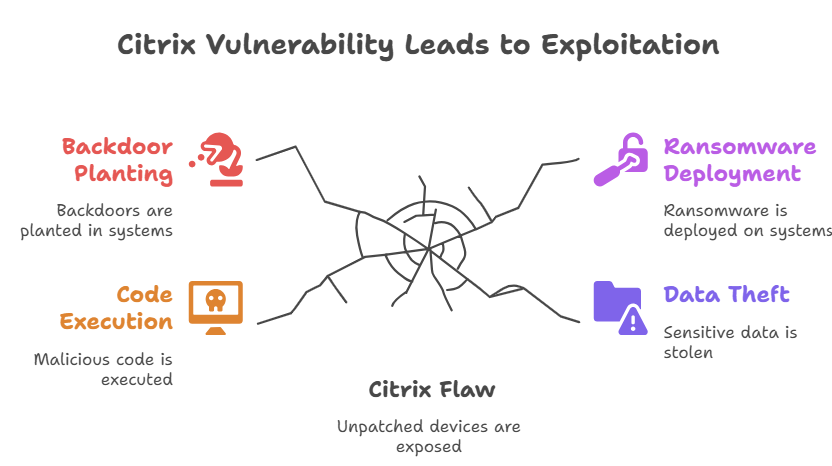
Attackers take advantage of this Citrix vulnerability exploited in key sectors by scanning the internet for exposed Citrix devices. Once they find vulnerable systems, they launch targeted attacks to execute malicious code. Common methods include exploiting the flaw to plant backdoors, deploy ransomware, or steal sensitive data.
For example, some attackers have used automated tools to scan large IP address ranges looking for unpatched Citrix servers. When found, these tools exploit the vulnerability to gain entry and move laterally inside networks. This stealthy approach makes it difficult for security teams to spot intrusions early.
Key Sectors Targeted by Exploits
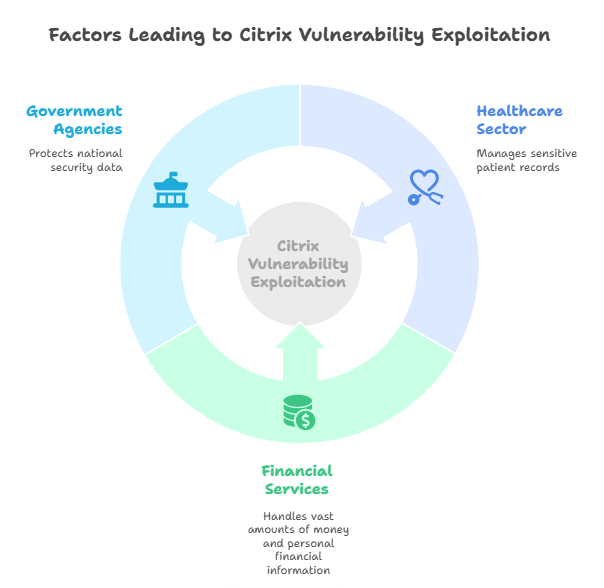
The Citrix vulnerability exploited in key sectors has not been limited to a single industry. Instead, it has impacted multiple critical sectors, including healthcare, financial services, and government. The reason behind this widespread targeting lies in the valuable data and resources these sectors hold, making them lucrative targets for cybercriminals.
Organizations in healthcare manage sensitive patient records, financial institutions handle vast amounts of money and personal financial information, and government agencies protect national security data. Attackers view these sectors as gold mines, which explains the increasing number of breaches tied to the Citrix flaw.
Impact on Healthcare Sector
Healthcare organizations have faced severe consequences due to the Citrix vulnerability exploited in key sectors. Patient data, which includes medical history and personal details, is highly sought after by attackers. Breaches can lead to identity theft, insurance fraud, and even disruption of critical medical services.
Hospitals and clinics often use Citrix solutions to provide remote access for healthcare professionals. This setup, while convenient, has also made it easier for attackers to exploit the vulnerability and gain entry into systems controlling patient information and medical devices. In some reported cases, ransomware attacks have forced hospitals to shut down critical systems, affecting patient care.
Impact on Financial Services
The financial sector is no stranger to cyberattacks, but the Citrix vulnerability exploited in key sectors has added another layer of risk. Attackers have leveraged this flaw to infiltrate banking networks, targeting sensitive customer data and transaction systems. The consequences can range from financial theft to erosion of customer trust.
Citrix products often serve as gateways for remote banking operations and internal communications. When attackers exploit these vulnerabilities, they gain access to backend systems that handle transactions, increasing the potential for fraudulent transfers or unauthorized access to accounts.
Government Sector Under Attack
Government agencies, tasked with safeguarding national infrastructure and citizen data, have also been affected by the Citrix vulnerability exploited in key sectors. The consequences of such breaches are far-reaching, involving not only data loss but also threats to national security.
Many government departments use Citrix technology to enable remote work and inter-agency communication. Cybercriminals and even nation-state actors have exploited this vulnerability to gain footholds in sensitive government networks. The resulting breaches have raised alarms over the integrity of critical services and the potential for espionage.
The Role of Remote Work in Increasing Vulnerability
The surge in remote work over the last few years has transformed the way organizations operate. While Citrix solutions have enabled flexible work environments, this shift has also expanded the attack surface for cyber threats. The Citrix vulnerability exploited in key sectors is a clear example of how increased remote access can lead to new security challenges.
With employees connecting from various locations and networks, the demand for secure, reliable remote access grew. Citrix became a popular choice to meet this demand. Unfortunately, the widespread deployment of Citrix servers, sometimes with delayed patching, provided ample opportunities for attackers to exploit vulnerabilities.
Signs Your Organization May Be Exploited
Detecting whether your organization has been targeted due to the Citrix vulnerability exploited in key sectors can be difficult. However, certain signs may indicate suspicious activity. These include unusual login attempts, unexpected system slowdowns, unknown processes running on servers, and sudden changes in network traffic patterns.
If IT teams notice repeated failed login attempts or unusual remote sessions on Citrix devices, it could mean attackers are trying to breach defenses. Monitoring for these warning signs and investigating anomalies promptly can help prevent larger incidents.
How Organizations Are Responding to the Threat
Organizations across affected sectors are responding quickly to the threat posed by the Citrix vulnerability exploited in key sectors. The first step has been issuing patches and security updates to fix the flaw. Citrix and security vendors have released detailed advisories and tools to help identify vulnerable systems.
In addition to patching, many organizations are enhancing their security posture by implementing stricter access controls, improving network segmentation, and increasing threat detection capabilities. Incident response teams have also been on high alert, ready to respond to any signs of intrusion.
Challenges in Patching and Mitigation
Despite the urgency, patching the Citrix vulnerability exploited in key sectors has not been without challenges. Some organizations run legacy systems that are difficult to update without disrupting operations. Resource constraints and lack of skilled personnel also slow down mitigation efforts.
Moreover, some administrators may underestimate the risk or delay applying patches due to concerns about compatibility issues. This delay increases the window of opportunity for attackers to exploit the vulnerability before defenses are strengthened.
Best Practices to Secure Citrix Environments
Securing Citrix environments requires a multi-layered approach. First and foremost, applying the latest patches is essential. Beyond that, organizations should enable multi-factor authentication to add a second layer of verification for remote users.
Network segmentation is another important step, limiting access to sensitive resources even if an attacker breaches the perimeter. Continuous monitoring of Citrix devices for unusual activity can help detect exploitation attempts early. Regular security audits and employee training on phishing and social engineering further strengthen defenses.
The Importance of Continuous Monitoring and Threat Detection
Continuous monitoring plays a critical role in defending against the Citrix vulnerability exploited in key sectors. Attackers often move slowly to avoid detection, making real-time analysis of network behavior vital.
Tools that provide detailed visibility into Citrix traffic, user behavior analytics, and automated alerts can give security teams the edge needed to respond quickly. Early detection can significantly reduce the damage caused by an exploit and help organizations recover faster.
The Role of Cybersecurity Awareness in Preventing Exploitation
While technical defenses are critical, raising cybersecurity awareness among employees and stakeholders plays a vital role in preventing exploitation of the Citrix vulnerability in key sectors. Attackers often use phishing emails or social engineering tactics to gain initial access or escalate privileges. Educating staff about suspicious links, proper password hygiene, and reporting unusual activity can significantly reduce the chances of a successful breach. Training programs and regular reminders create a security-conscious culture that complements technological safeguards.
Will Citrix Vulnerabilities Keep Being Exploited?
While Citrix has taken steps to address known vulnerabilities, the threat landscape continues to evolve. The Citrix vulnerability exploited in key sectors serves as a reminder that attackers are constantly looking for new weaknesses.
Organizations must remain vigilant and proactive. Investing in cybersecurity, updating systems regularly, and adopting a security-first mindset are crucial for preventing future exploits. The battle between attackers and defenders is ongoing, but preparation and awareness can tip the scales in favor of security.
Summary Table
| Action | Description | Outcome |
|---|---|---|
| Apply Patches | Update Citrix with latest fixes | Fix vulnerabilities |
| Enable MFA | Add extra login verification | Block unauthorized access |
| Network Segmentation | Isolate critical systems | Limit attacker movement |
| Continuous Monitoring | Watch for unusual activity | Early threat detection |
| Security Audits | Regular system checks | Find weaknesses early |
| Staff Training | Educate on phishing and attacks | Reduce human error risks |
| Incident Response | Prepare team and plan | Faster breach handling |
| Use Detection Tools | Automated alerts and analysis | Quick response to threats |
| Upgrade Legacy Systems | Update or isolate old systems | Close hard-to-patch gaps |
| Strong Password Policies | Enforce complex, regular changes | Lower credential theft risk |
Protecting Key Sectors from Citrix Exploitation
The Citrix vulnerability exploited in key sectors has exposed significant risks to some of the most vital industries in the world. Healthcare, finance, and government have all felt the impact, underlining the importance of strong cybersecurity measures.
By understanding how this vulnerability works and taking swift action to patch and secure systems, organizations can protect themselves from costly breaches. Continuous monitoring, employee education, and strategic investments in security tools will help keep attackers at bay.
As remote work and digital transformation continue to shape the future, Citrix security must remain a top priority. Only through vigilance and collaboration can key sectors defend against this ongoing threat and ensure the safety of critical data and services.
Hoplon Infosec helps protect against the Citrix vulnerability through patch management, monitoring, and quick incident response. We also offer staff training to reduce risks.
Follow us on X (Twitter) and LinkedIn for more cybersecurity news and updates. Stay connected on YouTube, Facebook, and Instagram as well. At Hoplon Infosec, we’re committed to securing your digital world.