The Noodlophile Malware Campaign’s Growing Shadow
On a quiet Tuesday afternoon, an IT manager in Singapore opened what looked like a letter saying they had broken the law by copying someone else’s work. The email seemed authentic since it featured logos that looked professional and severe language about “illegal use of copyrighted material.” Within minutes, hackers got into his computer, and the Noodlophile malware campaign, as experts now call it, crept silently over his network. What seemed like a typical complaint turned out to be the beginning of one of the smartest global malware campaigns in the past few years.
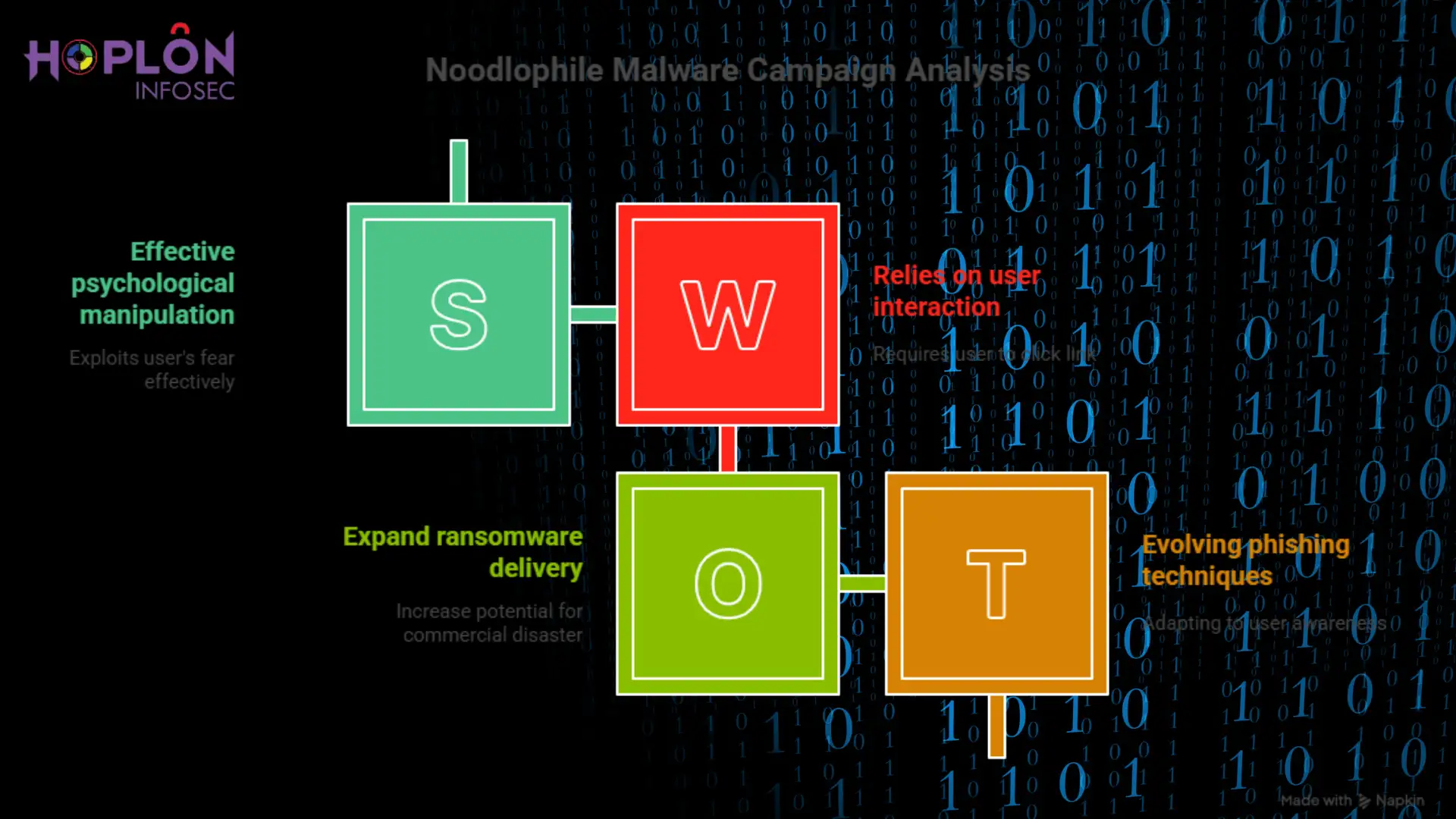
This isn’t just another virus that spreads over email. This ad is so disturbing because it uses both psychological manipulation and technical precision. It uses a bait that we all naturally fear: being accused of taking someone else’s work.
What Makes the Noodlophile Malware Different from Other Types
There are a lot of malware campaigns out there, but the Noodlophile outbreak is different because it employs both old-school phishing methods and novel techniques to stay hidden. A lot of phishing emails are badly written, with problems in spelling or strange layouts. This one, on the other hand, looks good. The contents are easy to read, the layout seems professional, and the fear factor is high.
Unlike most banking Trojans or ransomware droppers, Noodlophile doesn’t rush. It hides. Once it’s in, it quietly collects data and browser cookies and tracks login sessions. Instead of a burglar who breaks in and steals things, think of it as a practiced pickpocket who follows you about for weeks, looking for the right time to steal.
The Start of the Campaign: How It All Started
In late 2023, researchers detected the first sets of phishing complaints linked to takedown requests. This is how they found the initial wave of Noodlophile malware. At first, it didn’t appear like the magnitude was that big, since only a few people were affected in Asia. But in early 2024, reports of a coordinated operation began to appear in Europe and North America.
In one analysis, the security company Check Point warned that attackers “used the universal fear of legal threats” to lure people in. There was more to this than just a lot of spam emails. It looked like a planned, controlled, and focused effort, almost like a crime marketing campaign.
The Role of Phishing Lures in the Attack
If you’ve ever uploaded a video to YouTube or shared a picture online, you probably know how horrible it feels to get a copyright complaint. Hackers know how to use that fear. The phishing emails state that the victim’s information breaks intellectual property laws and then try to persuade them to “review the evidence.” That link is, of course, awful.
What makes it so powerful is the way it makes people feel. People don’t think about things; they only want to clarify their identity. It’s like being publicly accused; you click because you want to be safe.
How hackers get users to click
It’s interesting to think about the psychology behind this technique. These hackers don’t utilize obvious bait like “Win a free iPhone.” They instead play on people’s pride and reputation. A person who makes material doesn’t want to lose their channel. Someone who runs a small business is worried about being sued. These impulses are more powerful than logic.
Proofpoint completed a study that showed that phishing emails that threatened legal action garnered roughly twice as many clicks as ones that promised money. It reveals that people may be more afraid of ruining their reputation than of losing money.

How the malware works on a technical level
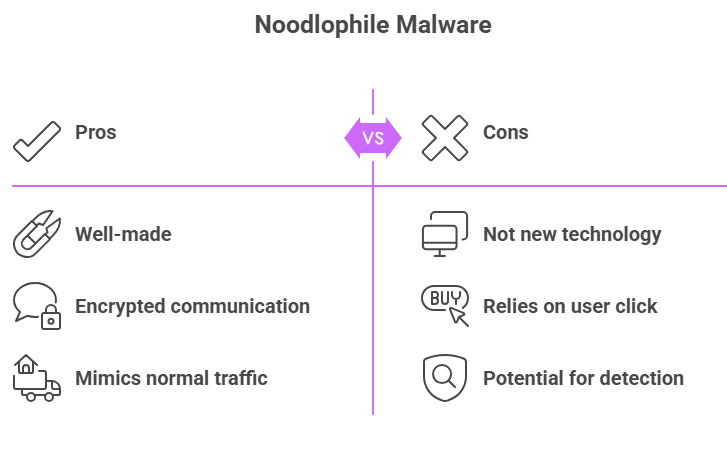
Noodlophile isn’t new technology, but it is well-made. When the victim clicks on the faulty link, the site sends a file that seems like a paper or a zipped file. After that, the virus downloads a loader that can get more modules depending on what the attackers want. This could be stealing passwords, hijacking sessions, or even getting remote access.
Researchers found that it uses encrypted communication with its command-and-control servers, which makes it harder for antivirus software to discover. It can even act like normal traffic, so network management won’t detect anything strange when they look at typical browsing.
Why the Campaign Is Getting Bigger All Over the World
Experts thought this was a joke that only happened in one place at first. But by the middle of 2024, there were reports of victims in the US, UK, India, and Australia. The company behind it is getting bigger, which suggests they are attempting new things and expanding into new sectors.
More global reach also implies that you can reach more people. The program is now aimed at content suppliers, law firms, marketing agencies, and even colleges and institutions. It goes after anyone who might be worried about breaking copyright.
Who Is Noodlophile Malware Most Likely to Attack?
YouTubers, digital publishers, and designers are the most obvious targets because they make a lot of stuff. But that’s not all. Even medium-sized businesses with a website that is open to the public can be caught. Hackers want to get into your email if you have contracts, invoice information, or client data there.
It’s intriguing that researchers also uncovered cases when NGOs and advocacy groups were affected. It doesn’t look like the hackers care. Anyone who quickly responds to a “copyright warning” is fair game.
Real-life examples that highlight the threat
BleepingComputer wrote about a tiny marketing company in Canada that opened a fake copyright email, which let hackers into their computers for weeks. The attackers discreetly grabbed customers’ login information and then sold it on dark web sites.
Another victim was a YouTuber from India. He couldn’t go into his account for days after falling for the scam. His channel was packed with bitcoin ads before he could get it back. These aren’t just numbers; they’re real people whose lives are being ruined by a carefully designed lie.
The Human Side of Falling for Phishing Scams
There is someone behind every headline about malware who is sitting at their computer and knows they have been tricked. It’s rude and even wrong. People who are upset often say something like, “I should have known better.”
But the truth is that even experts with a lot of expertise can mess up. A cybersecurity consultant who didn’t want to be named said that he almost clicked on one of these copyright emails because it looked just like the ones he gets for his clients. It only takes one second of doubt.
Connection Between Old Phishing Methods and This New Wave
Fear has been used as bait before. In the early 2000s, hackers sent a number of fake tax or bank letters. The Noodlophile virus campaign is a new version of that playbook, but with improved designs and stronger software.
The key thing that makes them different is how smart they are. Attackers today may utilize stolen data to make their phishing attacks more personal. They could take the name of your real business or video channel, which makes it much harder to prove it’s not real.

What Security Experts Are Saying About the Campaign
John Hammond, a security researcher at Huntress Labs, said it clearly: “These phishing campaigns are not random shots in the dark.” They are carefully constructed social traps that are supposed to terrify you.
Kaspersky specialists also warned that this may turn into a technique to transmit ransomware. If that happens, what appears like a small problem now could snowball into a big commercial disaster tomorrow.
Things you can do to keep the Noodlophile virus from getting to you
The good news is that you can keep yourself safe. First, never click on links in emails you didn’t ask for, especially if they threaten you with legal action. Instead, ask the platform directly (like YouTube, Facebook, or your hosting provider).
Second, show that you are who you say you are in more than one way. Hackers can still break into your account, but it’s a lot harder for them to do so. Last but not least, teach your workers and teams. A short meeting to promote awareness can stop someone from making a significant mistake. Learning is the best method to keep yourself safe in cybersecurity.
The Future of Malware Campaigns Like This
Campaigns like Noodlophile are likely to stick around in the future. In fact, they will definitely get smarter if they mix AI-generated text with deepfake logos and personal information. The next wave might not just say you broke the law; it could also be a job offer or a tax audit.
The essential thing is that our defenses and phishing assaults change at the same time. The battlefield is as much about the psyche as it is about technology. Hackers utilize fear, urgency, and curiosity to their advantage.
Last Thoughts: Why Being Aware Is the Best Defense
The Noodlophile malware campaign teaches us something very important: technology can’t protect us by itself. Firewalls and antivirus software can help, but the mind is the real front line.
Stop if you ever get an email that makes you scared. Breathe deeply. Check before you click. In the end, awareness isn’t just a defense; it’s the only thing that can stop even the most advanced attacks.
Follow us on X (Twitter) and LinkedIn for more cybersecurity news and updates. Stay connected on YouTube, Facebook, and Instagram as well. At Hoplon Infosec, we’re committed to securing your digital world.