Novel 5G attack bypassing base station
The Day I Found Out My Phone Wasn’t Alone ,I remember very clearly the morning my friend who works in mobile security called me. He sounded scared and thrilled at the same time. “Do you know how to use your 5G phone? Someone can get to the cell tower without ever touching it. I thought it was funny at first. That didn’t seem possible. But when he talked about the new 5G attack that goes around the base station, it really got to me. This was real, and it was happening all around us without anyone noticing.
Take a moment to think about it. Every time you check your bank account or look at Instagram, your device talks to towers and networks that you can’t see. These towers normally keep an eye on things. But now, hackers are finding ways to sneak around those measures without anyone knowing. It looked like something out of a spy movie, but it was real and it meant a lot to me.
5G: Quicker, Smarter, and More Dangerous
5G is awesome. When you can watch a movie without buffering, have video calls that make it feel like the other person is in the room, and have smart gadgets talk to one other without any hassles, it’s like living in the future. But it takes a lot of labor to make these improvements. Hackers like things that are hard to figure out.
The new 5G attack that gets past base stations takes advantage of slight issues with how devices connect to the network. There is no need for someone to touch a tower because it is not a physical hack. You installed an extremely high-tech lock on your front door, but the hacker discovers a method to get in through a small hole. This is what’s going on.

Why base stations aren’t enough anymore
Base stations have always been the most critical aspect of mobile networks. They keep an eye out for anything suspicious as they deliver your calls, messages, and internet data to the correct area. In the past, those who wanted to hack your network had to break into the tower. That made it hard and dangerous.
With this new plan, hackers can now fully avoid the tower. It’s like someone slipping into your house through a hidden side window while the guards at the front door are busy. Your phone thinks everything is alright, but a hacker could be snooping at your texts or other information in the background.
When Protocols Don’t Work for Us
The 5G protocols are what really confuse me. They are how devices connect to the internet and establish their identity. Hackers have figured out how to use small gaps in these restrictions to their advantage. A phone can think it’s connecting to a safe network, but it’s actually connecting to a system that has been modified.
Picture giving your ID to a hotel clerk who is sleepy and not paying attention. They check it and let you in without noticing the minor fake parts. That’s what the hacker is doing on the internet: tricking the network without leaving any clear clues.
The SIM Card’s Weak Point
We all have a lot of faith in our SIM cards. They carry keys, check devices, and are a big part of who we are on our phones. But these small cards aren’t perfect either. By modifying how subscriber identification verification works, hackers can get around the base station.
This is bad news for companies who need to be able to safely converse to each other over the phone. Someone who has hacked your SIM card could view your business emails or other private information. If you utilize it for personal reasons, everyone might suddenly view your messages, bank account, or pictures. The risk is small yet genuine.
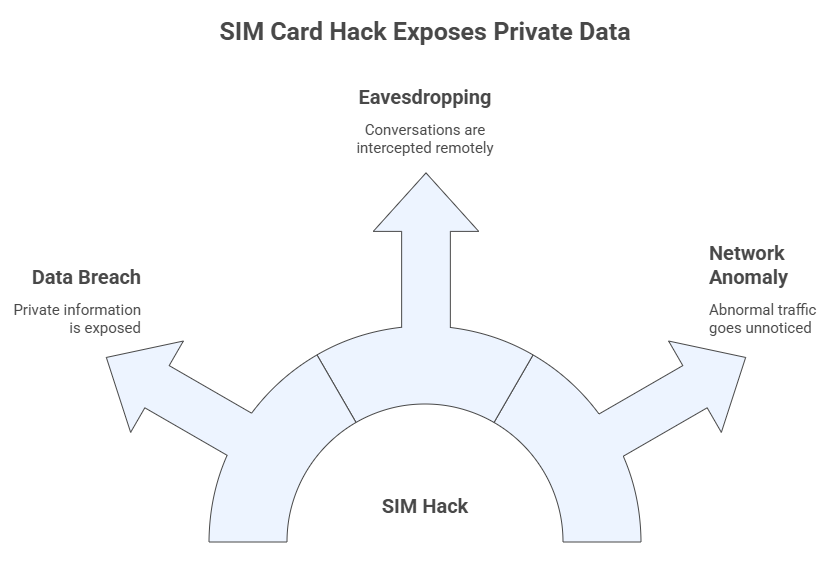
I spoke with a researcher who was looking at a lot of equipment from a distance. They could hear what people were saying without having to touch any of the towers. But the devices and network assumed everything was fine. In another case, a company didn’t identify abnormal patterns in its network traffic until weeks after workers accidentally connected to networks that had been hacked.
These stories show that this is not a threat that could happen in the future. We don’t notice it very often, but it’s happening right now. It’s a good idea to examine how safe your phone is.
What this strike really does
Finding devices that wish to connect to 5G is the first step in the attack. Hackers then modify messages during authentication to make devices think they are talking to actual infrastructure. People who have access can see, send, or even change information.
This is really bad because it’s sneaky. There aren’t any weird signals or towers that don’t belong there. Everything seems normal from the outside. This means that traditional protections don’t help cybersecurity teams very well. You need to look at how the device works on a much higher level to find the attack.
Why It’s Hard to Find
For decades, mobile networks have been fighting to defend their infrastructure. Firewalls, monitoring systems, and audits have all been used a lot. If you don’t use the base station, these methods don’t work as effectively. A hacker quietly disrupts the normal flow of the network.
Some businesses are already using AI to find problems. These systems don’t look for odd patterns at the tower level; instead, they seek for them at the device level. But it’s always a game of cat and mouse. If you’re not careful, every new feature in 5G could be a new hole.
What Happens in the Real World
People could have their money taken or their identity stolen, among other things. Companies are in a lot greater trouble. Imagine a hospital where patients can be watched over by 5G-enabled devices. A hacker could steal or manipulate data, which could put people’s lives in danger.
Small mistakes can have tremendous consequences. A leaked email, a confidential file that was viewed without permission, or IoT devices that were messed with might all cause major difficulties. People don’t usually realize the harm until it’s too late, and it might be really bad.
How to Stay Safe in Real Life
There should be more than one layer of security. You need strong encryption, better ways to check who you are, and regular software updates. Another important role is to pay attention to how electronics act in odd ways.
Users also need to be careful. Don’t connect to networks that seem weird, keep your gadgets up to date, and be on the lookout for strange behavior. Your awareness and attention are more important than technical measures.
What the government and corporations are doing
Finally, people in the field and the government are paying attention. There are now rules for using 5G safely, verifying users, and letting people know about problems. More and more people are sharing knowledge about threats in a way that everyone can use.
This means that the threat is hard to deal with, but it can be stopped. Operators, manufacturers, and regulators may work together to design defenses that block these threats before they can do any harm.
In the future
Security needs to be built in from the outset as 5G spreads and 6G gets closer. In the future, networks will need security at the protocol level, the ability to find problems in real time, and constant updates of threat intelligence. Hackers won’t wait for technology to catch up, so people and businesses need to stay on top of things.
Action Table
| Aspect | Details |
|---|---|
| Attack Type | Novel 5G attack bypassing base station |
| Target | Mobile devices, SIM cards, and 5G protocols |
| Method | Exploits authentication and signaling protocol flaws without touching base stations |
| Detection Difficulty | Very high; traditional base station monitoring often fails |
| Impact on Individuals | Identity theft, financial fraud, unauthorized access to personal data |
| Impact on Enterprises | Breach of confidential communications, intellectual property theft, IoT device compromise |
| Real-Life Example | Researchers intercepted device communications remotely while networks appeared normal |
| Mitigation | Strong encryption, improved authentication, device monitoring, software updates |
| Industry Response | Regulatory guidelines, threat intelligence sharing, enhanced network security protocols |
| Key Insight | Awareness, vigilance, and proactive security are as important as technical safeguards |
Final Thoughts
The new 5G attack that skips the base station is more than just a problem with technology. It reminds us that only the individuals who use technology can keep it safe. Stay informed, pay attention, and do something.
Remember that there are a lot of doors in the digital world that you can’t see. Hackers are always trying to get in, so we have to keep those doors closed. Sometimes, the best way to stay safe is to be curious, careful, and a little skeptical.
Follow us on X (Twitter) and LinkedIn for more cybersecurity news and updates. Stay connected on YouTube, Facebook, and Instagram as well. At Hoplon Infosec, we’re committed to securing your digital world.