UDisks daemon local privilege escalation CVE-2025-6019
It started during a routine laptop tune-up. An admin mounted a disk image to grab a few configuration files, nothing fancy. A minute later, an endpoint alert flared up, then went silent. No malware, no network beacon, just a simple mount that changed privileges in ways no one expected.
That moment captures why storage plumbing deserves respect. The tools that make removable drives and disk images just work can also blur the line between a regular user and root. If you care about least privilege, you care about how mounts happen, which options get applied, and which services sit in the middle. Security teams now label it as the UDisks daemon vulnerability in policy notes.
What UDisks does in plain language
UDisks is the service that listens for storage-related requests and helps the desktop mount drives, format volumes, and expose devices over D-Bus. It leans on helpers like libblockdev and coordinates with polkit to decide who is allowed to do what. When you see the phrase “UDisks daemon local privilege escalation CVE-2025-6019,” think about that decision path going wrong for very specific calls.
Put simply, UDisks is the friendly face of storage management on many Linux desktops and servers with a graphical stack. It abstracts messy kernel details. Most days, that is a gift. On bad days, one trusted abstraction can open a path to unintended authority. When people discuss the UDisks daemon vulnerability, they are usually describing how that friendly layer handled trust decisions under pressure.
How the libblockdev link creates a risky path
libblockdev handles low-level operations, and UDisks invokes it for tasks like creating or mounting loop devices. The risky part shows up when default assumptions collide with policy.
The heart of the UDisks daemon local privilege escalation CVE-2025-6019 sits at the junction where UDisks asks libblockdev to perform an action and the policy engine decides it is harmless for an active local user.
If a helper expects protective mount flags every time, and a calling service assumes the helper always sets them, you get a blind spot. That sort of misalignment is common in complex stacks. It rarely matters until an attacker strings the pieces together in the right order.
The chain from allow_active to root
Polkit has a concept called allow_active. It gives extra permissions to a person seated at the machine or logged in through the console. On its own, that model is useful for ease of use. Chained in the wrong way, it can be a stepping stone. The chain for UDisks daemon local privilege escalation CVE-2025-6019 often starts with an attacker reaching allow_active, then calling storage actions that end with root-level effects.
The best way to picture this is a set of doors in a hallway. The first door is labeled convenience. The second door is labeled “abstraction.” If both are open, the last door labeled “root” sometimes swings on the same hinge.
Where CVE-2025-6019 fits in
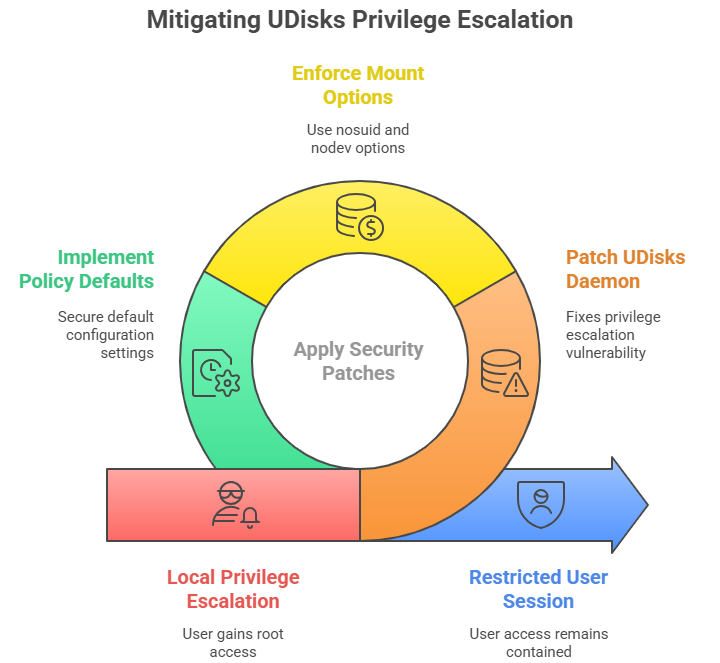
This specific issue is logged and tracked so defenders can triage and vendors can patch. In short, UDisks daemon local privilege escalation CVE-2025-6019 describes how an allow_active user can trigger operations that result in elevated privileges through UDisks and libblockdev. The details vary slightly by distribution, but the idea is consistent.
The practical impact is straightforward. A user who should be fenced in to their own session can end up with full control. That is why patch notes emphasize mount options like nosuid and nodev, and why policy defaults matter so much. The UDisks daemon vulnerability is a useful shorthand for the same risk picture.
Related CVEs you should know
There is a sibling vulnerability you will see referenced in the same breath. CVE-2025-6018 concerns PAM configuration and how a clever user can become allow_active on some systems. Paired with the UDisks daemon local privilege escalation CVE-2025-6019, it becomes a tidy two-step. More recently, CVE-2025-8067 points at an out-of-bounds read in UDisks loop device handling that can crash the daemon and may aid escalation under the right conditions.
Treat these as parts of one landscape. One flaw helps a user reach the stage. Another flaw hands them props. The combination is what makes defenders uneasy. Ubuntu and Red Hat both issued advisories that explain the scope and fixes in plain terms.
Who is affected across distros?
The short version is this. Many mainstream distributions ship UDisks by default, especially on desktop profiles. Ubuntu, Debian, Fedora, and openSUSE all acknowledged the risk and released updates. The exact exposure depends on defaults and how your policy rules were configured. The mitigation guidance around UDisks daemon local privilege escalation CVE-2025-6019 travels consistently across those vendors.
If you manage mixed fleets, do not assume parity. A laptop used by a developer with frequent disk image mounts looks different from a thin client. Inventory the places where users mount images, work with removable media, or run virtual machines that use loop devices.
Realistic attack paths and limitations
This is not a remote exploit in the classic sense. An attacker needs a foothold as a local user. That said, lateral movement often yields local shells. Kiosk setups and lab machines are common targets. With the UDisks daemon local privilege escalation CVE-2025-6019, the path from a restricted shell to root can be surprisingly short if patches are missing.
Real attack chains look ordinary. Someone plugs in a USB drive. Someone mounts a test image. A service account interacts with storage to prep a container. In each case, the action is legitimate. The difference is who ends up holding the keys after it completes.
Signals defenders can watch for
Defenders should watch for unusual loop device creation, odd mount options missing nosuid or nodev, and net new polkit decisions tied to storage actions. Correlate those with logins that switch between console and remote sessions. In environments where the UDisks daemon local privilege escalation CVE-2025-6019 is not yet patched, these are the events that tell a story early.
On EDR tooling, add simple detections for udisksctl calls that create or set up loop devices in user sessions. Even better, alert when a user who is not part of any storage groups executes those actions. It is not fancy, but it pays dividends.
Practical mitigation and patches
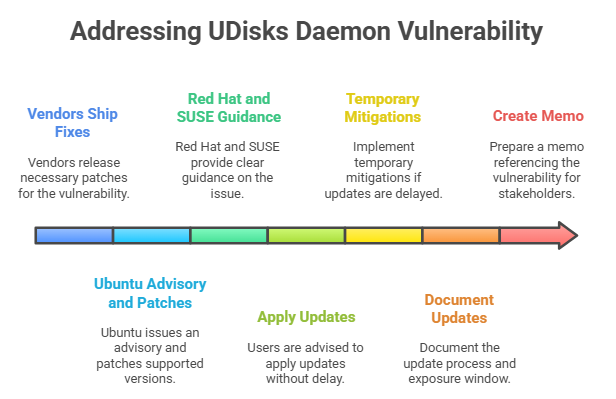
The good news is vendors shipped fixes quickly. Ubuntu assigned an advisory and patched supported versions. Red Hat and SUSE tracked the issue with clear guidance. Apply those updates without delay. If your change window is tight, use temporary mitigations like restricting D-Bus methods for untrusted users and tightening polkit rules that touch storage. Many advisories reference the mechanics behind UDisks daemon local privilege escalation CVE-2025-6019 so you can test effectively.
If you operate in a regulated environment, document the update, the exposure window, and any compensating controls. Auditors will ask. Your future self will thank you. Keep a short memo that references the UDisks daemon vulnerability by name so stakeholders connect the dots later.
Hardening Polkit and PAM safely
Hardening here is about sensible defaults. Ensure mount operations triggered through UDisks always inherit nosuid and nodev unless a specific admin policy overrides them for a rare case. Treat any path to allow_active as a potential privilege boundary. When you do, UDisks daemon local privilege escalation CVE-2025-6019 loses most of its bite.
Review the PAM order for modules like pam_env and pam_systemd, and confirm your polkit rules do not broaden allow_active beyond what the desktop experience truly needs. The smoother the user path, the easier it is to overshoot safety. Balance matters.
Testing your fleet without breaking things
You can test in a staging lab with simple scenarios. Create a standard user, simulate console login, and attempt the same actions an attacker would try to abuse. Record which calls succeed before and after updates. Sprinkle in a few oddly crafted images to make sure edge cases do not surprise you. Treat each successful reproduction as a checklist item that validates your coverage against UDisks daemon local privilege escalation CVE-2025-6019.
Remember to involve help desk staff in these drills. They see the odd errors first. If they learn what a risky mount looks like, they will escalate faster. That reduces dwell time, which is the whole game.
Lessons for desktop Linux in enterprises
Enterprises embraced Linux on developer workstations for good reasons. Package managers, containers, and rich tooling make teams productive. Storage services are the glue that keeps that experience moving. The lesson from UDisks daemon local privilege escalation CVE-2025-6019 is not to retreat.
The lesson is to pin down where user convenience relies on silent privilege and to make those edges explicit. Inside security reviews, name the UDisks daemon vulnerability plainly so it does not get lost among kernel bugs and container oddities.
When you write policy exceptions, treat them like you would sudoers entries. Name the reason. Set an expiry date. Review them twice a year. That habit prevents a dozen little shortcuts from turning into a silent escalation path.
What to tell developers and help desks
Developers should review scripts that mount images for testing, CI jobs, and container builds. If a job fails after a patch, fix the job rather than relaxing policy. Communicate that UDisks daemon local privilege escalation CVE-2025-6019 is not theoretical. It is a practical case of storage functions granting authority outside their lane. Speaking clearly about the UDisks daemon vulnerability helps teams prioritize the right fixes without fear or drama.
For help desks, build a short runbook. If a user reports odd permission changes after mounting a file, capture logs from polkit, udisksd, and the kernel ring buffer. It is fine to be a little nosy when the signals line up.
A short checklist you can run today
Update every host that ships UDisks. Audit policy rules that touch storage. Verify nosuid and nodev appear on mounts that originate from user sessions. Add simple detections for loop device creation. Capture before and after results for a few test images. If time is tight, prioritize systems where developers and admins work with disk images. That is where the UDisks daemon local privilege escalation CVE-2025-6019 is most likely to bite.
Close with a realistic step. Block untrusted users from calling sensitive D-Bus methods until the patches land. It buys you time without breaking day-to-day work. Small guardrails make a big difference.
Q1: What is the UDisks daemon local privilege escalation CVE-2025-6019?
A: It’s a Linux vulnerability where a local user can gain elevated privileges via UDisks and libblockdev due to misconfigured policies.
Q2: Which Linux distributions are affected?
A: Ubuntu, Debian, Fedora, openSUSE, and other mainstream distributions with UDisks installed by default are affected.
Q3: How can I protect my systems from this vulnerability?
A: Apply vendor patches immediately, enforce nosuid/nodev mount options, and tighten polkit rules to limit allow_active privileges.
The Linux UDisks Daemon flaw highlights the need for strong protection at the device level. Hoplon Infosec’s Endpoint Security services help block privilege escalation and safeguard systems from similar attacks.
Follow us on X (Twitter) and LinkedIn for more cybersecurity news and updates. Stay connected on YouTube, Facebook, and Instagram as well. At Hoplon Infosec, we’re committed to securing your digital world.



