Window BitLocker vulnerability
If you thought full disk encryption was a silver bullet, the recent Window BitLocker vulnerability news should make you pause. BitLocker has been the backbone of how millions protect data on Windows laptops and servers, and any flaw that touches that chain can quickly become a crisis for an organization.
I remember a small company I once advised that treated BitLocker like a checkbox. They had recovery keys piled in a shared spreadsheet and assumed physical theft was the only real risk. When researchers started publishing attacks that moved beyond theft and into clever boot environment tricks, the team finally sat up and rewired their thinking. That wake up call is exactly why a Window BitLocker vulnerability, even one that needs local access, cannot be shrugged off.
What is BitLocker and why disk encryption is not optional
BitLocker is Microsoft’s built in full disk encryption for Windows. It ties cryptographic keys to the platform, often involving the Trusted Platform Module, or TPM, and optionally a PIN or USB key at pre boot. The idea is simple: protect data at rest so that if a device falls into the wrong hands, the disk contents remain unreadable.
But disk encryption also introduces complexity. Keys, recovery mechanisms, and the boot path are all new attack surfaces. When a Window BitLocker vulnerability appears, it often targets one of those surfaces. That means attackers do not always need to break strong cryptography to win, they can instead exploit weak spots in how Windows loads, stores, or recovers encrypted volumes.
A quick timeline of the recent Window BitLocker vulnerability disclosures
Over the last several months security teams and researchers have disclosed multiple issues that impact BitLocker and the Windows pre boot environment. Some of these are traditional memory bugs that allow privilege escalation, while others let attackers bypass validation steps and extract keys from memory during recovery processes.
Microsoft and third party databases have cataloged a string of CVE entries tied to BitLocker behavior, and multiple write ups from research groups paint a picture of a larger pattern: a mix of software bugs and design gaps that together allow serious outcomes.
How an attacker can use BitLocker bugs to elevate privileges
At a high level, an attacker who can run code on a machine or who has physical access can sometimes chain a BitLocker flaw into a local privilege escalation. For example, a memory corruption in the BitLocker component could let an authenticated low privilege user execute code as SYSTEM. That means a user account that normally cannot read other users’ files might become an all powerful local admin.
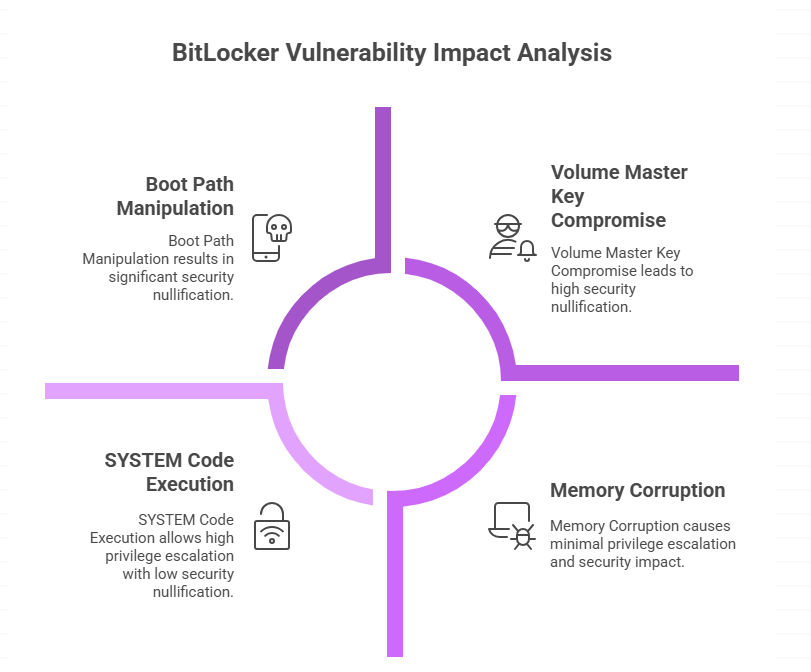
Worse, some vulnerabilities let an attacker get at keys or manipulate the boot path so that the protection BitLocker offers is nullified. Even if the cryptography is strong, the practical security crumbles if an attacker can coax Windows into handing over the Volume Master Key.
Key CVEs and what each one means for practitioners
A good starting point for defenders is to track specific CVEs and their mitigations. For example, a recently cataloged elevation of privilege entry describes a use after free in a BitLocker component that allows local privilege escalation. That kind of bug is dangerous because it often requires only low privileges and user interaction to escalate.
Other CVEs describe protection mechanism failures that enable bypasses when an attacker has physical access or can manipulate the recovery environment. Those entries show that the threat model for disk encryption must include both software flaws and operational mistakes such as unsecured recovery keys.
Real world attack chains: Bitpixie and boot environment tricks
Some of the most vivid demos are the attack chains researchers call things like Bitpixie. These techniques focus on the recovery and network boot processes, where Windows sometimes loads tools or images that can leave key material in memory. If an attacker can trigger a recovery process and then run code or inspect memory, they may extract the VMK and decrypt the drive in minutes.
I have seen demos where a skilled red teamer assembles a multi step sequence, starting with firmware configuration and ending with an extracted VMK. That is not a Hollywood level impossibility, it is a measured sequence that combines several weaknesses in the boot flow. Reading the write ups makes it clear this is a practical threat to laptops left unattended or data center machines with weak physical controls.
Technical deep dive: use after free and memory corruption in BitLocker
Memory vulnerabilities such as use after free are classic but still nasty. In the BitLocker context the problem typically looks like this: a component frees a structure but keeps a reference to it, which can later be reused by an attacker controlled allocation. When the component accesses that reclaimed memory it may be tricked into executing attacker supplied data.
That may sound arcane, but the practical effect is straightforward. An attacker can cause out of bound behavior, run crafted code paths, and pivot from a regular user to a SYSTEM account. Those kinds of flaws are why modern memory safety techniques and careful code review matter in encryption components as much as anywhere else.
Physical attacks, WinRE manipulation, and recovery key risks
Not every threat requires a memory bug. Some vulnerabilities focus on how the Windows Recovery Environment is invoked and how it handles images or Boot Configuration Data. If an attacker can alter the recovery image or inject a crafted WIM, they can subvert validation checks and make the system reveal secrets.
This class of attack intersects with operational hygiene. Recovery keys placed in accessible locations, recovery workflows that allow unattended recovery, and weak physical controls on devices all widen the risk surface. The takeaway is blunt: a Window BitLocker vulnerability can be technical, operational, or both.
Who is affected: home users, enterprises, and regulators
Everyone who relies on BitLocker should pay attention. Home users might assume they are safe because their threat model does not include advanced attackers, but targeted attackers often find home machines that are easier to reach. Enterprises face higher stakes: regulatory obligations, customer data, and compliance attestations can all be jeopardized by a successful exploitation.
From a legal and compliance point of view, a breach that stems from a Window BitLocker vulnerability may trigger breach notification laws, contractual penalties, and loss of trust. That is why security leads should factor in both the technical mitigation and the communication plan.
How to detect signs of a BitLocker compromise or exploitation
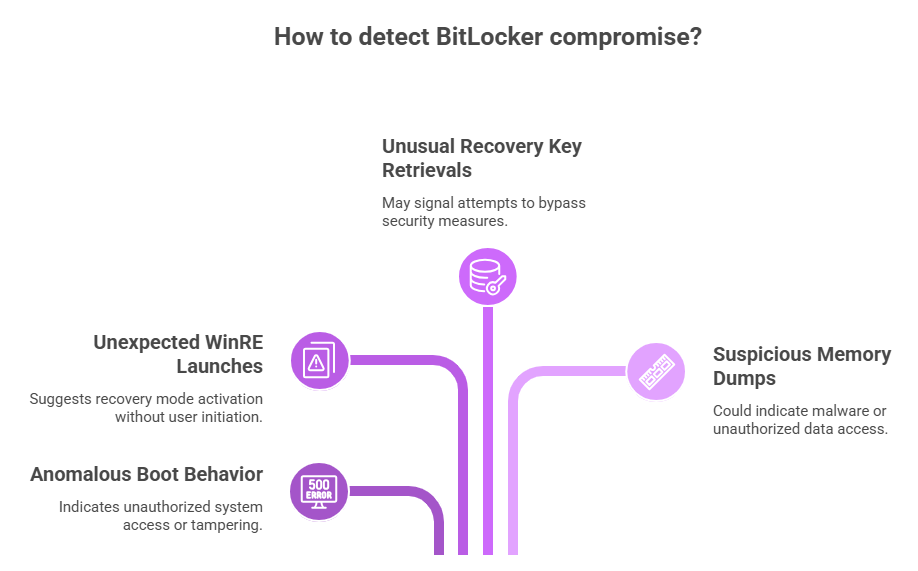
Detecting these issues can be tricky. Look for anomalous boot behavior, unexpected WinRE launches, and local processes trying to access BitLocker management interfaces. Audit logs that show unusual recovery key retrievals or repeated recovery attempts are red flags.
Also watch for unexpected privilege escalations and suspicious memory dumps. Endpoint detection tools that monitor process creation, unusual calls into kernel components, and changes to boot configuration can help. While detection is imperfect, layered logging and rapid analysis shorten the window attackers have to complete complex chains.
Immediate mitigations and Microsoft patch guidance
When Microsoft publishes patches or mitigations for a Window BitLocker vulnerability, apply them as quickly as your change control allows. Where patches are not yet available, follow published Microsoft guidance such as limiting local administrator access, forcing pre boot authentication with a PIN, and securing recovery key storage.
In many recent cases Microsoft and vendors provided step by step guidance and mitigations that reduce the attack surface until fixes are rolled out. Applying those mitigations is not glamorous, but in my experience the companies that prioritize them are the ones that avoid painful incident responses.
Long term hardening: TPM, pre boot authentication, and policy choices
Long term, think about hardening policies. Require TPM plus PIN for laptops that leave the building. Avoid storing recovery keys in shared documents. Use hardware rooted keys where possible and enforce strong group policies for BitLocker configuration.
There are trade offs. Requiring PINs can increase support calls, and stricter policies may slow down some users. But over time these choices pay off because they remove easy exploitation paths an attacker might rely on when exploiting a Window BitLocker vulnerability.
A short playbook for security teams and incident response
Build a simple playbook now. First, identify devices with BitLocker enabled and catalog where recovery keys are stored. Second, ensure patch windows are short for high risk CVEs. Third, run tabletop exercises simulating a local privilege escalation that leads to data exposure.
Finally, if an incident is suspected, capture volatile memory, preserve logs, and involve forensics early. These steps seem obvious, yet they are often missed in the heat of a real incident. Having a plan for a Window BitLocker vulnerability gives your team a head start.
Trade offs, usability, and the human part of disk encryption
People matter. I have seen security policies that look great on paper and then fail because no one trained the help desk. If users are forced into awkward workflows they will find workarounds that create new risks, like copying keys to USB sticks or emailing recovery keys to themselves.
Striking a balance between security and usability is an art. Make secure defaults easy, invest in good onboarding, and put clear recovery procedures in place. That reduces the chance that a Window BitLocker vulnerability becomes a catastrophic event simply because humans found an easier path.
what to do tomorrow and lessons for the future
If you take one thing away, make it this: treat disk encryption as an evolving risk, not a set and forget box. Patch when Microsoft releases updates, tighten pre boot authentication, secure recovery key storage, and rehearse responses. Small changes now avoid big headaches later.
Stay curious, read vendor advisories, and fold fresh intelligence into your patch and configuration cycles. The Window BitLocker vulnerability stories of the last months are a reminder that even foundational protections need continual attention. Do the basics well, and you will make exploitation much harder for anyone who tries to turn a disk encryption feature into an attack path.
Hoplon Infosec’s Endpoint Security services help protect devices from exploits like the Window BitLocker vulnerability, keeping your data safe.
Follow us on X (Twitter) and LinkedIn for more cybersecurity news and updates. Stay connected on YouTube, Facebook, and Instagram as well. At Hoplon Infosec, we’re committed to securing your digital world.



