Scattered Spider financial sector attack
When a name that used to dominate security bulletins shows up again, teams pay attention. The report of a Scattered Spider financial sector attack landed in inboxes and on SOC dashboards, pulling people away from routine tasks and back into triage mode. For many security leaders it felt less like a surprise and more like a test of whether lessons from past breaches had truly stuck.
Who is Scattered Spider?
Scattered Spider rose to notice after a string of incidents where persuasion mattered more than fancy exploits. The collective earned a reputation for calling help desks, mimicking employees, and coaxing password resets out of support teams. That focus on the human element made them both unusual and frighteningly effective for organizations that treated identity as handled rather than monitored.
A short recent timeline of activity and targets
In 2025 the pattern shifted. What once focused heavily on retail and hospitality broadened into financial services and insurance. Analysts flagged a series of ticket-themed phishing domains and credential harvesting pages, a sign that someone had done the legwork to target support channels and trusted vendor relationships. These moves were slow and deliberate, not noisy smash and grabs, which changed how defenders needed to hunt and respond.
How they gain access: social engineering to the fore
The core method is patient study of people and process. Operators research public profiles, learn support scripts, and call with a convincing tone. They target self-service password flows and impersonate administrators. A well-executed chain of calls and emails can reset multi-factor protections and hand an attacker roles that are hard to detect later. Because the effort is conversational, it slips past controls that hope to stop malware instead of deception.
Why financial firms are attractive to them
Financial firms hold money and credential-rich systems. That combination is high value for an intruder who can monetize access immediately or sell it to a buyer who will. A breach in a payment processor or insurer can expose accounts, confidential records, and vendor links that extend the damage across the supply chain. That potential to multiply returns makes the financial sector a logical place for a focused campaign.
Tactics and techniques observed in 2025
Reports from vendors and responders show a blend of phishing frameworks, credential harvesting, SIM swap attempts, and vishing. The operators chain small wins into larger compromises by abusing help desk workflows and service accounts. They try to access cloud stores and data repositories, hunting for Snowflake, AWS buckets, or other high-value targets where exfiltrated material can be monetized or used for leverage.
Cloud and identity as the new battleground
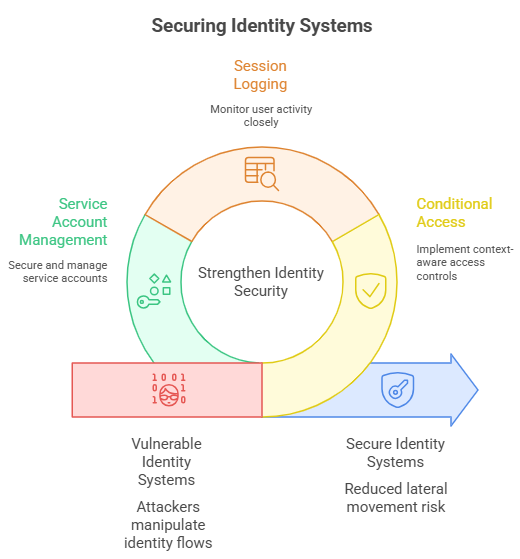
Identity systems are the key battlefield now. When an attacker manipulates an identity flow to add a global admin or export credentials, they can move laterally without touching the old kinds of malware footprints defenders look for. That means conditional access, session logging, and careful service account management are far more important than they used to be. Detection must follow identity events as much as it follows file changes.
Ransomware partnerships and the RaaS echo
This group often focuses on access and reconnaissance, then hands the environment to affiliates that deploy encryption or extortion tactics. That partnership model makes operations more scalable for the bad actors and more complex for defenders. Breaking the access pipeline, by which one crew sells or gives entry to another, reduces the multiplier effect of a single compromise.
Real-world impact on banks, insurers, and fintechs
When a critical account or service goes down, the result is immediate. Payment flows can stall, customer portals break, and regulators raise urgent questions. Smaller institutions feel the pressure most, where remediation costs, breach notifications, and reputational harm can outweigh the company’s capacity to recover. Consumers can be affected by slow account access, fraud, or exposure of personal details.
Why the “retirement” announcements may be a smokescreen
A number of criminal collectives recently announced they were stepping away. Public posts like those can be sincere for a few members, but they can also be distractions. Analysts noted ongoing domain registrations and credential harvesting activity even after the retirement claims. That mismatch suggests public statements were at best partial and at worst a deliberate misdirection to slow investigations.
Detection and response: immediate checks for defenders
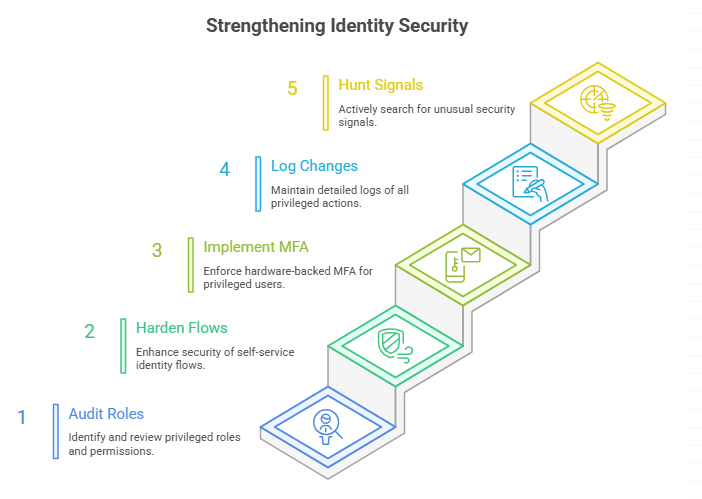
Start with identity hygiene. Audit who can perform password resets and which accounts have global admin roles. Harden self-service flows on identity providers, require hardware-backed MFA for privileged personnel, and log every privileged change. Hunt specifically for unusual Azure AD resets, new delegated roles, and access from unusual geographies or machines tied to help desk activity. Those signals are where this kind of campaign shows up first.
A mitigation playbook: immediate containment steps
If you suspect exposure, rotate or freeze the affected credentials right away and preserve logs for forensic analysis. Isolate implicated service accounts and consider temporarily restricting vendor and contractor sessions until you confirm they are clean. Notify your incident response partner quickly, and be transparent with affected customers while you gather facts. Fast containment lowers the chance of a broader ramp-up.
Long-term posture shifts that actually help
Invest in just-in-time access, reduce standing privileges, and require hardware-based authentication for help desk personnel. Regularly run red team and social engineering exercises and bake the lessons into training and process changes. Don’t treat this as a one-off project. Adopting a sustained identity-centric approach over years shrinks the attack surface social engineers love.
The role of information sharing and sector teams
When one institution sees a ticket-themed phishing domain and shares it, others can block and hunt for the same pattern. Sector groups and ISAC advisories shorten the window attackers exploit new lures. Those community feeds speed detection for smaller firms that lack large threat intelligence teams, and they make collective defense something practical rather than theoretical.
Legal and insurance consequences to anticipate
Regulators often require timely notifications. For cross-border firms, coordination between multiple authorities can be complicated and costly. Cyber insurance can help, but policies differ widely and may exclude certain social engineering failures or require documented preventative controls. Boards should review policy language and response plans now to avoid surprises later.
What customers should do now
If you are a customer of a potentially affected firm, change reused passwords and enroll in offered monitoring services. Use unique credentials and hardware- or app-based authentication where possible. Treat unexpected calls or messages asking you to confirm codes or reset passwords as suspect, and always verify via official channels.
Lessons learned and practical advice for teams
Attackers hunt the weakest link in people, processes, and technology. Prioritize identity, harden vendor access, and treat help desks as critical security assets. Make small, repeatable changes to the process and continue training; those compound into real reductions in social engineering success rates.
Q1: Who is Scattered Spider, and why are they targeting the financial sector?
A: Scattered Spider is a cybercriminal group known for social engineering and identity-based attacks. In 2025, they shifted focus to the financial sector because banks, insurers, and fintech firms hold valuable data and direct access to money, making them highly profitable targets.
Q2: How do Scattered Spider hackers typically gain access to systems?
A: They often use phishing, vishing, and help desk impersonation to trick employees into handing over credentials. Once inside, they exploit identity systems, escalate privileges, and sometimes partner with ransomware groups to maximize their impact.
Q3: What can financial institutions do to protect against Scattered Spider attacks?
A: Strong identity security is the key defense. Firms should implement hardware-backed multi-factor authentication, restrict help desk privileges, monitor for unusual password resets, and share threat intelligence within sector groups to detect attacks earlier.
Closing takeaways and actions to run today
The Scattered Spider financial sector attack wave reminds us that adversaries will change names and tactics, but they keep seeking value. For security leaders the steady, boring work of identity hygiene, logging, and honest tabletop practice is what reduces risk. Start with a focused audit of help desk privileges, lock down self-service password flows, and share indicators with peers. Those steps turn an alarming headline into a manageable incident.
Deep and Dark Web Monitoring from Hoplon Infosec helps financial companies stay one step ahead of threats like the Scattered Spider attack on the financial sector. They find exposed passwords, leaked information, and new phishing campaigns before they become full-blown breaches. Hoplon Infosec strengthens defenses and speeds up response times when used with Endpoint Security and Web Application Security Testing. This keeps sensitive data and customer trust safe.
Follow us on X (Twitter) and LinkedIn for more cybersecurity news and updates. Stay connected on YouTube, Facebook, and Instagram as well. At Hoplon Infosec, we’re committed to securing your digital world.




