Blockchain for Cybersecurity
Picture a world where logs can’t be deleted, you can prove your identity without a central password vault, and whispers in the supply chain turn into a clear recorded conversation. When engineers and security teams talk about blockchain for cybersecurity, they are talking about that promise. It sounds dramatic, almost like a dream come true, but some parts of it are already being used by companies that want to stop the same old tricks that keep bothering IT teams.
The idea is simple but very strong. You don’t put all your trust in one central database that can be changed or broken. Instead, you spread trust across many people and use cryptography to make sure records are honest. The result isn’t perfect, but it changes the rules of the game in ways that attackers have to adapt to and defenders can take advantage of.
A quick introduction to what blockchain adds to security
The technology is basically a shared ledger. Cryptographic hashing groups, links, and protects records. That means that every new entry points to what came before it, making it easy to see if someone has changed something in the past. This is a powerful tool for defenders because it makes it harder for stealthy changes to happen.
But just the idea of a ledger isn’t enough. To be truly safe, a system needs to be carefully designed, have clear threat models, and have controls over who can read or write data. Instead of treating blockchain like a magic bullet, developers often use it with other security tools.
Immutable ledgers and data integrity
One of the first things you hear is that records can’t be changed. When logs, certificates, or transaction stamps are linked to a distributed ledger, it is easy to see when they are changed later. That speeds up forensic work and gives auditors peace of mind that the evidence hasn’t been quietly deleted.
This unchangingness isn’t magic. It depends on how the network is set up and how the ledger is anchored. A public ledger and an enterprise-permissioned ledger work in different ways, and each has its own pros and cons. Still, immutability gives defenders a permanent record to use as a basis for their detection and response processes.
Identity and authentication that aren’t centralized
Passwords and systems that let you sign in once are common places where things go wrong. With decentralized identity, credentials are given out and checked without a central database that stores everyone’s keys. Users or devices can show cryptographic proofs that are linked to an identity. This makes big credential leaks less valuable.
This is not just a theory. Studies and tests have shown that identity frameworks based on blockchain can help control access and make audits easier. To protect privacy, careful design stops storing sensitive personal data directly on the chain and instead keeps pointers or hashed claims.
Audit trails that can’t be tampered with for incident response
Think about a time when a privileged account moved sideways. If every important action has a timestamp that can’t be changed and a chain of custody that can be checked, investigators can get from guesswork to evidence faster. That makes it easier to understand and cuts down on costly finger-pointing.
These trails can also be used by operational teams to automate finding the root cause. When log integrity is high, both machine tools and people can trust the data that is behind them more.
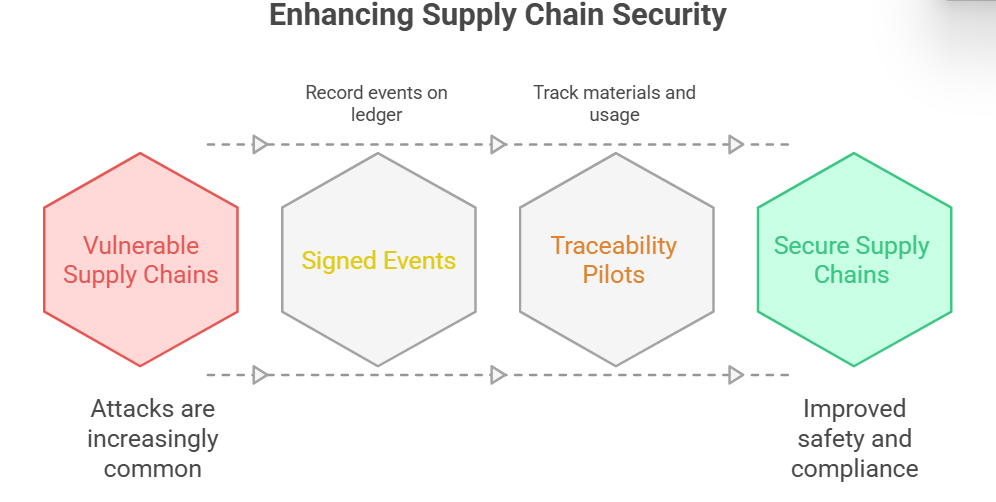
Safe supply chain and tracking of where things come from
Supply chain attacks are now a common weapon for smart enemies. When manufacturers, shippers, and retailers put signed events on a shared ledger, it’s easier to follow parts and software through all the steps of making and shipping them.
Automakers and logistics companies, for example, have run tests to find out where materials come from and how long they have been in use. Those pilots show how traceability can help find tampering or false claims, which makes both safety and compliance better.
Smart contracts and security controls that run on their own
Smart contracts let rules run on their own when certain conditions are met. This can cut down on the number of manual steps in security workflows. For example, on-chain checks could be used to make sure that policies are met before a credential is valid, which would keep the issuance of certificates in check.
Automation makes things faster and less likely to go wrong, but it also makes things go wrong in new ways. A bad decision can be enforced at machine speed by a buggy contract or an automated rule that is too broad. Before relying on hands-off enforcement, testing and staged rollouts are necessary.
Keys and hashing are the building blocks of cryptography.
Basic cryptography gives the whole idea its strength. Hash functions make short fingerprints of data. With public and private keys, you can sign and verify without giving away secrets. When you put them together, you get a ledger where each block is linked to the one before it by a cryptographic proof.
Those primitives are strong, but managing keys is still a problem. The security fails if private keys are lost or stolen. Good businesses spend as much on protecting their hardware and key lifecycle as they do on the ledger software itself.
Consensus mechanisms and the security trade-offs they make
What a network thinks is the canonical ledger is important. Proof of work, proof of stake, and other consensus algorithms all find a balance between speed, cost, and resistance to manipulation. For enterprise security projects, permissioned consensus methods can be selected that emphasize speed and governance rather than open participation.
If you choose the wrong consensus model, it could make the system useless or make it easier for attackers to get in. The consensus mechanism must be appropriate for the threat model and operational limitations.
Permissioned and public networks: which one is best for what?
A public network is very open and strong, but it can also be hard to keep private and follow the rules. A permissioned network lets organizations choose who can join, which gives them more control and compliance options. A lot of security use cases work better on private, permissioned ledgers where access and governance are clear.
That choice has an effect on performance, where data is stored, and how trust is built. There is no one size fits all. Companies often use a mix of methods, such as keeping sensitive proof records private and making non-sensitive digests public.
Combining blockchain with PKI and zero trust
Blockchain doesn’t replace zero trust; it works with it. While the zero trust controls handle enforcement, you can use the ledger as a source of truth for device states, certificates, or attestation results. In this setup, the blockchain gives access managers a way to check the context before giving out privileges.
You can also connect to public key infrastructure. For instance, verifiable ledger entries can make certificate transparency and certificate pinning stronger, making it harder to hack the PKI ecosystem.
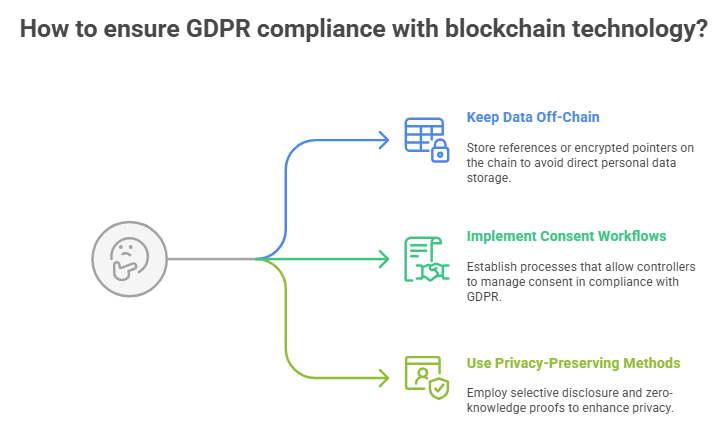
The puzzle of privacy, compliance, and the GDPR
Immutable records make it hard to keep your privacy. The right to erasure in rules like GDPR goes against a permanent ledger. The best way to handle this is to keep personal data off the chain, store references or encrypted pointers on the chain, and make consent workflows that let controllers follow the law.
Selective disclosure and zero-knowledge proofs are two privacy-preserving methods. They make things more complicated, but they also make blockchain solutions more useful in light of current privacy laws.
Practical limits and places where attacks can happen
Blockchain moves some security problems around, but it doesn’t get rid of them. It is possible to change oracles that bring off-chain data onto the ledger. There can be logic bugs in smart contracts. In practice, permissioning and governance may not be very strong, which can lead to insider risks.
The most important thing is that attackers still go after endpoints, wallets, and integration points instead of the ledger itself. It is still important to have strong endpoint hardening, supply chain audits, and operational security.
Examples from the real world and early adopters
Pilots are gaining traction in fields like finance and manufacturing. Big companies are trying out ledger-based provenance for materials and signed shipment states. Other groups use ledger-anchored logs to make it easier to audit workflows that are subject to rules.
These early deployments show one pattern: successful projects combine clear business needs with careful threat modeling and gradual rollouts. When everything is in the right place, the technology lowers risk and makes people more responsible.
Roadmap: how to safely pilot a team
Begin with a small amount. Choose one important problem where tamper evidence or traceability is important. Make a prototype with a simple data model and clear ways to measure success. To control risk, use permissioned networks and strong key management.
Check the results. Keep an eye on whether investigations are going more quickly, whether the costs of compliance reporting are going down, and whether stakeholders trust the results. Use the pilot as a chance to learn, and only move on to production when both security and operations are happy.
Final thoughts
Blockchain for cybersecurity is not a cure-all. It is a collection of tools that change where trust lives and how evidence is kept. When used with good design, strong encryption, and smart governance, it can make it harder for attackers to get in and easier for defenders to keep them out.
Follow us on X (Twitter) and LinkedIn for more cybersecurity news and updates. Stay connected on YouTube, Facebook, and Instagram as well. At Hoplon Infosec, we’re committed to securing your digital world.