Microsoft Entra ID flaw
I still remember the first time I learned just how fragile trust can be inside identity systems. One small piece of data, a token, sits at the heart of authentication and authorization. If that token can be forged or accepted outside its intended context, everything it protects can collapse. That is the uncomfortable truth behind the recent Microsoft Entra ID flaw that set alarm bells ringing across cloud teams.
In plain terms, a legacy token mechanism and an old API validation gap let an attacker present credentials in the wrong place and be accepted as somebody else. The discovery forced a rapid global fix and a fresh look at long-neglected code paths in identity stacks. The patch is live, and the incident has become a real-world lesson in why identity hygiene matters.
Why this matters to every Entra admin
If you manage an Entra tenant, you are not running just one lock. You run dozens of locks, linked locks, delegated keys, and logging systems. The Microsoft Entra ID flaw exposed how an unexpected and undocumented token type could be treated as a master key across boundaries that were supposed to be isolated. That means an issue in one tenant could, in theory, affect another tenant that trusted the wrong signals.
It is easy to feel detached from such theoretical risks until you imagine losing control of the Global Administrator account in your tenant. That account can reset other admins, change service configurations, and create new identities. Suddenly a vulnerability in a backend token system stops being academic and becomes one of the most critical items on any security leader’s list.
Who found the problem, and how did it reach Microsoft?
A security researcher, working through a series of curious authentication behaviors, discovered that undocumented backend tokens could be misused when combined with a validation error in an older API. The researcher promptly reported the issue, and Microsoft investigated and pushed fixes to eliminate the risky validation path. The disclosure timeline shows coordinated reporting, internal triage, and a staged remediation that was applied across Microsoft’s cloud services.
That sequence of discover, report, and patch is how serious vulnerabilities should be handled. In this case, the researcher’s meticulous analysis exposed not only a single bug but also a systemic weakness born of legacy systems that had not been fully retired. The responsible disclosure helped prevent potential abuse at scale.
The legacy plumbing behind the problem: tokens and old APIs
Identity systems evolve. Old APIs remain in production because they are convenient, because apps still rely on them, or because migrations are hard. The Microsoft Entra ID flaw hinged on an old Graph API path that failed to validate the originating tenant properly. At the same time, an obscure token type known internally allowed a caller to be treated as an actor with broader privileges than intended.
Think of it like an old door with a new lock installed, but the bolting mechanism is still the original. No matter how good the new lock is, the old bolt can still be forced. Legacy token mechanisms were the bolt here, and the old Graph API failed to check whether the bolt was meant for this door.
The wider lesson is about technical debt. Systems accumulate behavior that can be relied on by clients and integrations. Until those behaviors are intentionally retired or strictly reconciled, they remain an attack surface. That is a painful but necessary conversation for platform owners.
How cross-tenant impersonation was possible in practice
At a technical level the exploit combined two facts. First, certain actor tokens were able to assert an identity without being subject to standard tenant validation. Second, the retiring Graph API had a validation gap that did not verify whether the token was intended for the tenant being accessed. Put together, those gaps meant a token issued to one tenant could be accepted as valid in another tenant, impersonating any user there.
This is not a subtle privilege escalation. It is impersonation that can reach the top of the permissions ladder. Because actor tokens are first party and trusted by internal systems, they could bypass protections that normally stop external attackers, creating a path to global admin impersonation that would be invisible to many standard checks.
What an attacker could have done with global admin impersonation
If an attacker gained Global Administrator privileges in a tenant, the options are stark. They could create service principals, change authentication flows, exfiltrate mail and documents, or create backdoor accounts. In larger organizations, that could mean access to critical business systems and the ability to persist without detection.
Beyond data theft, a compromised global admin enables an attacker to alter audit settings and remove logs, making detection and recovery much more difficult. That stealth makes identity attacks particularly dangerous, because by the time defenders notice suspicious activity, the attacker may already have disabled key controls.
How modern protections were sidestepped: MFA, conditional access, and logging
What made this weakness especially worrying is that standard defenses were not fully effective. Multi factor authentication and conditional access rules operate at the surface when credentials or sessions are evaluated. But actor tokens and internal validation paths can be trusted by backend systems in ways that bypass these layers.
If a backend token is accepted at an internal validation point, conditional access might never be executed, and MFA prompts might never be-factor triggered. Similarly, some backend actions do not produce the same audit signals as user-interactive events, so activities can leave less obvious trails. That is why cloud identity hardening must be holistic and not rely on a single line of defense.
Patch timeline and Microsoft’s response
Microsoft responded quickly after the issue was reported, implementing code changes and rolling out global fixes to remove the risky validation behavior. Public reporting indicates the fixes were pushed within days, followed by additional mitigations and steps to retire the legacy paths that enabled the problem. Microsoft reported no evidence of active exploitation during their investigation.
For operators this timeline shows that platform owners can and will act fast when a critical identity risk is uncovered, but it also underscores why customers cannot simply rely on vendor patches alone. Rapid fixes are necessary, but local detection, review, and defensive configuration remain essential.
Quick checks: how to tell whether you might have been exposed
Start with the obvious: review privileged account activity and audit logs for unusual service principal creations, and look for changes to authentication policies. Even when Microsoft states a patch requires no customer action, it is wise to confirm your tenant does not show anomalies that match the attacker techniques described.
Organizations with robust logging can search for unexpected token usage patterns, unusual API calls originating from internal service principals, and any administrative changes made by accounts that should not have been able to act at that level. If your telemetry is thin, consider exporting logs to a longer retention sink before any cleanup activity.
Immediate fixes every admin should run today
If you are an Entra admin, consider three immediate moves. One, ensure your tenant is on the latest vendor guidance and patches. Two, enforce a strict least privilege model and review who holds the Global Administrator role. Three, retire or tightly monitor legacy applications and endpoints that use old authentication flows.
These steps are blunt but effective. Patching reduces immediate exposure. Least privilege limits blast radius. Retiring legacy flows removes the very pieces of plumbing that led to this problem. Together they form a simple short-term program you can start this week.
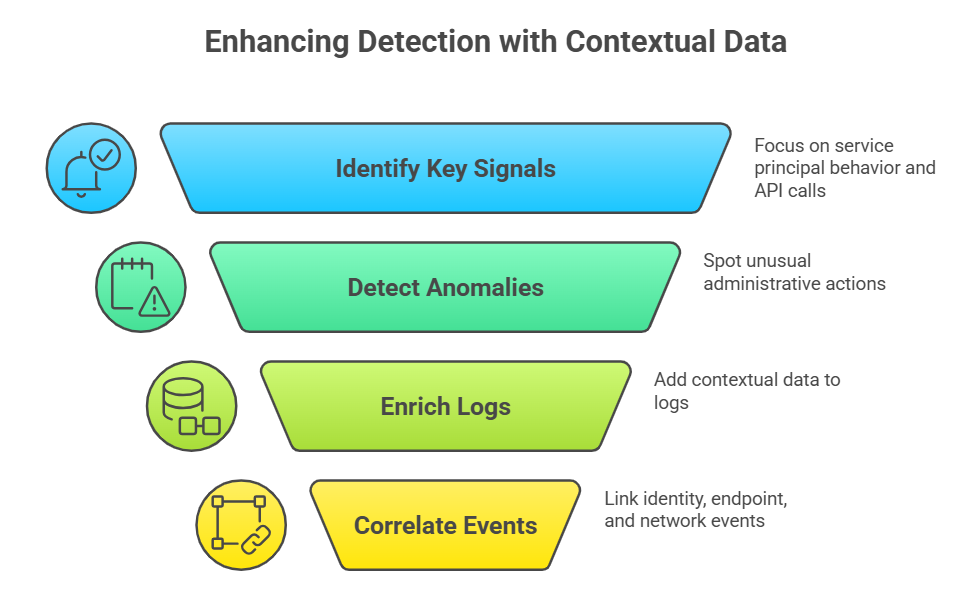
Detection tuning: log sources and signals to watch
Good detection is built on the right signals. For this class of issue, focus on service principal behavior, unusual API calls to Graph endpoints, and any anomalies in token issuance flows. Also tune alerting for administrative actions performed outside of known change windows or by accounts with no prior history of similar actions.
Enrich logs with contextual data so that an unusual administrative call is not a lonely event. Correlate identity events with endpoint and network telemetry to build a clearer picture when something suspicious happens. This makes post-incident analysis far faster and more reliable.
Longer term: retiring legacy paths and modernizing identity
The root cause involved legacy tokens and an old API. The long-term fix is to accelerate migration to modern APIs that do strict tenant validation and to remove undocumented or internal token types from production flows. That is organizational work as much as technical work, because app owners must update their clients and integrations.
Think of this as technical debt repayment. Spend time auditing all apps that use older authentication mechanisms, plan phased migrations, and enforce deprecation windows. If you wait until someone else finds the bug, it will likely be too late.
Risk management and incident playbooks for identity compromises
Identity compromises demand a distinct playbook. Rapid containment requires freezing privileged accounts, rotating application secrets and certificates, and forcing a reauthentication of service principals. Recovery requires a forensic review of logs and a careful rebuild of any modified trust relationships.
In the wake of this incident, organizations should rehearse identity incident drills that simulate token misuse and tenant impersonation scenarios. Practice reduces panic and improves the speed and accuracy of the real response. That practical readiness is the difference between a broken login and a catastrophic breach.
What the security community learned and the industry reaction
The reaction from researchers and vendors has been a mixture of relief and sober reflection. Relief that the issue was found and fixed before mass abuse. Reflection on how much legacy code still silently uncovers new risk. Many experts call for clearer deprecation policies for old APIs and more transparent telemetry about backend token use.
That conversation is healthy. It pushes platform owners toward more intentional decommissioning of legacy surfaces, and it reminds enterprise teams to treat identity as an evolving, high-risk domain that requires continuous attention.
Closing: practical takeaways and a simple action plan
Here are the quick wins: confirm your tenant shows no signs of compromise, review and reduce Global Administrator assignments, retire legacy apps that use old Graph APIs, and tune detection for service principal and token anomalies. These steps cost little and raise the bar immediately.
The Microsoft Entra ID flaw is a wake-up call, not a unique mystery. Identity systems will continue to evolve, and they will carry relics from past architectures. Your job as a defender is to treat those relics like fuel for fires and to remove them before the match is struck. Start today, and make that technical debt a line item that gets paid down on a schedule.
Follow us on X (Twitter) and LinkedIn for more cybersecurity news and updates. Stay connected on YouTube, Facebook, and Instagram as well. At Hoplon Infosec, we’re committed to securing your digital world.




