The threat actor identified as Storm-0501 has focused its efforts on the government, manufacturing, transportation, and law enforcement sectors within the United States to execute ransomware attacks.
This multi-faceted attack campaign aims to infiltrate hybrid cloud environments and facilitate lateral movement from on-premises systems to cloud infrastructures. The ultimate objectives include data exfiltration, credential theft, manipulation of data, establishment of persistent backdoor access, and the deployment of ransomware, as reported by Microsoft.
According to the threat intelligence team at the technology company, “Storm-0501 is a financially driven cybercriminal organization that employs both commercial and open-source tools to carry out ransomware operations.”
Having been active since 2021, this threat actor has previously targeted educational institutions with the Sabbath (54bb47h) ransomware. Over time, it has transitioned into a ransomware-as-a-service (RaaS) affiliate, distributing a variety of ransomware payloads, including Hive, BlackCat (ALPHV), Hunters International, LockBit, and Embargo ransomware.
A significant characteristic of Storm-0501’s attacks is its exploitation of weak credentials and excessively privileged accounts to transition from on-premises environments to cloud infrastructure.
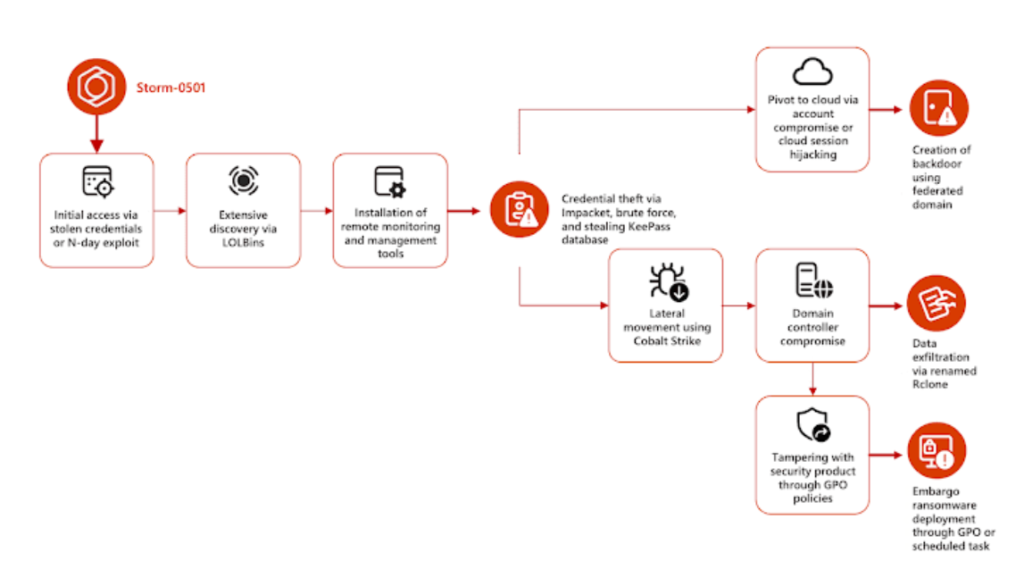
Additional initial access techniques involve leveraging footholds established by access brokers such as Storm-0249 and Storm-0900, or taking advantage of various known remote code execution vulnerabilities present in unpatched internet-facing servers, including Zoho ManageEngine, Citrix NetScaler, and Adobe ColdFusion 2016.
The access gained through any of these methods facilitates comprehensive discovery operations aimed at identifying high-value assets, collecting domain information, and conducting Active Directory reconnaissance. This process is subsequently followed by the implementation of remote monitoring and management tools (RMMs) like AnyDesk to ensure persistence.
According to Microsoft, the threat actor exploited administrative privileges on the local devices compromised during initial access and sought to gain entry to additional accounts within the network through multiple methods.
The threat actor predominantly employed the SecretsDump module from Impacket, which facilitates the extraction of credentials via the network, and applied it across a wide array of devices to gather credentials.
The acquired credentials were subsequently utilized to gain access to additional devices and retrieve further credentials. Concurrently, the threat actor accessed sensitive files to extract KeePass secrets and executed brute-force attacks to obtain credentials for particular accounts.
Microsoft reported the detection of Storm-0501 utilizing Cobalt Strike to navigate laterally within the network by leveraging compromised credentials to issue subsequent commands. The exfiltration of data from the on-premises environment is executed through Rclone, which facilitates the transfer of data to the MegaSync public cloud storage service.
The threat actor has also been noted for establishing persistent backdoor access to the cloud environment and deploying ransomware within the on-premises infrastructure, marking it as the latest entity to target hybrid cloud configurations, following Octo Tempest and Manatee Tempest.
According to Redmond, “The threat actor exploited credentials, specifically Microsoft Entra ID (previously known as Azure AD), that were acquired earlier in the attack to transition from the on-premises environment to the cloud, thereby creating a persistent access point to the target network through a backdoor.”
The transition to the cloud is reportedly achieved either through a compromised Microsoft Entra Connect Sync user account or through the hijacking of a cloud session belonging to an on-premises user account that possesses an associated admin account in the cloud, particularly when multi-factor authentication (MFA) is disabled.
The assault reaches its peak with the implementation of Embargo ransomware within the targeted organization, following the acquisition of adequate control over the network, the exfiltration of pertinent files, and lateral movement into the cloud environment. Embargo, a ransomware variant developed in Rust, was initially identified in May 2024.
According to Microsoft, “Operating under the RaaS model, the ransomware group behind Embargo permits affiliates such as Storm-0501 to utilize its platform for executing attacks in return for a portion of the ransom.”
“Affiliates of Embargo utilize double extortion strategies, whereby they first encrypt the files of the victim and subsequently threaten to disclose the stolen sensitive information unless the ransom is paid.”
The revelation arises as the DragonForce ransomware group has been focusing its efforts on companies within the manufacturing, real estate, and transportation industries, utilizing a variant of the leaked LockBit3.0 builder alongside a modified version of Conti.
These attacks are marked by the implementation of the SystemBC backdoor to ensure persistence, as well as the use of Mimikatz and Cobalt Strike for credential harvesting, with Cobalt Strike also facilitating lateral movement. The United States accounts for over 50% of the total victims, with the United Kingdom and Australia following.
“The group utilizes double extortion strategies, encrypting data and threatening to leak it unless a ransom is paid,” stated Group-IB, which is based in Singapore. “The affiliate program, initiated on June 26, 2024, allocates 80% of the ransom to affiliates and provides tools for managing and automating attacks.”
Reference
https://thehackernews.com/2024/09/microsoft-identifies-storm-0501-as.html