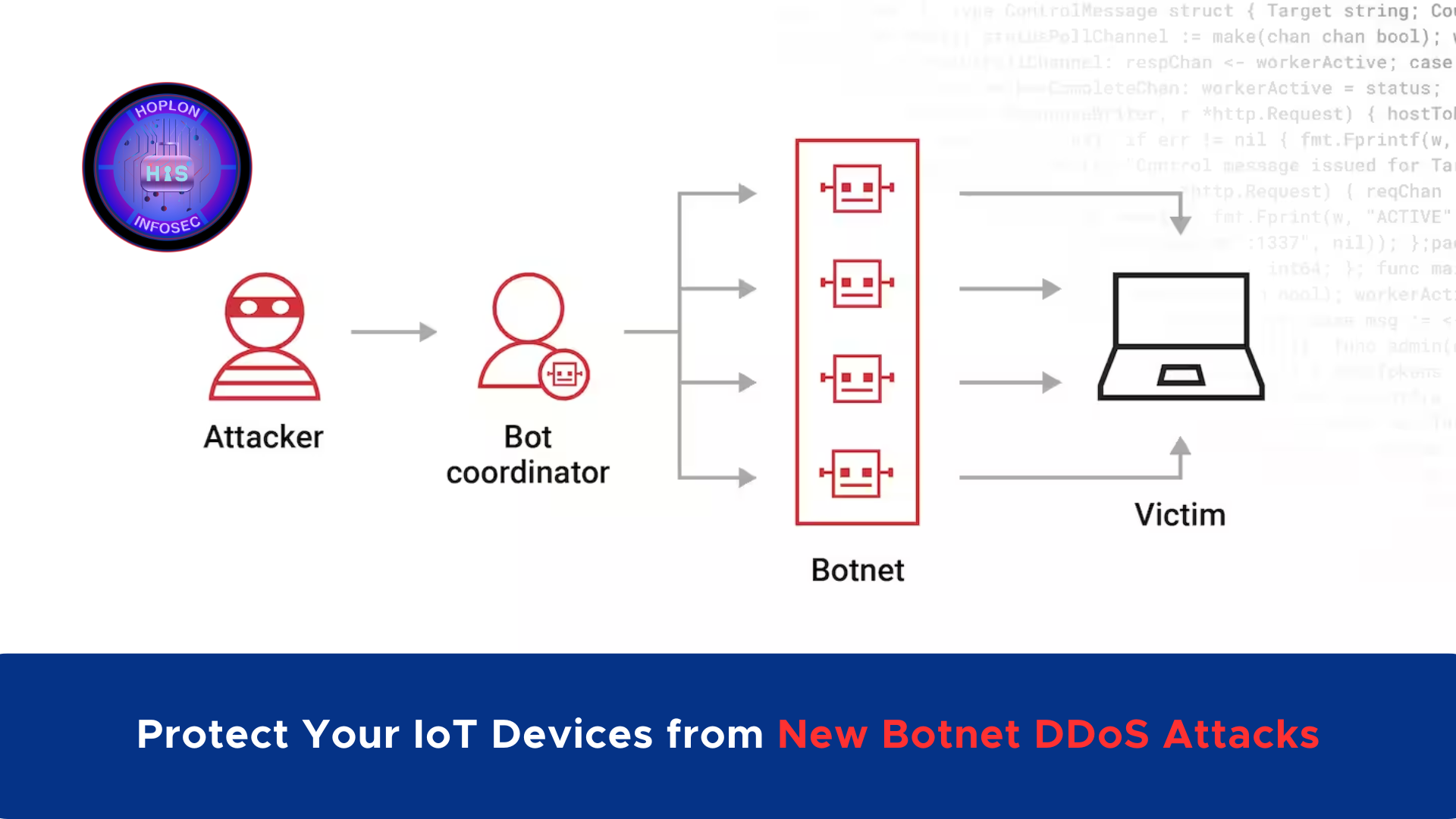
The rise of the Internet of Things (IoT) has brought immense convenience and connectivity and introduced new vulnerabilities to the cybersecurity landscape. One of the most concerning threats emerging in recent months is the rise of IoT botnets that have been orchestrating large-scale Distributed Denial-of-Service (DDoS) attacks globally. These botnets exploit the vulnerabilities inherent in IoT devices, such as routers, IP cameras, and other connected devices, to launch devastating attacks on industries and critical infrastructure worldwide. The malware behind these attacks, derived from notorious strains like Mirai and Bashlite, poses a significant risk to the stability of the internet and the safety of sensitive data.
What Is an IoT New Botnet and How Does It Work?
An IoT botnet is a network of compromised IoT devices that can be remotely controlled to carry out various cyberattacks, including DDoS attacks. In a DDoS attack, the botnet floods a target server, service, or network with massive traffic, overwhelming its resources and making it unavailable to legitimate users. IoT devices are particularly susceptible to being hijacked because they often come with weak default passwords or unpatched vulnerabilities that attackers can exploit.
Initial Exploitation: The Gateway for Malware
The infection process of an IoT botnet begins with exploiting vulnerabilities in the target devices. Attackers typically use two main tactics to gain control over IoT devices:
- Remote Code Execution (RCE) Vulnerabilities: Attackers exploit device software flaws to execute malicious code remotely. These vulnerabilities may be caused by outdated Firmware or unpatched software.
- Weak Default Credentials: Many IoT devices ship with weak or default usernames and passwords, such as “admin” and “password,” which are easily guessed by attackers using brute-force methods.
Once the attacker gains access, the next phase of the infection begins.
Payload Delivery: Downloading the Malware
Once the attacker has successfully infiltrated a device, the next step is to deliver the malicious payload. This is typically done using a loader script that downloads the main malware from a distribution server. The malware is executed directly in memory, which means it does not leave traces on the infected device, making detection more difficult for security systems.
Command-and-Control (C&C): Communication with the Botnet
After the malware has been deployed, the infected devices connect to a central Command-and-Control (C&C) server to receive instructions. These servers are responsible for issuing attack commands, including the targets and attack parameters, to the compromised devices in the botnet. The devices then carry out the attacks on behalf of the attackers.
DDoS Attack Vectors Used by IoT Botnets

Once a botnet is established, the next step is launching DDoS attacks on targeted services. The attackers use a variety of attack vectors to overwhelm the target’s resources. Some of the most common types of attacks used by IoT botnets include:
- SYN Floods: In a SYN flood, the botnet sends many SYN requests to the target server, which then tries to respond to each request. The server is overwhelmed by these requests, exhausting its resources and making it unable to respond to legitimate user traffic.
- UDP Floods: This attack targets the victim’s network by sending a massive volume of UDP packets. Since UDP is a connectionless protocol, the target cannot quickly identify whether the packets are legitimate, making it harder for the victim to defend against such attacks.
- GRE Protocol Exploits: Attackers also exploit General Router Encapsulation (GRE) protocol vulnerabilities to target routers. GRE is commonly used to encapsulate data packets for secure transmission across networks, and flaws in the protocol can lead to severe disruptions in the routing infrastructure.
- TCP Handshake Floods: In a TCP handshake flood, the botnet establishes numerous fake TCP connections with the target server, consuming its resources by forcing it to establish and attempt to maintain these fake connections.
A Global Threat: Geographic Reach and Affected Industries
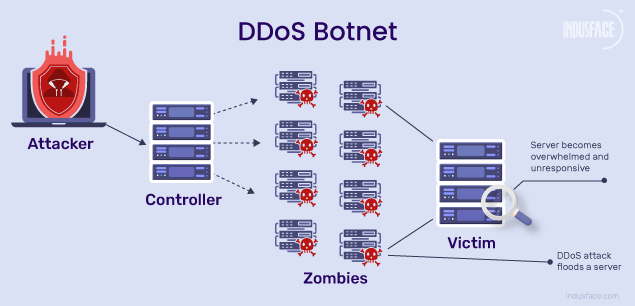
This IoT botnet has demonstrated a global reach, impacting various sectors, including finance, transportation, telecommunications, and more. The United States has been particularly hard hit, accounting for approximately 17% of identified targets. At the same time, Europe and Japan have also seen significant attacks, with Japan’s financial and transportation industries being prime targets.
The botnet is not limited to one geographic area or industry—it is a highly versatile threat that targets any vulnerable IoT devices within its range. As IoT devices proliferate globally, the number of potential targets for these botnets continues to grow.
Commonly Affected Devices and Brands
Security research reveals that most compromised devices in these botnet attacks are wireless routers (about 80%), followed by IP cameras (15%). These devices are targeted primarily because they are commonly used in households and businesses worldwide, and many come with known security vulnerabilities.
Brands such as TP-Link and Zyxel have been frequently compromised due to their widespread use and known product vulnerabilities. If left unpatched, these vulnerabilities allow attackers to gain control over the devices and use them for malicious purposes.
Techniques for Avoiding Detection
One of the more sophisticated aspects of this IoT botnet is its ability to avoid detection. The malware in these botnets turns off the watchdog timers on the infected devices, typically triggering a reboot in case of a high load caused by a DDoS attack. By turning off the watchdog timers, the malware ensures that the infected devices remain operational during attacks, making it harder for defenders to identify compromised devices.
Additionally, the malware manipulates iptables, a Linux-based firewall tool, to block external access while maintaining communication with the C&C servers. This ensures the devices can continue receiving attack commands without being detected or interrupted.
Mitigation Strategies for IoT Botnet Infections
To mitigate the risk of IoT botnet infections, experts recommend a series of proactive measures that individuals and organizations can implement:
- Change Default Passwords: Always change the default passwords of IoT devices as soon as they are installed. Use strong, unique passwords to reduce the likelihood of brute-force attacks.
- Update Firmware Regularly: Ensure that all IoT devices have the latest firmware updates to patch known vulnerabilities. Manufacturers frequently release updates to address security flaws, so staying current is essential.
- Isolate IoT Devices: Where possible, isolate IoT devices on separate networks from critical infrastructure. This limits the exposure of sensitive systems to attacks originating from compromised IoT devices.
- Use Intrusion Detection Systems (IDS): Deploying IDS can help organizations identify abnormal traffic patterns and suspicious behavior on their networks, enabling early detection of potential attacks.
- Collaborate with Service Providers: Organizations should work closely with their internet service providers (ISPs) to filter out malicious traffic. Service providers can implement filtering solutions that detect and block DDoS traffic before it reaches its target.
- Deploy Content Delivery Networks (CDNs): CDNs can help mitigate the impact of DDoS attacks by distributing the load across multiple servers, reducing the strain on any one server, and ensuring continued service availability during attacks.
Conclusion: The Growing Threat of IoT Botnets
As IoT devices become more widespread and integral to our daily lives, they also present new vulnerabilities that malicious actors can exploit. IoT botnets, such as the one described in this article, have proven to be highly effective tools for launching large-scale DDoS attacks that can disrupt critical services and infrastructure.
The key to combating this threat lies in proactive security measures, including regular device maintenance, strong authentication practices, and collaboration between individuals, organizations, and service providers. By staying vigilant and implementing these best practices, we can reduce the risk of IoT botnet infections and protect our digital infrastructure from the growing threat of cyberattacks.
For more:
https://cybersecuritynews.com/new-iot-botnet-launching-large-scale-ddos-attacks/