In today’s interconnected digital environment, Cyber Threats in 2025 have become formidable adversaries to businesses striving to survive and thrive. Like living organisms, these threats evolve, adapt, and multiply, constantly challenging security measures. This dynamic landscape demands proactive cybersecurity strategies prioritizing prevention over reactive cures and leveraging cutting-edge tools to safeguard businesses effectively.
The Importance of Threat Intelligence in Cybersecurity
Threat intelligence forms a cornerstone of a robust cybersecurity framework. It equips security teams with actionable data about new and emerging threats, enabling them to analyze potential attacks, predict their development, and prevent breaches before they occur. Organizations can avoid operational disruptions, financial losses, data leaks, and reputational damage by profiling adversaries and intercepting them early.
Core Business Goals Supported by Threat Intelligence
- Protecting Critical Assets: Enterprises house sensitive information such as intellectual property, customer data, financial records, and operational systems. Cybercriminals target vulnerabilities within these systems, potentially causing data breaches, intellectual property theft, and service disruptions that can compromise competitive advantages.
- Maintaining Business Continuity: Smooth operations and uninterrupted service delivery are crucial for business stability. Cyber threats can disrupt these processes, making proactive threat monitoring essential.
- Preserving Customer Trust: A data breach involving sensitive customer information damages trust, tarnishes brand reputation and may lead to legal liabilities. Threat intelligence ensures organizations stay ahead of potential risks.
- Managing Financial Risk: Cyber threats like ransomware demand significant payouts, and breaches lead to remediation costs, legal fees, and potential lawsuits. Proactive threat monitoring helps businesses take cost-effective preventive measures.
- Supporting Strategic Growth: Adopting new technologies without adequate security can expose vulnerabilities. Threat intelligence ensures that innovation remains an asset, not a liability, by addressing security gaps and safeguarding growth strategies.
By demonstrating strong cybersecurity practices, organizations position themselves as reliable partners, particularly in industries where data protection is a top priority.
Sources of Threat Intelligence: Harnessing the Power of Data
Threat intelligence relies on data collected from both internal and external sources:
- Internal Sources: Firewalls, endpoint protection systems, Security Information and Event Management (SIEM) systems, and other internal logs generate invaluable insights into the security landscape.
- External Sources: These include threat databases, feeds, dark web forums, open web discussions, and blogs. Additionally, third-party threat intelligence services, such as ANY. RUN’s TI Lookup provides specialized tools to gather and analyze data efficiently.
The Role of Third-Party Intelligence Services
Services like ANY. RUN’s TI Lookup enhances threat intelligence by offering search operators, team collaboration features, and comprehensive reports. Such tools ensure that businesses have real-time access to the most relevant threat data, enabling them to stay ahead of cybercriminals.
The Need for Real-Time Threat Intelligence for Cyber Threats in 2025
In the rapidly shifting cyber threat landscape, real-time intelligence is vital. Cyber adversaries thrive by staying steps ahead of their targets. Therefore, businesses must continuously monitor updates to the threat infrastructure—automated update tracking features, like live threat updates in ANY. RUN’s Threat Intelligence Lookup provides essential real-time insights.
Exploring Threat Intelligence Lookup by ANY.RUN
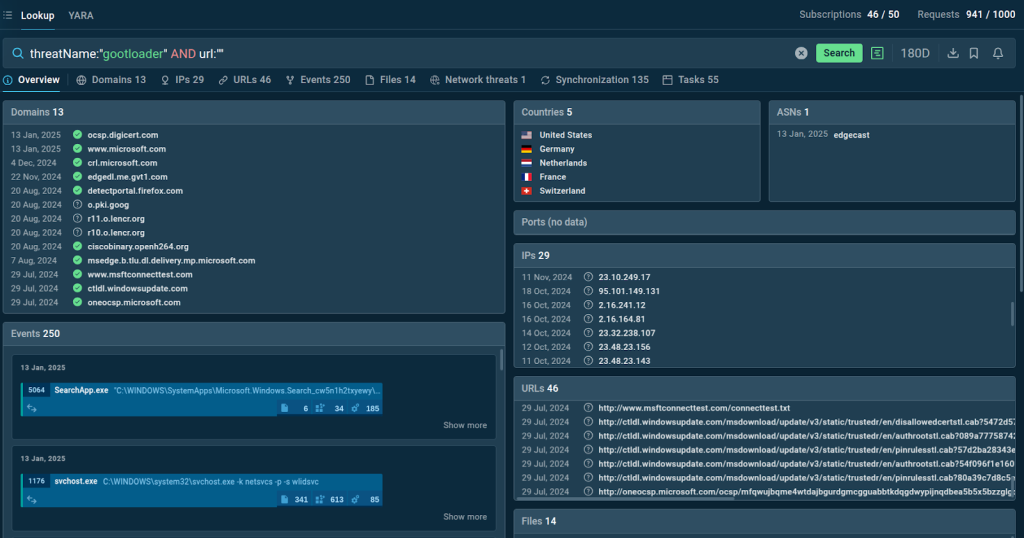
ANY. RUN’s Threat Intelligence Lookup is a cutting-edge security tool that delivers real-time insights into cyber threats. Aggregating data from sandbox analyses simplifies identifying, understanding, and enriching threat intelligence.
Key Features of Threat Intelligence Lookup
- Extensive Database: Access over 40 types of threat data, including system events, Indicators of Compromise (IOCs), Indicators of Behavior (IOBs), and Indicators of Attack (IOAs).
- Fresh Results: Data collected from thousands of sandbox sessions within 180 days ensures relevance.
- Fast Search: Retrieve results within seconds, enhancing operational efficiency.
- Real-Time Updates: Stay informed with timely alerts on evolving threats.
Practical Applications of Threat Intelligence Lookup
Monitoring Malware Evolution
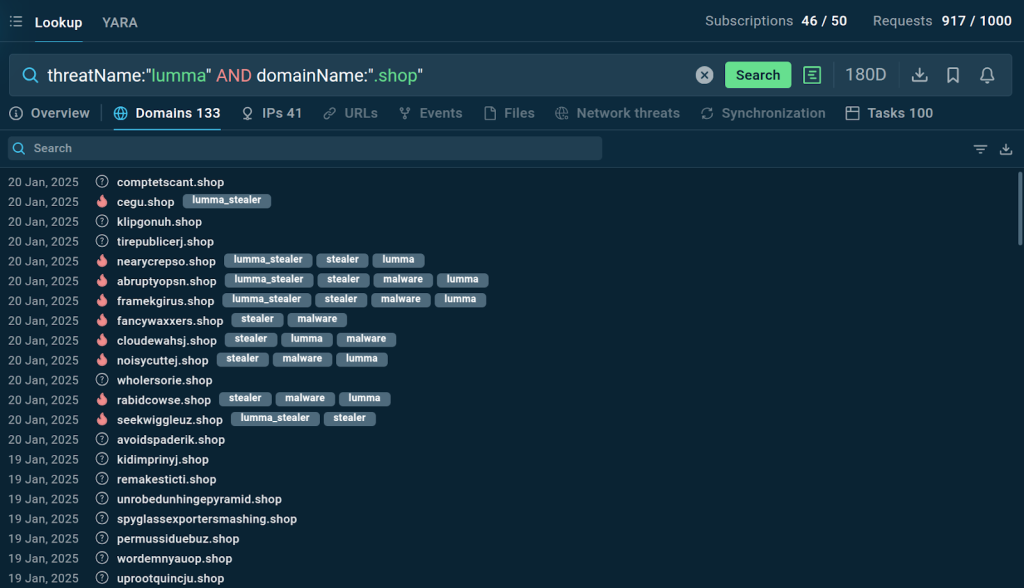
Organizations often face targeted attacks from specific malware families. For example, monitoring the network activity of malware like Lumma can reveal it’s evolving tactics. Using search queries such as:
Threat name: “lumma” AND domainName: “.shop”
Security teams can identify domains used by attackers. This capability allows businesses to block malicious activities and prevent breaches proactively.
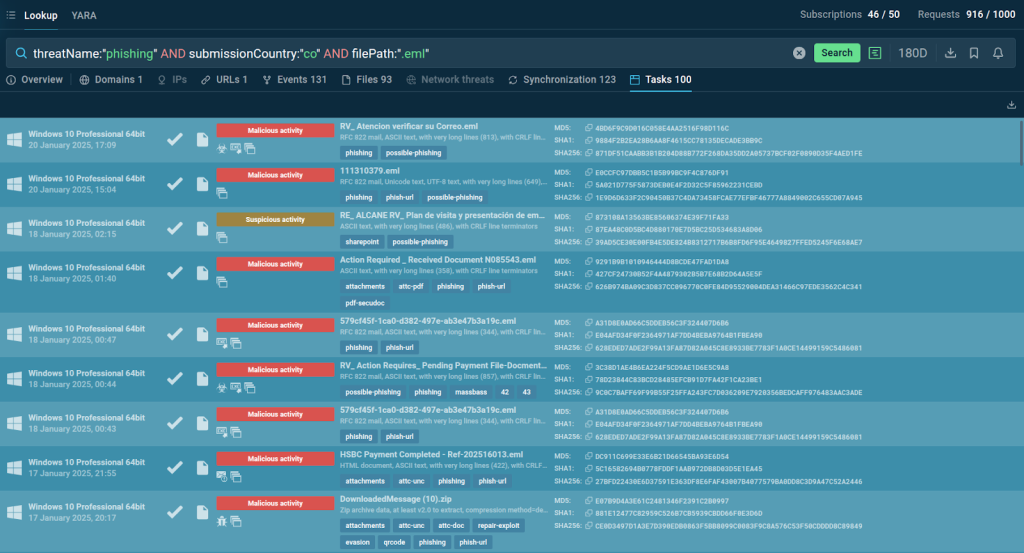
Addressing Country-Specific Threats
Threat Intelligence Lookup also facilitates tracking attacks targeting specific regions. For instance, to monitor phishing emails aimed at Colombian organizations, a query such as:
Threat name: “phishing” AND submissionCountry: “co” AND filePath: “.eml.”
Can provide detailed insights. Analysts can explore public sandbox sessions and examine the exact steps of phishing attempts, such as fake Microsoft login pages used to steal credentials.
Advantages of Implementing Threat Intelligence Lookup
Incorporating Threat Intelligence Lookup into an organization’s cybersecurity strategy provides numerous benefits:
- Proactive Threat Detection: Detect potential threats early, enabling businesses to take preventive actions and minimize risks.
- Informed Decision-Making: Data-driven insights allocate resources effectively, keeping security strategies aligned with current threats.
- Reduced Incident Response Time: Rapid identification and resolution of threats minimize downtime and operational disruptions.
- Optimized Security Investments: By focusing on relevant threats, businesses can spend their security budgets wisely, maximizing return on investment.
Conclusion: Strengthening Cybersecurity with Threat Intelligence
In today’s digital age, where cyber threats continuously evolve, businesses must adopt proactive and data-driven cybersecurity measures. Threat intelligence is no longer a luxury but a necessity for organizations seeking to protect their assets, maintain operational stability, and foster trust among customers and partners.
Tools like ANY. RUN’s Threat Intelligence Lookup exemplifies the power of real-time data in combating cyber threats. By integrating such solutions, businesses can not only bolster their defenses but also position themselves as leaders in cybersecurity, ready to tackle the challenges of an ever-changing digital landscape.
For more:
https://cybersecuritynews.com/how-to-track-evolving-cyber-threats/




