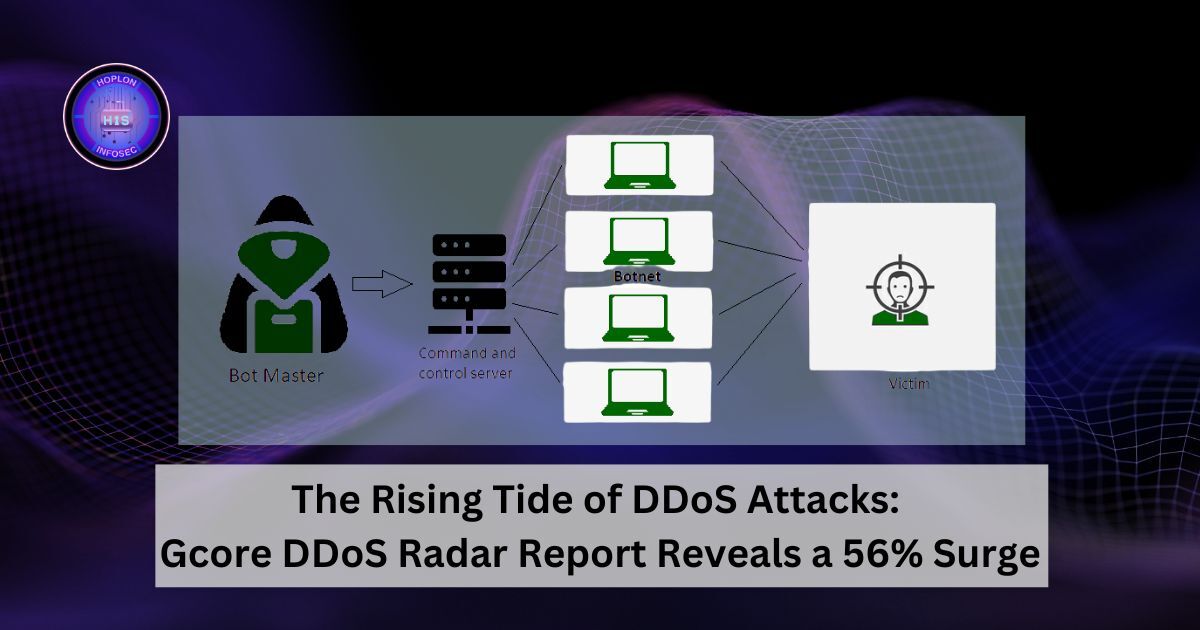
Cybersecurity threats continue to evolve at an alarming rate, and among them, Distributed Denial of Service (DDoS) attacks are becoming increasingly frequent and sophisticated. Gcore DDoS Radar Report for Q3–Q4 2024 delivers crucial insights into this growing menace, revealing a staggering 56% year-over-year (YoY) increase in total attacks. The financial sector witnessed an alarming 117% spike, while gaming remains the most targeted industry. The most significant recorded attack peaked at two terabits per second (Tbps), highlighting the urgent need for more adaptive and resilient mitigation strategies.
Let’s break down the key takeaways and explore how businesses can defend themselves against the rising wave of DDoS attacks.
Gcore DDoS Radar Report: Breaking Down the Numbers

Gcore’s findings paint a concerning picture of the current cybersecurity landscape. The volume and complexity of DDoS attacks are escalating, making it imperative for businesses to stay ahead of evolving threats. Here are the standout insights from the report:
- Attack Frequency Is Surging: The total number of DDoS attacks has increased by 56% compared to the same period in 2023.
- Financial Services Face Escalating Risks: Attacks on financial institutions skyrocketed by 117%, making them a prime target.
- Attacks Are Becoming More Precise and Short-Lived: High-intensity, short-duration burst attacks are becoming the norm.
- Geopolitical Factors Playing a Role: The origins of attacks are increasingly influenced by political and economic conflicts.
These findings underscore the importance of evolving cybersecurity defenses to counteract the growing sophistication of cyber threats.
The Growing Threat to Financial Services
Traditionally, gaming has been the most frequently targeted industry due to the competitive nature of online gaming and its lucrative digital economy. However, the financial sector is now emerging as a primary target, with attacks increasing by 117%.
Why the sudden rise?
- High-Value Targets: Financial institutions handle massive transactions, making them lucrative targets for attackers.
- Regulatory Pressures: The sector’s reliance on compliance frameworks means a successful attack can have severe legal and financial consequences.
- Rise in Ransom DDoS (RDoS) Attacks: Cybercriminals increasingly use DDoS attacks as leverage for ransom demands.
Financial institutions must ramp up their security posture with these escalating risks by integrating advanced threat intelligence and real-time mitigation strategies.
Gaming: The Perpetual Target
Despite the financial sector’s surge in attack frequency, gaming remains the number one target, albeit with a reduced share of total attacks (down from 49% to 34%). The gaming industry’s vulnerability stems from:
- High-Value Downtime: Any disruption in gaming services leads to immediate revenue loss and customer dissatisfaction.
- Competitive Sabotage: Players and bad actors may use DDoS attacks to gain unfair advantages in online gaming environments.
- Scalability Challenges: Game servers are frequent targets due to their requirement for low-latency performance, making them sensitive to traffic spikes.
Gaming companies must continue investing in proactive defenses as attackers refine their strategies to bypass traditional mitigation techniques.
The Rise of Ultra-Intense, Short-Burst Attacks
A significant trend highlighted in the report is the shift toward shorter yet highly disruptive attacks. The most extended recorded attack in Q3–Q4 2024 lasted only five hours, a sharp decline from 16 hours in the previous period.
Why are attackers moving toward short-burst attacks?
- Evading Detection: Traditional DDoS defenses rely on prolonged attack patterns to identify and mitigate threats. Shorter attacks can bypass these mechanisms.
- Maximizing Impact: High-intensity bursts can overload systems within minutes, causing immediate disruption.
- Multi-Vector Strategies: Attackers use short bursts as distractions while launching secondary attacks, such as ransomware or credential stuffing.
To counteract these rapid strikes, businesses must upgrade their defenses with AI-powered traffic analysis and real-time threat monitoring.
The Largest Attack Yet: A 2 Tbps Onslaught
The report reveals that the most significant recorded DDoS attack in Q3–Q4 2024 reached a peak of 2 Tbps, marking an 18% increase from the previous peak of 1.7 Tbps earlier in the year. The attack targeted a major global gaming company, emphasizing the growing intensity of cyber threats.
Large-scale attacks like these have the potential to:
- Disrupt entire networks within seconds.
- Cause financial losses due to prolonged downtime.
- Overwhelm mitigation strategies that are not designed for terabit-scale traffic.
Such incidents highlight the need for organizations to implement scalable, high-capacity defense mechanisms that can neutralize even the most extreme threats.
How Geopolitical Factors Are Influencing Attack Patterns
Cyber warfare is no longer just a concept; it’s a reality shaping the DDoS landscape. The report identifies several key trends linked to geopolitical tensions:
- Politically Motivated Attacks: State-sponsored cyber groups and hacktivists increasingly target financial services, infrastructure, and key industries.
- Emerging Attack Hubs: The US, the Netherlands, and China remain significant sources of attack traffic, while Brazil is emerging as a growing hub for network-layer attacks.
- Botnet Expansion: IoT vulnerabilities and malware-infected devices continue to amplify attack volumes, allowing malicious actors to strike from multiple regions simultaneously.
Organizations operating in high-risk regions must develop a cybersecurity strategy incorporating geopolitical threat intelligence to anticipate and mitigate attacks proactively.
The Evolution of DDoS Attack Strategies
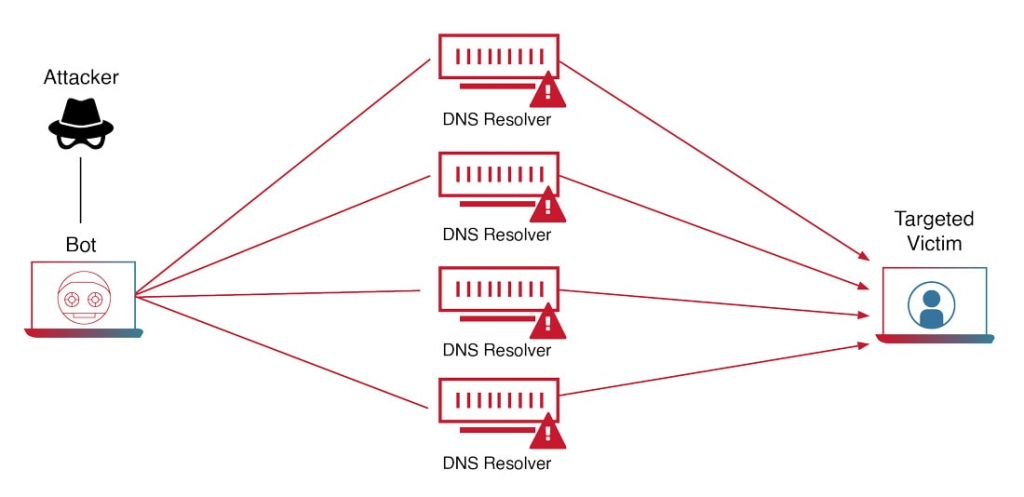
Attackers are continually refining their methods, and some of the most notable trends in 2024 include:
- The Rise of ACK Floods: These attacks, which mimic legitimate traffic, are becoming harder to detect and now account for 7% of total attacks.
- UDP Floods Continue to Dominate: Accounting for 60% of all network-layer attacks, UDP floods remain attackers’ primary weapon.
- Application-Layer Assaults: Layer 7 (L7) UDP flood attacks represent 45% of total incidents, while L7 TCP flood attacks have increased to 37%.
These evolving strategies demonstrate the need for more adaptive and intelligent mitigation techniques.
How Businesses Can Defend Against the Growing DDoS Threat
Organizations must adopt a proactive defense approach with attack volumes and complexity reaching new heights. Gcore’s report highlights the need for:
- Scalable Protection: High-capacity DDoS mitigation solutions capable of handling terabit-level attacks.
- Real-Time Threat Detection: AI-driven traffic analysis to identify and mitigate threats instantly.
- Multi-Layered Security: Combining network-layer defenses with application-layer filtering for comprehensive protection.
- Geo-Based Filtering: Implementing region-specific security measures based on attack origin intelligence.
Final Thoughts
DDoS attacks are no longer just an inconvenience; they are a critical threat capable of crippling industries and disrupting economies. Gcore’s latest report serves as a wake-up call for businesses worldwide. The rising attack frequency, the shift toward shorter high-intensity bursts, and the increasing geopolitical motivations behind cyber threats demand a new level of preparedness.
Organizations must embrace adaptive, AI-powered defense mechanisms to counter the evolving nature of DDoS attacks. With robust, scalable mitigation strategies, businesses can safeguard their digital assets against even the most formidable cyber threats.
If you like to read these blogs, please visit our website.
Source:
https://thehackernews.com/2025/02/gcore-ddos-radar-reveals-56-yoy.html