Cybersecurity continues to be a field marked by rapid innovation and equally swift adversarial tactics. Recently, ClearSky Cyber Security uncovered a critical Windows UI Vulnerability. This vulnerability is currently being exploited by a sophisticated threat actor, Mustang Panda, a group widely believed to have ties to Chinese state interests. In this article, we provide an in-depth exploration of this vulnerability, the techniques used to exploit it, and the broader implications for both individual users and enterprise environments.
Introduction
As the digital landscape evolves, so do the tactics of malicious actors seeking to exploit vulnerabilities in widely used software systems. ClearSky Cyber SecuritySecurity’sdiscovery highlights one such vulnerability in Microsoft Windows, where a seemingly benign user interface (UI) flaw can be weaponized to hide malicious files. While Microsoft has classified the issue as low severity, the implications of the exploit are far-reaching, primarily due to its stealthy nature. This article delves into the mechanics of the vulnerability, the methods of exploitation, and practical recommendations to safeguard against potential attacks.
The Growing Cyber Threat Landscape
In today’s connected world, cyber threats take many forms—from phishing attacks and ransomware to sophisticated state-sponsored espionage. State-affiliated groups like Mustang Panda have emerged as prominent players among these threats. Their operations often involve advanced techniques to evade detection and compromise systems without immediate alert. The recent discovery of the UI vulnerability in Microsoft Windows exemplifies how even a seemingly minor flaw can be manipulated for more nefarious purposes.
State-sponsored hackers have the advantage of significant resources and expertise, allowing them to exploit vulnerabilities that traditional threat actors may otherwise overlook. This underscores the critical need for ongoing vigilance, prompt software updates, and a proactive approach to cybersecurity.
What Is the Windows UI Vulnerability?

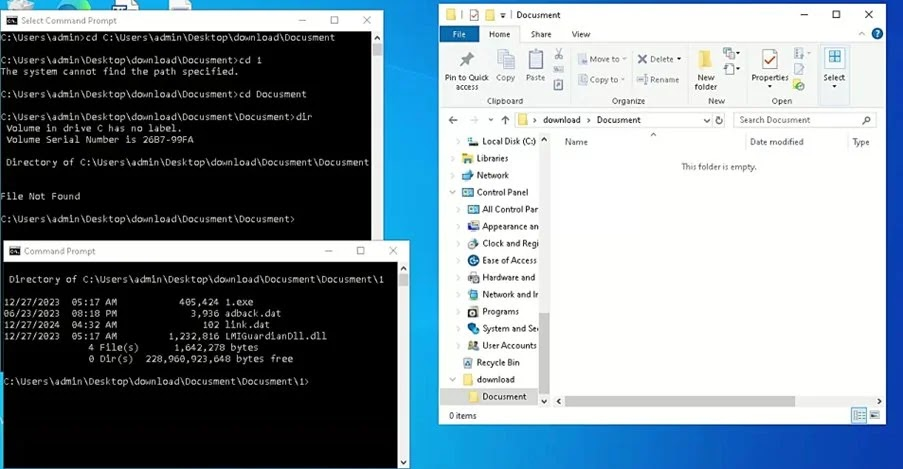
At the core of this emerging threat is a vulnerability related to Microsoft Windows’s user interface, specifically the extraction process of compressed files from RAR archives. When a user extracts files from these archives, the operating system’s Explorer may inadvertently hide them, making them an empty folder.
The hidden nature of these files is not due to their absence but instead how Windows Explorer interprets the file attributes. This anomaly can create a false sense of security, as users may assume that no files are present when, in fact, the files exist in an invisible state. This stealth characteristic is hazardous because it obscures the presence of potentially malicious files from standard user checks and basic command-line directory listings.
How the Exploit Works: Manipulation of File Visibility
The exploitation process involves manipulating the file attributes during or after the extraction of RAR archives. When files are extracted, they become hidden from view in Windows Explorer. Even when users attempt to verify the files using the command line interface—with commands such as “dir”—the” hi “den files do not appear. This discrepancy arises because the command line interface respects file attributes that are set to hidden or system, resulting in an empty folder scenario despite the actual presence of files.
Attackers leverage this vulnerability by planting malicious files within these archives. Once extracted, the files remain invisible to the user, effectively masking the malicious payload. The danger escalates if an attacker knows the exact file path. With this information, the attacker can execute the hidden file through a command-line prompt, bypassing the usual safeguards that alert a user to the file’s files.
Technical Details: Command-Line Manipulation and Hidden File Execution
A key exploit component is the ability to alter file attributes using specific command-line instructions. For instance, by running commands such as:
attrib -s -h "C:\Path\To\HiddenFile"
An attacker can remove the system and hidden attributes from these files. Once these attributes are removed, the file can be executed directly from the command line, even if the user is unaware of its existence. This manipulation creates a scenario where the files can be run as legitimate processes, potentially introducing malware or other harmful software into the system.It is important to note that this vulnerability relies not on complex kernel-level exploits but on simply manipulating file attributes that many users and even some administrators might overlook. The technique’s simplicity makes it a potent tool for an experienced attacker, especially when combined with the stealth methods employed by groups like Mustang Panda.
The Role of Mustang Panda
ClearSky Cyber Security has discovered a UI vulnerability in Microsoft Windows. This vulnerability is actively exploited by a suspected Chinese APT group – Mustang Panda.
— ClearSky Cyber Security (@ClearskySec) February 13, 2025
When files are extracted from compressed “RAR” files they are hidden from the user. If the compressed files… pic.twitter.com/Ip0L9nPRBX
Mustang Panda, a threat actor group with suspected Chinese state affiliations, has been identified as actively exploiting this Windows UI vulnerability. Known for its advanced techniques and strategic targeting, Mustang Panda is believed to focus on espionage and intelligence gathering. Its operations typically involve deep technical knowledge and a well-resourced infrastructure, which enables it to stay ahead in the cat-and-mouse game with cybersecurity professionals.
The involvement of a state-affiliated group heightens the stakes, as the objectives behind such attacks are often more strategic than financially motivated. By exploiting this vulnerability, Mustang Panda can potentially gain access to sensitive information or disrupt the operations of targeted entities. The exploit exploits characteristics allow the group to maintain persistence within a compromised environment without immediate detection.
Security Implications and the Hidden Threat
Although Microsoft has classified the vulnerability as low severity, the actual risk posed by this exploit may be understated. The primary concern lies in exploiting a system to hide files, which creates a significant blind spot in traditional monitoring and security mechanisms. The following points illustrate why this vulnerability demands serious attention:
- Stealth and Evasion: The exploit to hide files from both graphical and command-line interfaces means that users and system administrators may not be aware of malicious activities occurring in their systems. This invisibility can lead to prolonged undetected access by attackers.
- Execution of Unknown Code: By manipulating file attributes, attackers can execute malicious code without triggering standard warnings or alerts. This capability increases the risk of introducing malware, which can perform harmful activities such as data exfiltration, credential theft, or lateral movement within a network.
- Targeted Attacks: The vulnerability is already being used in targeted attacks. When combined with the resources of a state-sponsored actor, the exploit could be tailored to breach high-value targets, including governmental, industrial, or research institutions.
- False Sense of Security: The vulnerability’s low severity classification might lead some organizations to deprioritize updates or mitigation measures, inadvertently exposing their systems to this stealthy threat.
MicrosofMicrosoft’se and the Low-Severity Classification
MicrosofMicrosoft’sedgment of the vulnerability is a critical step in the response process. The company has reviewed the issue and classified it as low severity. This classification suggests that, under normal circumstances, the immediate risk may be moderate. However, the actual impact of the exploit in targeted environments or when combined with other vulnerabilities could be much more significant.
The low severity rating might be attributed to several factors:
- Limited Exposure: The exploit may require specific conditions to be effective, such as the precise method of file extraction and knowledge of the file path.
- User Interaction Required: The attack vector often relies on user actions (such as extracting files from an RAR archive), which may limit its general applicability.
- Detection and Mitigation Capabilities: Modern antivirus and endpoint detection systems often catch abnormal command-line activities, such as using the “attrib” commostandardunhide files.
Despite these considerations, the persistent nature of state-sponsored threats like Mustang Panda means that even low-severity vulnerabilities cannot be dismissed lightly. Attackers often combine multiple exploits to create a more robust and stealthy intrusion, making it imperative for users and administrators to remain vigilant.
Mitigation Strategies and Best Practices

Given the potential dangers posed by this vulnerability, both individual users and organizations should consider several mitigation strategies to protect their systems:
1. Regular Software Updates
Keeping Windows and all related software up to date is a critical first step in mitigating any vulnerability. Microsoft frequently releases patches that address known security issues. Users should enable automatic updates or regularly check for patches to protect their systems.
2. Enhanced Monitoring
Organizations should implement advanced monitoring tools to detect anomalous behaviors, such as unexpected file attribute changes or unusual command-line activity. Behavioral analytics can be instrumental in identifying stealthy exploits that bypass traditional signature-based detection methods.
3. User Awareness and Training
Educating users about the potential risks associated with downloading and extracting files from untrusted sources can help reduce the likelihood of exploitation. Awareness campaigns and regular training sessions on cybersecurity best practices can empower users to recognize and avoid risky behaviors.
4. Access Controls and Privilege Management
Limiting user privileges can reduce the impact of any single compromised account. By implementing robust access controls, organizations can ensure that even if an attacker gains access to a system, their ability to execute malicious code or alter system settings is constrained.
5. Incident Response Preparedness
Organizations should have a well-defined incident response plan in place. This plan should include procedures for detecting, analyzing, and mitigating security incidents related to this and similar vulnerabilities. Regular drills and simulations can help ensure that the response team is ready to act swiftly in the event of an attack.
6. Backup and Recovery Plans
Maintaining regular backups of critical data is essential. In the event of a successful exploit that leads to data corruption or loss, having a robust backup and recovery strategy can minimize downtime and data loss.
The Broader Implications for Cybersecurity
The discovery of this Windows UI vulnerability reminds us of the dynamic nature of cybersecurity threats. Even vulnerabilities that appear minor on the surface can be exploited to lead to significant security breaches. The fact that a state-sponsored group is actively using this exploit underscores the evolving threat landscape, where traditional security measures may not be sufficient to counter advanced adversaries.
This situation highlights the need for continuous research and development in cybersecurity. Both public and private sector organizations must collaborate to stay ahead of adversaries, sharing threat intelligence and best practices. Furthermore, the incident emphasizes adopting a multi-layered security approach incorporating prevention, detection, and response capabilities.
Future Outlook and Ongoing Developments
ClearSky Cyber Security has indicated that more detailed information will be released in an upcoming blog post. This forthcoming analysis is expected to provide additional insights into mitigation strategies, the broader impact of the vulnerability, and possibly even technical details that could help security professionals better understand the exploit.
As the story develops, cybersecurity professionals, IT administrators, and end-users are encouraged to stay informed about the latest updates from Microsoft and security researchers. Continuous vigilance and proactive measures are key to preventing exploitation by groups like Mustang Panda and others who may attempt to use this vulnerability as a foothold in otherwise secure systems.
Conclusion
The recent uncovering of a Windows UI vulnerability exploited by Mustang Panda is a stark reminder that even low severity issues can have significant security implications. By manipulating how Microsoft Windows handles file extraction from RAR archives, attackers can hide and execute malicious files without immediate detection. This stealthy technique exemplifies the sophisticated tactics employed by state-affiliated groups and highlights the need for enhanced vigilance and security practices.
Organizations and individual users alike must adopt a proactive approach to cybersecurity—ensuring regular updates, enhanced monitoring, and robust incident response strategies—to mitigate the risks associated with such vulnerabilities. As the cybersecurity landscape evolves, staying informed and prepared remains the best defense against emerging threats.
In conclusion, while MicrosofMicrosoft’s classification of this vulnerability as low severity might suggest a manageable risk, the exploitation techniques used by groups like Mustang Panda reveal that the threat can be far more insidious. Ongoing vigilance, user education, and timely software updates will safeguard systems against this and other evolving cybersecurity threats. Stay tuned for further updates and detailed mitigation guidance as more information becomes available from ClearSky Cyber Security and Microsoft.