Are you aware of China Hackers Exposed for US treasury breach? Recently, Microsoft threat hunters revealed alarming insights about a significant change in tactics by Silk Typhoon—a Chinese government-backed espionage group known for its high-profile hacks, including the breach of the US Treasury. This blog post dives deep into the evolving strategies of the Silk Typhoon, examines how these tactics affect the global IT supply chain and offers practical guidance on how organizations can bolster their security defenses.
China Hackers Exposed: The IT Supply Chain
Traditionally, cyber espionage groups have targeted high-profile targets like cloud service providers and critical infrastructure. However, Microsoft’s latest findings indicate that the Silk Typhoon is now directing its efforts toward a less conspicuous yet equally dangerous target: companies within the global IT supply chain. This includes IT services, remote monitoring and management firms, and managed service providers.
By attacking these organizations, Silk Typhoon can infiltrate downstream customer environments. Once inside, the group conducts extensive reconnaissance and gathers sensitive information, paving the way for lateral movement across networks. This shift in focus signifies a broader and more insidious risk: any organization, regardless of size, that relies on commonly used IT solutions without rigorous security protocols is potentially vulnerable to their methods.
The Anatomy of a Cyber Espionage Operation

Silk Typhoon’s operations exemplify modern cyber espionage’s complexity and multi-layered nature. Rather than directly targeting flagship cloud platforms, the group opts for indirect methods to infiltrate organizations. This strategy involves exploiting stolen API keys and compromised credentials to gain initial access. Once inside, attackers use various tools to maintain persistence and extract valuable data.
Exploiting Stolen Credentials and API Keys
One of Silk Typhoon’s core techniques is the abuse of stolen API keys and credentials. API keys are unique identifiers that grant applications or services access to specific functionalities. When these keys are compromised, attackers can bypass many traditional security controls, gaining unauthorized access to sensitive systems. The credentials breach means attackers can move seamlessly between systems, extending their reach within an organization’s network.
Advanced Reconnaissance and Lateral Movement
After establishing an initial foothold, Silk Typhoon employs extensive reconnaissance to map out the network architecture. They systematically search for sensitive data, identify key assets, and uncover vulnerabilities that could be exploited further. This reconnaissance is not limited to the compromised organization’s immediate network; the group also leverages multi-tenant applications to traverse different customer environments. Their ability to perform lateral movement—spreading from one network segment to another—illustrates a deep understanding of both on-premises and cloud infrastructures.
The Use of Sophisticated Tools
Microsoft’s threat intelligence documentation highlights that Silk Typhoon is adept at exploiting various tools. For instance, the group has been known to abuse Microsoft’s Entra Connect (formerly AADConnect) to escalate privileges within victim networks. In addition, they deploy a variety of web shells—scripts that allow remote access—to execute commands, maintain persistent access, and exfiltrate data. These web shells are often concealed within seemingly benign system processes, making them difficult to detect with traditional security measures.
Historical Context and Notable Exploits
Silk Typhoon is not a newcomer to the cyber espionage scene. Historically, the group has been linked to several high-impact breaches, targeting systems central to business operations. Past attacks have compromised Microsoft Exchange servers, VPN products, and firewall appliances—critical components that protect organizational networks.
One of the most notable incidents involved the US Treasury Department. In that breach, Silk Typhoon spied on sensitive financial and political information and exploited vulnerabilities in popular software solutions like BeyondTrust and PostgreSQL. These incidents underscore the group’s ability to identify and exploit weaknesses across various platforms, from legacy systems to modern cloud-based environments.
The Shift Toward IT Supply Chain Attacks
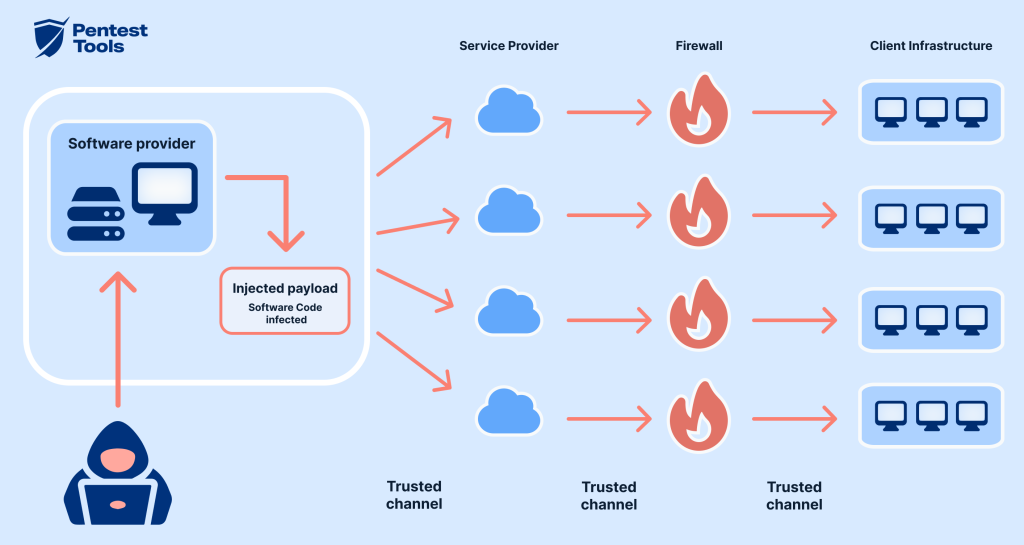
The recent pivot toward targeting the IT supply chain marks a significant evolution in the group’s operational strategy. By infiltrating companies that provide essential IT services, Silk Typhoon gains indirect access to the networks of numerous downstream clients. This “supply chain” approach is hazardous because it leverages trusted relationships between service providers and customers.
How Supply Chain Attacks Work
In a typical supply chain attack, threat actors compromise a less secure vendor or partner to infiltrate a more secure organization. IT, managed service providers (MSPs), and remote monitoring firms often have privileged access to their clients’ environments. Targeting these entities allows attackers to bypass many traditional security measures that would otherwise protect direct, high-profile targets like cloud service providers.
Broader Implications for Businesses
The implications of such attacks are far-reaching. Organizations that depend on third-party IT services are exposed to additional risks. A single compromised service provider can become a conduit for a large-scale breach affecting multiple clients across different industries. This interconnected nature of modern IT ecosystems means that a vulnerability in one supply chain link can have cascading effects throughout the entire network.
Techniques and Tactics: A Closer Look at the Attack Vectors
Microsoft’s researchers have identified several key techniques employed by Silk Typhoon, each designed to enhance the group’s ability to infiltrate and exploit victim environments.
Password Spray Attacks and Credential Theft
Silk Typhoon has been observed using password spray attacks, where attackers attempt to access multiple accounts using a small set of common passwords. These attacks become even more potent when combined with reconnaissance techniques that harvest leaked credentials from public repositories (such as GitHub). In some cases, the group could authenticate to corporate accounts using passwords that had been inadvertently exposed, highlighting the critical need for robust password hygiene and secure storage practices.
Abuse of Service Principals and OAuth Applications
Another significant tactic involves the abuse of service principals and OAuth applications. Many organizations rely on these applications to manage access and facilitate data sharing between services. Silk Typhoon exploits these trusted applications to perform unauthorized data exfiltration—specifically targeting email systems, OneDrive, and SharePoint. By infiltrating these platforms via Microsoft Graph API, the attackers can extract vast amounts of sensitive data without raising immediate alarms.
Multi-Tenant Application Compromise
In today’s cloud-driven environment, multi-tenant applications are crucial in managing resources across different users and organizations. However, this same convenience can be exploited by threat actors. By compromising multi-tenant applications, Silk Typhoon gains access to not just one but several tenants. This allows the group to move laterally across different networks, accessing additional resources and exfiltrating data from multiple environments. In cases where the compromised application had privileges to interact with the Exchange Web Services (EWS) API, the group could specifically target email data—a treasure trove of sensitive information.
Understanding the Broader Cybersecurity Implications

The actions of the Silk Typhoon serve as a stark reminder of the evolving nature of cyber threats. Their ability to pivot strategies and exploit supply chain vulnerabilities illustrates that no organization is immune to attack. This is particularly true for companies that operate in environments where IT solutions and services are interconnected across multiple platforms.
The Challenge of Modern IT Environments
A complex mix of on-premises systems, cloud services, and third-party applications characterizes modern IT environments. This interconnectedness, while offering significant operational efficiencies, also creates multiple entry points for potential attackers. Organizations must maintain robust security across all these touchpoints. Traditional security measures may no longer be sufficient to detect and mitigate the sophisticated tactics employed by advanced threat actors like the Silk Typhoon.
The Role of Zero-Day Exploits
One of the most concerning aspects of Silk Typhoon’s capabilities is its readiness to exploit zero-day vulnerabilities—security flaws unknown to the software vendor and with no available patch. With one of the largest targeting footprints among Chinese threat actors, the group is well-resourced and constantly monitors for any new vulnerabilities. This means that organizations must be proactive in their security posture, continuously updating and patching their systems to mitigate the risk of zero-day exploits.
Strengthening Defenses: Recommendations for Organizations
In light of these emerging threats, organizations must adopt a multi-layered security strategy that addresses the unique challenges of modern IT environments. Here are several recommendations to help mitigate the risks associated with advanced supply chain attacks.
1. Enhance Credential Management
Given the role of stolen API keys and compromised credentials in recent Silk Typhoon operations, it is imperative to adopt robust credential management practices. Organizations should enforce multi-factor authentication (MFA), rotate passwords regularly, and implement strict access controls to minimize the risk of credential theft.
2. Implement Continuous Monitoring and Threat Detection
Continuous monitoring of network activity is critical for detecting suspicious behavior early on. Advanced threat detection systems can help identify anomalies, such as unusual access patterns or unauthorized data exfiltration, allowing security teams to respond promptly. Additionally, organizations should invest in security information and event management (SIEM) systems to correlate data from multiple sources and provide a comprehensive view of the security landscape.
3. Secure Third-Party Relationships
As supply chain attacks become more common, it is essential to ensure that third-party vendors and service providers adhere to stringent security standards. Regular audits, security assessments, and the implementation of vendor risk management programs can reduce the risk of compromise from external partners. Organizations should also establish clear protocols for monitoring and managing third-party access to sensitive data.
4. Patch Management and Software Updates
A timely and efficient patch management process is vital to protect against known vulnerabilities. Organizations must ensure that all software, including legacy systems and third-party applications, is updated with the latest security patches. This is particularly important given the threat actors’ propensity to exploit vulnerabilities in widely used software products.
5. Employee Training and Awareness
Human error remains one of the leading causes of security breaches. Continuous training and awareness programs can equip employees to recognize phishing attempts, suspicious activities, and other threats. By fostering a culture of security awareness, organizations can significantly reduce the risk of successful cyberattacks.
6. Adopt a Zero-Trust Security Model
The traditional perimeter-based security model is no longer sufficient in today’s threat landscape. A zero-trust approach—where every access request is treated as potentially hostile—can help mitigate the risks associated with lateral movement and unauthorized access. This model involves strict identity verification, granular access controls, and continuous trust validation across all network interactions.
Future Outlook: Staying Ahead of Evolving Threats
The cyber threat landscape is constantly evolving, and threat actors like Silk Typhoon are continually refining their tactics. As organizations transition more of their operations to cloud-based environments and integrate third-party solutions, the need for proactive cybersecurity measures becomes even more critical.
Security teams must remain vigilant, constantly monitoring emerging threats and adapting their defenses to counter new attack vectors. Collaboration between industry stakeholders, government agencies, and cybersecurity experts is essential to develop strategies that effectively neutralize sophisticated adversaries. In addition, investing in advanced research and development to improve threat detection and response capabilities will be key to staying ahead of these rapidly evolving risks.
Conclusion
Silk Typhoon’s shift in tactics to target the IT supply chain clearly indicates cyber espionage groups’ changing priorities. By leveraging stolen API keys, compromised credentials, and sophisticated lateral movement techniques, the group poses a significant threat to organizations across various industries. The evolving nature of these attacks serves as a wake-up call for businesses to reassess their security strategies and invest in robust defenses that address both traditional and emerging vulnerabilities.
Organizations must embrace a proactive, multi-layered approach to cybersecurity, encompassing enhanced credential management, continuous monitoring, secure third-party relationships, timely patching, and comprehensive employee training. Adopting a zero-trust security model can further mitigate the risks of advanced threat actors, ensuring that every access point is scrutinized and protected.
In an era where cyber threats are increasingly complex and far-reaching, staying informed and vigilant is more critical than ever. The insights provided by Microsoft’s threat intelligence team highlight the dangers posed by groups like the Silk Typhoon and the opportunities for organizations to strengthen their defenses. By understanding the tactics employed by these sophisticated adversaries and implementing robust security measures, businesses can better protect their assets and maintain the trust of their customers in an ever-evolving digital landscape.
More at:




