Microsoft recently disclosed that a critical security flaw in the Windows Common Log File System (CLFS) was exploited as a zero-day in targeted ransomware campaigns. The vulnerability, which has since been patched, enabled threat actors to gain SYSTEM-level privileges, thereby facilitating further malicious activities. This article provides an in-depth analysis of the incident, explains the technical details behind the vulnerability, and offers guidance on how organizations can better protect themselves against similar attacks.
Overview of the PipeMagic Trojan and Its Impact
What is CVE-2025-29824?
CVE-2025-29824 is a privilege escalation vulnerability in the Windows Common Log File System (CLFS) driver. This vulnerability allowed attackers to bypass security restrictions and elevate their access level to SYSTEM privileges. SYSTEM privileges represent the highest level of access within Windows, granting complete control over the system. By exploiting this flaw, cybercriminals could perform various unauthorized actions, including process injection, credential theft, and file encryption.
The Significance of a Zero-Day Exploit
A zero-day exploit takes advantage of a previously unknown vulnerability before a patch is available or users know the risk. In this case, the exploitation of CVE-2025-29824 was used as a zero-day, meaning that organizations were caught off guard. Zero-day vulnerabilities are particularly dangerous because they allow attackers to infiltrate systems before any defensive measures can be implemented.
Patch Tuesday and the Response from Microsoft
Microsoft patched the vulnerability in April 2025 as part of its regular Patch Tuesday update. Patch Tuesday is a monthly event where Microsoft releases updates to address various security issues. In this instance, the update was crucial for mitigating the risk posed by the zero-day exploit. Despite the prompt response, the fact that the vulnerability had already been exploited underscores the constant need for vigilance in cybersecurity.
Detailed Analysis of the Exploit Mechanism
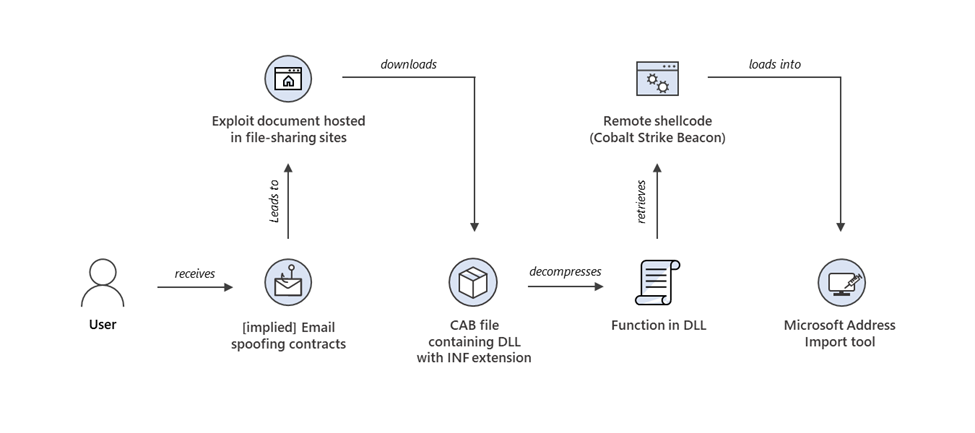
The Role of the CLFS Kernel Driver
The Windows Common Log File System is an integral component for managing log files within Windows. The flaw in the CLFS kernel driver allowed attackers to manipulate system processes—specifically, the exploit utilized memory corruption techniques with the RtlSetAllBits API. By overwriting the token associated with the exploit process, the attackers set the token value to 0xFFFFFFFF. This action granted the process every possible privilege, enabling it to inject code into critical SYSTEM processes.
How the Exploit is Delivered
The attackers behind the zero-day exploit have been linked to targeted ransomware attacks. Their operational tactics involve several sophisticated steps:
- Initial Access: Although the precise initial access vector remains unknown, investigators have observed using the certutil utility. Certutil, a legitimate Windows utility, was repurposed by threat actors to download malware from a compromised third-party website. This technique helped them stage the subsequent payloads without immediate detection.
- Malicious MSBuild Files: The downloaded malware was packaged as a malicious MSBuild file. MSBuild is a Microsoft build engine used to compile applications, and its abuse in this context demonstrates the attackers’ deep understanding of legitimate system tools. The MSBuild file contained an encrypted payload that, once unpacked, launched the malicious component known as PipeMagic Trojan.
The PipeMagic Trojan Family
PipeMagic Trojan is a plugin-based trojan that has been detected in various malicious activities since 2022. In this particular series of attacks, PipeMagic Trojanwas used as a delivery mechanism for the exploit and subsequent ransomware payloads. This malware is modular, meaning that it can be updated or reconfigured easily by threat actors to suit different attack scenarios. Prior incidents have linked PipeMagic to other notable vulnerabilities, including CVE-2025-24983 and CVE-2023-28252, involving privilege escalation in Windows systems.
Sectors and Regions Impacted by the Attack
A Diverse Range of Targeted Industries
Microsoft’s disclosure highlighted that the ransomware attacks affected organizations across various industries and regions. The targeted sectors include:
- Information Technology and Real Estate in the United States: Attackers have specifically aimed at companies within these sectors, possibly exploiting the interconnected nature of IT systems in both industries.
- Financial Institutions in Venezuela: Financial entities often represent high-value targets due to their data’s sensitive and valuable nature.
- Software Companies in Spain: The choice of a Spanish software company indicates that geographical boundaries do not limit threat actors and that the company is prepared to target organizations across different continents.
- Retail Sector in Saudi Arabia: With its extensive customer data and financial transactions, the retail industry presents lucrative opportunities for ransomware criminals.
The Global Nature of Cyber Threats
The fact that attackers have breached organizations in multiple sectors and regions illustrates the global threat posed by such vulnerabilities. Cybercriminals operate with international reach, leveraging vulnerabilities in widely used software like Windows to propagate their attacks. This transnational aspect emphasizes the need for a coordinated global response to cybersecurity threats and the importance for organizations to stay informed about the latest security advisories.
The Threat Actor’s Tactics, Techniques, and Procedures (TTPs)
Tracking and Attribution Efforts
Microsoft has been actively tracking the post-compromise exploitation of CVE-2025-29824 under the moniker Storm-2460. This designation helps cybersecurity professionals and incident responders understand the tactics and tools employed by the threat actors. Tracking such groups is critical for anticipating future moves and developing appropriate defence mechanisms.
Utilizing Certutil and Compromised Third-Party Sites
One notable technique involves the use of the certutil utility. By leveraging this legitimate tool, threat actors could stealthily download their malicious payloads from a previously compromised third-party site. This method highlights the dual-use nature of many administrative tools, which can be turned against organizations when proper safeguards are not in place.
The Use of Custom Modular Backdoors
In addition to PipeMagic Trojan, some attacks involved a custom modular backdoor. This backdoor is designed to persist on the victim’s machine and facilitate further exploitation. For example, Kaspersky researchers noted in previous investigations that victims’ machines were first infected with this modular backdoor before the CLFS elevation-of-privilege vulnerability was exploited. The backdoor’s modularity allows it to be easily updated with new functionalities, making it a versatile tool for cybercriminals.
Technical Details Behind the Exploit Process
Memory Corruption and Token Overwriting
At the heart of the exploitation process lies a technique involving memory corruption. By exploiting the vulnerability in the CLFS driver, attackers could manipulate memory allocation and process tokens. The RtlSetAllBits API was used to overwrite the exploit process’s token with the value 0xFFFFFFFF. This action granted the process all possible privileges, bypassing standard security checks and enabling unauthorized process injection.
Post-Exploitation Activities
Once the exploitation was successful, the threat actors moved quickly to consolidate their foothold on the compromised systems. The subsequent steps in the attack included:
- Credential Theft: Attackers extracted user credentials by dumping the memory of the Local Security Authority Subsystem Service (LSASS). LSASS is responsible for enforcing the security policy on Windows systems, and its memory dump can reveal sensitive information such as passwords and other authentication tokens.
- Ransomware Deployment: With privileged access secured, attackers encrypt files on the victim’s systems. Files were encrypted with a random extension, a common tactic in ransomware attacks that makes it difficult for victims to identify which files have been targeted. The encryption process is typically accompanied by a ransom note, which includes a TOR domain associated with the RansomEXX ransomware family.
Understanding the RansomEXX Connection
How RansomEXX Operates
RansomEXX is one of the many ransomware families that have emerged in recent years. Like other ransomware variants, it encrypts critical data and demands payment for decryption keys. The association with a TOR domain in the ransom note indicates an effort by the attackers to remain anonymous and provide a secure channel for ransom negotiations.
The Importance of Privilege Escalation in Ransomware
Microsoft has noted that ransomware threat actors place a high value on post-compromise privilege escalation. Achieving SYSTEM privileges allows them to move laterally within networks and maximize the impact of their ransomware campaigns. This level of access not only facilitates widespread deployment of the ransomware but also increases the difficulty of recovery for affected organizations.
Security Recommendations and Best Practices
Patch Management and Regular Updates
The most immediate lesson from the exploitation of CVE-2025-29824 is the importance of timely patch management. Organizations must prioritize applying security updates as soon as they are released. Microsoft’s Patch Tuesday updates are critical to maintaining security posture in Windows environments. Regular patching helps mitigate the risks associated with zero-day exploits and other vulnerabilities.
Hardening Administrative Tools and Access
Given the attackers’ use of tools like certutil and MSBuild, organizations should review and restrict the use of administrative utilities. Limiting access to such tools to only trusted administrators can reduce the risk of them being misused by threat actors. Additionally, monitoring and logging these utilities can help detect suspicious activities early on.
Employing Advanced Threat Detection Techniques
Organizations should implement advanced threat detection and response systems to counter sophisticated threats. Behaviour-based detection, anomaly monitoring, and endpoint detection and response (EDR) solutions can warn early about unusual activities, such as exploiting privilege escalation vulnerabilities or unauthorized memory dumps. Investing in such technologies is vital for reducing the exposure window during an attack.
Network Segmentation and Least Privilege
Another key security practice is implementing network segmentation and the principle of least privilege. By restricting the movement of attackers within the network, organizations can limit the potential damage from a compromised system. Segmentation ensures that critical assets remain protected even if one part of the network is breached. Similarly, enforcing the least privilege ensures that users and applications only have the access necessary for their roles, reducing the risk of privilege escalation.
The Role of Cybersecurity Vendors and Research Firms
Contributions from Industry Experts
The cybersecurity community, including vendors such as Kaspersky and ESET, has played a crucial role in identifying and mitigating threats like those associated with PipeMagic Trojan. Researchers from these organizations have provided insights into the evolution of the malware and its connection to earlier vulnerabilities, such as CVE-2025-24983 and CVE-2023-28252. Their findings have been instrumental in understanding how threat actors leverage known vulnerabilities to craft new attack vectors.
Collaboration Between Security Firms and Microsoft
Collaboration between security researchers and software vendors is essential for a timely and effective response to emerging threats. Microsoft’s proactive tracking of the Storm-2460 group and input from independent cybersecurity firms have enabled a more comprehensive understanding of the threat landscape. Such partnerships facilitate information sharing that can lead to faster identification of vulnerabilities and the development of robust mitigation strategies.
Addressing Concerns for Windows 11 Users
Impact on Windows 11, Version 24H2
One point of relief for many users is that this exploitation does not affect Windows 11, version 24H2. This is because of the access restrictions imposed on specific System Information Classes within the NtQuerySystemInformation API. These restrictions require that a user have SeDebugPrivilege, a privilege typically reserved for administrative accounts. This design choice adds an extra layer of protection, ensuring that even if attackers gain access to a non-privileged account, they are unlikely to exploit the CLFS vulnerability on these systems.
Continued Vigilance for All Windows Users
Despite this exemption, all Windows users need to remain vigilant. Cyber threats continue to evolve, and attackers are constantly developing new techniques to bypass even the most robust security measures. Regular updates, adherence to best practices, and user education remain the cornerstone of a secure computing environment.
Lessons Learned and Future Outlook
The Evolving Nature of Ransomware Threats
The exploitation of CVE-2025-29824 reminds us that attackers are increasingly sophisticated in their methods. The ability to repurpose legitimate tools for malicious purposes and the modular nature of malware like PipeMagic Trojan underscores the dynamic and ever-changing landscape of ransomware threats. As cybercriminals continue to innovate, organizations must adapt by enhancing their defensive measures and remaining informed about the latest developments.
Proactive Defense Strategies
Organizations should invest in proactive defence strategies, including regular security assessments, penetration testing, and threat-hunting exercises. These measures can help identify potential vulnerabilities before they are exploited. By adopting a proactive rather than reactive approach, organizations can significantly reduce the risk of falling victim to advanced persistent threats (APTs) and other cyber attacks.
Importance of Cybersecurity Training and Awareness
A crucial element in combating cyber threats is the training and education of employees. Many successful attacks begin with social engineering or insiders’ misuse of administrative tools. Comprehensive cybersecurity training programs can equip employees with the knowledge to recognize suspicious activities, follow secure practices, and report potential threats promptly. An informed workforce is a powerful asset in the fight against cybercrime.
Conclusion
Microsoft’s recent disclosure about the zero-day exploitation of a CLFS vulnerability highlights the persistent threats organizations face and the evolving techniques employed by cybercriminals. The exploitation of CVE-2025-29824 allowed threat actors to gain SYSTEM privileges and paved the way for subsequent malicious activities, including credential theft and ransomware deployment. While the patch released during April 2025’s Patch Tuesday update has mitigated this specific vulnerability, the incident is a stark reminder of the importance of a multi-layered cybersecurity strategy.
This targeted campaign affected organizations across various sectors—from IT and real estate in the United States to financial institutions in Venezuela, software companies in Spain, and retail entities in Saudi Arabia. The global nature of the attack emphasizes the need for coordinated defensive measures and ongoing vigilance in today’s interconnected world.
Sources: Galileo, Techradar, The Hacker News