The cybersecurity landscape is constantly evolving, as are the tools and resources that security professionals rely on to protect their organizations. One of the most critical components in this ecosystem is the CVE (Common Vulnerabilities and Exposures) database. For more than two decades, the CVE database has served as a centralized repository that helps teams across the globe track vulnerabilities and implement timely fixes. In this blog post, we will explore the history of the CVE database, the recent changes in its funding and management, and the potential implications for the cybersecurity community. We will also discuss alternative solutions and consider the broader impact of relying on a single source for vulnerability data.
Background of the CVE Database
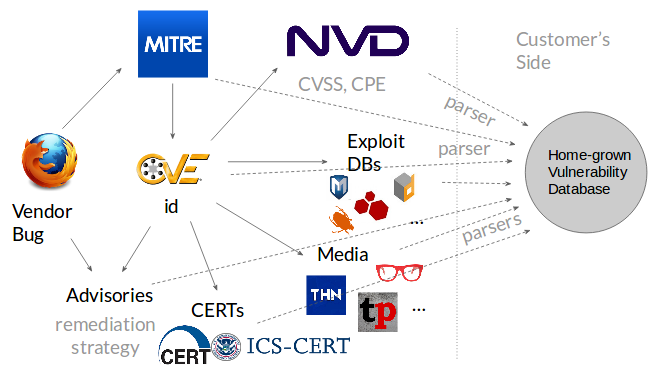
The Origins and Evolution of CVE
The CVE program was established 25 years ago to create a common identifier for publicly known cybersecurity vulnerabilities. By standardizing the naming of these vulnerabilities, the program has enabled cybersecurity professionals to communicate more effectively about security issues. Over the years, the database has grown in size and importance, becoming a cornerstone for numerous cybersecurity tools and services. Its structured approach has allowed teams to build efficient pipelines that rapidly respond to security challenges, a crucial capability in today’s threat environment.
MITRE’s Role and Contributions
The non-profit organization MITRE has been at the helm of the CVE program since its inception. MITRE’s stewardship has ensured the database’s reliability and comprehensiveness and built a foundation of trust within the cybersecurity community. By continuously updating and refining the database, MITRE has enabled DevSecOps teams to quickly implement fixes, ultimately contributing to a safer digital ecosystem. MITRE’s commitment to maintaining high-quality, accessible vulnerability data has been essential to the success and widespread adoption of the CVE program.
Recent Developments and Funding Changes
Announcement of Funding Changes
In a surprising development, MITRE recently announced that its contract with the US Department of Homeland Security (DHS) to operate the CVE program has not been renewed. This decision has raised concerns throughout the cybersecurity industry, as the absence of renewed funding could seriously affect the program’s future. According to a leaked letter posted on BlueSky’s social media platform, MITRE Vice President Yosry Barsoum confirmed that the US government funding for the CVE database and the Common Weaknesses Enumeration (CWE) programs would expire. This news has sparked a debate about the sustainability of a system integral to cybersecurity for so long.
Industry Reactions and Expert Opinions
The potential loss of this critical resource has generated considerable discussion among cybersecurity experts. Matt Saunders, DevOps lead at The Adaptavist Group, emphasized the CVE database’s significant role in building reliable and efficient security pipelines. He warned that securing software could become more challenging without the database’s centralization and dependability. Likewise, Kevin Robertson, CTO of Acumen Cyber, described the withdrawal of funding as “a tragic blow for the cybersecurity industry.” He pointed out that MITRE’s program is the most widely used CVE database, and finding a comprehensive alternative would be no easy task.
Chris Burton, head of professional services at Pentest People, offered a more measured perspective, suggesting that while the funding withdrawal is alarming, it could also be seen as an opportunity. Burton speculated that if the issue were solely financial, alternative funding methods such as crowdfunding might help rally public support for the project. He also noted the possibility of establishing a dedicated community board to oversee the program’s operation, thus ensuring that the resource remains available despite changes in its financial backing.
The Importance of the CVE Database

A Critical Resource for Cybersecurity
The CVE database is more than just a list of vulnerabilities; it is a vital tool for the cybersecurity community. Organizations worldwide depend on the database to identify and remediate security issues swiftly. The database facilitates communication among security professionals, vendors, and researchers by providing standardized identifiers. This standardized approach is essential for ensuring all stakeholders are on the same page when addressing security threats.
Moreover, the CVE database’s comprehensive nature means that it covers a wide range of vulnerabilities, from minor software bugs to critical security flaws. This breadth of information makes the database indispensable for maintaining robust cybersecurity defences. The centralization of vulnerability data simplifies the process of tracking issues and helps develop automated systems that can quickly deploy patches and updates.
The Role of CVE in DevSecOps Pipelines
Modern cybersecurity strategies increasingly rely on DevSecOps, which integrates security practices within the DevOps process. The CVE database plays a crucial role in these pipelines, enabling teams to quickly identify vulnerabilities and implement fixes. With the CVE program as a foundation, automated systems can scan code, detect issues, and trigger alerts, ensuring that vulnerabilities are addressed before they can be exploited. This rapid response capability is a cornerstone of effective cybersecurity and is one of the many reasons the potential loss of CVE funding is causing concern.
Potential Implications of the Funding Change
Impact on Global Cybersecurity
The decision not to renew the funding contract has raised several important questions about the future of the CVE program. One of the most pressing concerns is the potential impact on global cybersecurity. If the CVE database were to lose its centralized management, the entire industry could face significant challenges. The consistency and reliability of the vulnerability data might be compromised, leading to delays in identifying and fixing security issues. For organizations that rely on the CVE database, this could mean increased risk and reduced efficiency in their cybersecurity operations.
The Risk of Centralization
While centralizing vulnerability data has been a strength of the CVE program, it is also a potential point of vulnerability. Relying on a single source for such critical information could become problematic if that source experiences any disruptions. The recent funding changes highlight the inherent risks of depending on a single organization for a resource vital to the industry. This situation serves as a wake-up call for cybersecurity professionals to consider the potential consequences of centralized systems and explore alternative models offering greater resilience.
The Possibility of Private Sector Involvement
With the government stepping back from funding, there is speculation that major players in the global cybersecurity industry may step in to fill the void. This could involve one of the large cybersecurity companies taking over the management of the CVE database or a consortium of private entities coming together to fund and maintain the resource. While private sector involvement could bring additional resources and expertise, it raises concerns about control and neutrality. The cybersecurity community will need to carefully consider how best to balance the benefits of private funding with the need to maintain an open and unbiased source of vulnerability information.
Alternative Solutions and Future Directions

Exploring Vendor-Specific Databases
Without the MITRE-managed CVE database, organizations may turn to alternative sources for vulnerability information. Some companies already maintain their vendor-specific vulnerability databases, which can serve as a temporary stopgap. However, these databases often lack the comprehensiveness and standardization of the CVE program. While they may provide valuable insights for specific products or services, relying solely on these alternatives could create fragmentation in how vulnerabilities are identified and addressed across different sectors.
The National Vulnerability Database as an Alternative
Another potential alternative is the National Vulnerability Database (NVD), which provides detailed information about known vulnerabilities. The NVD is a valuable resource but is not as streamlined or user-friendly as the MITRE-managed CVE database. Additionally, the NVD may not comprehensively cover the full spectrum of vulnerabilities, making it less effective as a singular source of truth for cybersecurity professionals. For organizations that have built their security pipelines around the CVE program, transitioning to the NVD or other databases could require significant adjustments and retooling.
Crowdfunding and Community Governance
An emerging idea in response to the funding crisis is the concept of crowdfunding and community governance. As Chris Burton suggested, rallying public support through crowdfunding could provide a new financial model for sustaining the CVE program. This approach would involve engaging a broad base of stakeholders—ranging from individual cybersecurity enthusiasts to large organizations—to contribute funds and participate in the governance of the database. A dedicated community board could oversee operations, ensuring the resource remains independent and widely accessible. While still untested on a large scale, this model offers an intriguing alternative to traditional government or private sector funding.
The Role of Open Source Collaboration
The world of cybersecurity has long benefited from the principles of open-source collaboration. The CVE database, in many ways, embodies these principles by providing a freely accessible resource that anyone can use. In the wake of the funding change, there is an opportunity to reinvigorate the open-source model by encouraging more collaborative efforts. By leveraging the collective expertise of the global cybersecurity community, it may be possible to develop new tools and frameworks that complement or even replace the existing CVE database. This approach could lead to a more resilient system that is less susceptible to disruptions in funding or management.
The Broader Context of Cybersecurity Funding
Government and Private Sector Roles
The recent funding changes for the CVE database highlight the complex relationship between government support and private sector involvement in cybersecurity. Historically, government funding has played a critical role in establishing foundational resources like the CVE program. However, as the digital landscape has evolved, the private sector has increasingly taken on responsibilities that were once the exclusive domain of government agencies. This shift raises important questions about how best to fund and manage essential cybersecurity resources. The challenge lies in finding a balance that ensures the continued availability of high-quality data while fostering innovation and adaptability in the face of emerging threats.
International Implications
Cybersecurity is a global concern, and the effects of changes to the CVE database will be felt worldwide. Organizations in every corner of the globe rely on accurate and timely vulnerability information to protect their systems. Any disruption in the CVE program could have far-reaching consequences, potentially affecting international collaboration and threat intelligence sharing. As discussions about the future of the CVE database continue, it will be important for global stakeholders to work together to develop a sustainable model that benefits the cybersecurity community. This could involve new international partnerships or agreements that help ensure the stability and reliability of vulnerability data.
Preparing for the Future

Rethinking Vulnerability Management
The current situation presents a unique opportunity for the cybersecurity community to rethink how vulnerabilities are managed and communicated. The industry’s reliance on a single, centralized database has served it well for many years, but it also exposes organizations to certain risks. By exploring alternative models—whether through vendor-specific databases, the NVD, or a community-governed platform—the industry can build a more robust and diversified system. This diversification could improve vulnerability management’s speed and accuracy, resulting in better protection against cyber threats.
The Need for Innovation and Adaptation
The digital threat landscape is continually changing, and cybersecurity strategies must evolve accordingly. The funding challenges facing the CVE database underscore the need for constant innovation. Cybersecurity professionals must be prepared to adapt to new funding models, governance structures, and technological advancements. Embracing innovative solutions—such as automated vulnerability detection tools and collaborative open-source projects—will be critical for maintaining the momentum of progress in cybersecurity. This period of uncertainty can catalyze change, encouraging the industry to develop more resilient systems capable of withstanding future challenges.
Conclusion
The future of the CVE database is at a crossroads. With uncertain government funding and the prospect of transitioning to a model that relies on private sector contributions or community governance, the cybersecurity world faces challenges and opportunities. The CVE database has long been a dependable resource that has enabled rapid responses to vulnerabilities and has supported the development of robust security pipelines. Its importance cannot be overstated, and any changes to its management will have significant implications for the global cybersecurity community.
As we navigate this transition period, we must recognize the potential risks of relying on a single centralized source of vulnerability data. At the same time, this moment also offers a chance to innovate and explore new models for vulnerability management. Whether through crowdfunding, enhanced international cooperation, or the adoption of new technologies, the path forward will require a collaborative effort from all stakeholders.
The cybersecurity industry must remain vigilant and proactive, ensuring that the loss of government funding does not lead to a decline in the quality or accessibility of vulnerable data. Instead, it should serve as a call to action—an opportunity to build a more resilient, diverse, and sustainable system that continues to protect organizations from cyber threats. By embracing change and working together, the cybersecurity community can turn this challenge into a stepping stone for future innovation and enhanced security.
Sources: Apple Insider, Security Boulevard, Betanews







