In an era where cyber threats evolve at breakneck speed and digital transformation reshapes how organizations operate, traditional perimeter-based security models are no longer sufficient. Companies increasingly rely on cloud services, remote workforces, mobile devices, and third‑party integrations, all of which expand the attack surface. In response, the zero trust security model has emerged as a paradigm shift that fundamentally rethinks how we secure networks, assets, and data.
Rather than implicitly trusting users or devices based on their location inside a network perimeter, zero trust enforces continuous verification and granular access controls at every interaction. This blog explores the origins, principles, components, and real‑world benefits of zero trust security, and provides guidance on how your organization can adopt this forward‑looking strategy.
Understanding Zero Trust Security

Origins and Evolution
The concept of zero trust dates back to 2010, when Forrester Research analyst John Kindervag introduced the term “zero trust” in response to limitations of castle-and-moat security architectures. Traditional models assume that everything inside an organization’s network is inherently trustworthy, leading to insufficient protection against insider threats or attackers who have already breached the perimeter. Zero trust dispenses with implicit trust altogether, adopting the mantra “never trust, always verify.” Over the past decade, leading security vendors, government agencies, and industry standards bodies have embraced and refined zero trust approaches, culminating in NIST’s Special Publication 800‑207, which codifies zero trust architecture principles and guidance.
Core Principles of Zero Trust
At its heart, zero trust is guided by four interrelated principles. First, continuous authentication and authorization require every user and device to be authenticated and authorized before accessing any resource, regardless of location. Second, least privilege access ensures users and devices can only reach the specific resources they need to perform their roles, minimizing lateral movement. Third, microsegmentation divides networks and applications into fine‑grained zones, containing breaches and preventing unrestricted east‑west traffic. Fourth, visibility and analytics provide real‑time monitoring of all transactions, anomaly detection, and risk‑based policy adjustments. These principles work in concert to establish dynamic, context‑aware security policies that adapt to evolving threats and usage patterns.
Key Components of a Zero Trust Architecture
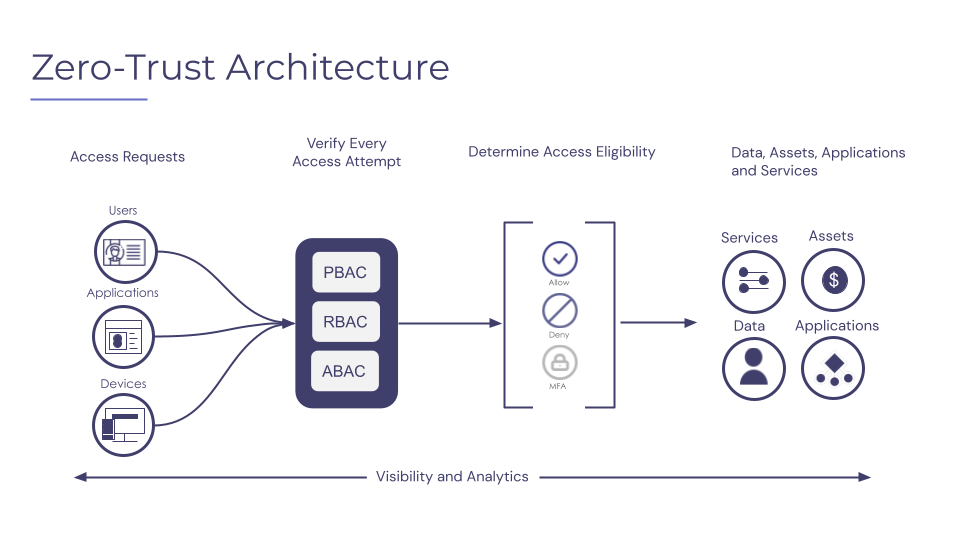
Identity and Access Management
Identity is the new perimeter in a zero trust world. Robust identity and access management (IAM) solutions verify user identities through multi‑factor authentication (MFA), risk‑based step‑up authentication, and strong passwordless methods such as FIDO2/WebAuthn. Privileged access management (PAM) systems further secure administrative accounts by enforcing just‑in‑time privilege elevation and session recording. By integrating IAM with directory services and identity providers, organizations ensure every access request is grounded in a vetted identity context.
Device Security and Endpoint Protection
In zero trust architectures, devices are continuously assessed for security posture, including operating system versions, patch levels, configuration compliance, and the presence of security agents. Endpoint detection and response (EDR) and unified endpoint management (UEM) systems provide telemetry and enforcement, isolating or remediating compromised endpoints before they gain access to critical resources. Devices that do not meet policy requirements can be quarantined or granted only limited, read‑only access.
Network Microsegmentation
Rather than relying on a flat network with a single perimeter firewall, zero trust employs microsegmentation to create isolated network segments around applications, workloads, or data repositories. Software‑defined networking (SDN) and next‑generation firewalls enforce policies that restrict traffic flows to only the minimal ports and protocols needed. This segmentation ensures that an attacker who compromises one segment cannot freely traverse the entire network, dramatically reducing the blast radius of breaches.
Data Protection and Encryption
Zero trust demands that data be protected at rest and in transit through robust encryption mechanisms. Organizations implement granular data classification to identify sensitive information, then apply encryption, tokenization, and digital rights management according to data sensitivity and compliance requirements. Encryption keys are managed through a centralized key management system (KMS) or hardware security modules (HSMs), ensuring the confidentiality and integrity of data even if storage or transmission channels are compromised.
Policy Engine and Orchestration
Central to a zero trust framework is a policy engine that evaluates each access request against a set of dynamic, context‑aware rules. These rules incorporate identity, device posture, location, time of day, behavioral analytics, and threat intelligence to compute an access decision. A policy orchestration layer then ensures consistent policy enforcement across multiple enforcement points, such as gateways, proxies, and endpoint agents. Automation—through security orchestration, automation, and response (SOAR) platforms—accelerates policy updates and incident response, reducing human error and reaction times.
Why Zero Trust Matters
Mitigating Insider Threats
Insider threats—whether malicious or accidental—pose a major risk because legitimate credentials can bypass perimeter defenses. Zero trust’s least privilege and continuous monitoring models significantly reduce the impact of insider actions. By logging every access event and applying real‑time risk scoring, organizations can swiftly detect unusual activities, such as privilege escalations or atypical data transfers, and automatically trigger additional authentication steps or policy changes.
Protecting Cloud and Remote Environments
With a global shift to cloud‐based services and remote work, traditional security perimeters have dissolved. Zero trust naturally accommodates hybrid and multi‑cloud architectures by securing access at the application layer rather than the network edge. Users can connect to cloud resources directly—without backhauling traffic through a corporate VPN—while still subject to strict authentication and policy enforcement. This flexibility enhances user experience and operational agility without sacrificing security.
Meeting Regulatory and Compliance Demands
Regulations such as GDPR, HIPAA, and PCI DSS mandate rigorous controls over personal data and financial information. Zero trust’s granular access controls, detailed audit logs, and strong encryption help organizations demonstrate compliance. By segmenting data and applying least privilege, companies can isolate regulated workloads and minimize the scope of compliance audits. Automated reporting tools further streamline evidence collection and audit readiness.
Reducing the Attack Surface
Zero trust shrinks the attack surface by enforcing minimal access rules and eliminating implicit trust zones. Attackers face friction at every stage: they must compromise valid credentials, bypass multi‑factor controls, breach segmented network enclaves, and overcome dynamic policy checks. This layered approach forces adversaries to expend disproportionate effort, increasing the likelihood of detection before significant damage occurs.
Implementing Zero Trust in Your Organization
Assessing Your Current Security Posture
Before embarking on a zero trust journey, conduct a comprehensive assessment of existing infrastructure, applications, user roles, and data flows. Map critical assets, identify trust boundaries, and catalog identity stores, network segments, and security tools already in place. A clear understanding of the current state reveals gaps, dependencies, and quick-win opportunities for pilot implementations.
Building a Zero Trust Roadmap
Zero trust adoption is a multi‑phase process, not a single project. Begin with high‑value, high‑risk use cases—such as privileged access to sensitive databases or external vendor connections—and apply zero trust controls incrementally. Define milestones, success metrics, and governance structures. Engage stakeholders from security, IT operations, application teams, and business units to ensure alignment on goals, timelines, and resource allocation.
Technology and Tool Selection
A robust zero trust strategy typically integrates multiple technologies: identity providers (IdPs), MFA solutions, endpoint security platforms, microsegmentation tools, secure web gateways (SWGs), and data loss prevention (DLP) systems. When selecting vendors, prioritize interoperability, API‑driven automation, and centralized policy management. Open standards such as SAML, OAuth 2.0, and XACML facilitate integration across cloud and on‑premises environments.
Cultural and Organizational Considerations
Zero trust represents a cultural shift as much as a technical one. It challenges assumptions about trust and access, requiring employees and partners to adapt to new authentication workflows and security checkpoints. Leadership must champion the initiative, communicate benefits clearly, and provide training on secure practices. Establishing a cross‑functional zero trust council helps maintain momentum, resolve policy disputes, and address user experience concerns.
Challenges and Common Pitfalls
Complexity and Integration Overhead
Implementing zero trust can introduce complexity, especially in large organizations with diverse legacy systems. Integrating disparate identity stores, on‑premises applications, and cloud services requires careful planning. Avoid “rip and replace” approaches; instead, use gateways and proxies to retrofit zero trust controls onto existing workloads.
Balancing Security and User Experience
Overly aggressive policies or cumbersome authentication steps can frustrate users and prompt shadow IT workarounds. Strive for adaptive, risk‑based authentication that dynamically adjusts security controls based on contextual factors. User behavior analytics can help fine‑tune policies to minimize friction while preserving robust protection.
Maintaining Visibility and Analytics
Zero trust success hinges on comprehensive telemetry from endpoints, network devices, applications, and identity stores. Overlooking log collection or failing to normalize data streams can leave blind spots. Invest in a scalable security information and event management (SIEM) or extended detection and response (XDR) platform that centralizes logs, applies threat intelligence feeds, and supports automated alerting.
Evolving Threat Landscape
Attackers continuously innovate new tactics ransomware‑as‑a‑service, AI‑driven phishing, and supply chain compromises—that challenge static policy frameworks. Zero trust must be viewed as an ongoing journey, with regular policy reviews, threat modeling exercises, and red team assessments. Embedding security into DevOps pipelines (“DevSecOps”) accelerates updates to policies and detection capabilities.
The Future of Zero Trust Security
As organizations embrace hybrid work, edge computing, and Internet of Things (IoT) deployments, zero trust will extend beyond traditional IT assets to secure everything from factory machinery to smart vehicles. Advances in machine learning and behavioral analytics will enhance risk scoring and enable fully autonomous policy decisions. Standardization efforts, such as the Cloud Security Alliance’s Zero Trust Working Group, will further refine best practices and interoperability guidelines. Ultimately, zero trust will become the de facto architecture for any organization that values agility, resilience, and data protection in the digital age.
Conclusion
Zero trust security is more than a buzzword it is a comprehensive framework for mitigating modern cyber risks by enforcing continuous verification, least‑privilege access, microsegmentation, and real‑time analytics. By embracing zero trust principles, organizations can secure cloud and remote environments, reduce the blast radius of breaches, meet stringent compliance requirements, and elevate their overall security posture.
Although the journey involves technical complexity and cultural change, the long‑term benefits of reduced risk, improved auditability, and enhanced user trust make zero trust an essential strategy for any forward‑thinking enterprise. If your organization has not yet begun its zero trust transformation, there is no better time than now to chart a roadmap and embark on the future of cybersecurity.







