Do you know the key differences about SIEM vs XDR? In today’s cyber threat landscape, detecting and responding to security incidents quickly is more critical than ever. Organizations looking to strengthen their threat detection and response capabilities often consider two powerful technologies: SIEM (Security Information and Event Management) and XDR (Extended Detection and Response). While both serve to identify, monitor, and react to threats, they differ significantly in architecture, scope, and usability. This article explores the key differences between SIEM and XDR, their strengths, limitations, real-world use cases, and which approach may best suit your organization’s needs.
What is SIEM?
Security Information and Event Management (SIEM) is a mature cybersecurity solution that collects and analyzes log data from a wide range of sources, including servers, firewalls, antivirus tools, endpoints, and network devices. SIEM aggregates this information in a central dashboard to help security teams detect anomalies and investigate security incidents.
Key capabilities of SIEM include:
- centralized log management
- real-time event correlation
- rule-based detection
- forensic analysis
- compliance reporting for standards like PCI-DSS, HIPAA, and ISO 27001.
However, SIEM systems are complex to deploy and maintain. They require fine-tuning of alert rules, constant tuning to reduce false positives, and skilled analysts to interpret alerts effectively. Licensing and data storage costs can also be high.
Popular SIEM solutions include Splunk, IBM QRadar, LogRhythm, Microsoft Sentinel, and ArcSight. These platforms are well-suited to large organizations with dedicated SOC teams. These systems are highly customizable, allowing teams to craft specific queries, dashboards, and detection rules tailored to their environment.
Additionally, SIEM plays a critical role in long-term forensic investigations. When a breach occurs, incident responders rely on SIEM logs to reconstruct attacker behavior, identify patient-zero devices, and pinpoint lateral movement within the network. It’s a powerful historical tool that aids in both remediation and reporting.
What is XDR?
Extended Detection and Response (XDR) is a more recent development in cybersecurity designed to unify detection and response across multiple domains, endpoints, networks, cloud workloads, and email through a single, integrated platform. It uses built-in analytics, machine learning, and threat intelligence to provide contextual and actionable insights.
XDR automates data collection and correlation across telemetry sources. It then presents security analysts with prioritized alerts that are easier to understand and act upon. XDR platforms typically include behavioral detection, automatic threat response, and rapid containment capabilities.
Popular XDR platforms include Palo Alto Networks Cortex XDR, Microsoft Defender XDR, CrowdStrike Falcon XDR, Trend Micro Vision One, and SentinelOne Singularity XDR. These are often bundled with endpoint protection and optimized for fast deployment and ease of use.
While XDR platforms are less customizable than SIEMs, they are often more accessible to teams with limited security staff. XDR also improves operational efficiency by reducing alert fatigue through better correlation, threat scoring, and automated playbooks that act on behalf of security teams.
Another advantage of XDR is its out-of-the-box integrations. Many XDR solutions come pre-integrated with threat intelligence feeds, MITRE ATT&CK mappings, and vulnerability data. This reduces the need for manual tuning and supports faster time-to-value.
How SIEM and XDR Differ?
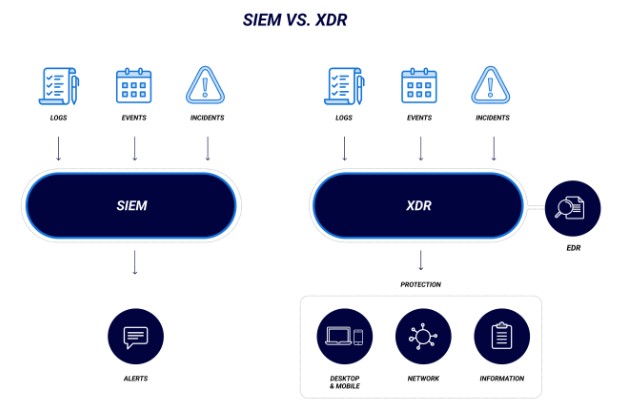
The core difference between SIEM and XDR lies in how they collect data, the depth of customization, and their approach to detection and response.
SIEM acts as a central repository of logs from across the environment. It can correlate any structured log data but often requires heavy tuning. In contrast, XDR platforms are opinionated, and they come with built-in logic and integrate tightly with specific tools, resulting in faster time-to-value and a smoother analyst experience.
XDR emphasizes proactive detection and automated response. SIEM emphasizes visibility, forensics, and compliance.
In terms of deployment, SIEMs are typically heavier, may run on-premises or in hybrid modes, and require more infrastructure management. XDR tools are typically cloud-native and designed for plug-and-play integration. Moreover, XDR’s consolidated interface helps eliminate the data silos that often exist in organizations using separate endpoint, network, and cloud security tools.
When Should You Choose SIEM?
Choose SIEM if your organization:
- Has advanced compliance needs (e.g., for audits or regulatory requirements).
- Operates across many custom systems and requires granular log visibility.
- Has a mature SOC team to manage tuning and threat hunting.
- Needs deep forensics and customizable alert workflows.
- Wants historical data retention for extended periods, sometimes several years.
SIEM is ideal for large enterprises in regulated sectors such as finance, healthcare, and government. Its flexibility allows these organizations to tailor detection rules and alerts based on niche requirements, providing unmatched customization compared to newer platforms.
When Should You Choose XDR?
Choose XDR if your organization:
- Needs faster threat detection and response with fewer resources.
- Is cloud-first or heavily reliant on SaaS platforms.
- Lacks a full-scale SOC and wants automation to reduce analyst fatigue.
- Wants an integrated experience across endpoints, cloud, and email.
- Prefers simplified licensing and easier platform management.
XDR is well-suited for SMBs, SaaS providers, and modern digital enterprises aiming for simplicity, speed, and strong protection without high operational costs. The user-friendly nature of XDR allows even small IT teams to implement best-in-class security workflows without the complexity associated with traditional SIEM tools.
Real-World Examples of SIEM vs XDR
A multinational bank uses Splunk as their SIEM to satisfy both internal policy and external regulatory requirements. They ingest terabytes of logs daily and employ full-time staff to monitor, fine-tune, and respond to alerts.
A mid-sized software company leverages Microsoft Defender XDR to unify its security posture across endpoints, cloud workloads, and email accounts. The platform’s built-in playbooks help them detect and respond to phishing campaigns and ransomware without the need for additional infrastructure.
A hybrid organization in retail uses both IBM QRadar for long-term log retention and compliance, and CrowdStrike Falcon XDR for day-to-day threat detection and response. The two platforms complement each other; QRadar provides the investigative depth, while Falcon provides speed and automation.
A university with limited IT staff adopts Trend Micro Vision One XDR to secure its student and faculty devices, cloud apps, and email systems. The platform’s guided response actions help reduce the time between detection and remediation, even when SOC analysts are unavailable.
Can SIEM and XDR Coexist?

Yes. Many organizations are now adopting a hybrid approach. SIEM serves as the historical record and compliance platform. XDR delivers agility and real-time detection. Together, they provide end-to-end visibility, deep investigations, and faster response.
Some vendors, like Microsoft and IBM, are building integrations between their SIEM and XDR tools to share context and accelerate workflows.
Integrating SIEM and XDR also allows for enhanced threat enrichment. For example, threat intelligence ingested by SIEM can augment the contextual data available in XDR, improving alert triage and decision-making.
What to Consider When Choosing
When evaluating SIEM vs XDR, consider:
- Your team’s expertise: Do you have the staff to manage a SIEM?
- Your tech stack: Are you invested in cloud-native tools that integrate better with XDR?
- Your priorities: Is compliance or fast response more important?
- Your budget: Can you support the infrastructure and license costs of a SIEM?
- Your threat profile: Are you a frequent target of advanced persistent threats (APTs)?
Also consider your long-term roadmap. Organizations planning to adopt a zero-trust architecture may benefit more from XDR’s integrated approach, while those needing deep forensic trails may require SIEM’s long-term log retention and granularity.
Conclusion of SIEM vs XDR

SIEM and XDR each have their strengths. SIEM is best for deep customization, log management, and compliance. XDR is best for automated, real-time detection and response. Both can improve your security posture, but the right choice depends on your environment, maturity level, and business goals.
For many organizations, a hybrid approach is the most strategic move. By combining SIEM’s visibility with XDR’s agility, you can stay ahead of evolving threats while meeting compliance and operational demands.
As threats become more advanced and attack surfaces continue to grow, the decision between SIEM and XDR should align with your long-term cybersecurity vision and resource capacity. Evaluating both technologies side by side and understanding how they complement each other is key to building a resilient, future-ready security strategy.