Inside the Ahold Delhaize Ransomware Breach: How 2.2 Million Lives Were Exposed

Hoplon InfoSec
01 Jul, 2025
In late 2024, a ransomware attack struck one of the largest food retailers in the United States, Ahold Delhaize USA, compromising the personal data of over 2.2 million individuals. This cyberattack didn’t target customers or payment systems; it went deeper. It exposed private employee information, including names, birthdates, Social Security numbers, bank account details, and even workers’ compensation records. The incident, which remained under wraps until mid-2025, now stands as one of the most significant employee-related data breaches in the retail sector.
This article discusses the full scope of the Ahold Delhaize ransomware breach, the methods used by the threat actors, the company’s response, and what businesses and individuals can learn from this high-impact breach.
Company Profile: Ahold Delhaize USA

Ahold Delhaize is a multinational grocery retail company headquartered in the Netherlands. Its U.S. division, Ahold Delhaize USA, operates some of the country’s most well-known grocery store brands, including Food Lion, Stop & Shop, Giant Food, Hannaford, and The Giant Company. Collectively, these brands operate over 2,000 stores across the United States and employ hundreds of thousands of workers.
Beyond being a grocery provider, Ahold Delhaize USA plays a vital role in regional economies. It manages complex operations, including logistics, pharmacy services, and e-commerce platforms. Given its scale and the volume of employee data it handles, the company became an attractive target for cybercriminals looking to steal sensitive records for profit.
How The Ahold Delhaize Ransomware Breach Happened: Timeline and Exposure
The breach was traced back to November 5 to 6, in 2024, when attackers gained unauthorized access to the company’s systems via a third-party vendor. The breach wasn’t publicly acknowledged until June 2025, when Ahold Delhaize reported the full scope of the incident to state authorities and the public.
Initial containment efforts began on November 6, 2024, when IT teams noticed unusual system activity. Key systems were shut down temporarily, including e-commerce and pharmacy services. Although customer payment data remained untouched, the attackers had already exfiltrated internal employee records. The cybercriminal group INC Ransom later published samples of the stolen data to their dark web site in April 2025, confirming their involvement.
The formal breach report, filed with the Maine Attorney General, revealed that exactly 2,242,521 people were affected. This included current and former employees, their dependents, and even beneficiaries listed on HR and payroll records.
What Data Was Compromised?
The type and volume of data exposed in this breach were both broad and deeply sensitive. The attackers stole more than just names and contact information. They accessed highly personal records that could easily be misused for identity theft, financial fraud, or social engineering attacks.
The information exposed included full names, dates of birth, Social Security numbers, passport and driver’s license numbers, bank account details, and health-related information tied to workers’ compensation claims. This wasn’t anonymized or encrypted data—it was raw, identifiable information stored in HR systems and databases maintained by the company and its vendors.
What makes this data breach especially serious is that many affected individuals were not aware their information was still stored by the company. In many cases, it involved dependents or former employees whose association with the company had ended years earlier.
A comparison of the Ahold Delhaize Breach with other notable ransomware incidents is necessary to understand the gravity of this attack.
To better understand the gravity of this attack, it helps to compare it with other high-profile ransomware breaches recently. The table below outlines key differences:
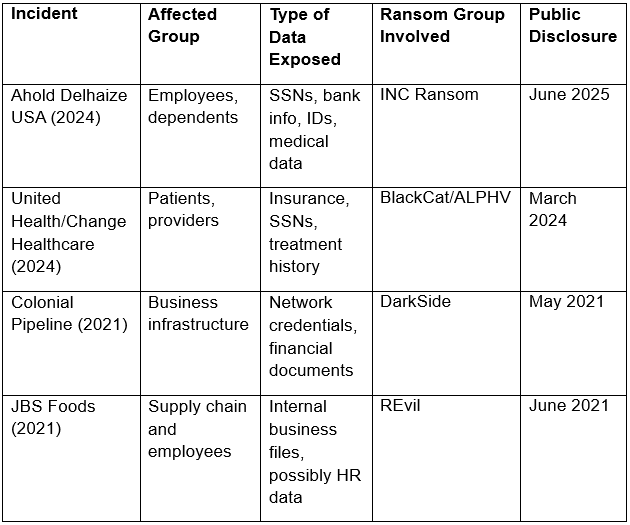
This comparison shows that while many ransomware incidents target operational disruptions or customer-facing systems, the Ahold Delhaize breach was unique in the scale and sensitivity of employee data exposed.
Who Is INC Ransom?
The threat group behind the attack, INC Ransom, is a relatively new but increasingly aggressive ransomware-as-a-service (RaaS) operation. First observed in mid-2023, INC Ransom quickly grew in notoriety due to its targeted attacks against healthcare, education, and now retail. By early 2025, the group had claimed responsibility for over 250 breaches globally.
INC Ransom is known for its “double extortion” technique. This means they not only encrypt a victim’s files but also steal them and threaten to release the data publicly if a ransom is not paid. In the case of Ahold Delhaize, INC., Ransom posted several employee records on their leak site in April 2025, months after the actual breach occurred.
The company has not confirmed whether a ransom was paid. This is common practice in the industry, as confirming payments can attract further attacks or complicate legal outcomes.
Impacts on Employees and Families

For over 2 million individuals, the breach has had lasting consequences. Many of them only learned their data had been stolen when they received a notification letter from the company in June 2025. Some found their names, social security numbers, or even scans of their IDs posted on dark web forums.
The emotional stress caused by identity theft, the burden of restoring bank accounts, and the fear of medical fraud are real and ongoing for these victims. This is especially true for people who may not have realized their data was still being held by a past employer.
To mitigate the damage, Ahold Delhaize offered two years of free credit monitoring and identity theft protection. While helpful, this gesture may fall short given the long-term risks posed by exposed SSNs and government IDs, which don’t expire the way credit cards do.
Corporate Response and Public Backlash
Following the disclosure, Ahold Delhaize USA took several steps to manage the fallout. The company brought in cybersecurity experts, worked with federal investigators, and launched a full internal review of their third-party risk management processes.
They also made a public statement expressing regret and outlining the steps they were taking to prevent similar incidents in the future. However, critics argue that the company’s delayed disclosure and reliance on a third-party vendor for employee data management highlight deeper flaws in their data governance.
Multiple law firms, including Woods Lonergan PLLC, have begun collecting complaints from affected individuals and may initiate a class-action lawsuit. These cases could hinge on whether Ahold Delhaize took “reasonable security measures” to protect sensitive information under state and federal laws.
Industry-Wide Lessons
The Ahold Delhaize breach has broader implications for the food industry and beyond. Grocery chains, which typically do not consider themselves high-value targets like banks or hospitals, must now rethink their cybersecurity postures.
The breach revealed the importance of employee data protection, not just customer information. It also exposed the risks of third-party vendors and the need for robust contracts that include cybersecurity standards, audit rights, and incident response obligations.
Companies are now being urged to adopt zero-trust architectures, regularly assess vendor risk, encrypt sensitive data at rest, and train employees on phishing and credential security. Governments may also tighten data protection regulations for industries not traditionally viewed as cybersecurity priorities.
What Affected Individuals Should Do
For those affected, the road to data security may be long. It is crucial for victims to immediately enroll in the credit monitoring services offered by Ahold Delhaize. They should also consider placing credit freezes with all major credit bureaus and checking their Social Security activity for any unusual claims.
People are advised to remain vigilant, not just for financial fraud but also for phishing attacks that may arise from their leaked information. Changing passwords, setting up multi-factor authentication, and reviewing health and insurance records regularly are all necessary precautions moving forward.
Conclusion
The Ahold Delhaize USA ransomware breach is a wake-up call. It serves as a stark reminder that even industries as essential and routine as grocery retail are not immune to sophisticated cyberattacks. The incident affected more than 2.2 million people; not through their online shopping habits, but through employment records entrusted to a company that didn’t adequately safeguard them.
As ransomware groups like INC Ransom continue to evolve and expand their reach, companies must take stronger and more proactive cybersecurity measures. The cost of inaction is no longer just financial; it’s personal.
References
Yahoo Finance
Ahold Delhaize
Share this :