Android Malware Octo2 is Targeting Users with the Intent of Stealing Their Banking Credentials

Hoplon InfoSec
26 Sep, 2024
The mobile threat environment has increasingly become a serious concern, primarily due to a substantial rise in cyberattacks, which increased by 350% in 2023 as a result of the move towards remote work. Consequently, mobile devices have become prime targets for an array of threats, including mobile phishing, malware, and harmful applications that exploit vulnerabilities in leading platforms like iOS and Android.
Cybersecurity experts at Threat Fabric have recently identified a new Android malware known as Octo2, which has been targeting users in an effort to obtain their banking credentials.
The introduction of a new variant named “Octo2” from the Octo malware family, formerly recognized as “ExobotCompact,” has marked a notable evolution in the cybersecurity landscape. This banking trojan, which primarily stems from the ‘Exobot’ lineage, was first identified in 2016 and has since undergone considerable evolution.
History of Octo
The initial instances of the Exobot malware family emerged in 2016, characterized as a banking trojan with the ability to execute overlay attacks and manage calls, SMS, and push notifications.
In 2019, a revised iteration known as “ExobotCompact” was advertised on underground forums as a streamlined version that preserved most functionalities of its predecessor.
Following a period of inactivity, a new variant of ExobotCompact was identified in 2021. Some antivirus vendors referred to it as “Coper”; however, analysts from ThreatFabric successfully traced and established its link to the original ExobotCompact.
Additionally, in 2022, the first references to a cryptic mobile malware family named “Octo” surfaced on underground forums. An individual using the alias “Architect” claimed ownership of Octo but exhibited minimal engagement on the forums, revealing only scant information regarding the malware. ThreatFabric managed to piece together the information provided by the owner, confirming that Octo is merely a rebranded version of ExobotCompact.
Since 2022, the Mobile Threat Intelligence team has noted a rise in activity from Octo and its operators. An increase in campaigns has been observed in the wild, with more actors gaining access to this malware family, drawn by its comprehensive capabilities, including continuously updated remote access features.
In 2024, several significant developments influenced the mobile threat landscape, some of which were associated with Octo. Firstly, the source code of Octo was leaked, leading to the emergence of multiple forks created by other threat actors. This leak was likely a primary factor contributing to the second significant event in the narrative of Octo: the release of a new version, Octo2, by the original threat actor.
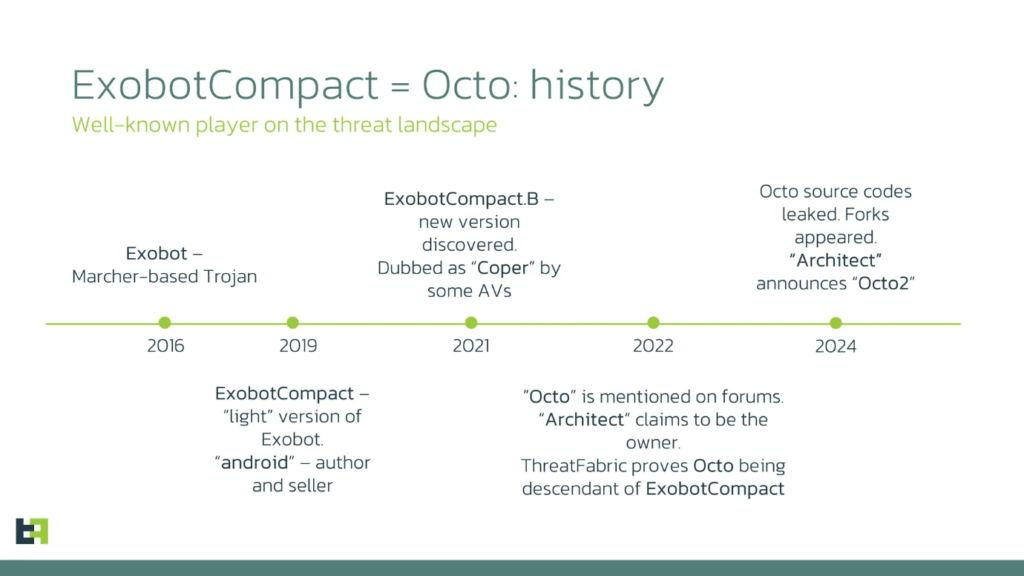
Image source: Threat Fabric
Android Malware Targeting Banking Customers
This malware, known as “Octo2,” greatly improves the remote operational capabilities essential for “Device Takeover” attacks and utilizes sophisticated obfuscation techniques.
It was first detected in Italy, Poland, Moldova, and Hungary. Additionally, Octo2 camouflages itself as widely used applications such as “Google Chrome” and “NordVPN.”
Threat Fabric’s analysis indicates that the malware employs “Zombinder” as a first-stage loader to circumvent the security restrictions imposed by Android 13 and later versions.
The malware intercepts ‘Push Notifications’ from the applications it aims at, underscoring its concentration on banking and financial services.
The Octo2 presents a range of advanced functionalities, including ‘overlay attacks’ aimed at credential theft and the ability to manage calls, SMS, and notifications. Due to its Malware-as-a-Service framework and the recent leak of its predecessor’s source code, security professionals predict a swift global proliferation of Octo2, which could represent a considerable risk to mobile banking users around the globe.
Recent Features and Updates Overview of Octo2
Below, we outline the new features and improvements introduced by Octo2:
- Enhanced stability of Remote Access Trojans (RAT)
- Advanced techniques for anti-analysis and anti-detection
- Communication capabilities with Command and Control (C2) and Domain Generation Algorithm (DGA)
The latest variant, Octo2, is developed from its predecessor, “Octo,” whose source code was compromised, allowing Octo2 to significantly improve its functionalities.
In addition to executing ‘Device Takeover attacks,’ it utilizes advanced remote-control sessions that are both more stable and harder to detect.
Furthermore, this new variant integrates superior anti-detection and anti-analysis strategies.
The malware primarily targets mobile banking applications, facilitating “on-device fraud” while remaining undetected and extracting sensitive information.
Its modular design allows for easy customization, enabling threat actors to tailor it to their specific needs and requirements. This advancement in mobile malware underscores the necessity for heightened vigilance among users and financial institutions.
Hoplon InfoSec Mobile Security
What Is Mobile Security?
Mobile security refers to the protection of mobile devices, such as smartphones, tablets, and other portable computing devices, from threats and vulnerabilities. This encompasses a wide range of practices and technologies designed to safeguard the data, privacy, and functionality of these devices.
Key Aspects of Mobile Security Include
Device Security: Protecting the physical device through measures like passwords, PINs, biometric authentication (fingerprint or facial recognition), and remote wipe capabilities in case of loss or theft.
Data Security: Protecting the data stored on and transmitted by mobile devices. This includes encryption of data both at rest (on the device) and in transit (over networks), as well as secure storage solutions.
Operating System Security: Keeping the device’s operating system up to date with the latest security patches and updates to mitigate known vulnerabilities.
Application Security: Ensuring that applications installed on the device are secure. This involves using trusted app stores, avoiding sideloading apps from untrusted sources, and regularly updating apps to patch security vulnerabilities.
Network Security: Ensuring secure connections when mobile devices access the internet or other networks. This involves using secure Wi-Fi networks, employing VPNs (Virtual Private Networks), and being cautious about connecting to public Wi-Fi.
Threat Detection and Response: Using mobile security software to detect and respond to threats such as malware, phishing, and other attacks. This software can provide real-time protection and remediation.
References
https://www.threatfabric.com/blogs/octo2-european-banks-already-under-attack-by-new-malware-variant
https://cybersecuritynews.com/octo2-android-malware-banking-credentials/
Share this :