A Closer Look at the Apple Zero-Day Vulnerability (CVE-2025-24200)

Hoplon InfoSec
17 Feb, 2025
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) recently issued an urgent warning regarding a critical zero-day vulnerability in Apple’s iOS and iPad, tracked as CVE-2025-24200. This blog post will explore the nature of this vulnerability, its implications for users and organizations, and the steps you can take to safeguard your devices.
Apple Zero-Day Vulnerability
Cybersecurity threats can emerge from any corner of the digital world, but a flaw affecting millions of devices is particularly alarming. The vulnerability in question—CVE-2025-24200—allows attackers with physical access to bypass built-in security measures on locked Apple devices. Given that these security features were designed to protect sensitive data, the potential for misuse is significant. This post will explain what this vulnerability entails, how it is exploited, and how users and organizations can mitigate the risks.
What is CVE-2025-24200?
CVE-2025-24200 is a zero-day vulnerability, meaning that it is a previously unknown flaw in the system that attackers are actively exploiting. This vulnerability resides in the state management of Apple’s USB Restricted Mode, a security feature designed to protect data when locked. Specifically, the flaw involves an authorization bypass, which means attackers can circumvent the usual permission checks that keep unauthorized tools and data extraction methods at bay.
This vulnerability is classified as CWE-863 (Incorrect Authorization). The system erroneously allows actions that should be blocked when a device is locked. Zero-day vulnerabilities are particularly dangerous because they allow attackers to exploit the flaw before a patch or fix is made available.
Understanding USB Restricted Mode
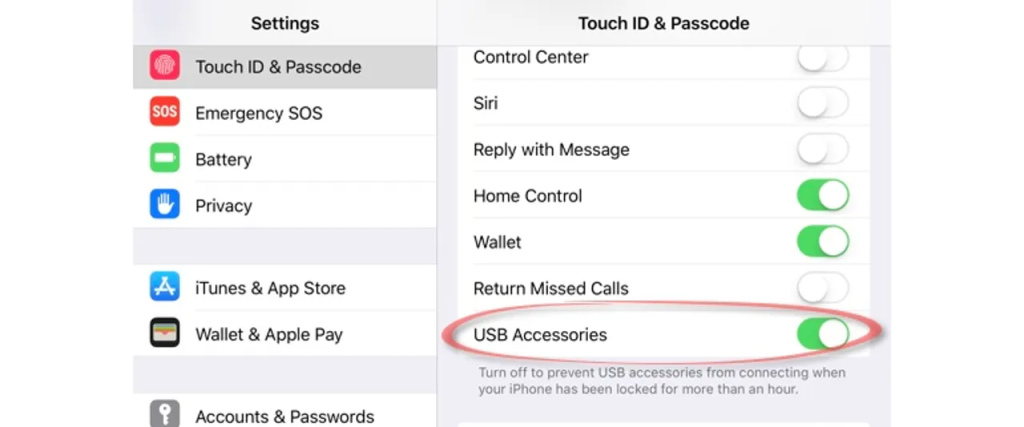
Introduced in iOS 11.4.1, USB Restricted Mode is a security measure designed to prevent unauthorized access to a device’s data through its USB port. The feature blocks USB communication with accessories if the device has been locked for over an hour. The goal is to reduce the risk of a malicious actor gaining access to the device simply by connecting it to an external tool.
Under normal circumstances, this feature provides a crucial line of defense. However, the discovery of CVE-2025-24200 reveals that an attacker with physical access can bypass these protections. This means that even if your device is locked, an individual with the right technical know-how can extract sensitive data without your consent.
How the Vulnerability Works
The flaw in CVE-2025-24200 specifically involves an authorization bypass in the USB Restricted Mode. When a device is locked, iOS and iPadOS are supposed to limit the amount of interaction available through the USB port. This safeguard is in place to protect users from data breaches that might occur if their devices were left unattended.
However, by exploiting the vulnerability, attackers can effectively turn off the intended security restrictions on locked devices. Practically, this means that even a locked device may be vulnerable to unauthorized data extraction techniques. Such methods could include specialized forensic tools typically reserved for law enforcement or even for more nefarious purposes by malicious actors.
The exploitation process is not remotely executed; it requires physical access to the device. This characteristic categorizes the attack as a cyber-physical threat—a blend of digital and physical security challenges. While the need for physical access may limit the scope of potential attackers, it still poses a serious risk, particularly for high-value targets such as journalists, activists, and government officials.
Who Is at Risk?

The impact of CVE-2025-24200 is far-reaching, affecting a broad range of Apple devices. Although the vulnerability has been exploited in what have been described as “extremely sophisticated” attacks against high-value individuals, no one is entirely immune. The list of affected devices includes:
- iPhone XS and later models
- iPad Pro 12.9-inch (2nd generation and later)
- iPad Air (3rd generation and later)
- iPad mini (5th generation and later)
These devices are used by millions worldwide, and even though the attack vector requires physical access, the potential risk to personal and professional data is immense. High-value targets are often in environments where they may be more likely to come into contact with potential attackers—ranging from political adversaries to organized crime groups.
The Role of Citizen Lab and the Possibility of State-Sponsored Exploits
The discovery of this vulnerability was not accidental. Researchers, including Bill Marczak from the University of Toronto’s Citizen Lab, played a crucial role in identifying the flaw and bringing it to Apple’s attention. Citizen Lab is renowned for uncovering advanced surveillance campaigns and has a long history of exposing state-sponsored cyber activities. Their involvement in the discovery of CVE-2025-24200 suggests that the vulnerability may be part of a broader set of tools used in sophisticated cyber-physical attacks.
Although Apple has not explicitly linked the exploitation to any specific state-sponsored group, the complexity of the attacks aligns with tactics typically seen in state-backed operations. This is further underscored by historical comparisons to surveillance tools such as Pegasus spyware, developed by NSO Group—a firm whose methods have raised concerns about the misuse of digital surveillance technologies against journalists, activists, and political figures.
Mitigation Measures and Patch Updates
In response to this urgent threat, Apple has acted swiftly to protect its users. Emergency patches were released on February 10, 2025, via iOS 18.3.1, iPadOS 18.3.1, and for older models with iPadOS 17.7.5. These updates are designed to address the vulnerability by correcting the authorization flaw in USB Restricted Mode.
CISA has also taken proactive steps by adding CVE-2025-24200 to its Known Exploited Vulnerabilities Catalog. Their recommendation is clear: users and organizations must patch the vulnerability as soon as possible—preferably before March 5, 2025—to mitigate the risk of exploitation.
The patch is not just a minor update but a critical security fix. Installing it promptly is essential for anyone using one of the affected devices. The update process is straightforward and can be initiated by going to your device’s Settings > General > Software Update. Additionally, enabling automatic updates is a highly recommended practice that ensures you always have the latest security patches installed without manual intervention.
Recommendations for Users
For everyday users, the primary defense against this vulnerability is to ensure that all your devices are updated with the latest software patches. Here are some detailed recommendations to help protect yourself:
1. Update Your Devices Immediately
The most crucial step is to install the latest updates provided by Apple. Navigate to Settings > General > Software Update on your iPhone or iPad to check for and install the newest version. Updating your device ensures you benefit from the latest security enhancements and fixes.
2. Enable Automatic Updates
Consider enabling automatic updates on your device. This ensures you receive security patches and new software versions as soon as they are released, minimizing the risk of exposure to vulnerabilities like CVE-2025-24200.
3. Be Cautious with Physical Access
Since the exploit requires physical access, always be mindful of who may have direct access to your gadgets. Avoid leaving your device unattended in public spaces or situations where someone with malicious intent could gain physical access. Additional physical security measures, such as secure storage and regular device inspections, are advised for high-value targets.
4. Monitor for Unusual Activity
Even if your device is up-to-date, remain vigilant for any signs of unusual behavior or unauthorized access attempts. Unusual battery drain, unexpected app behavior, or unfamiliar network connections can indicate a security breach. If you notice any anomalies, immediately contact Apple Support or a trusted cybersecurity professional.
Recommendations for Organizations
Organizations that rely on Apple devices for sensitive operations must adopt a multi-layered approach to security. Here are several measures to consider:
1. Enforce Device Management Policies
Implement strong device management policies that require all devices within the organization to be updated with the latest software. Use mobile device management (MDM) tools to ensure compliance and quickly push out security updates across the entire fleet of devices.
2. Implement Strict Physical Security Protocols
Organizations should enforce strict physical security protocols, especially for devices that handle sensitive or proprietary information. This may include secure storage solutions, access controls, and monitoring systems to prevent unauthorized physical access.
3. Conduct Regular Security Audits
Regular security audits can help identify vulnerabilities or lapses in your current security protocols. This proactive approach enables organizations to address potential issues before malicious actors exploit them.
4. Educate Employees
Ensure all employees know the potential risks and understand the importance of security best practices. Training sessions on device security, recognizing phishing attempts, and handling sensitive data can significantly reduce the risk of exploitation.
5. Prepare an Incident Response Plan
Develop and maintain a robust incident response plan. In the event of a breach or an attempted exploit, having a pre-established protocol can minimize damage and facilitate a quick recovery. This plan should include communication strategies, technical responses, and recovery procedures.
The Bigger Picture: Surveillance, Privacy, and Trust
The implications of CVE-2025-24200 extend beyond the immediate technical details. This vulnerability also touches on broader issues of surveillance, privacy, and the trust we place in our technology providers. Apple’s transparency report, for instance, reveals that its security tools have been sold to 54 government clients across 31 countries. This fact, combined with the sophisticated nature of the exploit, raises questions about how surveillance tools are deployed and whether they might be misused against vulnerable groups such as journalists, activists, or political figures.
While Apple maintains that it does not target any specific group with its security measures, the association with surveillance tactics reminiscent of those used by the NSO Group adds an extra layer of concern. It serves as a reminder that even companies known for their strong privacy stances are not immune to vulnerabilities and that continuous vigilance is necessary.
A Call to Action
In today’s digital age, no device is ever completely safe from threats. The discovery of CVE-2025-24200 is a wake-up call for individual users and organizations. It underscores the importance of proactive security measures, timely updates, and a comprehensive understanding of exploiting vulnerabilities.
Here are some final steps you can take to protect yourself:
- Stay informed: Follow reputable cybersecurity news sources and updates from agencies like CISA.
- Engage with your device’s ecosystem: Whether you are an individual user or part of an organization, make it a habit to review and update your device’s security settings.
- Advocate for transparency: Encourage companies to be transparent about vulnerabilities and the measures they take to protect users.
Conclusion
The critical zero-day vulnerability in Apple’s iOS and iPadOS—CVE-2025-24200—is a stark reminder of the persistent challenges in the cybersecurity landscape. With attackers exploiting an authorization bypass in USB Restricted Mode, the risk to high-value individuals and everyday users is significant. You can better protect your digital life by understanding how the flaw works, who is at risk, and what steps can be taken to mitigate its impact.
From installing the latest updates and enabling automatic software updates to enforce robust physical security measures, your actions today can prevent tomorrow’s security breaches. As cybersecurity threats evolve, staying proactive and informed is your best defense against potential exploits. Whether you are a tech-savvy professional or an everyday user, the importance of security cannot be overstated.
Remember: the digital landscape is constantly changing, and while vulnerabilities like CVE-2025-24200 pose serious challenges, a well-informed user community can significantly improve the security of an environment. Stay vigilant, keep your devices updated, and protect against cyber threats.
For more:
https://cybersecuritynews.com/cisa-apple-ios-vulnerability-exploited/
Share this :