Attackers Exploits SourceForge Software Hosting Platform to Deliver Malware

Hoplon InfoSec
09 Apr, 2025
In the constantly evolving world of cybersecurity, cybercriminals continually develop sophisticated techniques to deceive users and evade security measures. One recent scheme involves the exploitation of SourceForge—a well-known software hosting platform—to distribute malicious software. Attackers trick users into downloading harmful programs by masquerading as legitimate office applications. This blog post delves into the details of the scheme, explains how the deception works, and offers guidance on protecting your systems and data from similar threats.
Understanding the Threat Landscape
The Rise of Sophisticated Cybercriminal Schemes
Cyber threats have grown in complexity over the years. Attackers no longer use simple phishing emails or basic malware; instead, they leverage trusted platforms and social engineering tactics to access users’ computers. In this case, cybercriminals have targeted SourceForge, a reputable platform for hosting open-source software projects, to launch their attack. By creating seemingly legitimate projects, the attackers can exploit the platform’s infrastructure and trust, making their malicious activities more challenging to detect.
How SourceForge Became a Vector for Malware
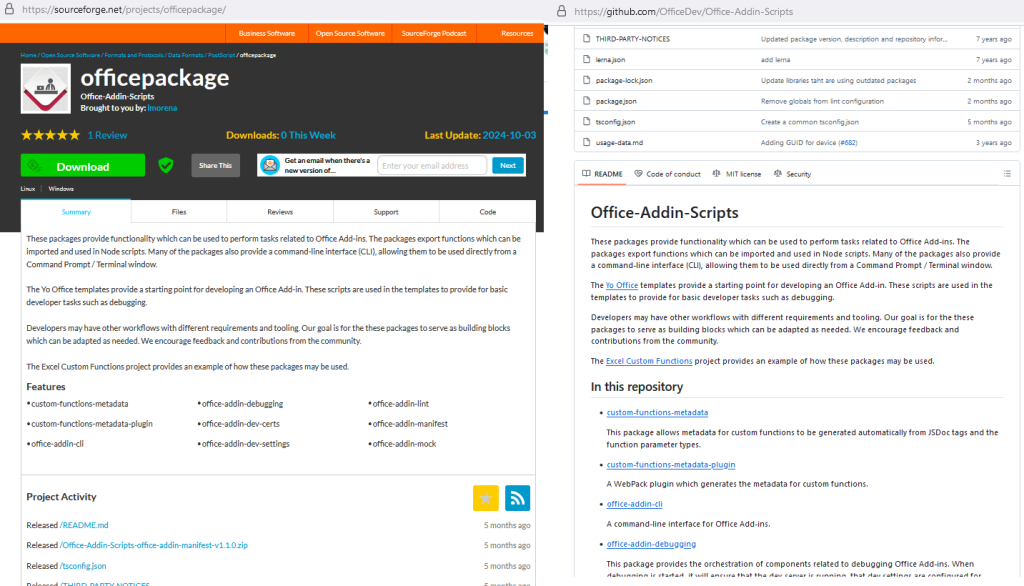
Developers widely use SourceForge to share and collaborate on software projects. Its features include automatically assigning sourceforge.io domains to hosted projects, functionality criminals have now exploited. Attackers create projects with names that resemble those of trusted applications. For instance, an “office package” project” might mimic a legitimate office suite or add-in service. When unsuspecting users click on download buttons, they are redirected to what appears to be an authentic SourceForge URL, only to receive a malicious payload instead. This clever use of domain assignment and project naming conventions is central to the attackers’ deceptive strategy.
Technical Details of the Malware Distribution

The Illusion of Legitimate Software
The attack begins with creating an “office package” project on SourceForge. On the surface, this project appears harmless, containing files identical to legitimate Microsoft Office add-ins sourced from a well-known GitHub repository. However, a closer inspection reveals that when users access the corresponding subdomain (officepackage.sourceforge.io), they are greeted with an interface that displays a list of office applications complete with download buttons.
These buttons are designed to mislead users by linking to URLs of the SourceForge ecosystem (for example, loading.sourceforge.io/download). This facade of authenticity makes it difficult for even experienced users to recognize the threat immediately.
The Deceptive Download Process
Once a user clicks one of these download buttons, the process begins with downloading a compressed archive file named “vinstaller.zip.” One of the red flags in this chain is the file size; at approximately 7 megabytes, it is significantly smaller than what one would expect from a fully functional office application package. Even when compressed, legitimate software applications usually require much more storage space. This discrepancy in file size should prompt users to exercise caution.
fter downloading, the archive is password-protected. The password is conveniently included in a separate text file—a technique frequently used by cybercriminals to bypass security solutions that might otherwise inspect the contents of encrypted files. Once the password is used and the archive is extracted, users are presented with an installer file, typically named “installer.msi.”
Padding and Inflation: The False Sense of Legitimacy
One of the most ingenious parts of the attack is manipulating the installer file. The installer.msi is artificially inflated to a size exceeding 700 megabytes by inserting null-byte padding into the file. This technique intends to create the illusion of a complete, legitimate software package. Much of this space is filled with meaningless data designed solely to trick users and automated analysis tools into thinking that the package is bona fide.
Anti-Analysis Measures and Multi-Stage Infection
Multiple stages further increase the complexity of the infection mechanism, each designed to evade detection by modern security tools. When the inflated installer is executed, it extracts several components. Among these is an executable file named “UnRAR.exe” and another password-protected archive (51654.rar).
The malware employs embedded Visual Basic scripts to further its objectives within these components. One of the scripts downloads a batch file (named “config”) from a repository on GitHub. This batch file contains the archive password and performs several anti-analysis routines. It checks for security software, virtual environments, and other research tools that indicate that the file is being analyzed in a controlled environment. This type of anti-analysis check is common in advanced malware, ensuring that the attack can evade sandboxing and other detection mechanisms employed by cybersecurity professionals.
Establishing Persistence on the Target System
After the initial execution, the malware creates multiple persistence mechanisms on the infected system. These include developing new Windows services, modifying the system registry, and scheduling tasks that ensure the malware runs on startup. Persistence mechanisms are crucial for cybercriminals because they allow the malware to survive reboots and remain active over an extended period. This persistence enables the malware to perform its malicious activities continuously without the user’s knowledge.
Deeper Analysis of the Malware Payload
Dual Threat: Cryptocurrency Miner and Clipboard Hijacker
Once installed, the malware’s final payload consists of two particularly dangerous components. The first is a cryptocurrency miner. Cryptocurrency miners covertly use the victim’s system resources to mine digital currencies, often without the user’s consent. This mining process can significantly slow down the system and increase power consumption, leading to higher electricity bills.
The second component is the ClipBanker Trojan. ClipBanker is designed to monitor the user’s clipboard for cryptocurrency wallet addresses. When a user copies a wallet address intended for transferring cryptocurrency, the Trojan automatically replaces it with an address controlled by the attacker. This clipboard hijacking allows criminals to intercept transactions and reroute funds into their own accounts. Resource theft and financial fraud make this malware particularly harmful, especially for active users in the cryptocurrency market.
Why Cybercriminals Target Russian-Speaking Users
Interestingly, the campaign explicitly targets Russian-speaking users. The choice of language in the interfaces and the strategic naming of files suggest that the attackers are concentrating their efforts on a particular demographic. This targeted approach might be due to several factors, including the potential for less rigorous cybersecurity measures in the region or a more significant number of users engaging in cryptocurrency trading and related activities. Understanding this geographical focus is crucial for security professionals and users alike, as it highlights the need for heightened awareness in communities that might be more vulnerable to such attacks.
Security Measures and Best Practices
Recognizing Suspicious File Sizes and Anomalies
One of the first signs that something might be amiss in the described attack is the file size of the downloaded archive. At around 7 megabytes, the compressed file is tiny for a complete office application suite. Users should be trained to question such discrepancies. A good rule of thumb is to compare the file size of a suspicious download against known legitimate software. If there is a significant mismatch, it might be an indication that the file is not what it purports to be.
Risks Associated with Password-Protected Archives
Password-protected archives are a standard tool in the cybercriminal’s arsenal. They serve the dual purpose of preventing immediate inspection by security software and obfuscating the true nature of the contents. When an archive is password-protected, and the password is provided in a separate file, it creates an extra layer of deception. Users should be cautious when downloading such files and consider using additional tools or services to analyze the contents of encrypted files safely. Organizations can also employ sandboxing techniques to execute the file in a controlled environment and monitor its behaviour before allowing it into the broader network.
Importance of Updated Security Software and Practices
Keeping security software up to date is one of the most effective ways to defend against sophisticated attacks. Modern antivirus programs and endpoint detection solutions are constantly updated with signatures and heuristics that can detect new threats, including those that use anti-analysis techniques. Both individuals and organizations must ensure that their security tools are current and configured to scan for encrypted files, unusual file size inflations, and other suspicious behaviours. Regular security audits and user training sessions are also vital to reinforce good cybersecurity practices.
Future Trends in Cybercrime and Mitigation Strategies
Evolving Techniques in Malware Distribution
The SourceForge exploitation is a prime example of how cybercriminals continue to innovate. In an era when traditional phishing emails are becoming less effective, attackers are turning to trusted platforms to hide their activities. As software hosting platforms grow in popularity and functionality, they inadvertently offer more opportunities for exploitation. Future trends may include similar attacks on well-known platforms or a combination of social engineering and technical exploits designed to take advantage of emerging technologies.
Strategies for Organizations and Individuals
A multi-layered approach to cybersecurity is essential to combat these evolving threats. Organizations should invest in advanced threat detection systems that analyze real-time file behaviour, network traffic, and user activities. Individuals should adopt safe browsing habits and be sceptical toward unsolicited downloads—even from reputable platforms. Additionally, regular backups, incident response planning, and multi-factor authentication can help mitigate the damage in a breach.
Collaborative Efforts and Information Sharing
The fight against cybercrime is not one that any single entity can win alone. Governments, private companies, and cybersecurity researchers must work together to share information about emerging threats. Collaborative platforms and forums for threat intelligence can be crucial in identifying and mitigating attacks before they reach a broad audience. By staying informed and fostering a culture of information sharing, the cybersecurity community can stay one step ahead of adversaries.
Practical Steps to Protect Yourself

Be Cautious with Unsolicited Downloads
One of the simplest yet most effective measures is to exercise caution when downloading files from the internet. Always verify the source of the file and be sceptical of offers that seem too good to be true. If a download originates from a trusted platform like SourceForge, double-check the project details, file sizes, and any accompanying documentation for signs of tampering.
Educate Yourself About Cyber Threats
Staying informed about the latest cyber threats is critical. Following reputable cybersecurity blogs, forums, and news sources, you can learn about emerging attack vectors and adjust your security practices accordingly. This education can empower you to recognize unusual patterns or file characteristics that may indicate a threat.
Utilize Advanced Security Tools
Beyond traditional antivirus software, consider employing advanced tools that analyze file behaviour in sandbox environments. These tools can execute files in isolated environments to observe their behaviour without risking your central system. Some solutions also offer real-time scanning of encrypted archives, which can help identify malicious content before it has a chance to execute.
Regular System and Software Updates
Keeping your operating system and software up to date is one of the most effective ways to protect against vulnerabilities. Cybercriminals often exploit known vulnerabilities that have already been patched in newer versions of software. You can reduce the risk of exploitation by enabling automatic updates or regularly checking for patches.
Conclusion
In summary, the recent malware campaign leveraging SourceForge’s domain and project assignment features highlights the evolving sophistication of cybercriminal tactics. By disguising malicious software as legitimate office applications, attackers bypass many traditional security measures and deceive users into unwittingly installing harmful payloads. The multi-stage infection process—ranging from the deceptive use of password-protected archives and inflated installer files to advanced anti-analysis and persistence mechanisms—illustrates the complexity of modern cyber threats.
This case is a stark reminder of the importance of maintaining robust cybersecurity practices for individuals and organizations. From being vigilant about file sizes and suspicious download links to updating software and employing advanced security tools, every step counts in the battle against cybercrime. As attackers continue to refine their techniques and target specific demographics, such as Russian-speaking users in this instance, ongoing education and collaboration in the cybersecurity community remain critical.
Sources: Techmirror, Cybersecurity News, Securelist
Share this :