Protect Against Auto-Generated Password Vulnerability in Sitevision

Hoplon InfoSec
21 Feb, 2025
One widely adopted platform is Sitevision CMS. Recently, a critical security vulnerability—tracked as CVE-2022-35202—was discovered in Sitevision CMS versions 10.3.1 and older. This flaw exposes SAML authentication signing keys, creating potential avenues for attackers to bypass authentication and hijack user sessions. In this comprehensive blog post, we will explore the technical aspects of this vulnerability, understand its implications, and provide actionable remediation and best practices to safeguard your systems.
Introduction of Auto-Generated Password Vulnerability
Sitevision CMS is popular in Sweden’s public sector and various enterprise environments due to its versatility and reliability. However, like many software platforms, it is not immune to security challenges. The recent vulnerability, CVE-2022-35202, highlights a severe weakness that affects the SAML (Security Assertion Markup Language) authentication process—an integral part of secure login procedures for many organizations. An attacker can potentially forge SAML authentication requests by exploiting this flaw, leading to unauthorized access and session hijacking. This blog post aims to elucidate the vulnerability’s mechanics and outline steps to protect against such threats.
Background: Understanding SAML and Secure Authentication
SAML is a standard for exchanging authentication and authorization data between parties, particularly between an identity provider (IdP) and a service provider (SP). In modern enterprise architectures, SAML is crucial in ensuring that authentication processes are secure and that only authorized users can access sensitive information. The integrity of SAML communications relies heavily on the proper management and protection of cryptographic keys, which are used to sign authentication requests and responses.
Within Sitevision CMS, SAML facilitates secure authentication flows. However, a flaw in how these cryptographic keys are stored and protected has led to severe security risks. This vulnerability underscores the importance of robust key management and stringent security practices within any authentication system.
The Vulnerability Unveiled: How CVE-2022-35202 Occurred
This vulnerability is at the heart of systemic issues related to automated credential generation and WebDAV misconfigurations. The flaw primarily stems from weak auto-generated passwords that protect Java keystores containing critical cryptographic keys. Let’s break down the chain of events that led to this security exposure:
Weak Auto-Generated Passwords
Sitevision CMS uses Java key stores (JKS) to store cryptographic keys essential for signing SAML authentication requests. In versions 10.3.1 and older, these key stores were protected by an 8-character password generated automatically. The password was composed of lowercase letters and digits only—a configuration that, while convenient, made it highly vulnerable to brute-force attacks. With a limited set of possible characters, the keyspace was significantly reduced, making it feasible for an attacker to crack the password using modern computational resources.
WebDAV Misconfigurations
Another significant factor contributing to the vulnerability was the misconfiguration of the WebDAV (Web Distributed Authoring and Versioning) service. WebDAV is a protocol used for managing files on web servers, and Sitevision CMS leverages it for content management. In non-default configurations, the /webdav/files/ directory became accessible, inadvertently exposing a critical file: the same keystore. This file contains the cryptographic keys used for signing SAML authentication requests. Once an attacker gains access to the same keystore file, the weak auto-generated password becomes the weak link in the security chain.
Technical Exploitation: From Access to Attack
Once the same keystore file is exposed, the vulnerability chain is complete. Attackers can execute a series of steps to compromise the security of the CMS:
Extracting the Keystore’s Password Hash
Security researchers, including analysts at ShellTrail, demonstrated that extracting the SHA1 hash of the keystore’s password is possible using tools like JksPrivkPrepare.jar. With the hash in hand, the next step is to use GPU-accelerated tools to perform a brute-force attack on the hash.
Brute-Force Attack Using GPU-Accelerated Tools
A standard tool for such brute-force attacks is Hashcat, which leverages the power of modern GPUs to accelerate password cracking. For example, an attacker might use a command similar to the following:
hashcat -m 15500 -a three same-keystore. hash -1 ?d?l ?1?1?1?1?1?1?1?1 -w 3 -OThis command configures Hashcat to target the 8-character alphanumeric password space. This command can crack the password on moderate hardware in roughly 15 hours. Once the password is recovered, the contents of the Java keystore, including the private key for SAML signing (known as the dismal private key), become accessible.
Forging Malicious SAML Authentication Requests
With the compromised private key, attackers can sign fraudulent SAML authentication requests. This manipulation is particularly dangerous because SAML 2.0 protocols require that the Identity Providers validate the Assertion Consumer Service URL (the endpoint where the authentication assertion is sent) against pre-registered metadata. In some cases, certain IdPs might rely more heavily on the presence of a valid signature rather than rigorous metadata validation. As a result, attackers can craft SAML requests with a manipulated AssertionConsumerServiceURL, effectively redirecting authentication tokens to endpoints under their control. This redirection opens the door to session hijacking, where an attacker gains unauthorized access to user sessions and, by extension, sensitive resources.
Deep Dive: Exploitation Mechanics and SAML Flow Manipulation
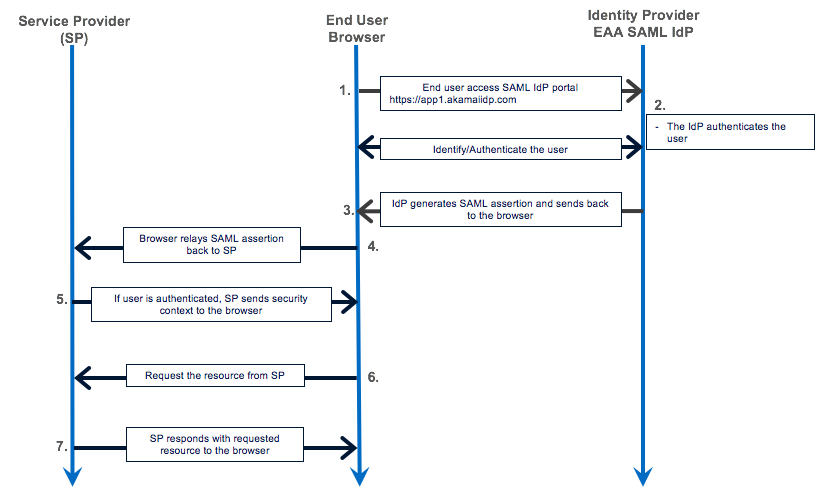
Understanding the full impact of the vulnerability requires a deeper look at how the exploitation process disrupts normal SAML flows. In a secure SAML implementation, the integrity of the authentication process is ensured by a series of checks and balances:
- Signing and Verification: When a service provider sends an authentication request, it is signed with a private key. The corresponding public key, stored in metadata, is used by the Identity Provider to verify the request’s authenticity.
- Metadata Validation: The Identity Provider must validate the URL specified in the request against pre-registered service provider metadata. This ensures that the authentication response is directed to a legitimate endpoint.
When the private key is compromised, attackers can bypass these safeguards. By forging a SAML authentication request with a malicious AssertionConsumerServiceURL, they can trick the Identity Provider into sending sensitive authentication tokens to a destination controlled by the attacker. This manipulation of the SAML flow undermines the security model and exposes the system to session hijacking, where active sessions can be intercepted and misused.
The technical process can be broken down into the following steps:
- Accessing the Keystore: Attackers access the same keystore file through a misconfigured WebDAV directory.
- Extracting and Cracking the Password: The weak 8-character password is extracted in hashed form and subsequently cracked using tools like Hashcat.
- Retrieving the Private Key: Once the password is known, the key for signing SAML requests is retrieved from the Java keystore.
- Forging SAML Requests: With the private key, attackers generate fraudulent SAML authentication requests, altering the AssertionConsumerServiceURL.
- Redirecting Authentication Tokens: If the Identity Provider fails to validate the URL against its metadata correctly, it may inadvertently send the authentication response to an attacker-controlled endpoint, thus enabling session hijacking.
Implications for Organizations and Enterprises
The discovery of CVE-2022-35202 is a stark reminder of the systemic risks associated with automated credential generation and misconfigured services. For organizations relying on Sitevision CMS, especially those in critical sectors like public administration, the following implications are worth noting:
Increased Risk of Unauthorized Access
The primary risk associated with this vulnerability is the potential for unauthorized access to systems through session hijacking. Once an attacker gains control over a session, they can access sensitive data, manipulate content, or even use the compromised session as a pivot point for further attacks within the network.
Compromise of SAML-Based Authentication Systems
SAML is widely regarded as a secure protocol for federated identity management. However, this incident reveals that even robust authentication systems can be undermined if their underlying key management practices are flawed. Organizations must reevaluate their reliance on auto-generated credentials and ensure that every component of their authentication infrastructure is secure.
The Domino Effect on Interconnected Systems
Modern IT environments are interconnected, and a compromise in one system can have cascading effects on other systems. Exploiting the SAML signing key not only endangers the CMS itself but also poses a risk to any system integrated with the SAML authentication process. This can include enterprise applications, internal portals, and external-facing services.
Remediation: Patching the Vulnerability and Strengthening Defenses
Recognizing the gravity of the situation, Sitevision has released an updated version—10.3.2—that addresses the vulnerability by enforcing stronger password policies for the Java key stores. However, patching the software is only one part of the solution. Organizations must adopt a comprehensive approach to remediate and mitigate the risks associated with this vulnerability.
Upgrading to a Secure Version
The immediate priority for any organization using Sitevision CMS is to upgrade to version 10.3.2 or later. This upgrade enforces stronger passwords for the keystore, reducing the likelihood of successful brute-force attacks. However, it is essential to note that the update does not automatically remediate existing installations; administrators must manually rotate any compromised keystore passwords.
Auditing WebDAV Configurations
Misconfigured WebDAV settings exacerbated the vulnerability, allowing unauthorized access to critical directories. Organizations should conduct a thorough audit of their WebDAV configurations to ensure that only authorized users have access to sensitive directories such as /WebDAV/files/. Implementing strict access controls and regularly reviewing directory permissions can prevent similar exposures in the future.
Strengthening Key Management Practices
Effective key management is a cornerstone of secure authentication systems. Organizations should move away from weak, auto-generated passwords and adopt more robust methods of protecting cryptographic keys. This might include using longer, more complex passwords or, ideally, integrating hardware security modules (HSMs) to manage and store keys in a tamper-resistant environment. Regularly rotating keys and conducting periodic audits of keystore contents should become standard practice.
Ensuring Rigorous SAML Metadata Validation
Another layer of defense lies in how Identity Providers (IdPs) handle SAML authentication requests. Even if an attacker manages to forge a request, a properly configured IDP will validate the AssertionConsumerServiceURL against the pre-registered metadata. Organizations must collaborate with their IDP vendors to enforce strict metadata validation, reducing the risk of token redirection and session hijacking.
Training and Awareness
Technical solutions alone cannot fully mitigate security risks. Organizations must invest in training and awareness programs for their IT staff and administrators. Understanding the nuances of SAML, the importance of secure key management, and the potential impact of vulnerabilities can empower teams to adopt proactive security measures. Regular training sessions and security audits can create a vigilance culture crucial for long-term cybersecurity resilience.
Best Practices for Future Security

The incident with Sitevision CMS offers lessons beyond the immediate remediation of CVE-2022-35202. As organizations look to fortify their digital infrastructure, several best practices should be considered:
Comprehensive Vulnerability Management
Adopting a proactive vulnerability management program is essential. This involves regular security assessments, penetration testing, and continuous monitoring of systems for emerging threats. Organizations can take preemptive measures to safeguard their infrastructure by identifying vulnerabilities before they can be exploited.
Emphasis on Secure Software Development
The incident highlights the need for secure software development practices for vendors and developers. These include incorporating security testing into the development lifecycle, using automated tools to detect weak configurations, and adhering to the best password generation and storage practices. A security-first mindset during development can significantly reduce the likelihood of vulnerabilities making it into production.
Multi-Layered Security Architecture
Relying on a single layer of security is no longer sufficient in today’s threat landscape. Organizations must adopt a multi-layered security architecture that includes firewalls, intrusion detection systems, robust access controls, and continuous monitoring. Each layer acts as a safeguard, ensuring that additional measures are in place to mitigate the impact if one defense is breached.
Collaboration with Security Vendors and Communities
Finally, organizations should not operate in isolation. Engaging with security vendors, participating in industry forums, and collaborating with cybersecurity communities can provide valuable insights into emerging threats and effective countermeasures. By sharing information and best practices, the broader industry can work together to raise the overall level of security.
Conclusion
The CVE-2022-35202 vulnerability in Sitevision CMS is a critical reminder of the intricate challenges of securing modern web applications. The exposure of SAML authentication signing keys—from weak, auto-generated passwords and misconfigured WebDAV settings—can potentially undermine even the most robust authentication systems. However, with the release of Sitevision version 10.3.2 and the implementation of comprehensive remediation measures, organizations can address this vulnerability head-on.
Upgrading to a secure version of the CMS, auditing and tightening WebDAV configurations, reinforcing key management practices, and ensuring strict metadata validation with Identity Providers are crucial to mitigating the risk. Moreover, adopting a proactive approach to vulnerability management, secure software development, and multi-layered security architectures can help organizations better prepare for future threats.
By understanding the technical details and broader implications of this vulnerability, IT professionals can not only remediate the current risk but also build a more resilient digital infrastructure for the future. The lessons learned from this incident underscore the importance of vigilance, collaboration, and continuous improvement in the ever-evolving realm of cybersecurity.
As organizations navigate these challenges, it is essential to remember that cybersecurity is a collective effort that requires constant adaptation and a commitment to best practices. By taking proactive measures and fostering a culture of security awareness, organizations can safeguard their critical systems and maintain the trust of their users in an increasingly connected world.
For more:
https://cybersecuritynews.com/auto-generated-password-vulnerability/
Share this :