Featured Blogs
Recent Blogs
Novel 5G attack bypassing base station The Day I Found Out My Phone Wasn’t Alone ,I remember...
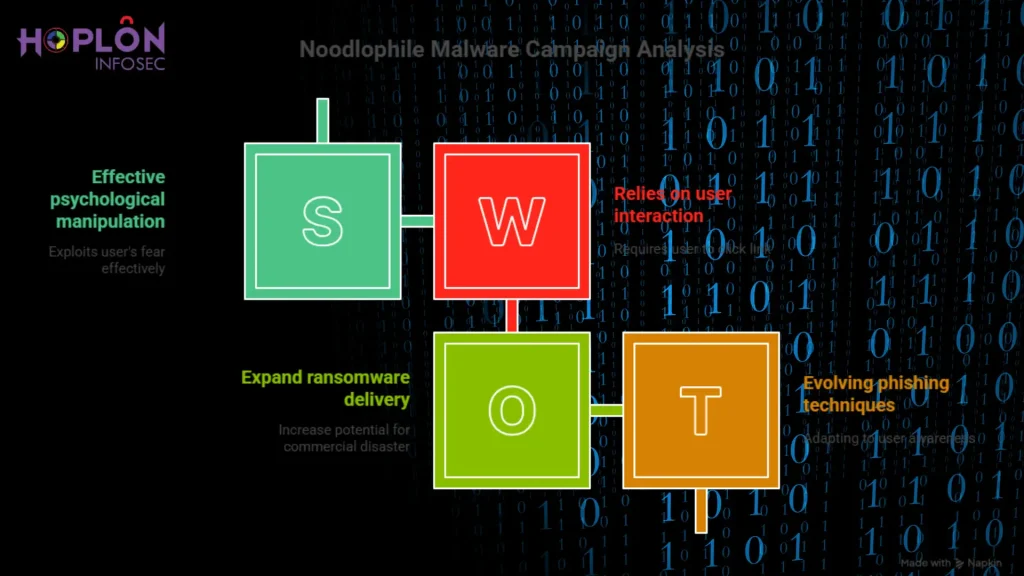
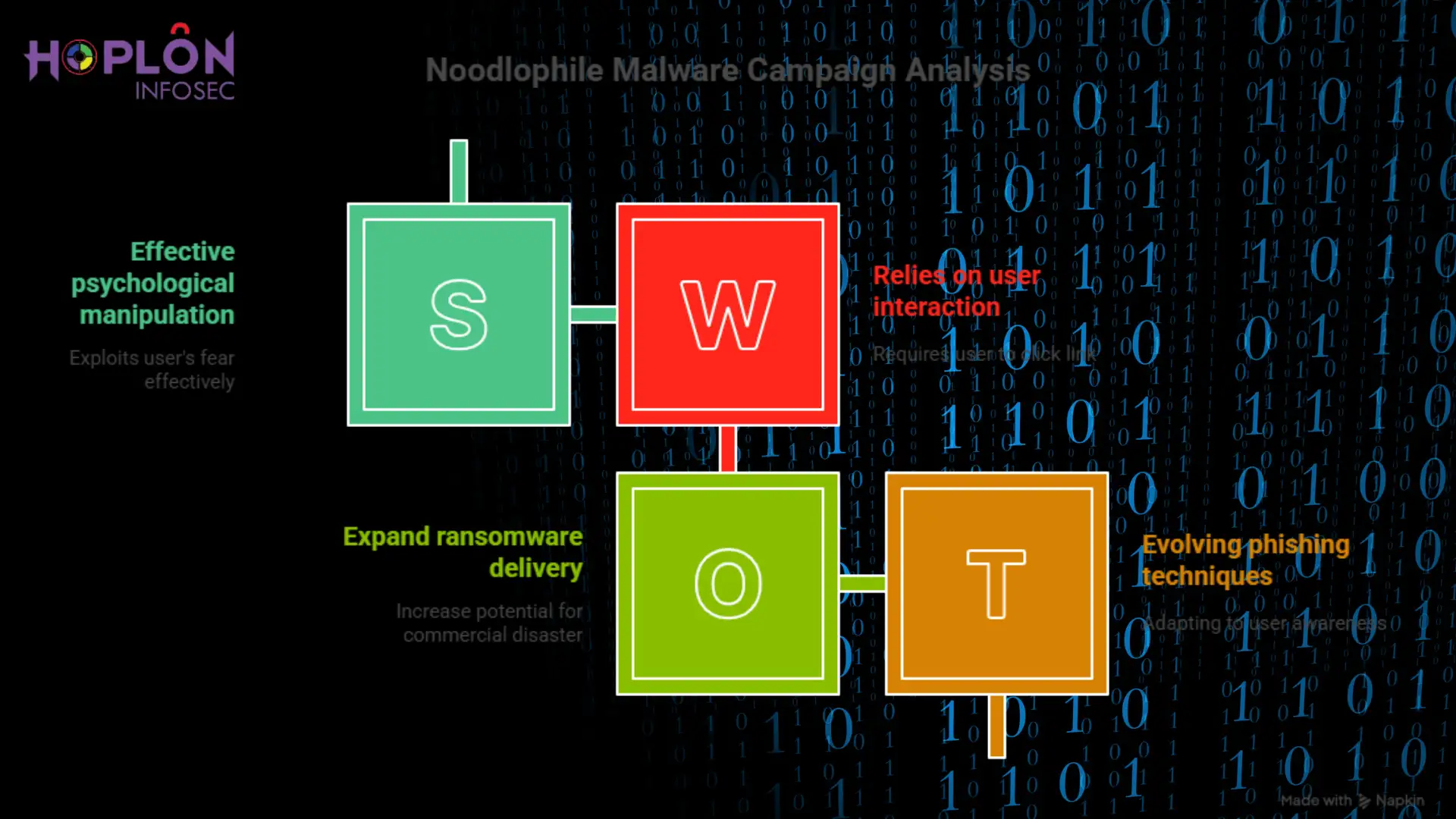
The Noodlophile Malware Campaign’s Growing Shadow On a quiet Tuesday afternoon, an IT manager...
By 2025, safeguarding your data is a business survival tactic rather than merely an IT duty...
windows 11 24h2 ssd/hdd failure You install a huge Windows update, sip your tea, and then restart...
Imagine discovering one morning that your banking app is empty, your phone has been compromised, or...
back-to-school shopping scams:Why Scammers Love the Beginning of School As the back-to-school rush...
Water sector cybersecurity Why the water business needs to be safe online Take a moment to think...
New Gmail phishing attack steals credentials It was hard to discern if an email was phishing a few...
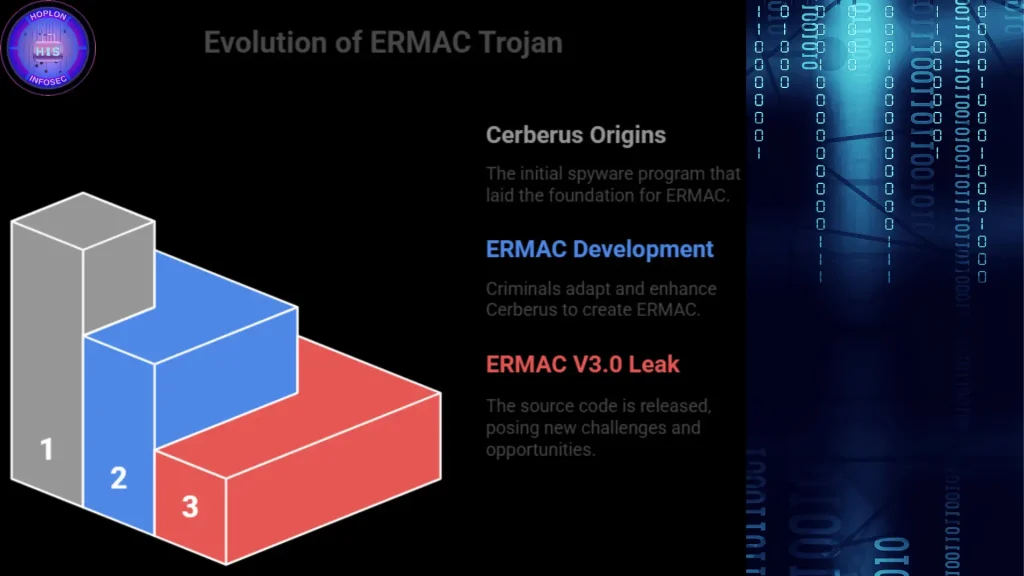
ERMAC V3.0 banking Trojan source code leak The release of the ERMAC V3.0 banking Trojan’s...
Recent Blogs
We’re Here to Secure Your Hard Work
Protect your system from cyber attacks by utilizing our comprehensive range of services. Safeguard your data and network infrastructure with our advanced security measures, tailored to meet your specific needs. With our expertise and cutting-edge technology, you can rest assured.