Featured Blogs
Recent Blogs
Erlang/OTP CVE-2025-32433 exploitation It was a late evening in a busy telecommunications control...
In our interconnected world, cyber threats are growing more advanced every day. Among these threats...
Imagine you are sitting on a crowded city bus, tapping away on your phone, connected to the bus’s...
As the modern workplace evolves, so does the cyber threat landscape. Employees are increasingly...
Artificial intelligence is revolutionizing every sector, from healthcare and finance to...
Cyber Security Incident Response Every business, government agency, and nonprofit that uses the...
AI management in 2025 In early 2025, Maya, a senior data scientist at a large multinational...
The majority of organizations think that their systems are secure until a breach occurs. Security...
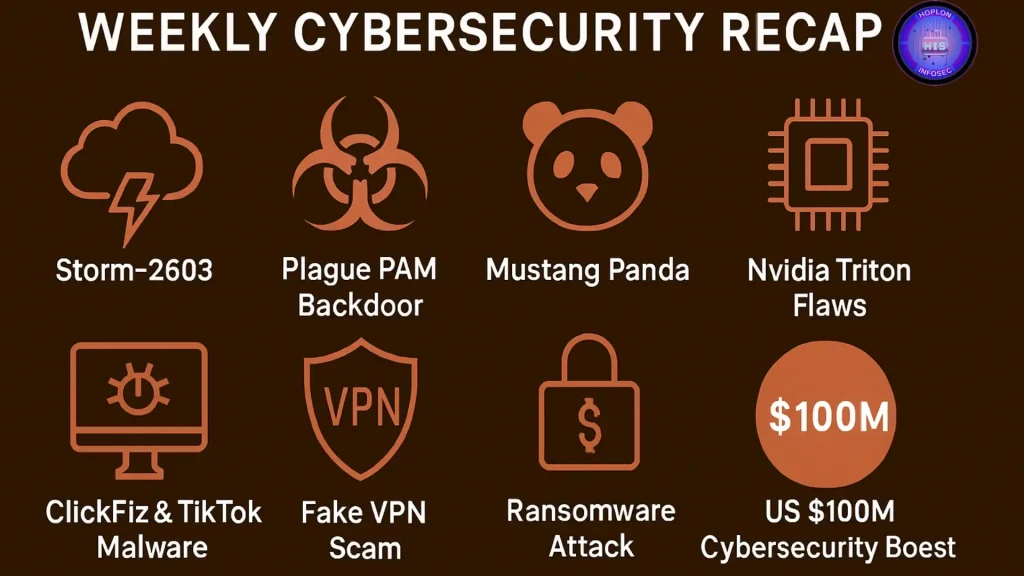
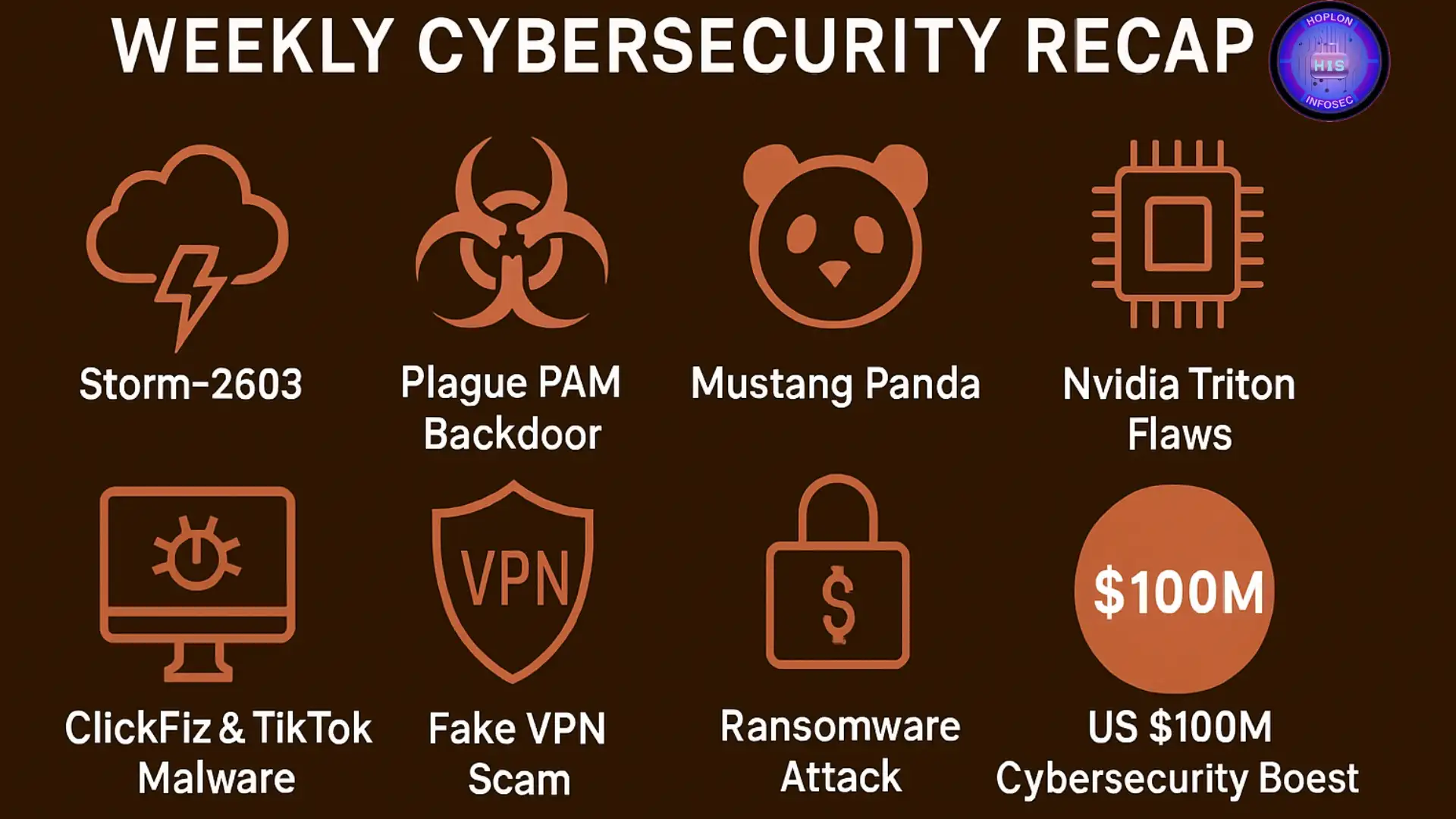
Weekly Cybersecurity Recap In the ever-evolving world of cybersecurity, every week brings new...
Recent Blogs
We’re Here to Secure Your Hard Work
Protect your system from cyber attacks by utilizing our comprehensive range of services. Safeguard your data and network infrastructure with our advanced security measures, tailored to meet your specific needs. With our expertise and cutting-edge technology, you can rest assured.