Cisco Data Breach – Intel Broker Group Stolen 4.5 TB of Data

Hoplon InfoSec
18 Dec, 2024
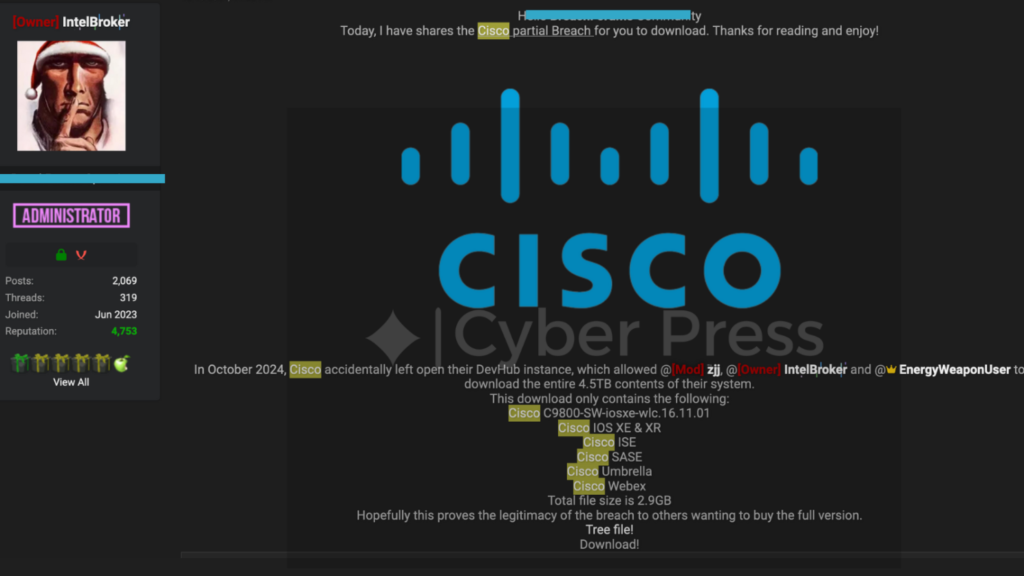
In a significant cybersecurity incident, Cisco Data Breach, a global leader in networking and IT solutions, has reportedly suffered a massive data breach. The breach, attributed to the hacker group IntelBroker, has resulted in the alleged exfiltration of 4.5TB of sensitive data. This incident has sparked widespread concern across the tech and cybersecurity communities.
What Happened about Cisco Data Breach?
The breach reportedly occurred due to an exposed DevOps instance that allowed unauthorized access to Cisco’s sensitive systems. Threat actors identified as “@zjj,” “@IntelBroker,” and “@EnergyWeaponUser” exploited this vulnerability to gain access to proprietary files. Samples of the stolen data, currently being shared within the cybersecurity community, have validated claims of the breach.
The data breach encompasses some of Cisco’s critical product offerings, including:
- Cisco C9800-SW-iosxe-wlc
- Cisco IOS XE & XR
- Cisco Identity Services Engine (ISE)
- Cisco Secure Access Service Edge (SASE)
- Cisco Umbrella
- Cisco Webex
Hackers are reportedly offering this data for sale on the dark web, signaling potential risks for Cisco’s customers and partners.
Implications of the Breach
This breach could have far-reaching consequences for Cisco’s business and reputation. Among the key risks are:
- Exploitation of Proprietary Software: Hackers could leverage stolen data to identify vulnerabilities in Cisco’s software, potentially leading to exploitation.
- Impact on Cisco’s Clients: Organizations relying on Cisco’s technologies, including widely used products like Webex and Umbrella, may face heightened security threats.
- Reputational Damage: The exposure of sensitive systems and data tarnishes trust in Cisco’s ability to safeguard its infrastructure.
The Role of Misconfigured DevOps Environments
This incident highlights a growing trend in cybersecurity breaches: the exploitation of misconfigured or improperly secured DevOps environments. These systems, often housing critical software and configuration files, have become lucrative targets for attackers due to their central role in agile development practices.
Organizations must recognize that leaving DevOps systems exposed or improperly secured opens the door for catastrophic breaches. Stringent security measures, such as access controls, encryption, and regular audits, are essential to mitigating these risks.
What Should Organizations Do?
For businesses utilizing Cisco technologies, proactive measures are crucial:
- Monitor for Vulnerabilities: Stay informed about potential vulnerabilities in Cisco’s products and apply patches as they become available.
- Implement Strong Security Protocols: Secure DevOps environments, enforce least-privilege access, and conduct regular security assessments.
- Stay Alert: Monitor network activity for signs of malicious behavior and ensure that incident response plans are in place.
Looking Ahead
Cisco has yet to release a public statement addressing the breach. In the meantime, cybersecurity experts are closely monitoring the situation, and industry leaders are urging organizations to take proactive steps to secure their systems.
This breach serves as a stark reminder that cybersecurity is not optional—it is critical. As attackers grow more sophisticated, organizations must prioritize robust security measures to protect sensitive data and maintain customer trust.
Share this :