Critical 7-Zip Zero-Day Exploit Alert that could let your Windows at Risk

Hoplon InfoSec
30 Dec, 2024
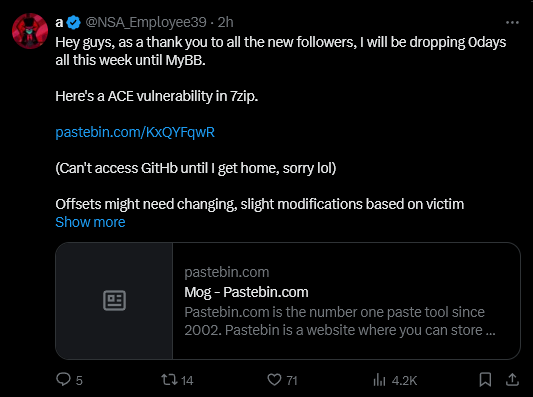
A hacker operating under the alias “NSA_Employee39” on X (formerly Twitter) recently disclosed a severe 7-Zip Zero-Day Exploit in the widely used 7-Zip file compression utility. This vulnerability enables attackers to execute arbitrary code on a victim’s machine when a malicious archive is opened or extracted using the latest version of 7-Zip. This revelation highlights the pressing need for cybersecurity vigilance as it presents significant risks to both individual users and enterprises, particularly in the context of Infostealer malware and supply chain attack vectors.
The Nature of the 7-Zip Zero-Day Exploit
The disclosed zero-day exploit specifically targets the LZMA decoder within 7-Zip. By leveraging a malformed LZMA stream, attackers can trigger a buffer overflow in the RC_NORM function. This exploit allows them to manipulate buffer pointers and payload alignment, resulting in the execution of arbitrary code on the victim’s system.

In practical terms, simply opening or extracting a compromised .7z file using the 7-Zip application could compromise the system. This zero-click vulnerability significantly heightens the threat level as it does not require additional user interaction to execute malicious shellcodes.
Proof of Concept
To demonstrate the exploit, “NSA_Employee39” uploaded a screenshot on Pastebin, showing code that executed a benign payload—launching the Windows Calculator app (calc.exe). While this example may appear harmless, the exploit’s real danger lies in its potential to execute more damaging payloads, such as ransomware or advanced spyware.
Implications for Infostealer Malware Attacks
The 7-Zip vulnerability is particularly concerning for its potential role in spreading Infostealer malware. These malicious programs silently extract sensitive data from infected systems, including login credentials, banking information, and personal details. Infostealers often use social engineering techniques, such as disguising malicious files within password-protected .zip or .rar archives to bypass antivirus detection. However, the new exploit in 7-Zip eliminates these barriers.
Simplified Infection Vector
Attackers can now embed malicious code directly into .7z files. When such a file is opened, the code executes immediately, giving attackers access to the victim’s system without complex methods or password protection. This streamlined infection vector dramatically increases the risk for both individuals and organizations.
Threat to Automated Workflows
The implications extend beyond personal devices. Many organizations automate workflows that involve extracting and processing files received from external sources. A compromised .7z file could infiltrate these automated systems, executing malicious payloads without detection. This could lead to:
- Data Breaches: Exposing sensitive organizational information.
- Ransomware Attacks: Encrypting critical files and demanding payment for their release.
- Operational Disruptions: Halting supply chain processes and other automated operations.
The Broader Impact of Public Disclosure
The public disclosure of this zero-day exploit raises questions about the responsible handling of software vulnerabilities. Typically, vulnerabilities are reported to developers privately, allowing them to release patches before details are made public. In this case, the immediate disclosure gives attackers a window to exploit systems that have yet to be patched.
Potential Escalation: MyBB Zero-Day
Adding to the urgency, “NSA_Employee39” has hinted at releasing another zero-day exploit targeting MyBB, an open-source forum software. Such a disclosure could lead to massive breaches, exposing sensitive databases and online community data. The potential combination of these vulnerabilities underscores developers’ and users’ need for immediate action.
Mitigation Strategies for Users and Organizations
While an official patch for the 7-Zip vulnerability has yet to be released, cybersecurity experts recommend several steps to minimize the associated risks. Both individuals and organizations should adopt a proactive approach to safeguard their systems.
Monitor for Updates
Users should stay informed about updates from the 7-Zip Development Team. Applying patches as soon as they become available is critical to mitigating the risk posed by this zero-day exploit.
Implement File Sandboxing and Scanning
Organizations should deploy sandboxing mechanisms to isolate and analyze files before processing them. Advanced scanning tools can detect malicious payloads embedded in archives, adding a layer of protection.
Raise User Awareness
Conduct training sessions to educate users on the dangers of opening unsolicited or suspicious archive files. Awareness campaigns can significantly reduce the likelihood of users inadvertently activating malicious code.
Strengthen Supply Chain Security
Businesses relying on automated workflows should reassess their security protocols. Implementing stricter validation measures for third-party files can prevent compromised files from infiltrating enterprise systems.
Collaborate Within the Community
The cybersecurity community must work together to analyze and counteract threats. Sharing insights and resources can expedite the development of protective measures against emerging exploits.
The Need for Vigilance
The 7-Zip zero-day is a stark reminder of the vulnerabilities in even the most trusted software. For cybercriminals, it represents a streamlined vector for delivering malware, particularly Infostealers. For defenders, it highlights the urgent need to bolster defenses and maintain vigilance.
Future Developments
Organizations and individuals must remain alert as the cybersecurity community awaits an official fix from 7-Zip developers. The promised disclosure of the MyBB zero-day further emphasizes the importance of proactive cybersecurity measures.
Key Takeaways
- The 7-Zip vulnerability underscores the critical need for regular software updates and robust security practices.
- Public disclosures without prior developer notification can amplify risks, exposing systems to immediate exploitation.
- Infostealer malware and supply chain attack vectors are poised to benefit significantly from this exploit, necessitating heightened awareness and preparedness.
Conclusion
The disclosure of the 7-Zip zero-day exploit marks a pivotal moment in the ongoing battle between cybersecurity professionals and malicious actors. While the vulnerability highlights weaknesses in even the most established software, it also serves as a call to action for users and organizations to strengthen their defenses.
For More:
Share this :