Deep Web and Dark Web Monitoring
What is Deep and Dark Web Monitoring ?
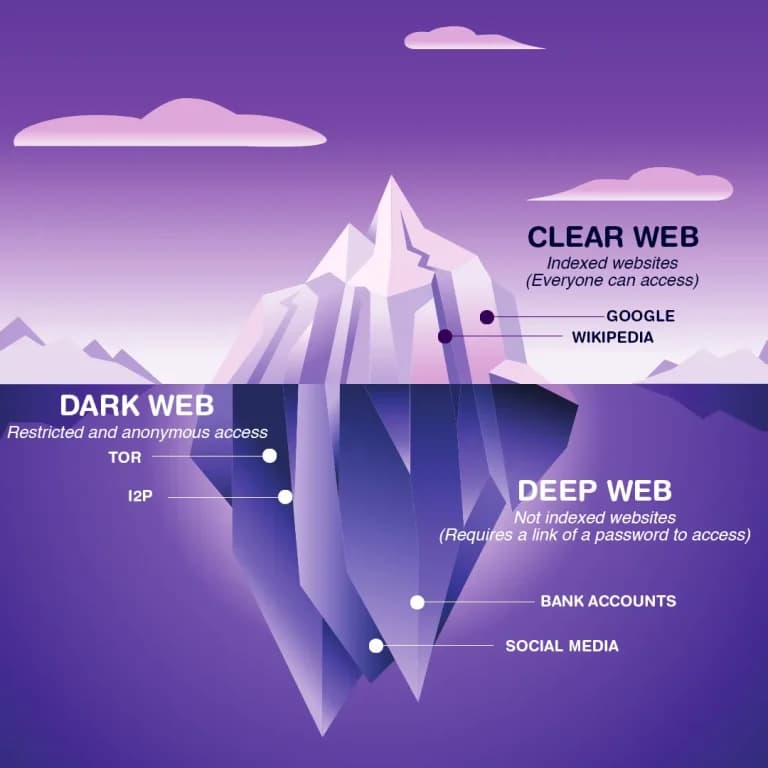
The deep web encompasses parts of the internet not indexed by standard search engines, including private databases and internal networks. The dark web, a subset of the deep web, is intentionally concealed and accessible only through specialized tools like Tor. This hidden realm often hosts illicit activities, including the trading of stolen data and planning of cyberattacks.
Deep and dark web monitoring and Protection Service involves proactively scanning these concealed areas to detect compromised credentials, data leaks, and discussions about potential threats to your organization.
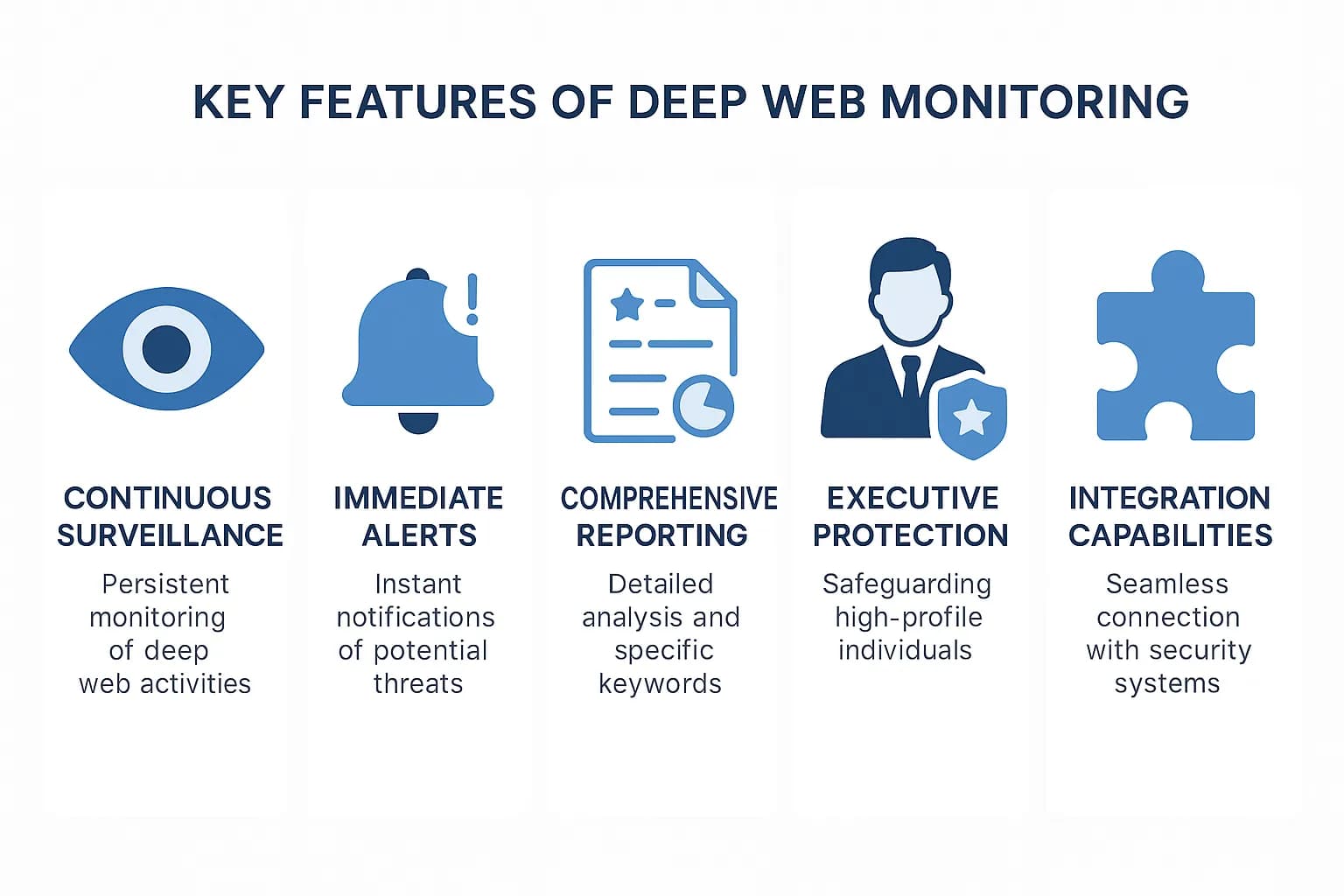
Dark Web Monitoring Service for Individuals:
- Continuous Surveillance: 24/7 monitoring of deep and dark web sources.
- Immediate Alerts: Rapid notification of detected threats or data leaks.
- Comprehensive Reporting: Detailed insights into exposures and recommended actions.
- Custom Watchlists: Tailored monitoring of specific domains, IPs, and keywords.
- Executive Protection: Safeguards high-profile individuals within your organization.
- Integration Capabilities: Compatible with SIEM/SOAR platforms for streamlined operations.
Why Deep and Dark Web Monitoring is Important?
Neglecting to monitor the deep and dark web can leave your organization vulnerable to:
- Credential Theft: Leaked login details can lead to unauthorized access and data breaches.
- Brand Impersonation: Fraudulent use of your brand can erode customer trust.
- Insider Threats: Malicious insiders may leak sensitive information.
- Delayed Breach Detection: Without monitoring, breaches may go unnoticed until significant damage occurs.
Proactive monitoring enables early detection and swift response, mitigating potential risks to your organization’s assets and reputation.

How Does Personal Information Leaked on the Dark Web?
Here are some common ways hackers steal personal information:
- Phishing: Fake emails that look real and trick you into giving away your info.
- Malware and Botnets: Harmful software that sneaks into your system and slowly steals your data.
- Unsecure Wi-Fi: Using public or weak Wi-Fi can let hackers nearby see your information.
- Exploiting Weaknesses: Hackers take advantage of bugs in software to break in and steal data.
- Keylogging: Software that records everything you type, like passwords or credit card numbers.
- Screen Scraping: Taking screenshots of what’s on your screen to steal visible info.

What Does Deep and Dark Web Monitoring Do?
- Discover Leaked Data: Uncover exposed credentials, emails, databases, and documents on dark web forums, marketplaces, and Telegram groups.
- Real-Time Alerts: Get instantly notified when your organization is mentioned or your assets are compromised.
- Takedown Support: Collaborate with legal teams and platforms to remove exposed data and shut down malicious content.
- Threat Actor Tracking: Identify conversations, chatter, or plans targeting your organization or sector.
- Risk Prioritization: Flare’s risk scoring helps prioritize threats based on severity and exploitability.

Hoplon Unified: Complete Zero Trust Endpoint Protection
Hoplon InfoSec presents Hoplon Unified, a comprehensive Zero Trust security suite that integrates all critical tools into one powerful bundle for full endpoint protection and centralized management.
Why Hoplon InfoSec?
- Extensive Coverage: Monitors over 10 million illicit sources, including forums and marketplaces.
- Real-Time Alerts: Immediate notification of threats or data exposures.
- Risk Scoring: Prioritizes threats based on severity and potential impact.
- Takedown Support: Assists in removing malicious content through legal channels.
- Attack Surface Mapping: Identifies and monitors your organization’s exposed digital assets.
- Supply Chain Monitoring: Extends protection to your vendors and partners.
- Brand Protection: Detects and addresses brand impersonation and phishing attempts.
- Advanced Dashboard: Offers intuitive insights into threats and exposures.
- API Integration: Seamlessly integrates with your existing cybersecurity tools for real-time intelligence.

Flexible, Affordable Security That Scales With You
Frequently Asked Questions
Everything you need to know about Deep Web and Dark Web Monitoring
We're Here to Secure Your
Hard Work
Protect your system from cyber attacks by utilizing our comprehensive range of services. Safeguard your data and network infrastructure with our advanced security measures, tailored to meet your specific needs. With our expertise and cutting-edge technology, you can rest assured that your system is fortified against any potential threats. Don't leave your security to chance – trust our proven solutions to keep your system safe and secure.
Share this :