Discover 100+ LTE & 5G Vulnerabilities Threatening Security
Hoplon InfoSec
24 Jan, 2025
Rapid advancements in mobile communication technologies like LTE and 5G have transformed how we connect and interact. These networks power everything from personal communication to business operations and emergency services, making them critical to modern infrastructure. However, a recent study by researchers from the University of Florida and North Carolina State University has exposed alarming vulnerabilities in LTE and 5G implementations that could jeopardize their reliability and security.
Analyzing LTE and 5G Vulnerabilities: Key Findings
The research team conducted a comprehensive analysis of seven LTE implementations, including Open5GS, Magma, and OpenAirInterface, as well as three 5G implementations. Their findings revealed 119 vulnerabilities, many allowing attackers to compromise cellular core systems remotely.
Shockingly, every system tested exhibited critical flaws, demonstrating a widespread issue across open-source and proprietary platforms. These vulnerabilities pose significant risks, ranging from localized service disruptions to nationwide network compromise.
The Scale of the Threat: Over 100 Vulnerabilities Identified
Each identified vulnerability can cause large-scale damage, such as city-wide denial of service (DoS) attacks. By exploiting these flaws, attackers can disrupt critical components of cellular networks:
- LTE Networks: Attackers could crash the Mobility Management Entity (MME), a core component responsible for managing subscriber connections and mobility.
- 5G Networks: Similar attacks could target the Access and Mobility Management Function (AMF), causing widespread disruptions.
Alarmingly, initiating such an attack requires sending a single malicious data packet. This can be done without a SIM card or authentication, making it easier for attackers to exploit. Once triggered, these disruptions could last until network operators identify and patch the vulnerabilities, leaving millions without phone, messaging, or internet services.
Systemic Issues Across Public and Private Networks
The vulnerabilities are not limited to open-source platforms. Proprietary systems used in commercial networks are equally affected, highlighting a systemic issue across public and private cellular infrastructures. This underscores the urgent need for comprehensive security measures to address the risks inherent in modern telecommunications.
Remote Access Risks: Espionage and Sabotage

In addition to causing service disruptions, some vulnerabilities allow attackers to gain unauthorized access to the cellular core network. These flaws enable buffer overflows and memory corruption, opening the door for adversaries to execute malicious activities such as:
- Monitoring the location and connection data of subscribers within a city.
- Conducting targeted attacks on specific individuals.
- Compromising critical network components like the Home Subscriber Service (HSS) or Unified Data Management (UDM), potentially escalating the scale of disruptions to a national level.
To demonstrate the severity of these risks, the researchers developed a proof-of-concept remote code execution (RCE) exploit targeting one of the vulnerabilities in SD-Core. This proof of concept is a stark reminder of the potential for exploitation if these vulnerabilities remain unaddressed.
Two Primary Threat Models
The researchers identified two primary threat models that categorize the vulnerabilities discovered in LTE and 5G implementations:
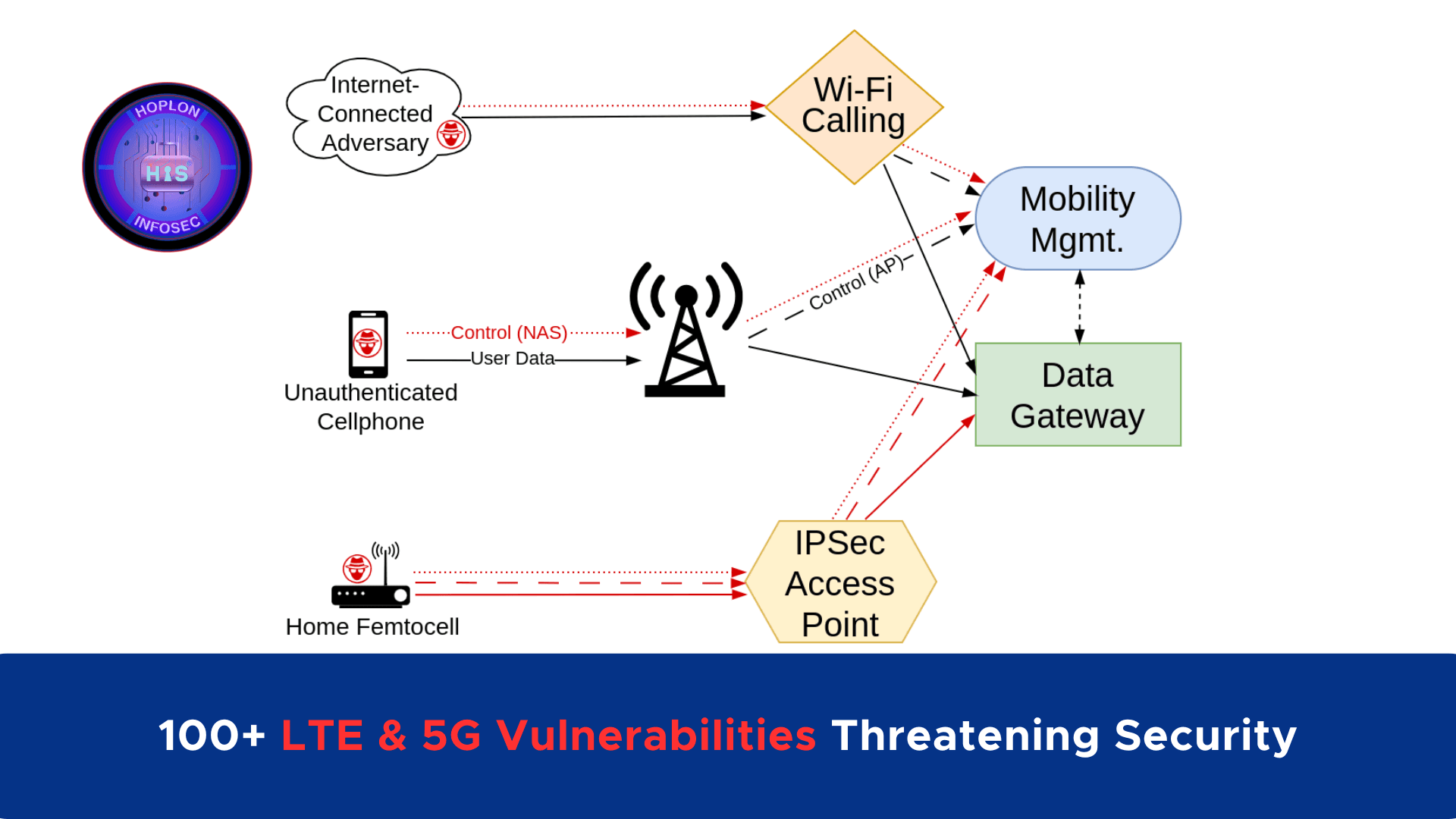
1. Unauthenticated Device Exploits
Attackers can exploit vulnerabilities using any mobile device capable of sending malformed data packets. This risk is amplified by the rise of Wi-Fi Calling services, which allow attackers to launch attacks remotely over the internet. By bypassing traditional geographic limitations, such attacks could target cellular networks from anywhere in the world.
2. Base Station Exploits
Adversaries with access to compromised base stations or femtocells can exploit misconfigurations or leaked IPsec keys to infiltrate the cellular core. The growing deployment of smaller 5G base stations in easily accessible locations further exacerbates this risk, as these stations may be more vulnerable to physical tampering or misconfiguration.
Responsible Disclosure and Vendor Response
The team adhered to responsible disclosure protocols that aligned with ethical research practices. They notified affected vendors and provided a 90-day window for patches before publicly disclosing their findings.
However, not all vendors responded to these notifications. For example, in NextEPC and SD-Core cases, the researchers released patches directly through GitHub alongside their public disclosures to ensure network operators could mitigate the risks.
The Broader Implications: A Threat to Public Safety
Cellular networks are integral to modern life, supporting emergency services, businesses, and personal communication. The ability to disrupt these networks at scale represents a significant threat to public safety and national security.
As 5G adoption accelerates, its integration with legacy LTE infrastructure exacerbates these vulnerabilities. This implements robust security measures that are more critical than ever. Without immediate action, the promise of next-generation connectivity could be overshadowed by its vulnerabilities.
Proactive Measures to Secure Cellular Networks
The findings of this research serve as a call to action for the telecommunications industry to prioritize security. Here are some key steps that can help safeguard cellular networks:
1. Regular Vulnerability Assessments
Telecommunications providers must conduct frequent and thorough vulnerability assessments to identify and address potential weaknesses in their systems. This includes testing both open-source and proprietary platforms to ensure comprehensive security coverage.
2. Adoption of Zero-Trust Architectures
Implementing a zero-trust architecture can significantly reduce the risk of unauthorized access. This approach minimizes the chances of exploitation, even if vulnerabilities exist, by requiring continuous verification of user and device identities.
3. Stringent Security Protocols
Network operators should enforce stringent security protocols, such as encrypted communication, secure key management, and robust access controls. These measures can help protect critical components from unauthorized access and tampering.
4. Collaboration and Knowledge Sharing
The telecommunications industry must foster a culture of collaboration and knowledge sharing to address emerging threats effectively. By working together, industry stakeholders can develop and implement best practices for securing cellular networks.
Conclusion
The vulnerabilities uncovered in LTE and 5G implementations highlight the urgent need for enhanced security measures across the telecommunications industry. As cellular networks become increasingly integral to modern life, their reliability and security must be prioritized.
Proactive measures, such as regular vulnerability assessments, zero-trust architectures, and stringent security protocols, are essential to safeguarding these networks from increasingly sophisticated cyber threats. Without immediate action, the risks posed by these vulnerabilities could outweigh the benefits of next-generation connectivity.
The research is a stark reminder that a commitment to security must match the promise of innovation. By addressing these vulnerabilities now, we can ensure a safer and more reliable future for mobile communication.
For more:
https://cybersecuritynews.com/100-vulnerabilities-in-lte-5g-implementations/
Share this :