EDDIESTEALER: The Rise of a Rust-Based Infostealer in CAPTCHA Campaigns

Hoplon InfoSec
01 Jun, 2025
In the ever-evolving landscape of cybersecurity threats, a new player has emerged, leveraging modern programming languages and sophisticated social engineering tactics. Dubbed EDDIESTEALER, this Rust-based infostealer has been identified by Elastic Security Labs as a significant threat, primarily distributed through deceptive CAPTCHA verification pages. This comprehensive analysis delves into the intricacies of EDDIESTEALER, its deployment mechanisms, technical architecture, and the broader implications for cybersecurity.
EDDIESTEALER represents a novel approach in the realm of infostealers, utilizing the Rust programming language to enhance stealth, stability, and resistance against traditional analysis workflows. Its primary objective is to harvest sensitive data, including credentials, browser information, and cryptocurrency wallet details, from Windows hosts.
Distribution via Deceptive CAPTCHA Campaigns
The initial vector for EDDIESTEALER involves compromised websites deploying obfuscated React-based JavaScript payloads that mimic legitimate CAPTCHA systems, such as Google’s reCAPTCHA. These fake CAPTCHAs serve as gateways for malware, leveraging social engineering to deceive users.
Attack Chain Overview:
Fake CAPTCHA Presentation: Users encounter a prompt like “Verify you are a human,” blending seamlessly into compromised websites.
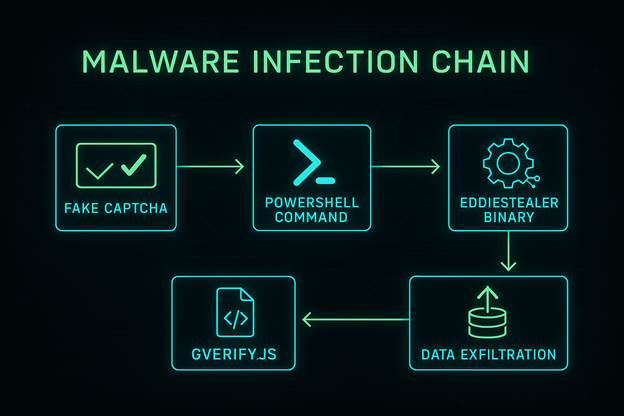
Clipboard Manipulation: The malicious JavaScript uses document.execCommand(“copy”) to copy a PowerShell command into the user’s clipboard.
User Execution: Users are instructed to press Windows + R, paste the clipboard contents, and press Enter, executing the malicious PowerShell command.
Payload Retrieval: The command downloads a second-stage payload (gverify.js) from an attacker-controlled domain (e.g., hxxps://llll.fit/version/) and saves it to the user’s Downloads folder.
Compromised Websites: Threat actors compromise legitimate websites, injecting obfuscated React-based JavaScript payloads.
Execution of gverify.js: The script is executed using cscript in a hidden window, which then fetches the EDDIESTEALER executable from hxxps://llll.fit/io, saving it under a pseudorandom 12-character filename.
This method exploits user trust and browser familiarity, facilitating the stealthy delivery of the infostealer.
Technical Architecture EDDIESTEALERand Obfuscation Techniques
EDDIESTEALER’s architecture is meticulously designed to evade detection and complicate analysis. Key features include:
String Obfuscation: To hinder static analysis, EDDIESTEALER encrypts most strings using a simple XOR cipher. Decryption occurs at runtime, with each routine utilizing distinct key derivation functions. Additionally, the malware employs a custom WinAPI lookup mechanism, dynamically resolving API calls and caching them for efficiency.
API Obfuscation: The malware utilizes a custom WinAPI lookup mechanism, decrypting module and function names at runtime, and dynamically loading required modules using a custom LoadLibrary wrapper.
Mutex Creation: To prevent multiple instances, EDDIESTEALER creates a mutex using a decrypted UUID string, ensuring only one instance runs at a time.
Sandbox Detection: A basic check assesses whether the total physical memory exceeds ~4.0 GB. If not, the malware deletes itself, avoiding execution in sandbox environments.
Self-Deletion: The malware can delete itself through NTFS Alternate Data Streams renaming, bypassing file locks. This technique involves renaming the default stream $DATA to :metadata, then setting a “delete on close handle” flag to remove the file upon closing. These techniques collectively enhance the malware’s stealth and persistence.
Command and Control (C2) Communication
Upon execution, EDDIESTEALER communicates with its C2 server to receive configuration data and exfiltrate collected information. The process involves:
Configuration Retrieval: An HTTP GET request is sent to the C2 server, retrieving AES CBC encrypted and Base64 encoded configuration data. The AES key for decryption is stored unencrypted within the binary.
Task Execution: The decrypted configuration contains a list of tasks targeting specific data, such as crypto wallets, browsers, password managers, FTP clients, and messaging applications.
Data Exfiltration: Collected data is encrypted and transmitted to the C2 server via HTTP POST requests, following a distinct pattern characterized by multiple, task-specific POST requests.

This communication strategy allows for dynamic task assignment and efficient data exfiltration.
Targeted Applications and Data
EDDIESTEALER is configured to target a wide array of applications and data types, including:
Cryptocurrency Wallets: Files associated with wallets like Armory, Bitcoin, WalletWasabi, Daedalus Mainnet, Coinomi, Electrum, Exodus, DashCore, ElectronCash, Electrum-DASH, Guarda, and Atomic.
Web Browsers: User data from browsers such as Microsoft Edge, Brave, Google Chrome, and Mozilla Firefox, including history, bookmarks, cookies, and login data.
Password Managers: Data from applications like Bitwarden, 1Password, and KeePass.
FTP Clients: Configuration files from clients like FileZilla, FTP Manager Lite, FTPbox, FTP Commander Deluxe, Auto FTP Manager, 3D-FTP, FTPGetter, and Total Commander.
Messaging Applications: Data from Telegram Desktop.
EDDIESTEALER reads the targeted files using standard Windows API functions, encrypts the data using AES encryption, and transmits it to the C2 server in separate HTTP POST requests for each completed task
Advanced Capabilities and Variants
Recent variants of EDDIESTEALER exhibit additional capabilities:
System Profiling: Collecting information such as running processes, GPU details, number of CPU cores, CPU name, and vendor.
Modified C2 Communication: In some instances, the malware sends host system information to the C2 server before requesting its configuration, allowing the server to withhold tasks if a sandbox environment is detected.
Hardcoded AES Keys: Later versions have hardcoded AES keys for both client-to-server and server-to-client communication, eliminating the need to retrieve them dynamically.
Function Inlining: Extensive use of function inline expansion, resulting in larger functions and complicating code analysis.
Chrome DevTools Protocol Exploitation: To extract credentials from Chrome’s Password Manager, EDDIESTEALER spawns a new Chrome process with the remote-debugging-port flag, enabling DevTools Protocol over a local WebSocket interface. It then opens the internal password manager page, causing Chrome to decrypt and load stored credentials into memory, which the malware subsequently extracts.

These enhancements indicate active development and adaptation by threat actors to improve the malware’s effectiveness and stealth.
Detection and Mitigation Strategies
Elastic Security Labs has developed YARA rules and behavioral prevention rules to detect EDDIESTEALER:
YARA Rule: Windows.Infostealer.EddieStealer
Behavioral Prevention Rules:
Suspicious PowerShell Execution
Ingress Tool Transfer via PowerShell
Potential Browser Information Discovery
Potential Self Deletion of a Running Executable
Implementing these rules within security solutions can aid in early detection and prevention of EDDIESTEALER infections.
Broader Implications and Trends
EDDIESTEALER’s emergence underscores several broader trends in cybersecurity:
Adoption of Modern Programming Languages: The use of Rust reflects a shift towards languages that offer enhanced memory safety and performance, complicating traditional analysis techniques.
Sophisticated Social Engineering: Leveraging familiar interfaces like CAPTCHA challenges increases the likelihood of user interaction and malware execution.
Dynamic Malware Capabilities: The ability to receive task lists and adapt targets indicates a move towards more flexible and customizable malware frameworks.
These trends highlight the need for continuous evolution in defensive strategies and user education to counteract increasingly sophisticated threats.
Conclusion
EDDIESTEALER represents a significant advancement in infostealer malware, combining modern programming techniques with effective social engineering to compromise systems and exfiltrate sensitive data. Its modular architecture, obfuscation strategies, and dynamic capabilities pose substantial challenges to detection and analysis. As threat actors continue to innovate, it is imperative for cybersecurity professionals to stay informed and adapt their defenses accordingly.
Did you find this article helpful? Follow us on Twitter and LinkedIn for more Cyber Security news and updates. Stay connected on Facebook and Instagram as well. At Hoplon Infosec, we’re committed to securing your digital world.
Share this :