Endpoint Security

What is an Endpoint Security Solution?
Endpoint security is a cybersecurity approach focused on protecting network endpoints, such as desktops, laptops, smartphones, tablets, and other devices that connect to a network. These endpoints are often vulnerable points through which cyber threats can enter an organization’s network, making them a prime target for cyberattacks.
Endpoint security protects devices like laptops, desktops, and mobile phones from cyber threats, offering a cost-efficient and customizable solution to meet the needs of businesses of all sizes.
Top Benefits of Endpoint Security :
- Real-Time Threat Protection: Defends devices from malware, ransomware, phishing, and other cyberattacks.
- Centralized Management: Allows IT teams to monitor and control all endpoints from one dashboard.
- Remote Work Security: Secures devices outside the office, supporting remote and hybrid work environments.
- Faster Incident Response: Quickly detects, contains, and responds to threats to minimize damage.
- Regulatory Compliance: Helps meet data protection standards like GDPR, HIPAA, and ISO 27001.
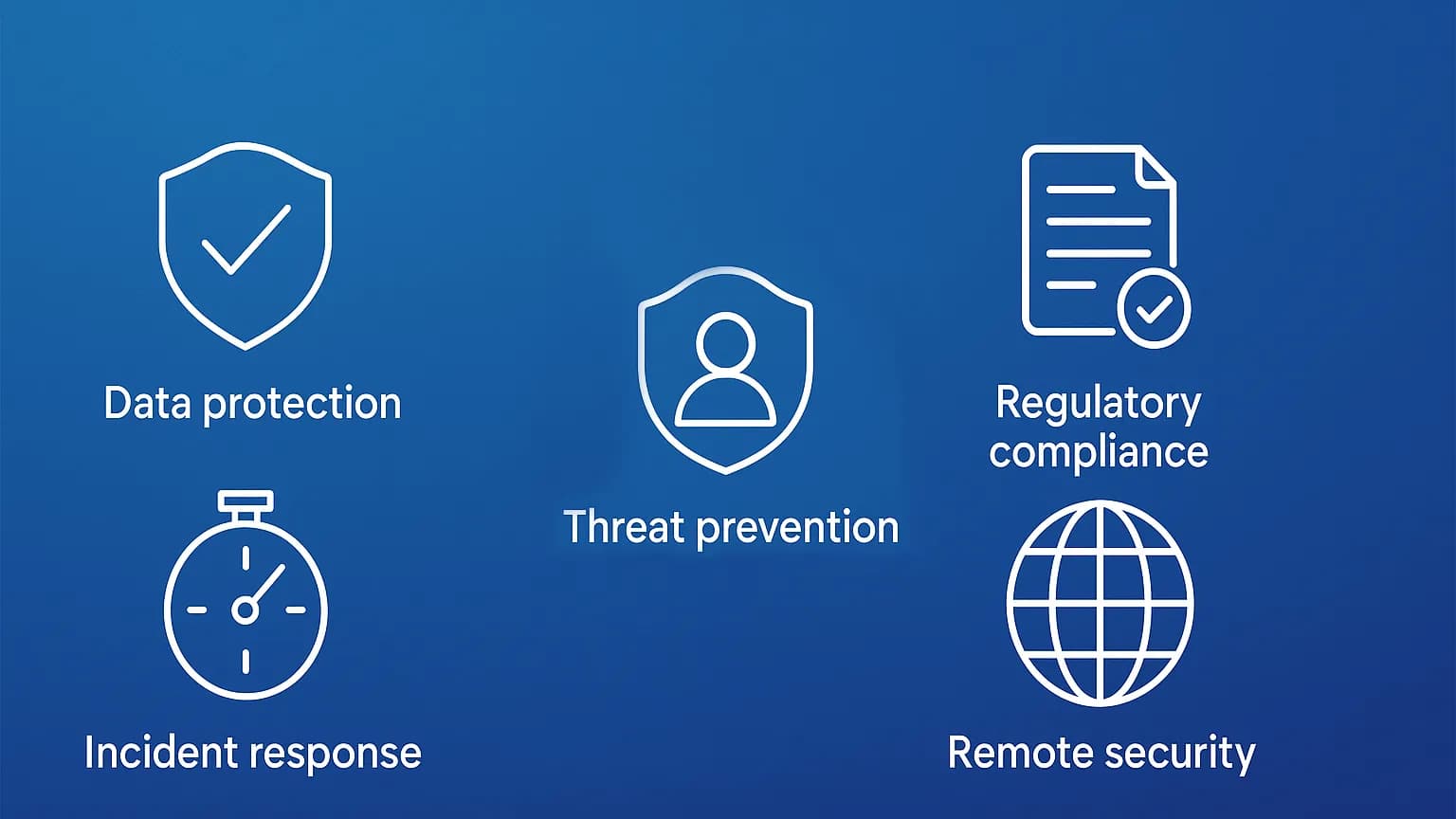
Why Endpoint Protection Service is Important?
Here’s a concise rundown of why endpoint security (edr) matters:
- Block Initial Attacks: Stops malware, phishing, and zero‑day exploits before they run.
- Contain Breaches: Detects suspicious behavior, isolates infected hosts, and prevents lateral movement.
- Protect Data: Monitors and controls copying or transmission of sensitive files (DLP).
- Defeat Ransomware: Recognizes and halts encryption activity in real time; rolls back changes.
- Ensure Compliance: Enforces encryption, access controls, and provides audit logs for GDPR, HIPAA, PCI‑DSS, etc.
- Support Remote Work: Agents travel with devices, enforcing policy and updates anywhere.
- Reduce Costs & Complexity: Centralized management automates patching, detection, and response, lowering MTTR.
- Stop Advanced Threats: Uses ML and behavioral analytics to catch fileless malware and stealthy attacks.
- Maintain Uptime: Automated containment and remediation keep critical services running.
- Build Trust: Strong endpoint defenses protect your brand and reassure customers and partners.

How Endpoint Security Solutions Works?
Hoplon Unified: Complete Zero Trust Endpoint Protection
Hoplon InfoSec presents Hoplon Unified, a comprehensive Zero Trust security suite that integrates all critical tools into one powerful bundle for full endpoint protection and centralized management.
Hoplon Unified is the all-in-one solution for organizations seeking to harden their environment and enforce Zero Trust—efficiently, intelligently, and securely.
Flexible, Affordable Security That Scales With You
Frequently Asked Questions
Everything you need to know about Endpoint Security
We're Here to Secure Your
Hard Work
Protect your system from cyber attacks by utilizing our comprehensive range of services. Safeguard your data and network infrastructure with our advanced security measures, tailored to meet your specific needs. With our expertise and cutting-edge technology, you can rest assured that your system is fortified against any potential threats. Don't leave your security to chance – trust our proven solutions to keep your system safe and secure.
Share this :