Gap Assessment
What is a Cybersecurity Gap Assessment?
A security gap assessment or security gap analysis measures the organization’s current security state and the desired state. It helps to flag areas that have to be improved, shows clarity areas of weakness in respect to security and how to deal with the lapses effectively. This proactive approach helps assess your current security posture and align it with industry-recognized security standard.
Why Gap Assessment is Important for Businesses?

How It Supports Compliance (NIST, ISO 27001, HIPAA)
A gap assessment plays a vital role in helping organizations meet cybersecurity compliance requirements. It evaluates your current security posture against industry standards such as NIST, ISO 27001, or HIPAA, identifying areas where your organization falls short.
By combining risk identification with compliance benchmarking, a gap assessment gives a complete roadmap. This process helps us to reduce legal risk, and demonstrating due diligence to stakeholders, auditors, and regulators.
Cybersecurity Risk Assessment and Gap Analysis
A cybersecurity risk assessment helps identify potential threats and evaluates their likelihood and impact on your business. A gap analysis complements this by evaluating your organization’s current capability to handle these identified threats. Together, these two processes provide a complete picture of where your business is vulnerable and how to effectively improve your cybersecurity defenses.
What Does Gap Assessment Evaluate in a Company’s Security?
Comprehensive gap analysis involves an evaluation of various elements of an organization’s cybersecurity, considering the existing security protocols, the training system of employees, the IT infrastructure, the network and endpoint security, the data encryption mechanism, and disaster plans. By closely examining these areas, organizations can gain a comprehensive understanding of their overall cybersecurity health.
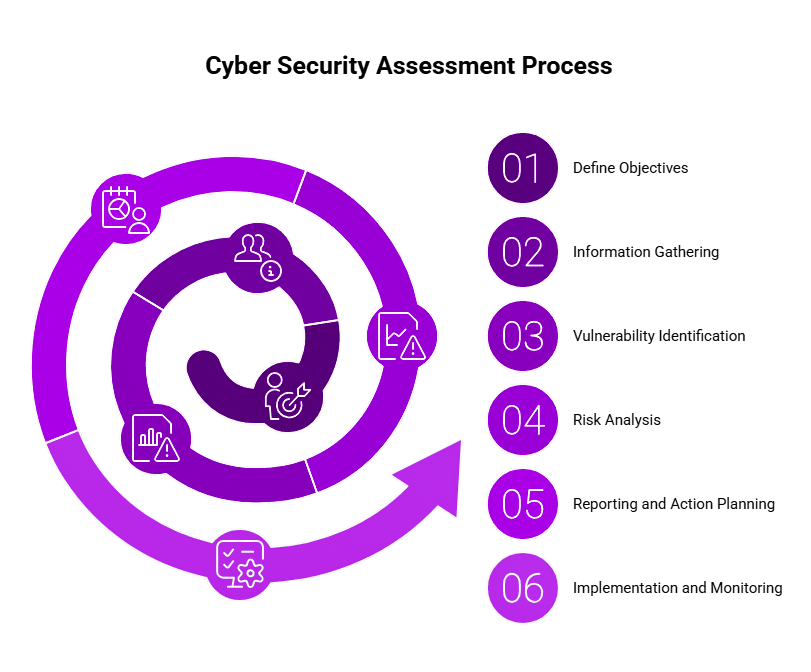
Steps to Conduct an Effective Gap Assessment

Effective Gap Analysis Strategies for Cybersecurity
A proper cybersecurity gap analysis must have well specified goals, and exhaustive documentation. Companies ought to seek many stakeholders from different departments, so that they obtain different views on security shortcomings. Periodical updates and reviews of the gap assessment procedure also enable organizations to adjust to the emerging threats, which permit them to retain cybersecurity strength.
Applying the industry-validated framework of cybersecurity, such as NIST, ISO 27001, CIS Controls, among others, can steer businesses through a more structured procedure of conducting the gap assessment, which will have a clear definition of the gaps that require some work and some common guidelines and benchmarks to compare to.
Gap Assessment for IT Infrastructure
How Gap Anlysis Helps in Identifying Vulnerabilities
A security gap analysis is a procedure in which the practices, procedures, and technologies in the organization are reviewed methodically. Investigating configurations, policies, and other security tools in use, businesses are able to find out security misconfigurations, unpatched software, and low-security measures. It is also obvious that when such vulnerabilities are clearly documented, organizations have a better chance of prioritizing them and dedicating their resources effectively.
One of the most common issue is the lack of visibility and coordination between different security layers; such as endpoints, networks, and cloud environments. Under these circumstances, implementing a solution such as Extended Detection and Response (XDR) can be highly effective in helping an organization substantially mitigate its capacity to monitor, detect, study, and react to threats within a reasonable time.
Cybersecurity Audit vs Gap Assessment

Benefits of a Gap Assessment
There are several practical purposes of carrying out cybersecurity gap assessment. Organizations have a great opportunity to enhance their cybersecurity posture, become compliant in a more effective way, and minimize cyberattack-related risks. Transparent, specific information obtained as the result of examinations allows companies to develop feasible implementation plans of cybersecurity enhancement. In general, such evaluations greatly improve the abilities posed by an organization to counter emerging threats.
How Gap Assessments Improve Security Posture
How to Prepare for a Gap Assessment
A successful gap assessment process takes place with proper preparation. Businesses ought to have clearly outlined assessment aims, collection of appropriate security records, and engage IT, security, and management party members in the early stages. Streamlined schedules and duties guarantee a smooth process with minor disturbances and maximum efficiency of the gap assessment process.
Why Partner with Professionals for Gap Assessments?
Most organizations gain an advantage by collaborating with cybersecurity professionals on gap assessments. Expert assessments offer objective widespread information on security practices. Professionals enable organizations to respond to sophisticated security issues and the need to meet compliance requirements within a short period by applying the most recent cybersecurity knowledge and practice. By taking advantage of expert knowledge, you can better evaluate the gaps and provide practical, reliable, and sustainable benefits to the security of your cybersecurity.
Why Hoplon?
Frequently Asked Questions
Everything you need to know about Gap Assessment
We're Here to Secure Your
Hard Work
Protect your system from cyber attacks by utilizing our comprehensive range of services. Safeguard your data and network infrastructure with our advanced security measures, tailored to meet your specific needs. With our expertise and cutting-edge technology, you can rest assured that your system is fortified against any potential threats. Don't leave your security to chance – trust our proven solutions to keep your system safe and secure.
Share this :