Hackers Exploiting VSCode Remote Tunnels

Hoplon InfoSec
18 Jan, 2025
VSCode Remote Tunnels is a cutting-edge feature of Visual Studio Code (VSCode), a widely-used integrated development environment (IDE). It allows developers to access their local coding environment remotely, enhancing flexibility and convenience. While this functionality offers substantial benefits to the developer community, it has also emerged as a potential avenue for exploitation by malicious actors. This blog will explore how VSCode Remote Tunnels are being misused and how organizations can protect themselves from such threats.
What Are VSCode Remote Tunnels?
VSCode Remote Tunnels are designed to enable developers to connect to their local development environments securely from remote locations. This feature eliminates the need for complex configurations or VPNs, making it easier for developers to engage with their code, no matter where they are. Using the Visual Studio Code Command Line Interface (CLI), developers can set up a tunnel to seamlessly access their projects and workflows.
However, this feature’s simplicity and accessibility have made it an attractive target for cybercriminals. Malicious actors have discovered ways to abuse VSCode Remote Tunnels to gain unauthorized access to devices, steal sensitive information, and deploy malware.
How Are Malicious Actors Abusing VSCode Remote Tunnels?
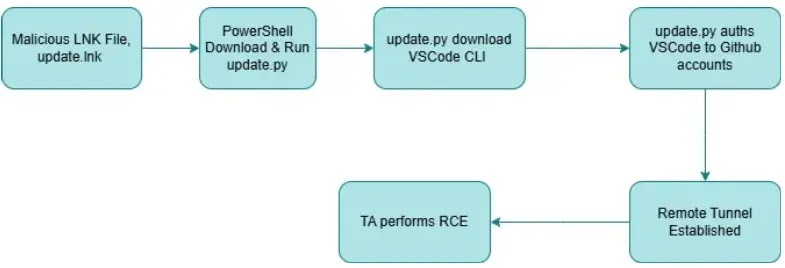
Threat actors exploit the VSCode Remote Tunnels feature by delivering malicious payloads that trick users into unwittingly installing compromised scripts. Let’s delve into the detailed process of how these attacks unfold.
1. Delivery of Malicious LNK Files
The attack begins with the delivery of a malicious LNK (shortcut) file. When the user clicks on this file, a PowerShell command embedded within it is executed. This command downloads and runs a Python script from a remote IP address. The simplicity of this method underscores how attackers can leverage seemingly innocuous files to initiate their campaigns.
2. Downloading and Executing VSCode CLI Binaries
The downloaded Python script facilitates the next phase of the attack. It retrieves and executes the VSCode CLI binary, specifically code-insiders.exe. This binary is essential for creating and authenticating the VSCode Remote Tunnel.
3. Establishing the Remote Tunnel
Using the VSCode CLI binaries, the Python script connects to GitHub to authenticate the remote tunnel. Once authenticated, the attacker accesses a list of remote hosts with active tunnels. This is insidious because it allows the threat actor to identify and target victim machines running active VSCode Remote Tunnels.
4. Exploiting the Victim’s Device
The attacker can connect to the active VSCode tunnel on that device by selecting a victim host. This enables them to traverse directories on the victim’s computer, create new files, execute scripts remotely, and even deploy additional malware. The level of access provided by these tunnels makes them a powerful tool for cybercriminals to accomplish their objectives.
Consequences of Exploiting VSCode Remote Tunnels
The misuse of VSCode Remote Tunnels can have severe consequences for individuals and organizations. Here are some potential risks associated with these attacks:
1. Unauthorized Data Access
Attackers can steal confidential information, including sensitive project files, intellectual property, and personal data. This stolen data can be used for corporate espionage, identity theft, or sold on the dark web.
2. Deployment of Malware
Once attackers gain access to a device, they can deploy malware to disrupt operations, steal additional data, or establish a persistent backdoor for future access.
3. Lateral Movement Across Networks
With access to a compromised device, attackers can move laterally across an organization’s network. This increases the scope of the attack, potentially compromising multiple systems and critical infrastructure.
4. Damage to Development Environments
By manipulating the victim’s development environment, attackers can introduce vulnerabilities, alter source code, or disrupt ongoing projects. This can have a cascading effect on the organization’s software development lifecycle.
Mitigating the Risk: Best Practices for Organizations
To prevent the abuse of VSCode Remote Tunnels, organizations must adopt proactive measures to safeguard their development environments and sensitive data. Here are some recommended strategies:
1. Restrict Tunnel Access
Limit the use of VSCode Remote Tunnels to authorized users within your organization. Restricting access to your tenant can reduce the risk of unauthorized connections.
2. Monitor Network Activity
Implement robust monitoring tools to detect unusual network activity. Alerts for unauthorized access attempts, unusual file modifications, or connections to suspicious IP addresses can help identify potential threats early.
3. Educate Developers
Ensure your development team knows the risks associated with VSCode Remote Tunnels and similar features. Training developers to recognize phishing attempts and malicious files can help prevent attacks at the initial stages.
4. Implement Endpoint Protection
Deploy endpoint security solutions to detect and block malicious scripts or binaries. These tools can provide an additional layer of defense against attacks initiated through LNK files or other entry points.
5. Use Access Controls
Enforce strict access controls for development tools and environments. Multi-factor authentication (MFA) and role-based access control (RBAC) can prevent unauthorized users from accessing critical resources.
6. Regularly Update Software
Ensure that your development tools, including VSCode, are always current. Software updates often include patches for vulnerabilities that attackers could exploit.
7. Disable Unused Features
If VSCode Remote Tunnels are not essential for your organization, consider eliminating this feature. Minimizing the attack surface can significantly reduce the likelihood of exploitation.
Proactive Measures for Individual Developers
Individual developers can also take steps to protect themselves from becoming victims of VSCode Remote Tunnel abuse. Here’s what you can do:
- Avoid Suspicious Files: Do not open LNK files or other attachments from unknown sources.
- Verify File Integrity: Check the authenticity of files and scripts before running them on your system.
- Enable Firewall Rules: Use firewalls to block unauthorized connections to your device.
- Review Tunnel Configurations: Review and manage your tunnel settings to ensure they align with security best practices.
Conclusion
Threat actors’ abuse of VSCode Remote Tunnels highlights the importance of balancing functionality and security in modern development tools. While features like remote tunnels enhance developer productivity, they also introduce potential risks that must be addressed proactively.
By understanding the tactics employed by attackers and implementing robust security measures, organizations, and individual developers can safeguard their devices, data, and development environments from these emerging threats. Staying informed and vigilant is the key to effectively navigating the evolving cybersecurity landscape.
For more:
https://cybersecuritynews.com/hackers-abusing-microsoft-vscode-remote-tunnels/
Share this :