Researchers Leverage HTTP Range Header to Circumvent Browser Restrictions
Hoplon InfoSec
22 Dec, 2024
The HTTP Range header allows clients to request specific portions of a resource from a server. While this functionality is beneficial for optimizing data transfer and improving user experience, malicious actors can also manipulate it to circumvent browser security measures. This document explores how reflected input can be exploited through the HTTP Range header and the potential risks associated with this technique.
In a groundbreaking discovery, security researchers have demonstrated a method to exploit previously untouchable reflected input vulnerabilities by leveraging HTTP Range headers. This novel approach transforms these vulnerabilities into fully functional attack vectors, challenging long-held assumptions about the security of web applications.
Traditionally, reflected input vulnerabilities have posed a moderate concern due to their inherent limitations. These flaws typically rely on the context in which malicious input is reflected, making exploitation complex and often impractical. However, the new technique effectively circumvents these barriers, opening up an alarming avenue for attackers to exploit previously deemed safe web applications.
The findings serve as a wake-up call for developers, security professionals, and organizations. Once considered secure, web applications must now be reassessed to address this emerging threat vector. As attackers continue to innovate, the need for proactive measures and robust security frameworks has never been more critical to safeguard sensitive data and maintain user trust.
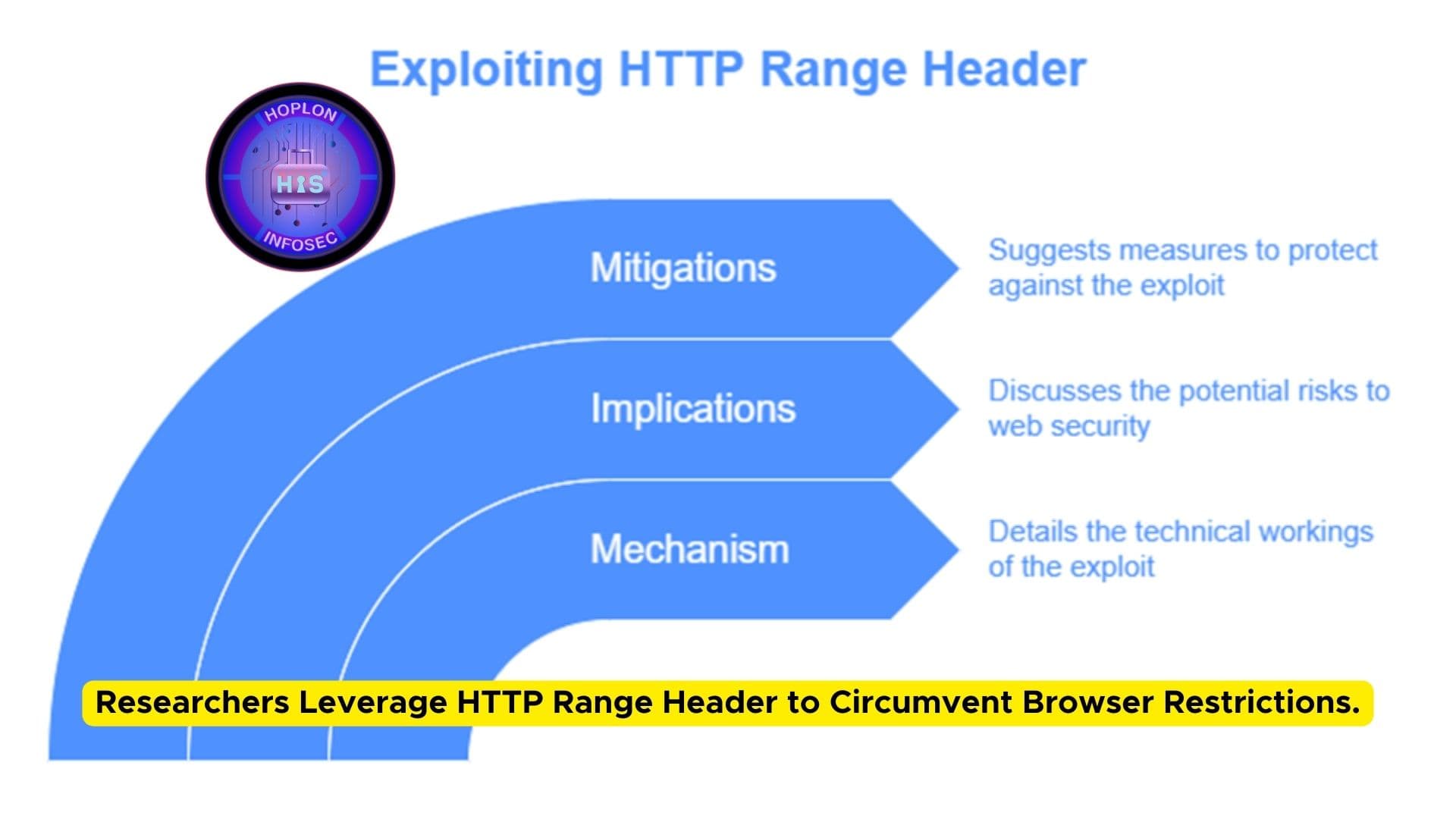
Mechanism of the Exploit
Reflected Input: The exploit begins with the attacker crafting a request that includes reflected input, which is data sent by the user that is echoed back by the server.
HTTP Range Header Manipulation: By manipulating the HTTP Range header, the attacker can request specific byte ranges of a resource, potentially leading to unintended behavior or information disclosure.
Bypassing Restrictions: Many browsers implement restrictions to prevent cross-origin resource sharing (CORS) and other security measures. However, by exploiting the Range header, attackers can bypass these restrictions, gaining access to sensitive data or functionalities.
The Attack’s Process
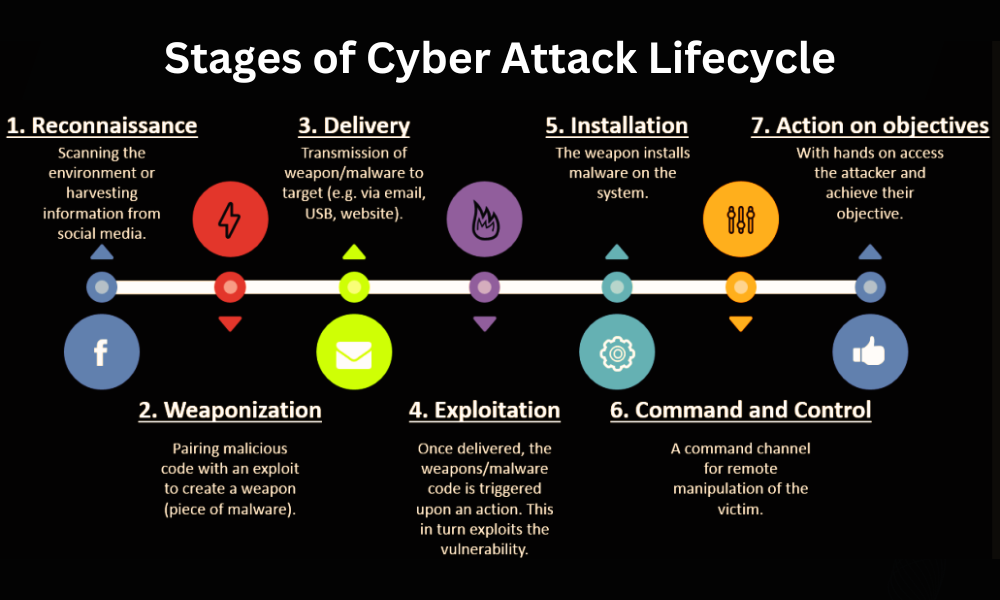
This attack works by targeting web endpoints that reflect user input in their HTTP responses but in a way that seems harmless or unusable for malicious purposes. These responses often include input within parts of the page, such as HTML attributes, which don’t directly pose a threat due to built-in browser protections.
Next, the attacker tests whether the same endpoint supports the Range HTTP header. This header typically requests specific portions of a file or web resource, enabling partial content delivery. While harmless in most cases, this feature plays a key role in turning a weak point into an actual vulnerability.
The exploit becomes possible when these two factors align. The attacker crafts a request containing both a malicious input payload—such as JavaScript code—and a Range header. The Range header isolates just the malicious part of the response, effectively bypassing the protections that would normally neutralize the threat.
An example of such a request would involve injecting malicious code into the user input field and specifying a byte range in the header that precisely isolates this code in the server’s response. The crafted request tricks the server into highlighting only the malicious content.
When the server processes this request and responds with a “206 Partial Content” status, the isolated malicious payload is sent back. In a victim’s browser, this payload is no longer neutralized and can execute directly, often resulting in cross-site scripting (XSS) attacks.
This clever combination of a seemingly safe reflected input vulnerability and the use of HTTP Range headers creates a powerful attack vector. It highlights the need for developers to implement strict validation of user inputs and carefully evaluate the use of HTTP headers to ensure that no exploitable behavior is inadvertently introduced.
Mitigations
To protect against this type of exploit, developers and organizations should consider implementing the following mitigations:
Input Validation: Ensure that all user inputs are appropriately validated and sanitized to prevent the injection of malicious payloads.
CORS Policies: Implement strict CORS policies to control which origins are allowed to access resources, reducing the risk of unauthorized access.
Rate Limiting: Apply rate limiting to API endpoints to mitigate the risk of DoS attacks.
Monitoring and Logging: Continuously monitor and log requests to detect unusual patterns that may indicate an attempted exploit.
Practical Demonstration of Range Header Exploitation

Consider a scenario where an attacker injects a script payload like (console.log(‘XSS’)) into a vulnerable web endpoint. The crafted request triggers a server response that isolates the payload and returns it as partial content.
HTTP/1.1 206 Partial Content
Content-Range: bytes 80-99/105
Content-Length: 20
(console.log(‘XSS’))
This response isolates the injected code snippet, making it accessible and ready to execute in the victim’s browser.
Browsers interpret the partial content response as legitimate and execute the returned script. In this case, the payload (console.log(‘XSS’)) runs, revealing how the attack successfully bypasses traditional safeguards applied to reflected input vulnerabilities.
This method is complicated to defend against because both elements required for the attack—reflected inputs and the Range header support—are not inherently malicious. They are widely used and typically considered harmless, making them easy to overlook during security checks.
Reflected input vulnerabilities that seem harmless and endpoints supporting partial responses often receive little attention during penetration testing. In many cases, they’re not even flagged as low-severity issues, allowing attackers to exploit them relatively quickly.
This proof-of-concept underlines the importance of reexamining seemingly minor issues in web applications. Developers and security teams must adopt stricter input validation measures and thoroughly assess how features like partial content responses could be misused to prevent such attacks.
Implications for Web Security
The ability to exploit reflected input through the HTTP Range header poses significant risks for web applications. Some of the potential implications include:
- Data Leakage: Sensitive information may be exposed to unauthorized users, leading to data breaches.
- Cross-Site Scripting (XSS): Attackers could inject malicious scripts that execute in the context of the victim’s browser.
- Denial of Service (DoS): By manipulating requests, attackers could overwhelm the server, leading to service disruptions.
Creative Use of HTTP Range Header Exploits
The HTTP Range header highlights how attackers can ingeniously turn minor, seemingly insignificant vulnerabilities into powerful attack methods. By combining harmless features, they reveal new possibilities for impactful exploits.
This discovery reminds web developers and cybersecurity experts of the need to analyze system behaviors. Treating vulnerabilities as isolated problems often overlooks the potential for their combined misuse.
Developers are encouraged to explore resources like the MDN Web Docs to gain a deeper understanding of how the HTTP Range header functions and behaves. These references provide valuable insights into safeguarding web applications.
The breakthrough was achieved thanks to the researchers’ persistence and creativity. They acted on unconventional ideas and questioned standard assumptions about web vulnerabilities.
This finding underlines the importance of innovative thinking in cybersecurity. Researchers must continuously challenge norms to uncover new weaknesses and improve security systems.
Although no real-world incidents involving this technique have been reported, it is a critical reminder to strengthen defenses. The discovery emphasizes the necessity for more thorough and imaginative approaches to securing web applications.
For more:
Share this :