Mobile Malware and Malicious Apps: How to Stay Safe

Hoplon InfoSec
31 Mar, 2025
Mobile malware refers to malicious software designed to infiltrate smartphones and tablets—often aiming to steal data, spy on users, or disrupt functionality. In today’s hyper-connected world, these threats are more dangerous than ever. We rely on our phones for banking, shopping, email, and private conversations, making them prime targets for cybercriminals.
In this blog, we’ll break down what mobile malware is, how it spreads (with real-world examples), the common types of mobile threats, and—most importantly—how you can stay safe.
How Mobile Malware Spreads
Cybercriminals use various methods to infect mobile devices. Knowing how these attacks work helps you avoid falling victim.
Malicious Apps in Disguise
Many malware infections start with apps that appear legitimate—games, utilities, or even fake security tools. While most official app store apps are safe, bad actors occasionally sneak malicious apps past security reviews.
A notable example is Color Message, which had over 500,000 downloads on Google Play before researchers exposed it as housing the Joker malware. Once installed, it accessed contacts and secretly subscribed users to premium services.
Phishing Links and Smishing
Phishing is when attackers trick users into clicking harmful links. On mobile, phishing often comes via text messages (smishing) or emails, imitating companies like banks or delivery services.
In 2023, a campaign called FluHorse targeted Asian users by leading them to fake banking apps that stole login credentials and intercepted 2FA codes. Similar smishing tactics were used by FluBot, luring users with fake parcel tracking texts.
Malvertising and Drive-by Downloads
Infected websites and online ads can deliver malware automatically via drive-by downloads, exploiting browser vulnerabilities. A single tap on a malicious ad may install malware—especially if your phone’s software is outdated.
Pre-Installed Malware
Some budget phones come with malware preloaded at the factory—known as supply chain attacks. Devices infected with BadBox and PeachPit trojans were found being sold online, often from uncertified manufacturers.
Zero-Click Exploits
Advanced attackers may exploit mobile OS vulnerabilities, infecting devices without user interaction. Pegasus spyware is a prime example: it infiltrated phones via iMessage or WhatsApp, so no clicks were needed. These attacks highlight the importance of keeping your phone updated.
Common Types of Mobile Malware
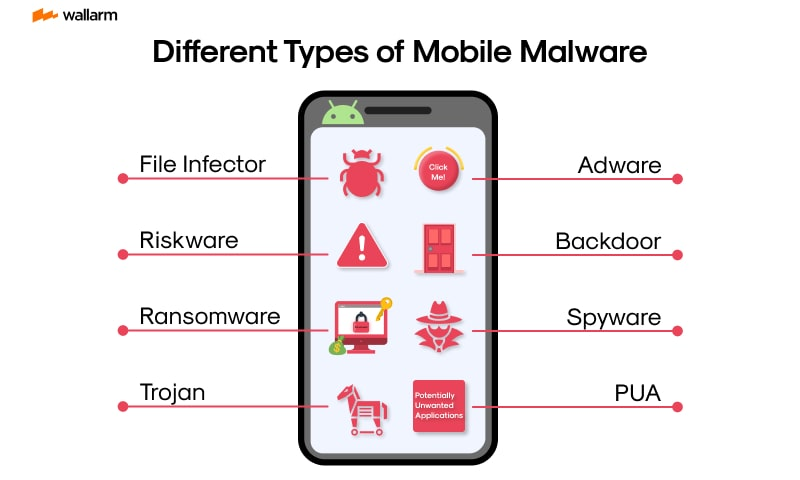
Spyware
Spyware secretly monitors your phone activity—tracking GPS, logging keystrokes, accessing messages, and even turning on your mic or camera. Notorious examples like Pegasus can steal passwords, read messages, and track movements.
Ransomware
Mobile ransomware locks you out of your device or encrypts files, demanding payment—usually in cryptocurrency. Victims may lose both money and data if they pay and don’t receive a decryption key.
Banking Trojans
These trojans mimic legitimate financial apps to steal credentials. Xenomorph and Anatsa (TeaBot) are two examples capable of full account takeover and unauthorized money transfers.
Adware
Adware floods your phone with intrusive ads, slows performance, and sometimes steals data. The “Judy” adware campaign infected millions of Android devices, using background processes for click fraud.
Phishing & Fake Apps
Some malicious apps are designed solely to phish. Fake banking, crypto wallets, or social media apps harvest login credentials. FluHorse, for instance, impersonated financial apps to steal user data and bypass 2FA.
Many malware apps are hybrids—spyware that also serves ads or banking trojans with ransomware features.
Why We Fall for Malicious Apps

Cybercriminals rely on user trust, curiosity, and carelessness. Here’s how they trick users into downloading malware:
Deceptive App Icons & Names
Some apps mimic popular ones—like fake “WhatsApp” clones—with nearly identical names and icons. They fool users into thinking they’re downloading the real thing.
Third-Party App Stores
Unofficial app stores and APK-sharing websites are malware breeding grounds. Studies show that 99.9% of mobile malware originates from outside official app stores.
Social Engineering Tactics
Messages like “Your phone is infected! Click to clean now” or “I found this photo of you” are designed to provoke clicks. These emotional triggers often lead to malware downloads.
Permission Abuse
Malicious apps often request excessive permissions. A flashlight app asking for access to contacts or SMS should raise red flags. Many users unquestioningly grant access, unknowingly enabling data theft.
Consequences of Mobile Malware
Installing malicious apps can lead to:
- Privacy Loss: Malware can access messages, photos, contacts, and location data—leading to identity theft or surveillance.
- Financial Damage: Banking trojans, premium SMS malware, and ad fraud can cost users real money. The Joker malware, for instance, quietly subscribed users to premium services.
- Performance Issues: Battery drain, overheating, app crashes, and slowdowns are common malware side effects. Some users blame aging hardware when malware is the true cause.
Mobile Security Tips: How to Stay Protected
The good news is that by following a few smart habits, you can drastically reduce your risk of infection.
- Stick to Official App Stores: Google Play and Apple App Store screen apps for malware. Google Play Protect blocked over 2.3 million suspicious apps in 2024. Always download apps from trusted sources.
- Keep Your Device Updated: Updates fix known vulnerabilities that malware exploits. Enable automatic OS and app updates. An outdated phone is a vulnerable phone.
- Think Before You Tap: Be cautious with email, text, or social media links—especially urgent or emotional ones. Instead of clicking, manually visit the website or open the app directly.
- Check App Permissions: Always review what permissions an app requests. Deny unnecessary access (especially to SMS, contacts, or microphone), and uninstall apps that demand too much.
- Use a Trusted Mobile Security App: Consider using apps from reputable vendors like Hoplon InfoSec to scan your phone regularly and detect threats early.
- Don’t Root or Jailbreak Your Device: Rooting or jailbreaking removes built-in OS protections, making it easier for malware to gain deep access to your phone.
- Use VPNs on Public Wi-Fi: Avoid sensitive activities (like online banking) on public Wi-Fi unless you’re using a trusted VPN. Attackers can intercept your data on unsecured networks.
- Backup Your Data Regularly: Backups won’t prevent malware but ensure you don’t lose important data if you need to reset your device after an infection.
How the Mobile Ecosystem Fights Malware
You’re not alone in this fight. Security vendors, platform developers, and app stores work together to reduce threats.
App Stores’ Role: Google and Apple use AI-powered app review systems, flagging suspicious apps during submission. In 2024 alone, Google blocked millions of bad apps and banned thousands of shady developers.
Operating System Updates: OS developers regularly push security patches. Google releases monthly Android updates, while Apple has rolled out features like automatic permission resets to limit dormant app access.
Security Researchers: Companies like Lookout, Zimperium, and Avast continuously uncover new threats, share findings with platform providers, and release protective tools for users.
User Education: Carriers, phone makers, and tech platforms increasingly promote mobile hygiene—offering security tips, alerts, and privacy settings guides to help users make better choices.
Is Your Phone Infected? Common Warning Signs
Watch for these symptoms of malware infection:
- Sudden lag, freezing, or crashes
- Fast battery drain or phone overheating
- Unexplained spikes in mobile data usage
- Random pop-ups or ads—even when not browsing
- Unknown apps appearing without your consent
- Messages sent from your number you didn’t send
- Unauthorized charges on your phone bill or accounts
- Security settings changed or antivirus disabled
Any one of these may be benign—but multiple signs likely mean something is wrong.
What to Do If You’re Infected
Uninstall Suspicious Apps: Identify and delete apps you don’t recognize or that behave strangely. On Android, use Safe Mode if needed. If an app has device admin rights, revoke them first.
Clear Downloads and Browser Cache: Delete suspicious files and clear your browser’s cache and history—especially if malware arrived via the web.
Scan with Mobile Security Tools: Use a reliable antivirus or anti-malware app to scan and clean your phone. Enable Play Protect or similar built-in tools.
Update OS and Change Passwords: Install all available system and app updates. Change passwords for any accounts accessed on the device—especially financial or email accounts.
Factory Reset (Last Resort): If malware persists, perform a factory reset. Backup your data carefully—but avoid restoring from backups that might reintroduce the malware.
Conclusion
Mobile malware is a serious and growing threat, but one you can defend against with awareness and good habits. Your phone holds a wealth of personal data—treat it like the digital vault it is.
Avoid sketchy apps, update regularly, install only from official sources, and scrutinize permissions. Be skeptical of messages or prompts urging you to act fast or install unknown apps. Use security software, especially on Android, and stay informed about evolving threats.
Ultimately, mobile security is a shared responsibility between you and the broader tech ecosystem—but your choices matter most. With caution and a little cybersecurity know-how, you can stay ahead of the attackers.
Stay safe, and browse smart.
Share this :