New Triada Malware Attacking Android Devices to Replaces Phone Numbers

Hoplon InfoSec
03 Apr, 2025
A sophisticated new variant of the Triada malware family has recently come to light, targeting Android devices with alarming precision. This updated strain not only intercepts outgoing calls but also manipulates them in a way that redirects users to fraudulent premium-rate numbers. The level of stealth and technical expertise behind this attack makes it a significant threat, underscoring the need for enhanced vigilance and improved security measures in the mobile ecosystem.
How the Triada Malware Operates
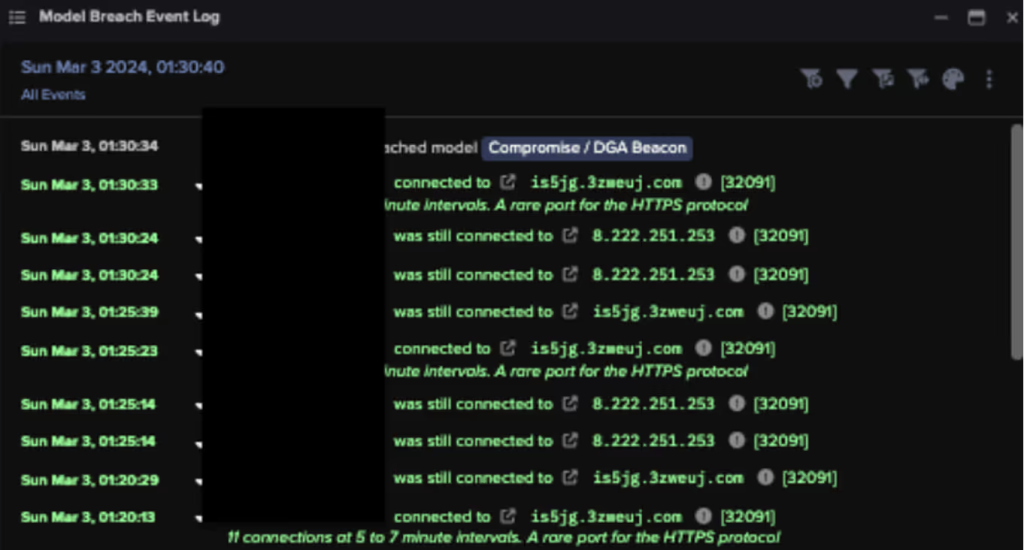
This advanced malware operates silently in the background, meaning that most users remain oblivious to the malicious activities taking place on their devices. The core functionality of this Triada variant is its ability to intercept and modify outgoing calls. When a user initiates a call, the malware steps in to replace the legitimate phone number with a fraudulent one. This redirection not only exposes users to unexpected charges through premium-rate calls but also increases the risk of eavesdropping on sensitive conversations.
Interception and Redirection Process
At the heart of this malware is a mechanism that hooks into the Android telephony subsystem. During the call initiation process, the malware intercepts the outgoing number and compares it against a remotely controlled database. This database contains a list of target numbers and their malicious replacements. Once a match is found, the malware silently replaces the original number with the fraudulent one, redirecting the call without the user’s knowledge. Such sophistication in design is a clear indicator of the technical prowess of the attackers.
Exploiting System Vulnerabilities
The malware exploits privilege escalation vulnerabilities to gain system-level access. By leveraging these vulnerabilities, the malware can monitor and manipulate the Android dialer framework effectively. This exploitation of the telephony service is particularly dangerous as it allows the malware to operate with minimal detection, even in devices that might otherwise have robust security measures in place.
Infection Mechanism and Code Analysis
The infection process typically begins when users download applications from unofficial app stores or compromised sources. These applications often request permissions that far exceed what is necessary for their intended function. Once granted, these permissions open the door for the malware to install itself on the device. The initial foothold is established through this stealthy method, and the malware quickly escalates its privileges to gain deeper access into the operating system.
Detailed Code Examination
An important aspect of understanding this threat lies in examining the code used by the malware. The following code snippet illustrates how the malware intercepts outgoing calls:
@Override
public Boolean onOutgoingCall(String number, Intent intent) {
String modified number = checkAndReplaceNumber(number);
intent.putExtra("android.intent.extra.PHONE_NUMBER", modified number);
return true;
}In this example, when a user initiates a call, the malware intercepts the original phone number. The checkAndReplaceNumber function then verifies the number against a remotely controlled database and substitutes it with a fraudulent alternative if a match is found. Finally, the modified number is reinserted into the intent, ensuring that the call is directed to the attacker’s designated premium-rate number.
Geographic Spread and Financial Impact

Initial investigations have revealed that thousands of devices across Eastern Europe have already been compromised. There is an increasing trend of infections spreading to Western Europe and North America. This expansion not only highlights the malware’s adaptability but also its potential to affect a global user base.
Financial Consequences
The financial ramifications of this malware are severe. Fraudulent premium-rate calls have already resulted in losses exceeding an estimated $2 million. Beyond the direct financial impact, there is a significant risk that sensitive business communications may be intercepted, leading to further indirect losses. Businesses and individual users alike are at risk, making it crucial for everyone to remain alert to such threats.
Technical Sophistication Behind the Attack
The attackers behind this malware have shown a high degree of technical sophistication. By integrating a novel technique to hook into the Android dialer framework, they have effectively bypassed many traditional security measures. This represents a significant evolution in mobile threat capabilities and illustrates how attackers are continuously adapting their methods to exploit new vulnerabilities.
Evolution from Previous Variants
Previous variants of Triada focused primarily on creating persistent infections by modifying system files or bypassing security measures without directly affecting user interactions. In contrast, this new variant directly targets the telephony subsystem, thereby manipulating a core function of the device. Such an evolution indicates that the attackers are not only capable of maintaining stealth but also innovating new methods to cause disruption and financial damage.
Implications for Mobile Security
The emergence of this sophisticated malware variant serves as a stark reminder of the vulnerabilities present in the mobile ecosystem. It highlights the ongoing arms race between attackers and security professionals. For security vendors and mobile operating system developers, this means continuously refining their defense mechanisms and patching vulnerabilities as soon as they are discovered. For end users, it underlines the importance of vigilance when installing applications and monitoring device activity for any unusual behavior.
Infection Vectors and Prevention Techniques
One of the primary ways this malware spreads is through unofficial app stores and compromised applications. These platforms often lack the rigorous security checks that are standard in official app repositories, making them fertile ground for malicious software.
Importance of Sourcing from Authorized Distributors
To mitigate the risk of infection, users should only download applications from trusted sources such as the Google Play Store. Authorized distributors adhere to strict security protocols, including regular malware scans and stringent app review processes, which help to prevent the distribution of harmful software. Additionally, users should exercise caution when granting permissions to applications. If an app requests permissions that seem excessive or unrelated to its functionality, it is advisable to reconsider its installation.
Deploying Robust Security Solutions
Another critical prevention measure is the deployment of robust security solutions. Security applications like Kaspersky for Android are designed to detect and neutralize such threats before they can inflict damage. These tools continuously monitor the device for unusual activity, providing real-time protection against malware infections. Furthermore, keeping the operating system and all applications up to date is essential, as updates often include security patches that address known vulnerabilities.
Recommendations for Businesses and End Users
Given the increasing threat posed by this new Triada variant, both businesses and individual users must take proactive steps to protect their devices. The following recommendations can help mitigate the risk of infection and reduce the potential financial impact.
Best Practices for Device Security
It is critical to adopt a layered security approach that includes:
- Using Authorized App Stores: Only install applications from recognized and verified sources.
- Regular Software Updates: Ensure that both the operating system and installed applications are always updated to the latest versions.
- Restrictive Permissions: Only grant necessary permissions to applications. If an app requests excessive permissions, consider alternative options or avoid installation altogether.
- Mobile Security Solutions: Install reputable mobile security software that can detect and remove malware.
- User Education: Stay informed about the latest mobile security threats and practice caution when downloading and installing new apps.
Corporate Security Measures
For businesses, the stakes are even higher. Intercepted calls and compromised communications can lead to significant operational and financial losses. Companies should implement the following measures:
- Employee Training: Educate employees about mobile security risks and best practices for device usage.
- Mobile Device Management (MDM): Deploy MDM solutions that enforce security policies on all corporate devices.
- Regular Audits: Conduct regular security audits to identify and address potential vulnerabilities within the mobile ecosystem.
- Incident Response Plan: Develop and maintain an incident response plan specifically tailored to mobile security threats. This plan should include steps for isolating affected devices, assessing the extent of the breach, and restoring normal operations.
- Collaboration with Security Vendors: Work closely with mobile security vendors to ensure that the latest threat intelligence and mitigation strategies are in place.
Deep Dive into the Technical Aspects
Understanding the technical mechanics behind this malware can provide valuable insights into how attackers exploit vulnerabilities and what steps can be taken to counteract such threats.
The Role of Privilege Escalation
One of the key strategies used by this Triada variant is privilege escalation. By exploiting known vulnerabilities in the Android operating system, the malware elevates its permissions to a system-level status. This level of access is crucial for intercepting calls and modifying the dialer framework. Once system-level access is achieved, the malware can operate with minimal interference from the device’s built-in security features.
How the Android Dialer is Exploited
The Android dialer framework is a critical component of the operating system that is responsible for handling outgoing calls. By integrating into this framework, the malware is able to intercept and alter call data in real-time. The provided code snippet illustrates how the malware achieves this:
@Override
public Boolean onOutgoingCall(String number, Intent intent) {
String modified number = checkAndReplaceNumber(number);
intent.putExtra("android.intent.extra.PHONE_NUMBER", modified number);
return true;
}In this function, the call is intercepted, and the original number is replaced with a fraudulent one. The malware then allows the call to proceed, leaving the user unaware of the manipulation. This level of integration into the Android system showcases the attackers’ deep understanding of mobile operating system internals.
The Broader Implications of Mobile Malware
The rise of sophisticated mobile malware variants like this Triada strain has broad implications for both individual users and the global cybersecurity landscape. As attackers continue to refine their techniques, the need for robust, proactive security measures becomes increasingly urgent.
Impact on Personal Privacy
When malware intercepts calls, the consequences extend beyond financial fraud. Intercepted communications can include sensitive personal or business information, potentially leading to identity theft, corporate espionage, or other forms of privacy violations. This breach of personal privacy is particularly concerning given the amount of sensitive data that modern smartphones typically store.
The Evolving Threat Landscape
The evolution of malware tactics, such as the exploitation of the Android telephony subsystem, underscores a broader trend in cybersecurity: attackers are continuously adapting to overcome new security measures. This evolving threat landscape requires that both developers and security professionals remain vigilant and proactive in their defense strategies. The ability to detect and respond to these threats swiftly is paramount to minimizing damage.
Industry Response and Future Outlook
In response to the discovery of this new Triada variant, cybersecurity researchers and industry experts have been actively analyzing the threat and developing strategies to counter it. Initial investigations by firms such as Kaspersky have provided critical insights into the malware’s behavior, allowing for the development of targeted detection and mitigation tools.
Collaboration Among Cybersecurity Firms
One encouraging development in the fight against mobile malware is the increased collaboration among cybersecurity firms. By sharing threat intelligence and analysis, these organizations can develop more effective defenses against emerging threats. Such collaboration not only speeds up the identification of vulnerabilities but also enhances the overall security posture of the mobile ecosystem.
The Role of Regulatory Bodies
Regulatory bodies also play a crucial role in ensuring mobile security. By enforcing strict guidelines and security standards for mobile applications, governments, and regulatory organizations can help reduce the risk of malware infections. In many regions, ongoing efforts are being made to update and enforce these standards, ensuring that both app developers and distributors maintain high-security standards.
Practical Advice for Protecting Your Mobile Device

Given the sophisticated nature of the Triada variant, users need to take practical steps to protect their mobile devices. The following advice can help reduce the risk of infection and ensure that your personal information remains secure.
Steps to Secure Your Android Device
- Download Apps Only from Trusted Sources: Avoid unofficial app stores and websites that lack proper security protocols. Stick to the Google Play Store or other verified platforms.
- Review App Permissions Carefully: Before installing any app, review the permissions it requests. If an app asks for more permissions than necessary, consider it a red flag.
- Regularly Update Your Device: Keep your Android operating system and all installed applications up to date. Software updates often include patches for security vulnerabilities.
- Install Mobile Security Software: Utilize reputable mobile security solutions that offer real-time monitoring and protection against malware.
- Monitor Your Device Activity: Be aware of any unusual behavior on your device, such as unexpected call charges or changes in settings, and report any anomalies immediately.
Enhancing Corporate Mobile Security
For businesses that rely on mobile communications, taking additional steps to secure devices is critical. In addition to the practices mentioned above, companies should consider implementing Mobile Device Management (MDM) solutions to enforce security policies and monitor device activity across the organization.
Conclusion
The emergence of this sophisticated Triada variant serves as a stark reminder of the evolving nature of mobile threats. With its ability to intercept and modify outgoing calls, this malware not only poses a significant financial risk but also jeopardizes the privacy of millions of users worldwide. The complexity of the infection mechanism, which involves exploiting privilege escalation vulnerabilities and integrating deeply into the Android telephony framework, highlights the need for both individual and organizational vigilance.
By adopting best practices—such as downloading apps only from trusted sources, regularly updating software, and using robust mobile security solutions—users and businesses can significantly reduce their exposure to such threats. Moreover, increased collaboration among cybersecurity professionals and the enforcement of stringent regulatory standards will be key in the ongoing battle against mobile malware.
As the threat landscape continues to evolve, staying informed and proactive is the best defense. With the rapid pace of technological change, continuous education on mobile security is crucial. Both end users and organizations must remain alert to the latest developments and be prepared to take swift action in response to new threats. The fight against malware like this Triada variant is not just about protecting devices—it’s about safeguarding personal privacy, ensuring financial security, and maintaining the integrity of our digital communications.
Source: Cybersecurity News
Share this :