New Tunneling Protocol Flaws Risk 4M+ Hosts & VPN Security
Hoplon InfoSec
16 Jan, 2025
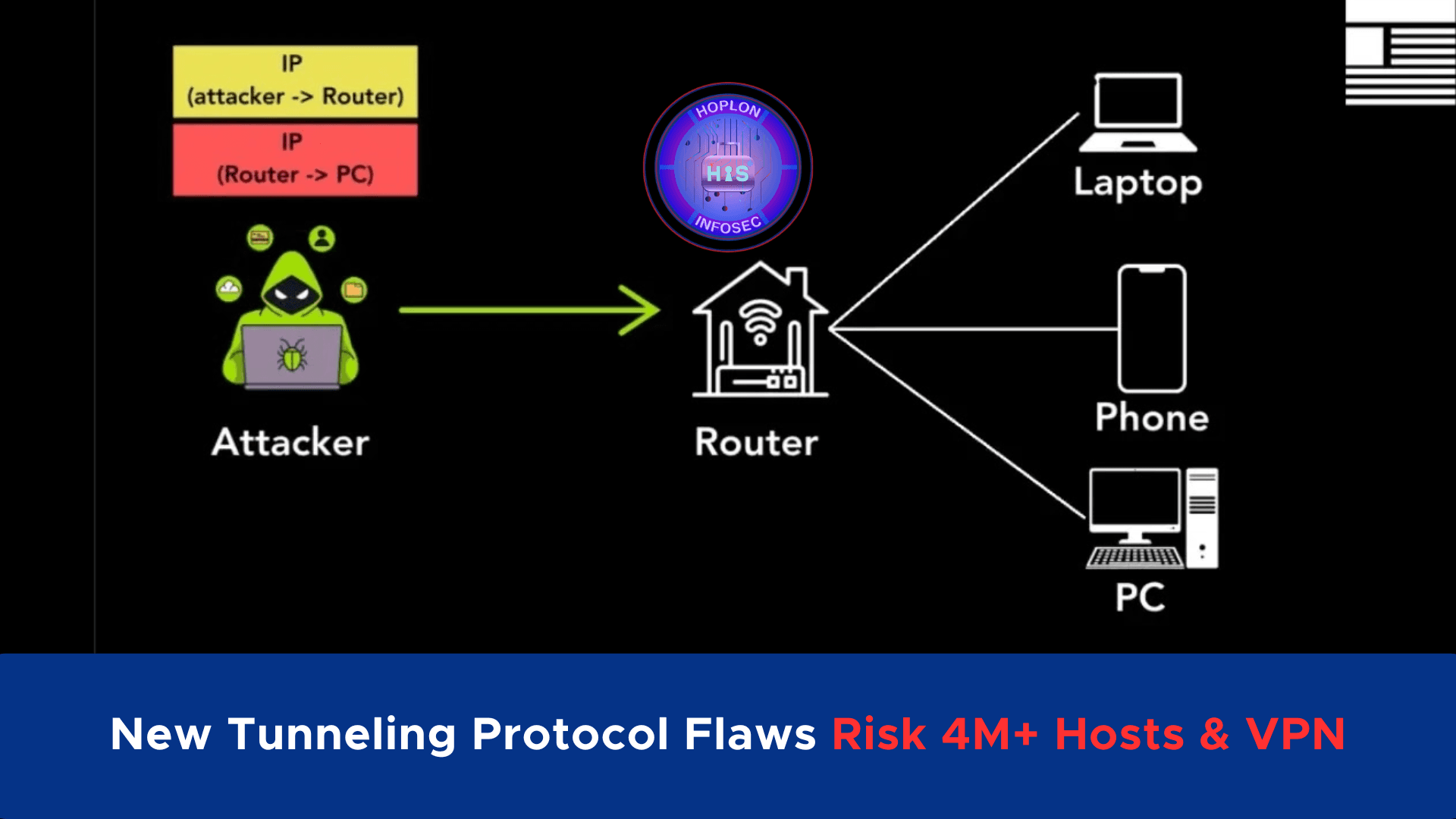
Are you aware of new Tunneling Protocol Flaws? In a groundbreaking report by Top10VPN, researchers have uncovered critical vulnerabilities in widely used internet tunneling protocols. These flaws expose over 4.2 million hosts, including VPN servers and private home routers, to potential exploitation. This discovery reveals how attackers can hijack devices to perform anonymous attacks, denial-of-service (DoS) campaigns, and unauthorized access to private networks.
Understanding Tunneling Protocols and Their Risks
Tunneling protocols enable secure communication over the Internet by encapsulating one network protocol within another. These protocols facilitate virtual private network (VPN) connections, routing, and interoperability between IPv4 and IPv6 networks. However, the lack of robust authentication mechanisms in specific protocols creates opportunities for cybercriminals to exploit these systems.
Key Vulnerabilities in Tunneling Protocol Flaws
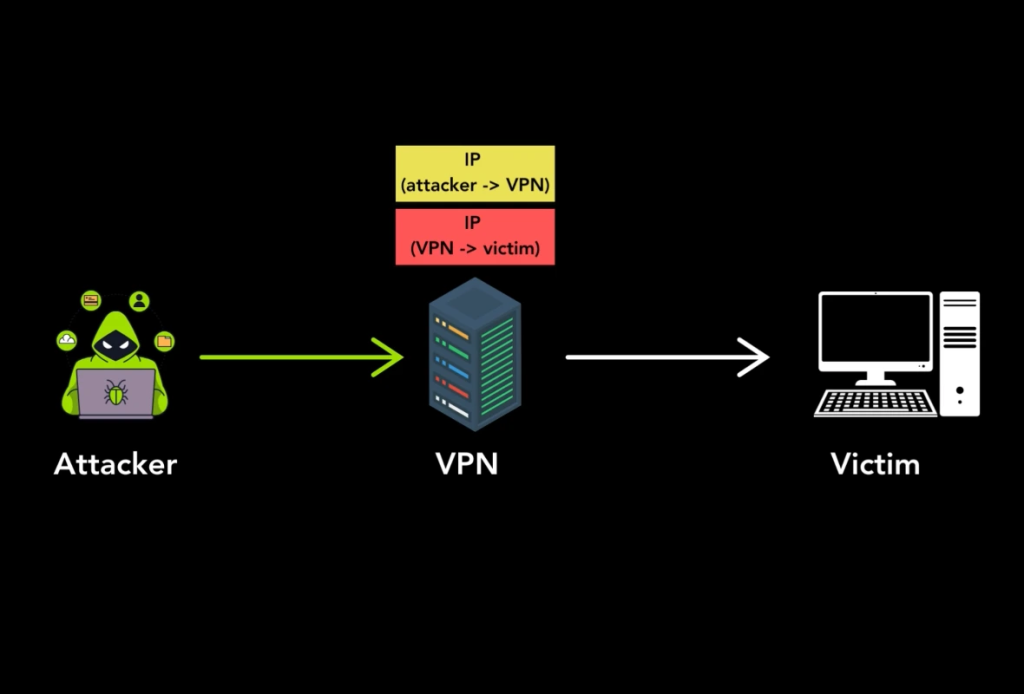
The researchers identified several attack methods exploiting tunneling protocol weaknesses. These techniques highlight the dire consequences of failing to authenticate incoming packets properly.
- Ping-Pong Amplification Attack
- This attack loops packets between vulnerable hosts, amplifying traffic volumes and causing disruptions. It can generate excessive outgoing traffic, leading to an economic denial of sustainability (EDoS) and increasing costs for cloud services.
- Tunneled-Temporal Lensing (TuTL)
- This sophisticated method routes traffic through compromised host chains, creating massive inbound traffic spikes at the victim’s endpoint. The surge overwhelms the system, forcing it to drop legitimate traffic.
- Routing Loop DoS
- Attackers create endless loops within tunneling interfaces by sending packets with invalid destinations. This overloads the target system with traffic, causing it to crash.
- Abusing Abuse Reports
- Cybercriminals can spoof traffic to trigger abuse reports against victims. As a result, hosting providers may deactivate accounts, effectively achieving an administrative DoS.
Scope of the Vulnerability
The research revealed that over 4.26 million hosts are at risk, spanning various devices and systems, including:
- VPN servers
- ISP home routers
- Content Delivery Network (CDN) nodes
- Mobile network gateways
- Core internet routers
The affected tunneling protocols include:
- IPIP/IP6IP6
- GRE/GRE6
- 4in6
- 6in4
A detailed breakdown of vulnerable hosts is as follows:
| Tunneling Protocol | Vulnerable Hosts | Spoofing Capable |
|---|---|---|
| IPIP | 530,100 | 66,288 |
| IP6IP6 | 217,641 | 333 |
| GRE | 1,548,251 | 219,213 |
| GRE6 | 1,806 | 360 |
| 4in6 | 130,217 | 4,113 |
| 6in4 | 2,126,018 | 1,650,846 |
The vulnerabilities are widespread, affecting countries like China, France, the United States, Japan, and Brazil.
New Attack Techniques in Focus
Two newly identified attack techniques—Tunneled-Temporal Lensing (TuTL) and Economic Denial of Sustainability (EDoS)—stand out for their devastating impacts:
- TuTL: This method overwhelms victims’ resources by concentrating attack traffic into narrow timeframes.
- EDoS: This attack amplifies data traffic to inflate operational costs for cloud-hosted services.
Both methods target various devices, including consumer VPN servers, enterprise systems, and home routers.
Geographic and Network Analysis
The researchers conducted a global scan and found vulnerabilities in 218 countries. China and France host the majority of spoofing-capable devices. The analysis also revealed that two autonomous systems account for nearly half of the identified weaknesses, indicating systemic risks.
Tunneling Protocols Under Scrutiny
The research focused on several critical tunneling protocols:
- IPIP and IP6IP6 Protocols
- These protocols, affecting 747,741 hosts, are commonly used in Linux-based networking and VPN setups. However, their lack of encryption and authentication mechanisms exposes endpoints to significant risks.
- GRE and GRE6 Protocols
- With over 1.55 million vulnerable hosts, these protocols are widely used in enterprise and mobile networks. Their minimal security features make them prime targets for exploitation.
- 6in4 and 4in6 Protocols
- These methods facilitate IPv6 over IPv4 communication and vice versa. They accounted for nearly half of all vulnerabilities, affecting 2.25 million hosts.
Affected Devices
The vulnerabilities impact various devices and systems, including:
- VPN Servers: Over 1,365 servers were identified as vulnerable, though the number could exceed 46,000. Providers like AoxVPN and defunct services like AmanVPN are among those affected.
- Dynamic DNS Routers: Approximately 1,200 Synology routers and devices linked to the French ISP Free were found to be exposed.
- Business VPNs: Around 171 company VPNs across 33 countries were at risk, primarily using GRE protocols.
- ISP Home Routers: French ISP Free had 726,000 vulnerable routers, although these flaws have been addressed.
Most Affected ISPs
The top ISPs affected include:
- Free (France): 726,194 hosts
- Softbank (Japan): 238,841 hosts
- Eircom Ltd (Ireland): 7,557 hosts
Mitigation Strategies
Addressing these vulnerabilities requires coordinated efforts at both host and network levels.
- Host-Level Defenses
- Restrict tunneling traffic to trusted sources.
- Implement secure protocols like IPsec or WireGuard to ensure proper authentication and encryption.
- Network-Level Defenses
- Internet Service Providers (ISPs) should filter malicious traffic, inspect deep packet structures, and block unencrypted tunneling packets.
Collaborative Efforts for Security
The study builds on previous work by researcher Livneh Yannay, who identified similar flaws in IPv4 tunneling protocols in 2020. Expanding on these findings, the latest research highlights vulnerabilities in IPv6 and additional tunneling protocols. Researchers working with CERT/CC have alerted affected parties, urging them to secure their systems.
Conclusion
The vulnerabilities in tunneling protocols underscore the critical need for stronger security measures in network infrastructure. By addressing these weaknesses through advanced authentication mechanisms, secure protocols, and coordinated industry efforts, organizations can protect millions of devices and maintain the integrity of global internet systems.
For more:
https://cybersecuritynews.com/new-tunneling-protocol-vulnerabilities/
Share this :