North Korean Hackers Use OtterCookie Malware in New Attackaaa

Hoplon InfoSec
27 Dec, 2024
The cybersecurity landscape continues to be dominated by sophisticated threat actors, and North Korea’s infamous cyber units remain at the forefront of these operations. Among the most concerning campaigns is the ongoing Contagious Interview campaign, a persistent and deceptive attack strategy that preys on job seekers through social engineering tactics. Recent developments have revealed the deployment of a new JavaScript malware named OtterCookie Malware, marking a significant evolution in this campaign. Let’s delve into the details of this threat, its implications, and the broader cyber activities orchestrated by North Korean actors.
The Nature of the Contagious Interview Campaign
The Contagious Interview campaign, also known as DeceptiveDevelopment, exploits the aspirations of job seekers by masquerading as legitimate recruiters. Threat actors employ convincing social engineering tactics to trick individuals into downloading malware under the guise of participating in job interviews. The campaign leverages multiple vectors, including:
- Malware-laced videoconferencing applications: These apps are crafted to look like legitimate platforms but serve as carriers for malicious software.
- Compromised npm packages: Hosted on platforms like GitHub or the official npm registry, these packages act as a conduit for malware delivery.
Once the initial payload is delivered, the attackers pave the way for deploying other malware strains, such as BeaverTail and InvisibleFerret, designed to execute advanced malicious operations.
Key Discoveries and Attribution
In November 2023, Palo Alto Networks Unit 42 unveiled the operations of the Contagious Interview campaign, tracking it under the designation CL-STA-0240. Other aliases include Famous Chollima and Tenacious Pungsan. The campaign’s sophisticated tactics have drawn parallels with other North Korean cyber campaigns but are assessed to be distinct from similar operations like Operation Dream Job.
Evolution of the Attack Chain
In September 2024, Group-IB, a prominent Singaporean cybersecurity firm, highlighted significant revisions to the Contagious Interview attack chain. Notably, they identified an updated version of BeaverTail, which has transitioned to a modular structure. This approach outsources its information-stealing functionality to a series of Python scripts called CivetQ.
Introduction of OtterCookie Malware: A New JavaScript Malware
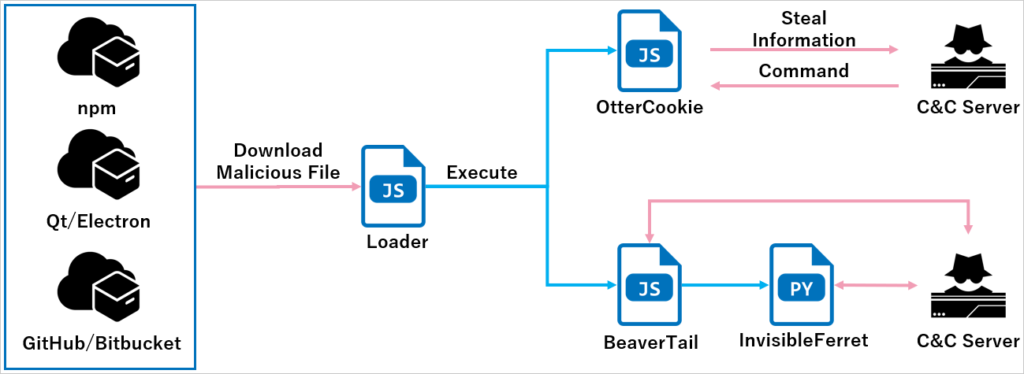
Recent investigations by NTT Security Holdings, a Japanese cybersecurity company, uncovered the emergence of OtterCookie, a new malware strain introduced as part of the Contagious Interview campaign in September 2024. This malware is a critical addition to the attackers’ toolkit and showcases their ongoing efforts to refine their techniques.
Technical Details of OtterCookie Malware
OtterCookie connects with a command-and-control (C2) server using the Socket.IO JavaScript library. Once communication is established, it awaits instructions to perform malicious activities, which include:
- Executing shell commands to facilitate data theft.
- Stealing files, clipboard content, and cryptocurrency wallet keys.
Interestingly, the older variant of OtterCookie detected in September 2024 embedded the functionality for cryptocurrency wallet key theft directly into the malware. In contrast, newer versions have shifted this feature to be executed via remote shell commands, demonstrating a strategic shift in its implementation.
Implications of OtterCookie’s Development
The continuous evolution of OtterCookie underscores the adaptability of North Korean threat actors. Despite updating their tools, the infection chain remains unaltered mainly, indicating its effectiveness. This stability in their approach suggests that the attackers have achieved a high success rate with minimal need for drastic changes.
Broader Cyber Activities and Sanctions

The Contagious Interview campaign is part of a broader ecosystem of North Korean cyber activities that extend beyond traditional espionage and data theft. In November 2024, South Korea’s Ministry of Foreign Affairs (MoFA) imposed sanctions on 15 individuals and one organization linked to a fraudulent IT worker scheme. This operation was designed to generate revenue for the North Korean regime, with additional aims of stealing sensitive data and, in some cases, demanding ransoms.
Key Entities and Individuals Sanctioned
Among those sanctioned is Kim Ryu Song, who the U.S. Department of Justice indicted for his role in a conspiracy involving sanctions violations, wire fraud, money laundering, and identity theft. Kim’s activities included illegally securing employment in U.S. companies and non-profit organizations.
Another notable entity is the Chosun Geumjeong Economic Information Technology Exchange Company, accused of dispatching North Korean IT personnel to countries like China, Russia, Southeast Asia, and Africa. These IT workers, often part of the 313th General Bureau, are tasked with:
- Generating foreign currency for North Korea’s nuclear and missile programs.
- Developing software for military applications.
Broader Implications of Cyber Activities
North Korea’s cyber operations are not limited to financial crimes. According to South Korea’s MoFA, these activities pose significant threats to global security by funding nuclear and missile development. The ministry emphasized the dual danger of these operations—their criminal nature undermines cybersecurity ecosystems while bolstering North Korea’s military ambitions.
Conclusion: Strengthening Cyber Resilience

The Contagious Interview campaign and its associated developments, such as the introduction of OtterCookie, are a stark reminder of the persistent threats posed by state-sponsored cyber actors. As these campaigns evolve, it becomes increasingly critical for organizations and individuals to adopt proactive cybersecurity measures. Here are some key steps to enhance resilience:
- Awareness and Training: Educate employees and individuals about social engineering tactics and the risks of unsolicited recruitment offers.
- Robust Security Protocols: Implement multi-layered security measures, including endpoint detection and response (EDR) solutions.
- Regular Updates and Monitoring: Keep systems and software updated and continuously monitor for unusual activities.
- International Collaboration: Strengthen global cooperation to track and mitigate the activities of state-sponsored threat actors.
For More:
https://thehackernews.com/2024/12/north-korean-hackers-deploy-ottercookie.html
Share this :