Infiltrated from Afar: The North Korean Remote‑Worker Cyber Espionage Operation

Hoplon InfoSec
02 Jul, 2025
In late June 2025, the United States Department of Justice (DOJ) revealed an extraordinary cyber intrusion orchestrated by North Korean nationals posing as legitimate remote IT workers. These individuals secured employment with over 100 companies across the U.S., including at least one defense contractor, gaining access to sensitive internal systems and extracting valuable data. This revelation marks an important change in cyber warfare, shifting from traditional hacks to subversive infiltration through remote hiring.
This incident exposes critical vulnerabilities in how businesses verify identity, vet remote workers, and monitor internal systems. It also underscores the growing sophistication of adversarial states in penetrating high-value targets by blending in with the very workforce they’re infiltrating. The implications are both immediate and far-reaching, raising urgent questions about the future of corporate trust, national security, and global cybersecurity norms.
The Anatomy of Infiltration

How the Operation (North Korean Remote Worker Cyber Espionage) Unfolded
The scheme began as a seemingly innocuous recruitment drive. North Korean operatives crafted detailed personas, using stolen or fabricated identities to register on freelance platforms such as Upwork, Freelancer. com, and remote job portals. They tailored their fictional resumes to align with sought-after skills like software engineering, administration, and cloud architecture, making them ideal remote hires.
Once onboarded, these operatives were granted varying levels of access: some had read-only permissions; others received privileges that enabled them to change configuration files, access source repositories, or traverse internal networks undetected. One particularly alarming instance involved a North Korean operative being hired by a U.S. defense contractor, a move that technically granted them access to classified or sensitive defense applications.
What sets this infiltration apart is how stealthy and long-lasting it was. Rather than relying on malware or phishing campaigns, the attackers leveraged legitimate credentials and standard access tools. They worked from home, over virtual private networks (VPNs), and sometimes even using company-owned laptops shipped to U.S. addresses provided by local accomplices. Their activity blended in with legitimate remote work traffic, avoiding detection.
Techniques of Deception and Sophistication
Constructing Convincing Identities
Facilitating this infiltration was a meticulous approach to identity fabrication. The forgeries, which included various types of identity fraud, utilized stolen Social Security numbers, driver’s licenses, and other U.S.-based documents. These details, shredded from dark web data dumps, were arranged into polished LinkedIn profiles and professional biographies. To all outward accounts, these remote candidates appeared as legitimate American workers.
They used deepfake voice modulation and video overlays during remote interviews to convincingly impersonate Americans. In some cases, human accomplices in the U.S. performed voice verification checks to authenticate the applicants. This level of preparation made it very difficult for hiring managers and HR personnel to question their legitimacy.
Remote Work Infrastructure and Security Evasion
After gaining employment, the operatives avoided suspicion by strictly maintaining a remote presence via VPNs and virtual desktop infrastructures (VDIs). They would work during normal business hours, interact in team meetings, and deliver tasks on schedule, all aimed at blending in seamlessly.
Furthermore, they employed obfuscation techniques such as IP spoofing and time zone manipulation so that endpoint monitoring systems didn’t catch them accessing company networks from unusual locations. They avoided downloading suspicious files or accessing network resources in suspicious patterns, further reducing the chance of triggering security alerts.
Data Access: What Was Compromised?
Intrusion into Intellectual Property
The operators gained access to proprietary source code repositories, detailed software arcand,ecturand, and,,,,, in some cases, internal policy documents related to system integrations. This kind of sensitive material is especially valuable: a single module or design file could be repurposed to replicate systems, undermine future product launches, or even be weaponized in cybersecurity attacks.
In the defense contractor setting, while exact details remain classified, the informal disclosures suggest access to systems that could pertain to aerospace systems or satellite navigation. When individuals with foreign ties gain legitimate login credentials, defeating additional layers of security, such as multifacauthentication,n,,n,on,, becomes significantly easier.
Financial Data and Credentials
Some infiltrated environments contained cloud API keys, employee payroll information, and financial transaction logs. A compromised API key, for example, could allow attackers to spin up entire infrastructure, extract data, or connect laterally to other systems. These credentials are akin to digital skeletonand,and,,nd,d, in the hands of state-sponsored actors, can devastate both business and national security interests.
The Payout: Funding the Regime
Investigators traced over $3 million in illicit earnings from this operation. North Korean-linked entities owned or controlled cryptocurrency wallets that received payments made in U.S. dollars. This digital laundering bridge facilitated the funding of the North Korean government’s strategic programs, particularly its missile development, and highlights how rapidly stolen funds can convert into geopolitical leverage.
Government Response and Enforcement Actions

DOJ Indictments and FBI Raids
The DOJ unsealed criminal indictments naming several North Korean nationals and U.S.-based collaborators. Felonies included identity theft, wire fraud, money laundering, and violations of the International Traffic in Arms Regulations (ITAR). The DOJ accuses the suspects of orchestrating a cyber-espionage campaign that went beyond mere criminal gain, extending into the realm of national interest.
Concurrently, the FBI, DHS, and Treasury Department executed coordinated raids across at least 16 states. These operations led to the seizure of hundreds of devices, laptops, routers, smartphones, and an array of forged documentation. These raids sent a strong signal: cyber intrusions don’t have to be explosive to be impactful, and undercover operatives can be physically located and disrupted.
Sanctions, Advisories, and Strategic Warnings
The Treasury Department sanctioned multiple cryptocurrency wallets and shell companies used to funnel payments for this scheme. Authorities also targeted entities in China and Russia that facilitated the laundering infrastructure. Simultaneously, the FBI issued an urgent cybersecurity advisory urging companies,nies,,s, especially those in tech, defense, and criticainfrastructure,re,,, to scrutinize remote hiring processes, invest in endpoint monitoring, and enforce strict identity-proofing measures.
Strategic Consequences and Systemic Vulnerabilities

National Security at Risk
This breach is not just a corporatefailure, it is a national security issue. Defense contractors maintain secrets ranging from program budgets to satellite system architectures. If North Korean actors accessed such systems, the international stability equation shifts, militarily sensitive technologies may end up compromised or stolen, while adversaries could gain insights years ahead of expected timelines.
The threat is not theoretical: covert access, maintained over months or years, allows for exfiltration of high-value information, such as prime software development methodologies, upcoming product plans, or data on defense readiness. In a world where time-to-market matters and defense algorithms determine strategic dominance, stolen IP is often more valuable than stolen cash.
Erosion of Tech Industry Trust
Beyond defense, the tech industry suffers an erosion of trust. Remote hiring platforms are now under renewed scrutiny. Financial services, healthcare, and software development clients are questioning the thoroughness of their partners’ vetting. Investors may balk at funding startups reliant on global talent if there’s a chance of state-level infiltration.
Companies that outsource critical development overseas now face pressure to reassess the risk-reward calculus. The lesson is that any unverified or under-verified contributor can be a hidden liability, regardless of skills or credentials.
Comparing Attack Methods: Technical vs. Human-Based Intrusion
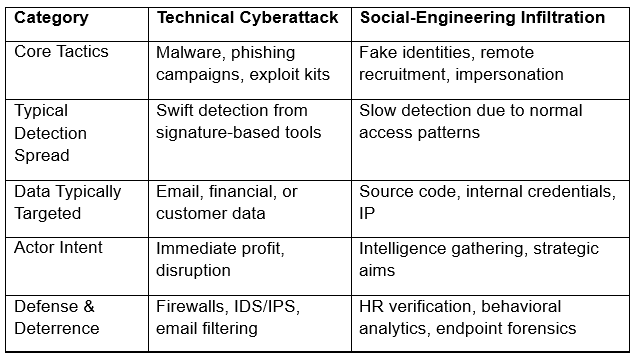
This table illustrates that while technical defenses remain critical, human-centric tactics highlight an entirely different battlefield. Successful defense now requires tightening organizational processes and cultivating cross-functional awareness.
Lessons for the Evolving Cyber Landscape

Strengthening Remote Hiring Protocols
Hiring practices must evolve in parallel with cyber threats. Background verification, including SSN checks, ID cross-referencing, and geolocation tracking, needs to be as rigorous for remote hires as for full-time employees. Companies should consider using live video ID checks and voice-matching solutions, plus regular re-verification or audits for remote workers, especially those with access to sensitive data.
Enhancing Technical Security Measures
Endpoint detection and response (EDR) platforms must be calibrated to flag deviations from typical user patternsss, like access from unexpected IP addresses or login times. Strict role-based access controls (RBAC) should limit privileges to the bare minimum. Zero-trust network architectures, requiring authentication for every access attempt, are becoming essential in this new threat landscape.
Frequent audits of cloud credentials and API usage can detect the silent creation of unauthorized resources or the misuse of keys. Internal monitoring dashboards should be able to drill down to per-user activity logs and spot anomalies at scale.
Bridging Trust Gaps Across Teams
This breach indicates that there must be coordinated efforts between HR, cybersecurity, legal, and operations departments. HR teams need to know which security red flags to watch for. IT and security teams need to receive hiring pipeline data to integrate with identity systems. Legal teams should be prepared for notifications of compliance breaches. Cross-training and shared responsibility across these groups will help companies preemptivelyshut down insider impersonation attacks.
North Korea has shifted its cyber tactics strategically.
From Extrusion to Infiltration
Historically, North Korea leveraged malware campaigns, such as WannaCry, and high-value thefts, like the Bangladesh Bank heist. This operation represents a transition to infiltration methods and long-term presence. Rather than causing immediate disruption, the adversary chose to quietly live within corporate frameworks.
The attack signifies a strategic evolution: embedded insiders, working under the guise of legitimate contractors, can gather intelligence over months, prepare future attacks, and manipulate systems from within, without ever triggering external defenses.
Implications for International Cyber Posture
The attack’s multinational infrastructure, involving proxy wallets, decentralized VPNs, and shell entities, raises coordination challenges. As investigations progress, it’s likely the U.S. will push for global cooperation on remote worker verification frameworks, cyber hiring vetting technology, and sanctioning banks or IT services that facilitate such schemes.
This breach could shape future cyber norms and policy discussions and may accelerate the adoption of remote-work regulations requiring transparency or certification of cross-border labor.
Rewriting the Rules: Cybersecurity for a Remote Era
The rise of remote hiring posed a fundamental challenge: how do you ensure the trustworthiness of someone you’ve never met in person? The North Korean infiltration shows that hiring someone remotely might also be a door into your network.
Security protocols must now begin at the recruitment table, not at the firewall. Organizations need identity verifiers, setup watchers, continuous monitoring, and cross-departmental accountability to stop threats before they coalesce into breaches. The stakes are no longer profit or reputation; they’re national security and global stability.
Final Thoughts
This unprecedented case of North Korean operatives gaining authorized access to U.S. systems through fabricated identities serves as a somber lesson. No system is secure if the person using it hides behind a convincing facade. In an era defined by remote collaboration and online recruitment, cybersecurity must expand to include human verification and ongoing trust checks.
Ultimately, cyber resilience now depends not just on codes and firewalls, but on verifying every face in a Zoom window before they touch any code, data, or systems. The future of cybersecurity and international cyber warfare highlights the vulnerability of national defenses to remote infiltration. The solutions lie in vigilance, cross-functional cooperation, and continual rethinking of what workplace trust really means.
Share this :