Penetration Testing VS Vulnerability Testing: Understanding the Key Differences
Hoplon InfoSec
29 May, 2025
In today’s interconnected world, cybersecurity is more than just a technical necessity; it’s a critical component of trust and business success. Two essential practices penetration testing and vulnerability testing play a pivotal role in keeping your systems secure. Although these terms are often used together, they serve distinct purposes and require different approaches.
Understanding how these two testing strategies differ, and how they complement each other, can transform your security posture from reactive to proactive. Let’s break it down.
What Is Vulnerability Testing?

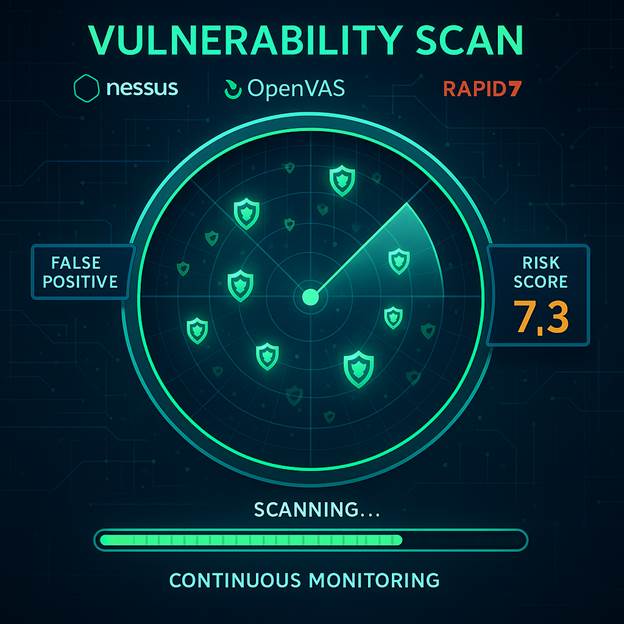
Vulnerability testing, also referred to as vulnerability assessment or scanning, is a process that identifies, categorizes, and reports known security weaknesses in IT systems. It is often automated and used routinely to maintain awareness of the current threat landscape affecting your assets.
Key Characteristics
- Automated Tools: Most vulnerability scans are conducted using automated tools such as Nessus, OpenVAS, Rapid7 InsightVM, or Qualys. These tools are configured to scan specific targets for known vulnerabilities.
- Scope and Coverage: It covers a wide range of IT assets, servers, databases, endpoints, applications, and cloud services.
- Regular and Scalable: Vulnerability scanning can be run as frequently as needed, making it ideal for continuous monitoring and compliance purposes.
- Risk Identification: Reports typically include CVSS (Common Vulnerability Scoring System) scores, severity ratings, and remediation recommendations.
Limitations
While highly valuable, vulnerability testing also has several limitations:
- False Positives: Automated scanners can sometimes flag issues that are not truly exploitable, leading to wasted remediation efforts.
- Lack of Context: These tools assess technical flaws without considering the system’s actual architecture, user behavior, or business impact.
- No Proof of Exploitability: Vulnerability tests do not demonstrate whether an attacker can chain or exploit the findings in a real-world scenario.
- Over-Reliance on Signatures: Scanners depend on updated databases; newly discovered vulnerabilities might not be detected until signatures are updated.
Real-World Example
An IT administrator at a financial institution runs a weekly vulnerability scan across all branch office servers to identify and prioritize patching of outdated services, unencrypted protocols, and exposed ports. However, a flagged vulnerability turns out to be a misconfiguration with no actual security impact, highlighting the need for manual review and prioritization.
What Is Penetration Testing?

Penetration testing, also known as pen testing or ethical hacking, is a simulated cyberattack conducted by skilled professionals to evaluate the effectiveness of security defenses. The primary goal is not just to identify vulnerabilities, but to actively exploit them in a controlled environment to assess their impact.
Key Characteristics
Manual Execution: Unlike automated vulnerability scans, pen testing requires human ingenuity. Testers use a mix of publicly known exploits, custom scripts, and social engineering techniques.
Tailored Objectives: Tests are designed with specific goals in mind, such as gaining admin access, exfiltrating sensitive data, or breaching isolated network segments.
Deep Analysis: Penetration tests often simulate multi-step attacks and lateral movement within networks, mimicking advanced persistent threats (APTs).
Reporting and Remediation Guidance: Reports include not only exploited vulnerabilities but also detailed walkthroughs of attack paths, impact assessments, and prioritized remediation steps.
Types of Penetration Testing
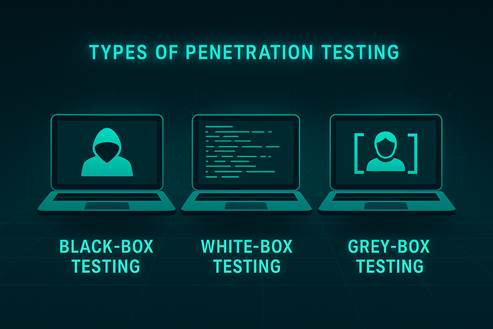
- Black-Box Testing: The tester has no prior knowledge of the target system. This simulates the approach of an external attacker and tests defenses from the outside.
- White-Box Testing: The tester has full access to internal documentation and system architecture. This allows for a more thorough, in-depth analysis of the system’s resilience.
- Grey-Box Testing: The tester has partial knowledge of the system. This approach balances realism and efficiency, mimicking an attacker with limited insider information.
Each type of test provides different insights. Black-box tests evaluate external defenses, white-box tests assess internal security controls, and grey-box tests offer a realistic scenario of what a sophisticated attacker might achieve with some inside information.

Real-World Example
A company launching a new mobile banking app hires a cybersecurity firm to perform a penetration test. The ethical hackers discover an insecure direct object reference (IDOR) vulnerability that allows unauthorized access to other users’ transaction histories. The issue is resolved before launch.?
Major Differences Between the Two

Although both vulnerability testing and penetration testing contribute to a stronger security posture, they serve very different purposes and are conducted in different ways.
- Objective: Vulnerability testing aims to create a list of known issues. Penetration testing aims to exploit weaknesses to demonstrate real-world risks.
- Tools vs. Expertise: Vulnerability testing is tool-driven and automated; penetration testing is human-driven and highly analytical.
- Depth of Engagement: Vulnerability scans offer breadth by covering many systems. Penetration tests go deep into fewer systems to expose chained vulnerabilities.
- Output and Reporting: Vulnerability testing produces a technical report listing issues and their severity. Penetration testing offers a narrative of how the security was breached, what was accessed, and what that means in context.
- Regulatory Requirements: Many compliance frameworks (e.g., PCI-DSS, HIPAA) require both types of testing for comprehensive security validation.
When to Use Each?

Use Vulnerability Testing
- For Routine Maintenance: Weekly or monthly scans help identify and fix new vulnerabilities quickly.
- To Maintain Compliance: Regulations often mandate regular vulnerability assessments.
- For Broad Awareness: Ideal for gaining visibility into enterprise-wide risk exposure.
- During Infrastructure Changes: When upgrading systems, changing configurations, or migrating services to the cloud.
Use Penetration Testing
- Annually or Biannually: As part of a red team/blue team exercise or regular security audits.
- Before Launching Products: Especially for customer-facing apps or services.
- After Major Changes: Following a merger, significant network architecture shift, or implementation of new security controls.
- To Simulate Real Attacks: Understand how attackers might move through your system, escalate privileges, or exfiltrate data.
Why You Need Both?
Think of vulnerability scanning as using a medical checklist like measuring temperature, blood pressure, and general vitals. Penetration testing, on the other hand, is like sending in a doctor for a detailed physical examination, probing and diagnosing deeper systemic issues that basic tools can’t catch.
Vulnerability scans will show you what’s vulnerable. Pen tests will show you what’s dangerous.
Running both helps organizations:
- Prioritize risk: Not every vulnerability is exploitable, and not every issue is high risk. Pen testing reveals actual exploitability.
- Measure resilience: How well do your defenses hold up under simulated attacks?
- Improve incident response: Pen tests can uncover flaws in detection, alerting, and response mechanisms.
- Strengthen user awareness: Social engineering during pen tests can assess how well employees recognize and react to suspicious activities.
Tools Commonly Used
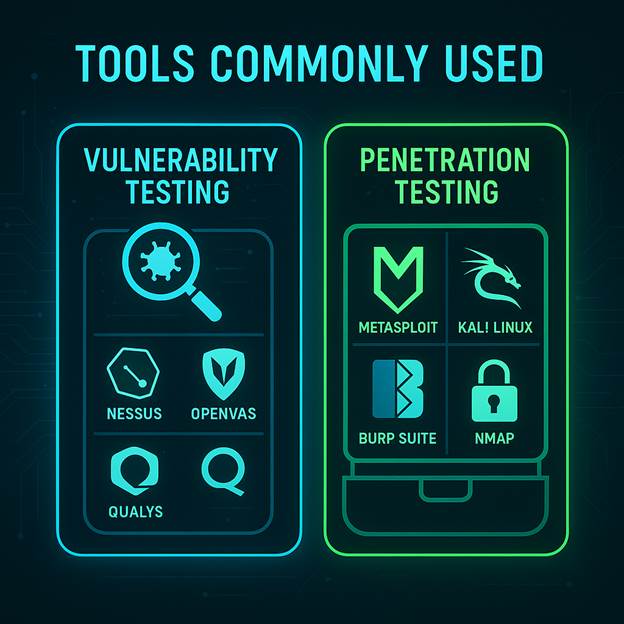
For Vulnerability Testing
- Nessus: Known for its comprehensive plugin library and accurate detection. Ideal for enterprise environments needing detailed vulnerability insights.
- OpenVAS: A powerful open-source option, suitable for organizations looking to customize scanning rules and reduce costs.
- Nexpose (Rapid7): Integrated with Rapid7’s Metasploit for exploitation validation; useful in environments focused on remediation prioritization.
- QualysGuard: Cloud-based and highly scalable, best for continuous monitoring across large, distributed environments.
- Microsoft Defender Vulnerability Management: Seamlessly integrates with Microsoft environments, offering endpoint-centric risk insights.
For Penetration Testing
Metasploit Framework: A versatile platform for developing and executing exploits; widely used by penetration testers for payload creation and post-exploitation.
Burp Suite: Popular among web application testers for intercepting and modifying HTTP/S traffic to find vulnerabilities in real-time.
Kali Linux Toolset: A Linux distribution loaded with hundreds of tools tailored for reconnaissance, exploitation, and reporting; suitable for all forms of testing.
Nmap: Used for network discovery and port scanning; serves both vulnerability assessments and initial reconnaissance in pen tests.
Cobalt Strike: Advanced red team tool simulating real-world threat actor tactics; valuable for post-exploitation and command-and-control testing.
Each tool plays a role, but the value of pen testing lies heavily in the skills and experience of the tester, whereas vulnerability testing relies more on the accuracy and timeliness of the scanning tools.
Common Misconceptions
Misconceptions around penetration testing and vulnerability testing persist largely due to a lack of understanding about the unique purposes and methodologies behind each. These misunderstandings can lead to critical gaps in security strategy, budget misallocation, and compliance issues.
- “Pen testing is just advanced vulnerability scanning.” While they both look for flaws, pen testing is about strategy, creativity, and simulating real-world attacks. Vulnerability scanning is about detection and cataloging.
- “Vulnerability scanning is enough for compliance.” Some compliance frameworks require penetration tests to validate that identified vulnerabilities are not just theoretical.
- “Pen testing always requires a big budget.” While thorough pen tests can be expensive, scoped and targeted testing is possible even for smaller organizations.
- “Pen tests make systems less secure.” A well-conducted pen test is safe and does not damage the system. It should be done with proper planning, rules of engagement, and executive approval.
Final Thoughts
Security is not a one-time fix but a continuous journey. By strategically deploying both vulnerability assessments and penetration tests, organizations can proactively identify risks, validate their severity, and reinforce their cybersecurity defenses against real-world threats.
Stay tuned for our next post, where we’ll break down the process of preparing for a penetration test and how to turn the findings into an actionable security roadmap.
Did you find this article helpful? Follow us on Twitter and LinkedIn for more Cyber Security news and updates. Stay connected on Facebook and Instagram as well. At Hoplon Infosec, we’re committed to securing your digital world
Share this :